Protect against WordPress XSS Attacks: A Complete Guide
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

WordPress XSS or cross-site scripting attacks are the most common WordPress attack mechanisms today. They target visitors of your website, wanting to steal their information. The worst part of XSS attacks is that attackers use vulnerabilities on your WordPress website to do this.
Protect your visitors from XSS attacks by installing a WordPress firewall.
On the surface, XSS attacks don’t appear very threatening, especially when compared to other attacks like brute force or SQL injections. Cross-site scripting attack is carried out using JavaScript, and JavaScript is tightly controlled by the browser. Thus, it should have very limited access to the rest of a person’s device. That is the case, but that doesn’t translate to less danger.
WordPress XSS attack is a gateway to more damaging attacks and should be treated as dangerous in its own right.
TL;DR: The best way to stop hackers from exploiting XSS vulnerabilities is to install a strong WordPress firewall. MalCare’s advanced WordPress firewall prevents hackers from stealing your visitors’ data. In fact, MalCare is a comprehensive WordPress security plugin that bundles a powerful malware scanner and removal tool, with the firewall together for complete security.
What is a WordPress XSS attack?
A cross-site scripting attack, WordPress XSS for short, is when an attacker injects malicious JavaScript code into a website. When a visitor lands on that website, their browser executes the code. The malicious script is assumed to be from a trusted source, which in this case is the website.
XSS attacks are possible because the website has a cross-site scripting vulnerability. The security vulnerability is that the website uses external input in the output it generates, without first validating or checking it.
An analogy for how XSS attacks work: Imagine for a moment you are working with ABC company. ABC hands you a folder with the work that you need to do. You read it and start doing the work. You assume that the folder is trustworthy, because it belongs to ABC. However, suppose that ABC left their work folders out in the open, where anyone could come in and insert a page. A malicious actor could insert a page that has bad instructions. Although they should, ABC doesn’t check any of the inserted pages. Instead, they hand the folder directly to you. You proceed. This is a simplistic analogy because obviously you can gauge good from bad, but your browser can’t. It follows instructions to the letter.
Check if your site has a WordPress XSS vulnerability
XSS vulnerabilities exist in code; either WordPress core code or that of plugins and themes. Unless you are developing custom code for your website, it is unlikely that you are dealing with user input directly, and therefore figuring out how to make it secure doesn’t fall within your purview. As a site admin, you cannot prevent an XSS vulnerability.
The only real way you can check if your WordPress website is susceptible to XSS attacks is to use a scanner like XSS Hunter, or hire the services of a penetration tester.
However, that doesn’t mean you cannot protect your website visitors from potential XSS vulnerabilities on your website. Installing a WordPress firewall keeps out the attacks and goes a long way into protecting your visitors. MalCare’s Atomic Security is a revolutionary firewall that is deeply integrated with WordPress and blocks XSS attacks by default, without needing custom rules for every new discovered vulnerability.
Additionally, you can keep a tab on the installed plugins and themes. If any of them disclose XSS vulnerabilities, make sure to update them as soon as possible. MalCare makes this easy, because it scans your website every day. If there is a vulnerable plugin or theme discovered, you can update it safely from the MalCare dashboard.

WordPress XSS Protection: 5 ways to prevent XSS attacks
WordPress cross-site scripting vulnerabilities are found in code, and there is little a WordPress admin can do to remove those vulnerabilities. However, there are definitely things you can do to protect your site visitors from XSS attacks.
1. Install a web application firewall
Firewalls are your best defense in the face of a constantly evolving threat. Firewalls, like MalCare, have special XSS rules which look for requests that can contain suspicious text typically associated with attacks. In fact, XSS attacks are evolving rapidly, confounding many firewalls. MalCare’s advantage is that it is deeply integrated with WordPress, and is designed to block all kinds of attacks out of the box.
2. Update all your plugins and themes
WordPress security vulnerabilities are discovered in plugins and themes all the time. Responsible developers release security patches for them, so that the websites are not at risk. Once the patches are available, the people who discovered the vulnerabilities release the news. Therefore, websites that have not updated their plugins and themes become targets for malicious actors.
3. Install a good WordPress security plugin
XSS attacks are really dangerous for website owners, if the targeted user is an admin. XSS can be used to get login credentials, and then infect the website with malware. A good security plugin will help you monitor users for unusual activity, and the daily scans will pinpoint any malware quickly. MalCare scans your site daily, staying on top of any infections that may have occurred after a successful XSS exploit.
4. Implement WordPress hardening
WordPress hardening is a series of steps that you can take to make your WordPress site more secure in general. Of these, we especially recommend two-factor authentication. The biggest danger of XSS attacks is the theft of login credentials and identities, so two-factor authentication goes a long way in preventing stolen credentials being used to access your site. Other hardening steps like disabling XML-RPC are also good to implement.
5. Follow the least privilege user policy
If a user’s account is compromised because of an XSS attack, the damage they can potentially do is limited by their permissions on the website.
If you are a WordPress developer, always sanitise user inputs. Your website should check every input for malicious code, especially before displaying it as output.
What if an XSS exploit attack gets malware on your website
Site visitors are ostensibly the targets of XSS attack, however that group can also include website administrators. If there is a cross-site scripting vulnerability on your website, and an administrator’s account was compromised, you should assume your website security is compromised as well.
In addition to stealing data from individuals, XSS attacks are also used to perpetuate other attacks like remote code executions.
So, even though a WordPress XSS attack doesn’t immediately translate into malware, it is better to err on the side of caution. If your website has malware, deal with it right away.
Scan your website
The only way to figure out if your website really has malware is to scan it. There are several ways you can do this, however, not all of them are equally effective.
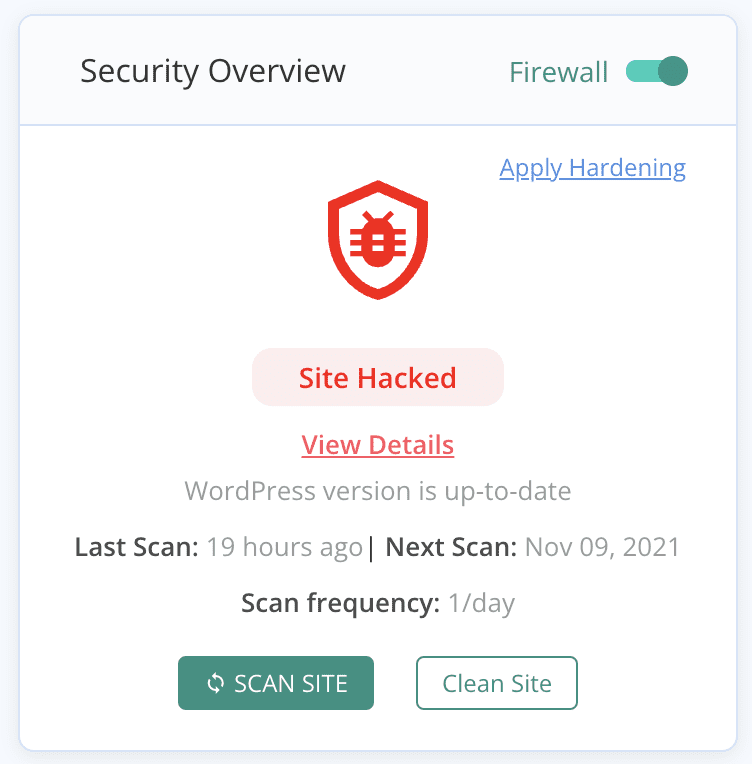
We recommend you deep scan your website with a security scanner to find the smallest traces of malware in your website or database. This is the definitive way to determine if there is malware on your website. Once you have an answer, you can follow our guide on dealing with a hacked WordPress site to get rid of it.
How WordPress XSS attack works
XSS attacks work in two parts: the injection and the fallout.
First, the malicious actor injects the malicious JavaScript code into a vulnerable website. This can be done in a few ways, which we will be discussing in the next section. Next, when a visitor lands on the site, the browser executes the malicious JavaScript code because it thinks it is part of the website.
The consequence of this is that a hacker now has access to all the visitor’s data that is visible to the website. This might include their cookies, session information, and login data. The information can be used to launch other attacks like phishing or cookie stealing.
What does this have to do with your WordPress website?
At this point, it looks like the problem lies with the visitor and their browser. However, that is not accurate. The browser would not execute the malicious code unless it thought it was a part of a trusted website. If the visitor is on your site, the trusted website is yours.
The XSS attack works because a website needs to have an XSS vulnerability. That means it should accept user input without checking or validating the input in any way. Only then does WordPress XSS exploit allow an attacker to inject JavaScript into the website without a problem.
Let’s look at an example.
On a WordPress blog, the admin wants to be able to allow readers to post comments under articles. The admin installs a plugin to manage said comments.
When a reader wants to post a comment, they type it into a text field, which has been provided by the plugin. Anyone can type up their comment and send it to the website database. So far so good.
The problem appears when someone who is not-so-nice types up a comment, but adds a script to it as well. The input would be something along the lines of: “This cake recipe is superb! <script> //bad code here </script>” The script tags enclose JavaScript code that is malicious and designed to interact with other visitors to the site.
The plugin doesn’t check the comments for these scripts, assuming that it is all text. And then saves it, as is, to the database. This is a WordPress XSS vulnerability.
Now, another visitor comes to the blog page, and their browser loads the page and the comments. The website database has saved all the comments, and so sends it to the browser so the new visitor can see them. But because there is JavaScript in one of the comments, the browser thinks that bit of code needs to be executed. And it does that, assuming the code is a part of the website. But it wasn’t. The website thought the code is text, and has saved it as such. The browser sees a script and executes it. This is how an XSS attack works.
If the plugin checked the comments for malicious code before saving them to the database, the website wouldn’t have the XSS vulnerability. The browser wouldn’t receive the JavaScript code, and the visitor’s data would be safe.
Types of cross-site scripting attacks
Cross-site scripting attacks are categorised depending on where the code is stored and executed. There are 3 main types of attacks: stored or persistent, reflected, and DOM. However, they are not mutually exclusive. XSS attacks can be a combination of these types. It is still useful to understand these types though, and see how they intersect with each other.
In both stored and reflected XSS attacks, the website is involved in the attack. The malicious code actually goes into the web server or database, and is sent back to the visitor. The only difference is whether the attacker sends it to the website or the visitor themselves.
To understand types of XSS attacks better, check out this dedicated resource.
That being said, the types of XSS attacks shouldn’t be of concern to you, because there is little you can actively do to resolve cross-site scripting vulnerabilities. It is not feasible to vet plugins and themes to see if they have these vulnerabilities before they are discovered after all. However, once they are discovered, you should update them right away.
You can protect your website visitors from cross-site scripting attacks by installing a firewall. This is the only real defense against malicious code.
Consequences of XSS attack in WordPress
The main targets of XSS attacks are your website visitors, or more specifically their information. Therefore, if an XSS attack is successful, the malicious script will have access to all the information on the visitor’s browser to which your website has access. This includes the cookies, session information, and so on.
A lot of things can go wrong at this stage:
- The hacker gains access to the visitor’s private data, and can take over their account on your website. Things can escalate fast from this point on.
- The hacker can impersonate the visitor because they have access to their data
- The malicious script can send the visitor to another website, or show them content that is not from the original site they visited. The malicious script can even change the way the page appears on the browser.
- In really bad cases, the attacker can target the visitor with a social engineering attack like WordPress phishing.
For the website, the impact of a WordPress XSS attack can vary. WordPress websites can get in serious trouble when they store private user data which can be stolen by malicious actors. If the user in question is an admin or someone with sufficient privileges, then the hacker can impersonate them and compromise the website entirely.
Takeaways
A WordPress XSS attack is very common and they target website visitors to steal data. As a responsible website admin, you want to protect your visitors from harm. Installing a WordPress firewall will go a long way in doing that. MalCare is a sophisticated WordPress firewall, and a great security plugin. The security vulnerability and malware scanner helps mitigate the ill effects of malware quickly and effectively.
FAQs
Is WordPress vulnerable to XSS?
Yes, WordPress is vulnerable to XSS attacks. There are many XSS vulnerabilities discovered in the WordPress core files, in addition to the plugins and themes. Responsible developers resolve these WordPress XSS vulnerabilities quickly and update their software so it cannot be exploited by hackers.
What does cross-site scripting mean?
Cross-site scripting (XSS) is a cyberattack that uses malicious scripts on your web browser to hack browser session cookies to steal highly sensitive data. Used effectively, cross-site scripting can steal passwords and financial information. WordPress XSS hacks are very difficult to defend against unless you use a powerful firewall.
How to Prevent XSS in WordPress?
The simplest way to defend against XSS attacks in WordPress is to install a firewall that can effectively block out malicious traffic. For WordPress, we also recommend hardening your website against typical hacks.
Share it:
You may also like

MalCare Ensures Proactive Protection Against WP-Members XSS Vulnerability
MalCare continues to protect its customer sites from all kinds of attacks, even the ones exploiting zero-day vulnerabilities. The recent stored cross-site scripting (XSS) vulnerability found in the WP-Members Membership…
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…

MalCare Proactively Defends Against Icegram Express SQL Injection Vulnerability
MalCare’s recent data has revealed numerous attempts to exploit a newly found SQL injection vulnerability in the Icegram Express plugin. Attackers commonly use this sophisticated SQL injection technique to extract…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








