Fix Japanese Keyword Hack on WordPress and SEO
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

Japanese keywords showing up randomly on your website search results can be perplexing. If you don’t already know why, it is the result of malware on your site.
The Japanese keyword hack is confounding on many levels. Website owners experience many symptoms in the beginning, like being unable to login or being redirected when accessing their websites. Others have experienced unknown users getting added to their Google Search Console, and a drop in ad revenue. The coup de grace is evidently the Japanese text showing up in the search results.
The first thing you need to do is scan your WordPress website, and then proceed to malware removal. Fixing the Japanese SEO hack is difficult, and many users find that it keeps coming back.
In this article, we will show you exactly how to remove Japanese keyword hack from your WordPress website, and make sure it doesn’t come back again.
TL;DR: Get rid of the Japanese keyword spam from your WordPress website in 5 minutes. Install MalCare, sync your website and you’re done. MalCare cleans your website, and protects it from being hacked again. It is your all-in-one WordPress security solution for enduring peace of mind.
What is the Japanese keyword hack
The Japanese keyword hack or Japanese SEO spam is when hackers inject spammy Japanese pages into your site, so when the page gets indexed by Google, your website will start ranking for those keywords.
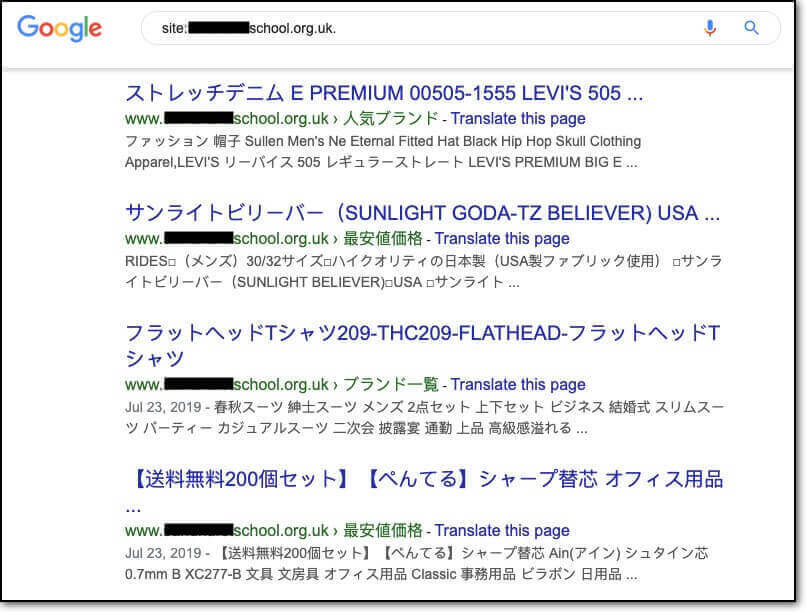
Important: If your search results look like this, scan your site immediately for malware.
Japanese SEO attack is very similar to the pharma hack and SEO spam hack, because the malware uses your site to boost the rankings of other websites. This is a typical tactic used by hackers because they want to promote websites and products that would ordinarily not be allowed under Google Ads or search policies. Grey market or illegal products and services, for instance. The malware can also redirect your website users to spam websites.
The problem with all of these malware effects is that the average visitor doesn’t realise that you are a victim of malware, so they might associate your brand with the poor experience. On the off chance that a visitor knows that this is due to malware, chances are that they are going to be scared of getting malware on their devices and leave very quickly. Either way, your website and brand loses out.
Related article: Chinese search results spam
Diagnostics for the Japanese keyword spam on your website
Malware doesn’t always come with alarm bells, and often people find out their WordPress websites are hacked only after a while. The problem with finding out late is that the longer it stays on a website, malware can cause some serious damage.
We’ve seen Google deindexing websites, and web hosts suspending sites with malware—and that’s just the tip of the iceberg. You could lose your entire website because of missed malware; it really is that dangerous. It is critical to discover malware as soon as possible, and there are a few ways to do that.
Scan your website for malware
The only definitive way to know if your website is hacked is to scan it. Scanners check the files and database of your website for malware. However, all scanners don’t work in the same way, so you can get varying results from them, depending on how they work and what they scan.
Deep scan your website with MalCare
Find every instance of the Japanese keyword hack on your website in minutes with MalCare. The scanner looks into every file and every database table for malware code and backdoors. If there is any malware on your website, no matter how well it is hidden, MalCare will find it.
We recommend MalCare for a number of reasons:
- Scan the database and files of the website
- Finds malware and backdoors
- Scans don’t impact the performance of your website
- Uses an advanced algorithm for scanning
- Completely free to use
MalCare’s scanner uses a strong underlying algorithm to detect malware, which goes over and above the file matching that other malware scanners do. Because of this reason, not only is all the malware detected—which is especially important in case of the Japanese keyword hack—but there are fewer chances of false positives.
Using an online scanner
As a first-level diagnostic tool, you can use an online scanner to check for malware. In the case of the Japanese keyword hack, an online scanner will detect the malware for sure, because the spam code is in the visible parts of the website. Sucuri SiteCheck will show up the following code, if it detects the Japanese keyword spam on your website:
known spam detected: spam-seo?japanese.0 The caveat for using an online scanner is that their ability is limited. Online scanners can only access the frontend of your website, like the posts, pages or comments from the database, and the uploads folder from the files. The core WordPress files and some other critical parts of the website are inaccessible externally for security reasons. Thus, online scanners cannot scan those places for malware.
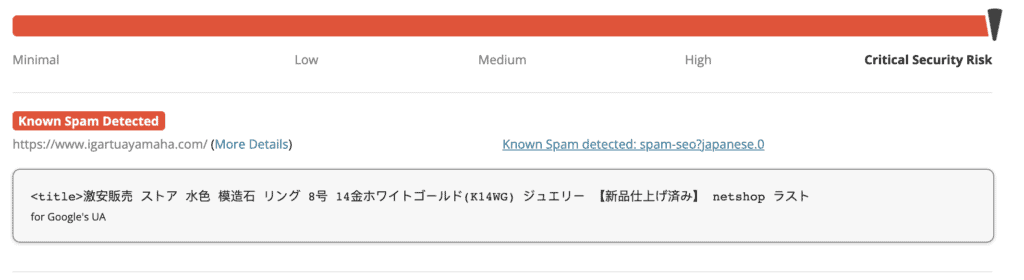
However, malware can and very often does reside in core WordPress folders. Therefore, while an online scanner is a good diagnostic tool, it cannot be expected to present a complete picture.
Manual scanning
The least efficient way to scan your website is to do so manually, by checking the files, folders, and database for malware. As we have said before in this article, malware can be absolutely anywhere. Hackers want to keep the malware hidden for as long as possible, and will come up with clever ways to avoid detection.
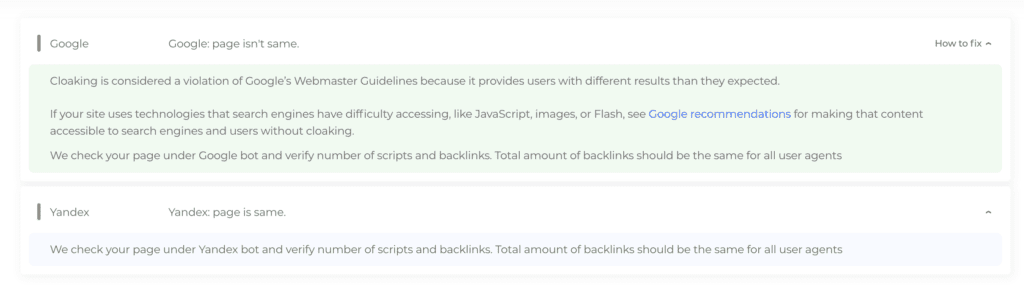
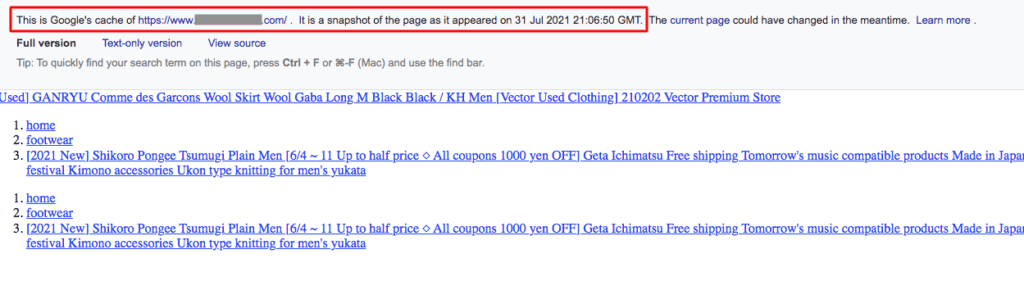
In the case of the Japanese keyword hack, you can see an instance of this tendency from the results on Google. Try clicking through one of the links with Japanese characters. More often than not, you will either see your website as it is supposed to be, or a 404 page. The hacker has used cloaking to achieve this cognitive dissonance, so you are thrown off guard.
Look at the following example:
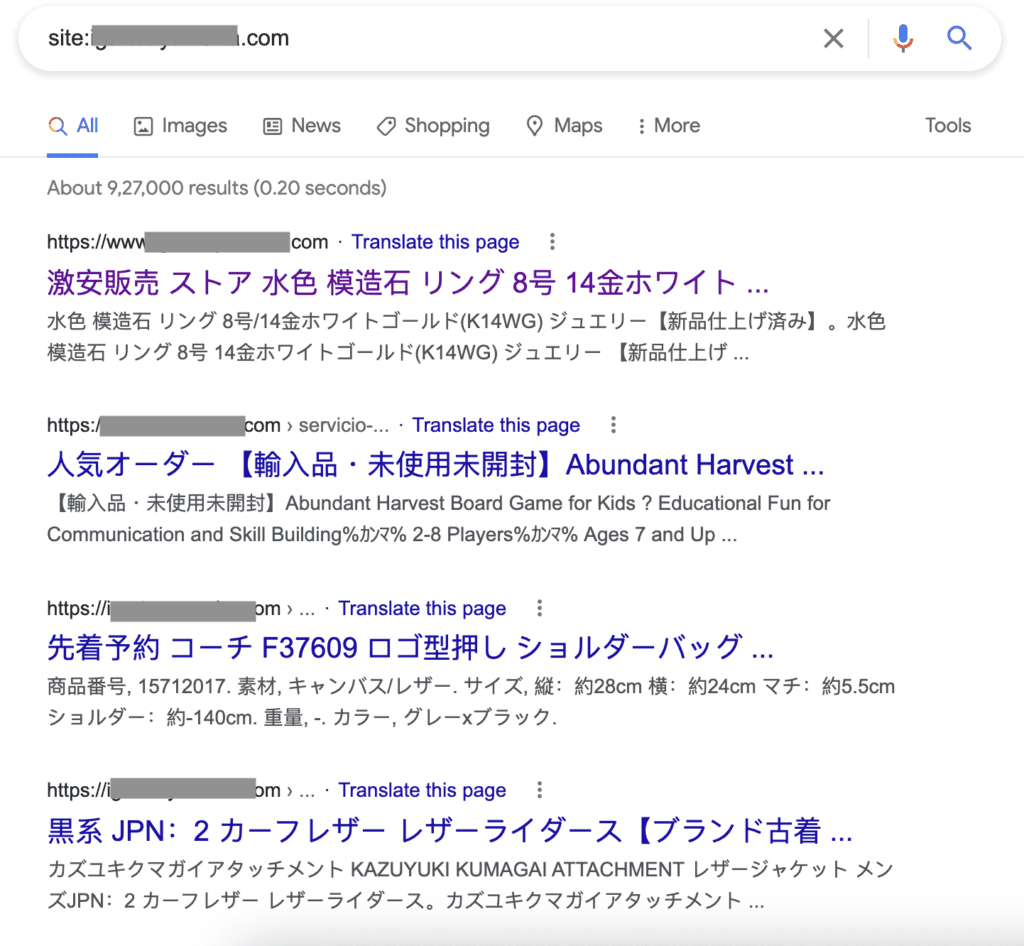
The image above shows the search results full of Japanese characters. The image below is what a user, including the website admin, sees when they click through the first result result.
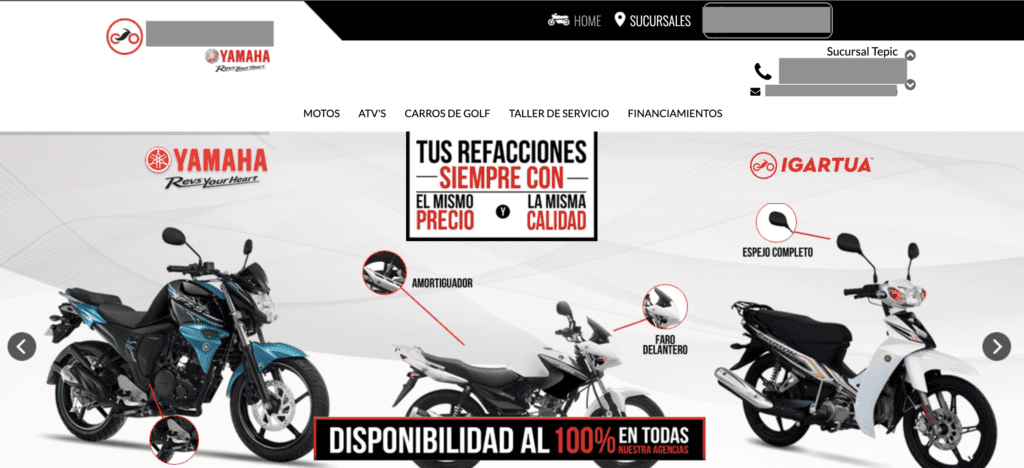
Looks like it is absolutely normal. No Japanese characters in sight. But, if you use a little code to fool the website into thinking you are googlebot and not a human, you will see this page instead:
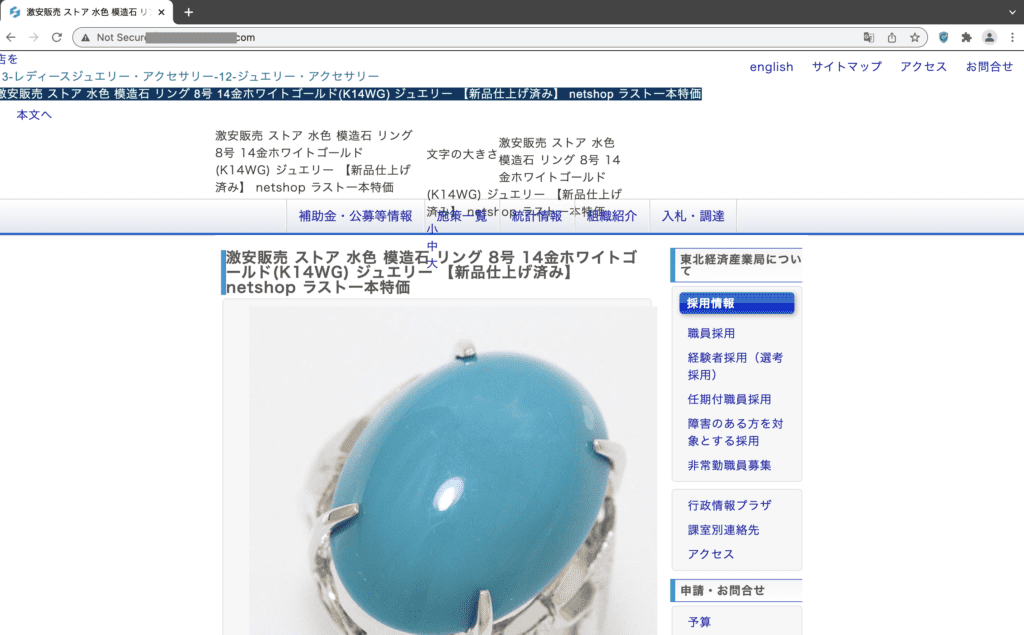
Vastly different, isn’t it? This is an example of cloaking and it hides the Japanese SEO spam very effectively from site admin for a long time.
There are many other methods that hackers use to disguise malware on websites. Therefore, the best way to detect a hack on your website is to scan it using MalCare.
Other diagnostics
Deep scanning your website with MalCare is the only method of detection that stands alone. If you don’t want to deep scan your website, then these other diagnostics can help determine if your website has the Japanese keyword hack.
- Check search results for your site, using site:mysiteurl.com to get results that are related to your domain. If you see pages that you have not created, this is a good sign of an SEO spam infection. For the Japanese keyword malware specifically, use the site:mysiteurl.com japan to look for evidence.
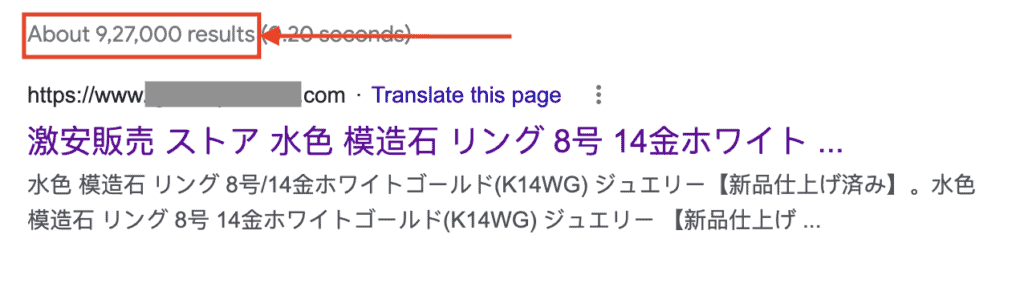
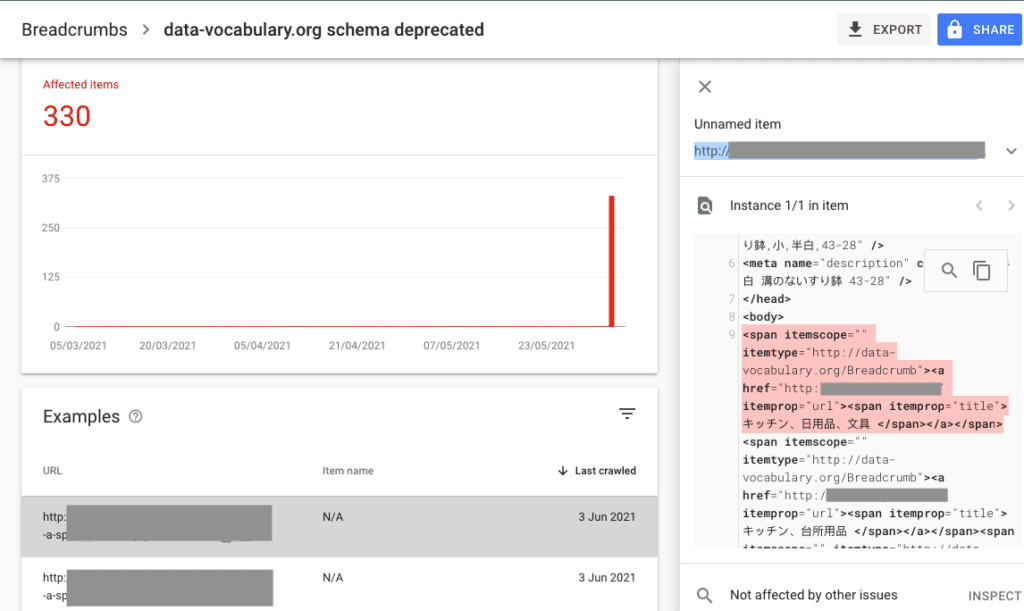
- Check the number of search results to see if the number tallies with how many pages are actually on your website. The Japanese keyword attack adds many pages to your website, sometimes in the hundreds of thousands. If your website has around 40 results on a normal day, 800,000 results on another is the result of a hack.
- Check the users on your website’s Google Search Console. If you find any odd users whom you don’t recognise, then also check your sitemap. There might be a different one to what you added for your website. The new one, if added by an unauthorised user, will certainly contain spam pages.
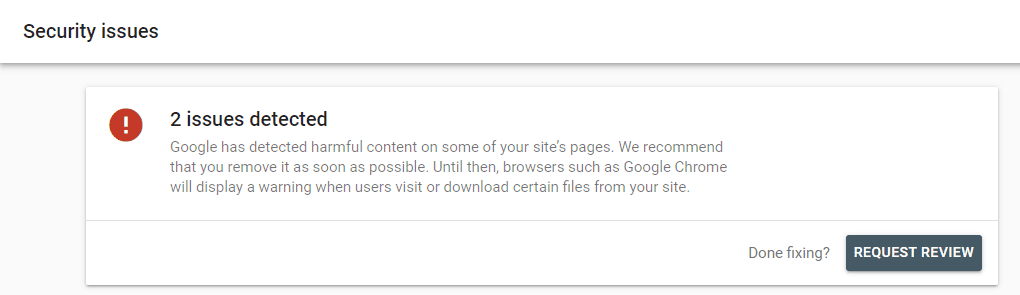
- Check the Security Issues tab on Search Console to see if Google’s scanners have flagged suspicious or deceptive content while crawling your website.
- There may be more than one .htaccess file that is the cause of the redirects, if your visitors are experiencing them. Your website should only have one .htaccess file.
- Use the URL inspection tool to check for cloaked content, in case one of the spam pages generates a 404 error. Using this tool, you can see if the page is genuinely unavailable, or is using cloaking to show googlebot a different version of the page. Cloaking is considered a deceptive practice by Google, so this will eventually cost you your SEO ranking and organic traffic.
As we’ve said before, hackers do a lot to make sure that website admin don’t find malware for as long as possible. The Japanese keyword hack is no exception, even though it has very visible symptoms. In its case, the malware spreads to almost every part of the website, and is a stubborn infection to remove. This way, the hackers can ensure that an inexperienced website admin is stuck with the malware for a while.
How to fix the Japanese keyword hack in WordPress
Once you have confirmed that your WordPress website has been hacked, the next critical step is to remove it as fast as possible. Malware causes exponentially worse damage the longer it remains on a website.
There are 3 ways to remove the Japanese keyword hack on your WordPress site:
- Use a security plugin to clean the hack
- Hire a WordPress security expert
- Clean the hack manually
1. [RECOMMENDED] Use MalCare to remove the Japanese keyword hack
The quickest and most effective way to remove any malware from your website is to use MalCare. It is a best-in-class security plugin for WordPress websites, and will make short work of any malicious code on your website.
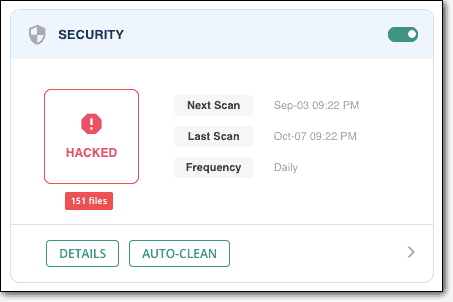
MalCare uses an intelligent system to detect and remove malware, making sure to keep your website intact. The plugin works quickly through the core files, plugin and theme files and folders, and the website database. Best of all, you don’t have to wait for more than 5 minutes to get your website malware-free.
All you need to do is:
- Install MalCare on your WordPress website, and activate the plugin
- Wait for your site to sync with our servers. This includes the first scan.
- Once the scan results are displayed, clean on auto-clean to remove the malware completely.
That’s all there is to it. In a matter of minutes, your WordPress website is absolutely clean, and you can go about reverting the damage that was caused by the hack. If you used MalCare to scan your website, then all you need to do is upgrade to clean. Your website is protected for a year, and you have access to top WordPress security experts to help with any issues you may face with your website.
Why choose MalCare?
- Removes only malware from your website, so your data and the good code is completely untouched
- Removes backdoors so that your website won’t get hacked again. Backdoors allow hackers to reinfect websites almost immediately after malware is removed. Many cleaning services fail in this respect, and the costs of malware removal skyrocket with repeated infections.
- Detects vulnerabilities in plugins and themes that can be exploited by hackers
- Has an integrated firewall to protect your website from common WordPress exploits like SQL injections, XSS attacks, and remote code injections. It will also block bad bots from a country or device visiting your site
MalCare protects over 100,000 websites with the firewall and learns from the attacks that occur on all of these websites. So not only is your website protected from attacks that it experiences directly, but also from attacks that it may experience in the future.
2. Get a malware removal service to clean your website
The next best option to using a security plugin to clean your website is to get a malware removal service to do it.
Sometimes, it is not possible to install a plugin on your website. Your web host may have suspended your site, or your site may be redirecting, so it is impossible to access your wp-admin. In these cases, expert help is often a good solution.
At MalCare, we do have an emergency malware removal service for these situations. Security experts will guide you through the process of regaining access to your website with your web host, and removing malware.
You can also contact a security expert outside of MalCare to get the malware removed. However, please keep in mind that they will assign you a slot based on their availability, so you may have to wait a few days before you get a resolution. Additionally, malware removal services are expensive because they charge per cleanup. Since they do not guarantee against reinfection, these costs can rapidly become prohibitive.
3. How to remove the Japanese keyword hack manually in WordPress
It is theoretically possible to remove any malware manually from a WordPress website, but that doesn’t mean it is at all advisable.
Admin who have tried to clean their website manually have either seen the hack reappear almost immediately because not all the malware was removed, or their website has broken because they deleted good code accidentally. In all cases, it has been a frustrating experience with small chances of success.
Therefore, after seeing hundreds of websites in bad shape, we strongly advise against manual malware removal.
Steps to remove the Japanese keyword hack from your website
1. Regain access to your website
If the web host has suspended your account, this is the first order of business. Otherwise, you can skip to the next step. Ask your web host to whitelist your IP so you can access your website to clean it.
Also, the web host suspended your account based on data from their malware scanner. Ask them to share that information, and it could work as a starting point for the cleanup.
2. Backup your website
Take a full backup of your website before making any changes at all. A full backup includes the WordPress core files and folders, plugin and theme files and folders, and the website’s database. You can use cPanel’s File Manager and phpMyAdmin tools to download a backup, but we recommend a dedicated backup plugin instead. If your site is very large, you will have difficulty restoring the database via cPanel, so a backup plugin is your best option.
3. Download WordPress, and the plugins and themes from the repository
Make a list of plugins and themes that are installed on your website, along with their versions. This is important, because you will be using that code to detect malware in your website’s code. Same goes for WordPress. Ideally you should be using the latest versions of everything, but that is not always the case.
Note: If you have any nulled software on your website, this is the time to jettison it. Nulled software is a red carpet invitation for malware. Hackers break licenses of premium plugins and themes, and make them available for free downloads for a reason. That reason is malware. Remember, there is no such thing as a free lunch.
4. Reinstall WordPress
Certain WordPress core files and folders remain mostly unchanged on a website, so you can replace them right away: /wp-admin and /wp-includes
The next thing to do is check the following files for odd-looking code that isn’t present in the clean install you downloaded in the previous step: index.php, wp-config.php, wp-settings.php, wp-load.php, and .htaccess
Odd-looking code can be php scripts that seem out of place, or with weird content in them. There is no particular set of characters to identify malware visually, so we can’t get more specific. If your web host shared the list of hacked files with you from the first step, you can use those to figure out which code is malicious.
The /wp-uploads folder shouldn’t have any PHP files at all, so any that you see there can be deleted without thought.
While cleaning the code, if you aren’t 100% certain if it is bad or good, you can comment out the code if it is in a file, or change the file extension to something that is not executable. This way, you are rendering the potential malware useless, without deleting it. If it does turn out to be benign, you can revert your changes quickly.
5. Clean plugins and themes
The /wp-content folder will have all the plugin and theme files and folders. Similar to what you did with the WordPress installation, go through each of them thoroughly for suspicious code and files.
Be cautious here though, because not all differences are bad. Customisations you make to plugins and themes will show up as differences too, and those are parts of your website that you would want to retain intact. If customisations are not an issue, nor is the data related to the extension critical, the easier option would be to replace the entire plugin or theme.
6. Remove malware from the database
Now that the files are clean, you need to remove the malware from the database. In the case of the Japanese keyword hack, this is no mean task. The primary function of this malware is to fill up your website with spam pages. Check your wp_posts table for these pages, and if you are infected, you may see several hundred thousand pages to what you originally had.
Also, this malware occasionally exhibits redirect hack symptoms, which is a whole different ball game. Check out how to remove hacked redirect malware in our dedicated guide.
7. Check your root for suspicious files
All of the above—WordPress core, plugins, and themes—is usually found in the public_html folder. This is the root folder of your website, and may contain malicious standalone files as well. All unknown files are not necessarily bad, but it is worth checking out just in case.
8. Remove all backdoors
Backdoors are a subset of malware, which allow a hacker to regain access to your website even once the malware is removed. They work by circumventing the login page, hence the name.
Backdoors can be anywhere, just like malware. Some functions to look out for in the code are: eval, base64_decode, gzinflate, preg_replace, and str_rot13.
These functions enable external access to the website, but that doesn’t mean they are necessarily bad. They can be a part of a plugin’s code, but are rarely used legitimately.
9. Upload your cleaned files and database
Once the malware is cleaned from your files and database, you need to replace the infected code on your website with the cleaned copies you have.
You can use cPanel to do this. Use File Manager to delete the existing files, and upload the cleaned versions, and phpMyAdmin to do the same for the database. Before this step though, make sure you have a full backup of your website. If any of your cleaning has gone awry, a backup is the only thing that can save your website.
Large databases are difficult to restore via cPanel, so we recommend using SFTP. It is a slow process, but at least the transfer will be successful eventually.
10. Check the plugins and themes
You’ve uploaded the cleaned files and database, and the website is loading. This is a great sign. Now you need to go through each of the pages, and check if everything works the way it is supposed to. You can disable the entire plugin folder, and enable one at a time to make sure everything works smoothly. Same thing goes for the themes.
11. Repeat the malware removal process with subdomains and nested WordPress sites
Many websites can have an older WordPress website on the same server. This is often the case with a site redesign, a subdomain, or even an old staging site.
Malware can move between sites that are hosted on the same cPanel, and that includes nested WordPress websites. If you have one or more nested sites, you need to repeat steps 1 to 10 again with each of them, otherwise the malware will reinfect your website again in no time.
12. Scan your website again to confirm
This step is the proof of the pudding. Run your website through MalCare again to check if your website is clean of malware. If MalCare’s scanner gives you a clean bill of health, congratulations! Your website is Japanese keyword hack-free.
Once you’ve gotten rid of the malware, you’ve accomplished a great deal. You now need to think about damage control.
Post-cleanup checklist
The Japanese SEO spam is off your website. Because MalCare cleans out backdoors in addition to the actual malware, you’ve bought yourself a little time to remove the last remnants of the hack, and revert the damage caused.
There are a few things you need to do, and we’ve listed them here in order of priority.
- Remove unauthorised users from Google Search Console. Go into your Search Console, and you should be able to remove them easily. If there are unauthorised owners added, the removal process is a little more complicated. In addition to removing them from Search Console, you also need to get rid of the associated verification token from the website’s .htaccess file as well. Follow Google’s guide to removing an unwanted owner carefully to do this. The .htaccess file is a critical file, so it is wise to backup your website before making any changes to it.
- Delete WordPress cache to remove any cached copies of your site that may still contain the malware.
- Request Google to reindex your site and resubmit a cleaned sitemap. If your site’s search results are still showing Japanese characters after the malware removal, it is because Google hasn’t recrawled your website. Requesting reindexing will solve this issue, and submitting a clean sitemap will speed up the process.
- Removing Google’s blacklist from your site. In case your website was flagged as deceptive because of the Japanese keyword hack, you need to take steps to remove it. Although the process is similar to getting Google to reindex your site, you can read our dedicated guide for getting off the blacklist as well.
- If you had nulled plugins or themes before, get rid of them entirely
- Update everything: WordPress, plugins and themes. Updates address vulnerabilities, which are the biggest reasons websites get hacked
- Reach out to your site visitors to reassure them and to repair the damage the malware caused to your brand. Clear and transparent communication is the way to go, and will help you regain trust.
Detection and removal are two of the pillars of WordPress security, the third being prevention. Prevention is arguably the most important in the long-term because not having a hack at all is vastly better than having to deal with one. In the next few sections, we will look at how to prevent the Japanese keyword hack—or any other malware for that matter—from infecting your site again.
How to Prevent Japanese SEO Attack
Now that you have removed the Japanese keyword hack from your website, the major battle has been won. MalCare’s auto-clean removes malware and backdoors, so you don’t have to worry about the malware recurring quickly. The important thing to do now is plug any loopholes in your website security, and revert the damage caused by the malware.
Here are a few things you can do to protect your website from hackers:
- Install a WP security plugin, which has daily scans, automatically cleans malware, and has a firewall to protect your website from exploits
- Change all the passwords, including user passwords, database and SFTP passwords
- Force reset all the user accounts
- Review plugins and themes, and remove ones that aren’t in active use
- Implement SSL
- Invest in regular backups, as they can be a lifesaver when things go sideways
WordPress security is an ongoing process, rather than a one-time activity. A good strategy is to have a plan in place to review things like users, activity logs, passwords on a regular basis.
How your website got hacked
There are 3 major reasons how a site can be vulnerable to hackers and their malware. Often site admin start questioning whether it is WordPress that is vulnerable or if they made a good decision by choosing their web host. More often than not, the security flaws are with the website itself.
- Vulnerabilities in out-of-date plugins and themes: When vulnerabilities are discovered, software developers release a security patch as an update. It is often a pain to update plugins and themes, so many people avoid it for as long as possible, but that causes a lapse in website security.
- Nulled software is a no-no: We cannot stress this enough: nulled plugins and themes are riddled with malware that’s why you can get premium software for free. Apart from this, nulled software doesn’t get updates, and you cannot receive support from the developers. If you are keen to get a good deal, look out for lifetime licenses instead.
- Poor passwords: If you don’t have strong passwords for your website, no amount of security is going to keep hackers out. Don’t reuse passwords across different accounts, make sure to enforce strong password policies, and update them regularly. Use a password manager to circumvent the issue of remembering complex passwords.
- Brute force attacks: One of the most common ways for hackers to gain entry into your website is through brute forcing your login page. If you have strong passwords, the likelihood of them succeeding is considerably less, but nevertheless you can do more to protect your website, like install two-factor authentication, limit login attempts, and use reCAPTCHA.
WordPress is rarely at fault for your website security, although it gets a lot of flak. Because of its immense popularity, WordPress has become a target for hackers. This is obviously a bad thing, but conversely, because of this very reason, it has solved a number of the security issues that still plague other CMS.
Similarly, your web host can be the cause of malware entering your website, but it is unlikely. Web hosts have network and server-level firewalls because malware on your site is very damaging for them. Therefore they take a great of precaution against infection.
Why your website got hacked
You may be wondering why your website was targeted by hackers. Perhaps, it is a hobby site or a blog, and doesn’t store user data. But that doesn’t mean your website doesn’t have value. There are many reasons why hackers target websites with the Japanese keyword hack:
- They want to improve the SEO of their websites, by filling your website with backlinks
- Hackers can place advertisements and redirects on your website to promote their unsavoury websites
- They can use your website to hack into other websites
There are many more reasons to hack into websites, but these are typically the cases we have seen specific to the Japanese keyword malware.
Impact of the Japanese keyword malware on WordPress sites
Malware on your site is always damaging, but the Japanese keyword hack brings its own particular brand of damage to the table.
If your site is infected with this malware, and the search results are flooded with irrelevant Japanese keywords, then you can rest assured that there will be several negative impacts on your visitors.
- Japanese characters in your site’s search results. This is the most obvious symptom of the hack, and can be shocking to encounter. Also, if you click through from a result, you may see your normal website, or a 404 error. This will tank your SEO, and all the effort you have put into it thus far.
- Many spam pages will be added to the website, sometimes in the hundreds of thousands. Again, this is something that you can see in the search results, or in your wp_posts table in the website database. Apart from SEO consequences and Google blacklist, this additional bloat will add to your server costs.
- Hackers often will add themselves to Google Search Console account to manipulate geotargeting and sitemaps results. You will receive an email notification that someone has verified themselves as an owner on your site’s Google Search Console. Imagine letting an unscrupulous hacker have access to the central dashboard for your site’s search performance.
- Redirects to another site from the spam pages, you lose visitors to spammy, shady sites. They will lose trust in your site and brand, and gain fear about visiting an unsafe site.
Malware is designed to be inconsistent, so there are chances that you see only a few of the issues we’ve listed, but not all of them. While it is true that coding errors can cause these symptoms, it is rather unlikely. In any case, it is always best to play it safe, and figure out if your website has an infection or not.
That’s a wrap
We hope that you found this Japanese keyword hack removal guide helpful and easy to follow. If you have any questions, reach out to us because we are here to help!
FAQ
How to fix a Japanese keyword hack?
To fix a Japanese keyword attack, you need to first remove malware from your website and then index your website with Google. We have a handy Japanese keyword hack fix guide that’ll help you with the process.
How did a Japanese SEO hack occur on my website?
The Japanese SEO attack occurred due to a vulnerability present on your website. Common vulnerabilities are outdated plugins, themes, and weak usernames and passwords. We have compiled a handy guide on how to make your WordPress website secure.
Why is my WordPress security plugin saying there is no Japanese keyword spam?
Your WordPress security plugin is saying that there is no Japanese keyword spam because this type of hack is difficult to find. Hackers are clever. They know what tactics security plugins use (like signature matching) to detect malware. They develop methods to hide malware in plain sight which is why security plugins with outdated techniques fail to find difficult hacks like the Japanese keyword attack.
What is a Japanese keyword hack?
The Japanese keyword hack or Japanese SEO spam is an SEO malware that infects WordPress sites with spammy Japanese pages. When the pages are indexed by Google, your site’s search results are manipulated. So your website starts ranking for Japanese keywords, and your site loses its organic SEO.
What does the WordPress Japanese hack do?
In a WordPress Japanese hack, pages on your website are injected with spammy Japanese words. When your website shows up on Google, users can see spammy keywords and are unlikely to visit your website. Learn more on how the hack work.
Share it:
You may also like
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…

MalCare Proactively Defends Against Icegram Express SQL Injection Vulnerability
MalCare’s recent data has revealed numerous attempts to exploit a newly found SQL injection vulnerability in the Icegram Express plugin. Attackers commonly use this sophisticated SQL injection technique to extract…

Atomic Security’s Deep WordPress Integration Helps Protect Against Core XSS Vulnerability
The recent WordPress core vulnerability is a critical one, primarily because of two reasons. Firstly, it affects the WordPress core itself, which means that every WordPress site is vulnerable to…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








