MalCare Ensures Unmatched Protection Against User Registration Privilege Escalation Vulnerability
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

Imagine discovering that your WordPress site, which should be secure and under strict control, has suddenly become accessible to unauthorized users who have the same administrative powers as you. This nightmare scenario was recently made possible for users of the popular User Registration plugin, which suffered from a critical privilege escalation vulnerability. This breach meant that essentially, any subscriber could upgrade themselves to an administrator, gaining abilities to alter content, install potentially dangerous software, and overall, control the site to their liking.
Thankfully, MalCare’s Atomic Security had already safeguarded its users against this threat, without the need for last-minute updates. Unlike other security plugins such as Wordfence, which had to quickly devise and implement new rules to address this vulnerability, Atomic Security was inherently equipped to handle it thanks to our deep integration with WordPress’s architecture.
This proactive capability stems from MalCare’s comprehensive understanding of WordPress’s unique architecture and vulnerabilities. This ensured that users relying on MalCare had their sites secure without any need for panic. This unmatched ability to proactively secure WordPress sites against such vulnerabilities illustrates the effectiveness of a well-integrated firewall like MalCare’s Atomic Security.
What is the User Registration vulnerability?
Plugin information
- Vulnerable plugin version: v3.1.5 and earlier
- Patch release version: v3.2.0 and newer
User Registration by WPEverest lets users create custom registration forms of any kind for their WordPress site, be it simple forms or complex multi-step ones. It boasts of unlimited customization options for each field and form, along with premium add-ons that include extra functionalities. With over 70,000 active installations, it is one of the most popular WordPress user registration and login plugins.

About the vulnerability
The User Registration plugin uses a form_save_action() function in its UR_AJAX class to save form data and settings. Unfortunately, due to an insecure implementation, this function allows all authenticated users to modify the form, including the registration default user role setting.
Although the function includes a nonce check, this nonce was available to all authenticated users, like subscribers, on the edit profile page.
This vulnerability stems from the absence of capability checks within the AJAX function. This issue is compounded by the fact that authenticated users can access the necessary nonce to run the form_save_action() function. As a result, authenticated users, including those with subscriber-level access, have the ability to alter the default role in the registration form to that of an administrator. This flaw enables attackers to register new accounts with administrative privileges, thereby gaining full control over the website.
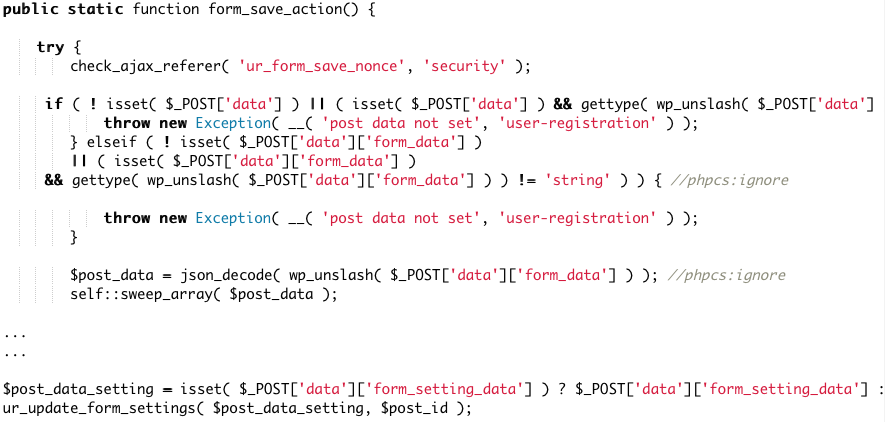
Like any other privilege escalation vulnerability, this too can lead to a total compromise of the site. Once an attacker obtains administrative access to a WordPress site, they have the same capabilities as a regular administrator. This includes the power to upload plugin and theme files, which could be malicious zip files with backdoors, as well as modify posts and pages. Such modifications can be used to redirect visitors to malicious websites or to inject spam into the site content.
To achieve this, the user_registration_form_save_action() function has to be used first to change user_registration_form_setting_default_user_role for that particular post ID or form ID to Administrator. The user_registration_user_form_submit() function can be then used to register a user with the Administrator role.
The flow is shown below:
- ur_update_form_settings() function uses update_post_meta
- this is used to edit user_registration_form_setting_default_user_role option in wp_postmeta table
- user_form_submit() function uses insert_wp_user and update_user_meta to add a new user.
This vulnerability has now been fixed with the release of User Registration v3.2.0 on April 15, 2024.
Who discovered this vulnerability?
The User Registration privilege escalation vulnerability was discovered by AyeCode security researcher Stiofan, who reported it to Wordfence’s Bug Bounty Program. Consequently, Wordfence informed WPEverest, the plugin developers, on April 10, 2024, following which a patch was released on April 15, 2024.
How is your WordPress site at risk?
Your WordPresss site is at risk if it runs the User Registration plugin v3.1.5 or earlier.
Imagine securing every door and window in your home, only to inadvertently leave the back door wide open. This is essentially what has happened with the vulnerability found in the User Registration plugin—an oversight that inadvertently invites trouble.
In simple terms, an ordinary user with subscriber privileges could potentially hijack your online domain by escalating their privileges to an administrator role without your consent.
This issue extends beyond just unauthorized access; it jeopardizes your entire site, leaving it vulnerable to anyone who exploits this flaw. The potential damage is considerable, comparable to an intruder having complete control inside your home. With administrative access, they can:
- Transform your website into a source of online mischief, affecting other sites and possibly leading to penalties from search engines like Google;
- Use your site to mine for cryptocurrency, significantly slowing down or even crashing your site;
- Send out masses of deceptive or spammy emails to your site visitors, damaging their trust in your website;
- Redirect your visitors to malicious or adult sites;
- Install hidden backdoors to regain access to your site even after you think the issue has been resolved;
- Damage your site to the extent that you might need to rebuild it from scratch, hoping that you have a backup from before the chaos ensued.
Hence, we strongly recommend you update the User Registration plugin on your WordPress site immediately, at least to v3.2.0, regardless of whether you are a MalCare user or not.
What are the symptoms of a hacked site?
If you have reason to suspect that your WordPress site might have fallen victim to attacks exploiting this vulnerability, check for:
- a query containing user_registration_form_save_action and/or user_registration_user_form_submit in your site’s database logs
- a record in your site’s activity or firewall logs containing the path /wp-admin/admin-ajax.php
The presence of such a query and/or path could mean that your site is compromised. Take immediate action to update the User Registration plugin and scan and clean your site using MalCare.
How to clean your site?
When your WordPress site has been compromised, maintaining calm is crucial. Below are effective steps to recover and boost your site’s security:
- Start with a MalCare scan: Deploy MalCare to swiftly remove any malware and to strengthen your site’s defenses against future incursions with its Atomic Security feature.
- Update plugins and themes: Consistently monitor and update your plugins and themes, especially the User Registration plugin. Older versions of plugins and themes may contain vulnerabilities that hackers target. MalCare’s dashboard provides notifications about outdated plugins and themes, enabling easier maintenance and enhanced site security.
- Review user roles and permissions: Examine the roles and permissions assigned to all users. Immediately revoke access if anything appears abnormal.
- Refresh WordPress salts and security keys: This action forces all users to log out and terminates active sessions, enhancing your site’s security. MalCare includes this in its cleanup routine for convenience.
- Alter login credentials: Change your admin password without delay. Ensure that all user sessions are terminated, advise users to update their passwords, and promote the creation of strong, new passwords.
- Strengthen login security: Implement two-factor authentication (2FA) and limit login attempts to minimize the risk of unauthorized entries.
- Monitor your site continuously: MalCare takes charge of this aspect by continually monitoring your site for any unusual activities, providing alerts for potential threats, and persistently scanning for malware.
How does MalCare protect your site?
MalCare provides robust security for your WordPress site with a range of essential features:
- Rapid malware detection and cleanup: MalCare conducts daily scans of your site, automatically identifying any malware presence. Should any malware be detected, its potent removal tool swiftly eliminates it, restoring the security and health of your site.
- Enhanced firewall protection: MalCare includes Atomic Security, a sophisticated firewall that monitors incoming traffic and blocks malicious attacks effectively. It’s continuously updated to defend your site against the latest security threats.
- Vulnerability alerts: MalCare vigilantly monitors your plugins and themes for potential vulnerabilities. If it detects any issues, it promptly alerts you, enabling you to fortify your site’s defenses.
- Bot protection: Recognizing the impact bots can have on your site’s performance, MalCare establishes robust defenses to prevent bot interference, ensuring your site operates smoothly.
- Reliable backups: MalCare’s automated, offsite backup system keeps you prepared for any situation. These backups are your safety net, allowing for quick recovery if problems arise.
MalCare envelops your WordPress site in a protective shield, combining proactive measures with strong defenses to maintain your site’s security and integrity.
Category:
Share it:
You may also like

How to Fix the Google Blacklist Warning from Your Website
Google blacklist is a colloquial term used to describe big red warnings visible when visiting websites. There are a few flavours, depending on various factors, but they all mean that…

MalCare Stands Strong Against WP Activity Log Premium SQL Injection Vulnerability
A significant SQL injection vulnerability was identified in the WP Activity Log Premium plugin, a popular tool for tracking user activity on WordPress sites. An SQLi vulnerability poses a serious…
Fix Pharma Hack on WordPress and SEO
Pharma hack is a prolific malware that redirects visitors from your site to an online pharmacy that sells Viagra, Cialis, Levitra, Xanax, Tadalafil, and other drugs. It also shows up…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








