WordPress Sending Spam Emails? Fix the Issue
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

Is your WordPress sending spam emails that are not from you? Are you worried that your visitors and customers are getting spammed? If you are facing these problems, your website has most likely been hacked.
The first thing you need to do is scan your website for malware.
You need to act fast because as we speak, your subscribers are getting WordPress spam emails that could put them in danger.
If this continues, your web host will blacklist emails, or even suspend your entire site because of the malware. Or your email provider will stop delivering emails, and you will get an error saying ‘MTA queue is too large’. All of these are severe consequences just because your website has malware on it.
In this article, we show you how to remove malware from your website, and do some serious damage control. We cannot emphasize this strongly enough: malware becomes worse the longer it remains on a website. That’s why we always advocate quick removal by experts.
TL;DR If your WordPress site sending out spam emails, scan your site for malware. Your customers are already being affected by spam emails, and you need to act fast. MalCare will scan your site and remove the malware in minutes. Once the malware is gone, you can start on damage control.
Email communication is one of the cornerstones of digital marketing because it is so effective. Building an email marketing list is not easy, especially since you have worked to get people to trust you and your communications by providing value.
So, when your email list starts receiving spam emails from you (or so it seems to them), this is a huge breach of trust. Spam emails compromise their security and data, and some may be affected seriously because of the emails. Not to mention that your email marketing efforts are torpedoed.
In this article, we are going to focus on removing malware that causes your WordPress website to send out spam emails without your knowledge. We will also talk a little about why your legitimate emails land in spam or junk email folders, and the problem of receiving spam emails from your website contact forms.
Why is your WordPress sending spam emails?
There may be a few reasons why your WordPress site is sending out spam emails. We can all agree that regardless of the reason though, it is still a terrible situation to be in. In this section, we talk about possible reasons, so that you can identify what you need to fix in order to move towards resolving the issue.
Malware on your website
The most common reason we see for WordPress websites sending out spam emails is that the website in question has been hacked. The malware is a malicious mailer script that can send out large volumes of emails to many addresses in a short span of time. It can do this by manipulating the email sending code on the website.
⚠️ If you have seen other odd behaviour on your site, then you should absolutely scan your site first to make sure that malware isn’t the problem. MalCare will scan your entire site, and find the smallest bit of malware on it. If your site gets a clean bill of health, then you should proceed with other mitigation efforts. Malware is the worst thing that can happen to your site.
WordPress has a core function wp_mail() that is used to manage WordPress emails. The function is limited in terms of features, so website admin often install a SMTP mail plugin for better flexibility and control over their emails.
The malware is then able to manipulate the script or the plugin functionality to send out spam emails, making it seem like the website is sending email. Often, in addition to the email content, hackers also provide email addresses to the malicious mailer. Their goal is to use your website IP to send out spam emails.
As a side note, vulnerable WordPress email plugins are not the only causes of hacks. Even though popular mail plugins like WP Mail SMTP and Easy WP SMTP have had vulnerabilities in the past, the fact is that the malware could have come from any plugin, or indeed theme. It just so happens that malware is designed to send out spam emails as well.
Compromised email account
When we talk about best practices to secure your website, your visitors, and your data, we always talk about the importance of strong passwords. As security experts, we have lost count of the number of times we have seen users pick passwords like ‘password’ or ‘pass123’ for critical accounts like logins and FTP credentials.
Poor passwords are extremely easy to crack. They are barely a defense against hackers, so hackers can gain access to user accounts in literally a matter of seconds.
One of your email accounts may be compromised, and that’s why your users are getting WordPress spam emails. If this is the case, the solution is to go into the account and reset the password to a stronger one.
We’ll talk more about password security and better policies in a later section.
Step 1. Detect that my WordPress is hacked and sending spam emails
Hackers want to exploit your website for as long as possible, so they want the malware to go undetected as long as possible. Therefore you may or may not see symptoms of malware on your website. There are, however, definitive ways to check for malware present on your website.
Scan your website for malware
The quickest and most effective way to discover if your website has malware is to use a deep scanner. A deep scanner checks every file and folder and scans every bit of your website’s database in order to find malware.
Deep scan your website with MalCare’s free scanner

All you need to do is install MalCare on your website, and wait a few minutes for a definitive result. The scan results will tell you if your website is hacked and how many files are affected.
Other ways to scan your website
There are two other ways to scan your website for malware: using an online scanner or scanning your website manually.
We recommend using the online scanner only as a first-level diagnostic for malware infections. It cannot give you a definitive result, because an online scanner can only scan the parts of the website that are visible to it. WordPress core files and other critical files, which often have egregious malware in them, will not be scanned at all.
Online scanning is only partially effective in our opinion, but still orders of magnitude better than trying to scan your website manually. Apart from the immense time that it requires to perform such a daunting task, there is also the very real possibility of missing malware. You can use results from an online scanner to check listed files, but again, it is not a complete scan.
As WordPress security experts, we also use tools to scan for malware during manual cleanups for customers. The risk to a website from a protracted malware infection is too great, and it is our endeavor to always ensure our customers get support quickly.
Alternative diagnostics to detect malware on your website
In our experience, not all security scanners are built the same. Each has its own ways of detecting malware, and some are less effective than others.
If you have used WordFence or Sucuri to scan your website, you may be looking for other ways to confirm if you really have malware on your website. WordFence is known for excessive alerts and false positives on many occasions, whereas Sucuri often fails to detect malware altogether. iThemes has been known to lock out admin from their own websites.
All in all, it is handy to know a few tips for checking malware on your website, if you rely on any of these plugins.
- Check your website by logging in from an incognito browser
- If you have a fair idea of the number of pages on your website, Google your website and check the search results. The number should roughly tally with the number you know. If there are many more than you expect, that’s a sign of a hack.
- It is good practice to check activity logs for user activity that is out of the ordinary, in case a hacker has gained unauthorised access to an admin account
- Check your Google Analytics data for unexpected or unexplained traffic trends
- You will also see warnings in Google Search Console when your website is hacked
- Review your installed plugins and themes for updates. Maybe one of the outdated versions has a recently discovered vulnerability
- Do you have nulled software installed on your website? There’s your culprit then.
The easiest way to check for malware on your website is to use MalCare’s free scanner. Save yourself a ton of time and hassle, and install it now.
Step 2. Fix hacked WordPress sending spam emails
Once you have gotten a definitive answer regarding the presence of malware on your website, you need to get rid of it. Spam email sent from your website—bad as it is—is only the tip of the iceberg. Much worse will come if the malware is left as is.
There are 3 ways to clean malware from your website:
- Use a security plugin [RECOMMENDED]
- Hire a security expert
- Do it yourself manually
We want to reiterate how important it is to move quickly. Your website is still hacked at this point and sending emails to your users and customers.
Option 1: Use a security plugin [RECOMMENDED]
We strongly recommend you install MalCare, and use the auto-clean feature to remove malware in minutes. It is widely known to be a best-in-class security plugin that scans, cleans and protects your website.
Once you’ve installed MalCare and synced your website for the free scan, all you need to do is upgrade to clean your website in minutes. You can do this directly from your MalCare dashboard, without having to configure anything on your website.
It is a simple process:
- Install MalCare on your website, and wait for it to sync
- The plugin will then scan your website to detect malware
- Auto-clean when prompted to do so
That’s it! MalCare was built to be extremely user-friendly and easy to use. It surgically removes malware, while leaving your website entirely intact and as good as new. Apart from the speed of malware removal, you don’t lose any of your data either.
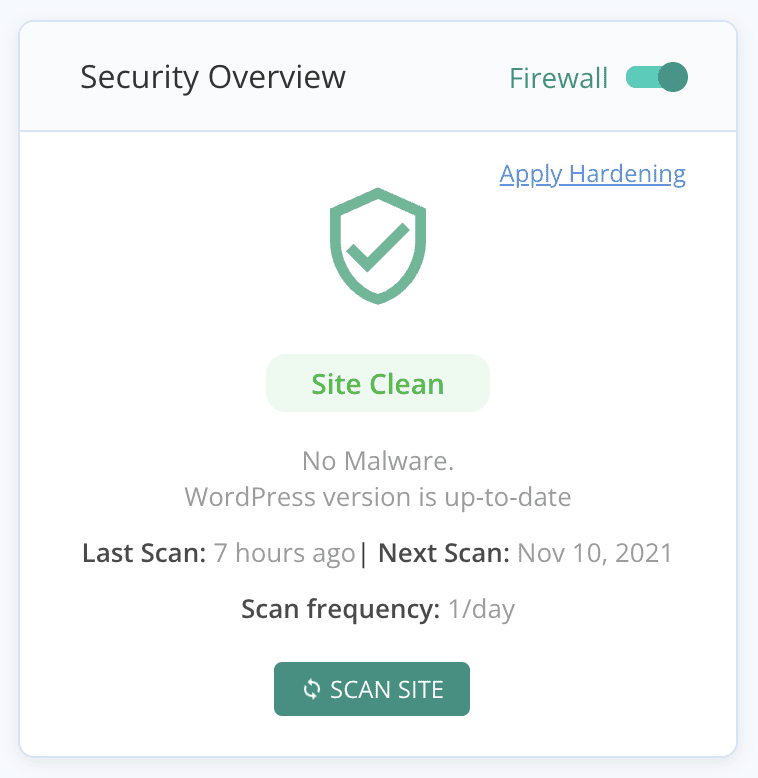
If auto-clean isn’t able to get rid of the malware safely, you can always reach out to support. Every MalCare subscription comes with unlimited cleanups and the guarantee of a malware-free website. You will have a year’s protection for your website, with daily scans, an intelligent firewall, and a powerful dashboard to manage all your websites in one place.
How to install MalCare if you don’t have access to your website
If your web host has suspended your website, you can’t access your website to install MalCare. Head over to our customer support, and they will walk you through the exact steps you need to take to get your web host to whitelist IPs for cleaning.
If all else fails, we can clean your website manually too.
Option 2: Hire a security expert
There are several malware removal services available for sites that are unreachable. MalCare also provides an emergency cleanup service, but we strongly advocate installing the plugin instead.
We cannot comment on other cleanup services and presume them to be reasonably adept at cleaning malware. However, the laborious nature of the service, together with the great expertise required, means that the costs are usually exorbitant. Very few will offer a guarantee against your site getting reinfected, so tread carefully if you choose to go this route.
Option 3: Clean hacked WordPress sending spam emails manually
Let’s face it: you wouldn’t be reading this section if you were a WordPress expert. But that’s what you need to be able to pull off manual cleaning successfully.
At MalCare, we have cleaned hundreds and thousands of websites in the last so many years. All that expertise has gone into building the product, and that’s why we so strongly advise against manual malware removal.
Quite apart from expertise, manual cleaning is a time-consuming process. And we know we keep saying this, but it is really that critical: malware does more damage the longer it is left on the website.
Things you should know before attempting a manual cleanup of your site
- WordPress file and database structure; core, plugins, and themes
- Hands-on ability with php, JavaScript, and SQL
- How to navigate cPanel, FTP, File Manager and phpMyAdmin
These prerequisites are the bare minimum needed to clean a website. Ideally, you should also know code logic, so you can evaluate what scripts do. This will enable you to differentiate between good and bad code.
Step-by-step instructions to cleaning your website manually
- If your web host has suspended your website, you need to regain access to it. For this, you need to contact your web host, and request them to whitelist your IPs for cleaning. Some hosts, like Bluehost, will not do it. In which case you will need to do without. The steps below will still work.
- Get scan results with the list of hacked files. You will get this either from your web host (if they alerted you to the hack), from Google Search Console, or from online scanners. The list of hacked files is an excellent starting point, but it isn’t the whole picture. Online scanners are unable to deep scan websites, so there may be malware in places other than those indicated.
- Take a backup of your website without fail. Yes, your website has malware, but it is still functional at the moment. If manual cleaning breaks your website in any way, you can use this backup to revert to a working website without too much hassle. This is one of the main reasons why we advise against manual cleaning.
- Go to the WordPress repository and get fresh installs of WordPress and all your plugins and themes. You will be using these to replace parts of your website code, and in some cases to compare code with your website. Firstly, remember to get the versions that were installed on your website. You may have to look through the archived versions in the repository to find the right versions. Secondly, when comparing the code between the hacked website and the clean installs, keep in mind that customisations may show up as additional code. This is not malware, obviously, so be mindful of deleting anything that looks different.
- Look for fake plugins and remove those altogether. Now that you have a list of plugins and themes, which you used to download clean installs from the repository, you can cross-check if any aren’t on that list.
Fake plugins have a few telltale giveaways: they obviously won’t be on the repository; they will have a single or two files at the very most; the names will be very odd, like wp-zzz for instance. - Get rid of nulled themes and plugins. This is a non-negotiable part of your website security. Nulled themes and plugins are pirated, as their licenses are cracked. Nulled software is not only unethical as a result, but full of malware and backdoors. If you have nulled software installed on your website, this was the genesis of the hack.
- Replace the WordPress installation. There are some WordPress core folders and files that don’t contain user data or changes. These you can replace with impunity, and it will save you from checking them for malware.
To replace the core files, log into cPanel to access your website files. Remove the following folders, and replace them with the clean versions:
/wp-admin
/wp-includes
Next, check the /wp-uploads folder. It shouldn’t have any PHP files at all. Delete any scripts that you find there.
Finally, check core files. These, you cannot replace en masse, because they contain configuration data for your website. Be very careful with these files, because if something goes awry with the index.php or the .htaccess files for instance, your website will not load at all.
index.php
wp-config.php
wp-settings.php
wp-load.php
.htaccess
Due to the nature of malware, we cannot be more specific about what to look for here. Each hack can be vastly different from another. - Remove malware from plugin and theme folders. As you checked the core WordPress files for unusual code, you need to do the same for plugins and themes. We mentioned this before, but it is worth reiterating: the fresh installs will not have custom code that was added to your website later. Be wary of deleting anything without understanding clearly what it does. Also, seemingly innocent files like favicon .ico can be malware too. Tread carefully here. Malware is often found in the key theme files: header.php, footer.php, and functions.php, so that’s a good place to start.
- Clean the database of malware. This is a considerably large task, so it is wise to set aside several hours or days to tackle the database. The database has all your user data, content, posts, pages, images, and everything else that you have added to your website. Effectively, it is what makes your website yours. Please exercise great caution when deleting scripts from the database, unless you are absolutely certain it is malware. You can mostly restore a site without its plugins and themes, but not without the database.
- Once the malware is removed, you need to get rid of all backdoors. Backdoors are the entry points for malware, and can be anywhere on the website: files or database, or even both. Cleaning the malware was only getting rid of a single infection. To get rid of the cause, backdoors need to go too.
Typically, backdoors use one of the following functions:
eval
base64_decode
gzinflate
preg_replace
str_rot13
However, these functions have actual functionality too, like the XMLRPC function is not inherently bad, but can be used to gain unauthorised access. - Reupload cleaned files to your website, using cPanel. You will need File Manager to replace the files, and phpMyAdmin to replace the database. If your database is very large, then you may face an issue with this. In which case, switch to SFTP instead. Delete the existing files, and then paste your clean files.
- The last step in the cleaning process is to clear all caches. Caches are used to improve performance by storing older versions of your website. Therefore, cached versions will still have the malware you have just cleaned. In fact, if you are appealing a Google blacklist, review requests often fail because Google scans the cache and detects malware intact.
If you have gotten this far, then that’s a great achievement. We’ve seen so many sites broken beyond repair when admins have tried to clean the sites themselves. It is a thankless and fraught undertaking, because of the enormous risk involved.
Why pay for a security plugin when you can do it yourself for free?
The short version is that a security plugin is the only way to really get rid of the malware.
The long version is as follows:
- Manual cleanups leave behind malware because of human error
- A good security plugin will be able to detect even the most well-hidden malware and backdoors
- Manual scanning and cleaning of files and the database will take days at the very least; as compared to literal minutes
- There is a huge risk of breaking the website with manual cleaning
There is no contest here: the security plugin is the best way forward. Install MalCare and click once to auto-clean your website.
Even WordPress security experts use tools and coding skills to find and remove malware from websites. They also have the advantage of being involved in the ecosystem and are probably aware of the new trends in malware.
Step 3. Prevent WordPress from being hacked and sending out spam emails again
Congratulations! Your website is now clean, and you can set about doing damage control. However, before we get into that, we want to cover some of the measures that you should take to protect your website from being hacked again.
Install a security plugin with an integrated firewall
In the last 10 years, we have seen hacks mutate and become more and more fiendishly clever about hacking into websites. Security experts have had to keep up because the hacker only needs to be able to get through once, whereas security needs to be constantly updated to keep out attacks successfully.
A good security plugin for WordPress will scan your website daily to check for malware, backdoors, and vulnerabilities. It should have an integrated firewall to keep out bot attacks and prevent brute-force login attempts. And finally, it should have an easy way to clean the malware off the website quickly.
Update everything
In case your website had old versions of plugins and themes, or even WordPress, you need to update those as soon as possible. Developers release security patches in their updates, often to address vulnerabilities. For instance, WP Mail SMTP had an XSS vulnerability, and Easy WP SMTP had an admin reset vulnerability. Both of these were patched in subsequent versions, but all those who didn’t update the plugins suffered huge losses.
It can be tricky to update WordPress websites, because of how interconnected everything is. Updates have been known to break the UI or design, and sometimes even take the website offline. Therefore it is always best to test updates on a staging site first, after taking a backup.
Implement a user account policy
It is good practice to review user accounts every so often, especially with large sites. As people leave and join the website management team, their user accounts lie unused but with the same level of privileges as before. This is a security hazard because passwords are then not updated regularly, and those accounts can be compromised.
In a similar vein, require everyone to change their passwords regularly. Strong passwords prevent unauthorized access, but since they are difficult to remember, we recommend the use of password managers.
Step 4. Recover from your WordPress website sending spam emails
You’re almost at the finish line now. Your website is free of malware, and you’ve taken steps to ensure your website is not hacked again.
The next step to sorting out this spam email issue is to do damage control. Hopefully, you caught the spam email issue in time, and not too many people were affected. If not, the following steps are only a starting point. You may have bigger reparations to make to your user list.
- Contact your web host and email service provider: If they have blacklisted your website or your email provider, you need to take steps to get it sorted. It is always helpful to detail the steps you have taken to address the issue, clean the malware, and indicate steps you have taken to ensure it does not happen again, for good measure.
- Email your list with information about spam emails: Reach out to the affected people and reassure them. Ask them to change passwords and scan their devices for malware. Offer as much support as possible, and try helping resolve any problems they have faced as a result of the spam emails.
- Prep support team for incoming user queries: Give your team the tools required to field questions and address issues. It may or may not be required, but it is always good to be prepared.
Malware leaves a trail of destruction in its wake, as many people are affected with identity or data theft. That is why Google and web hosts take such a strong view of websites infected with malware.
A good rule of thumb is to be transparent in any and all communication. Stick to the facts, don’t make excuses, and you may be able to turn this disaster into something positive. People respond to honesty and integrity after all.
Other symptoms of malware on a website
Since you are experiencing spam emails being sent from your WordPress website, this is a pretty good indication of a hack. You may also see some of the following symptoms, which are directly related to WordPress spam email hacks:
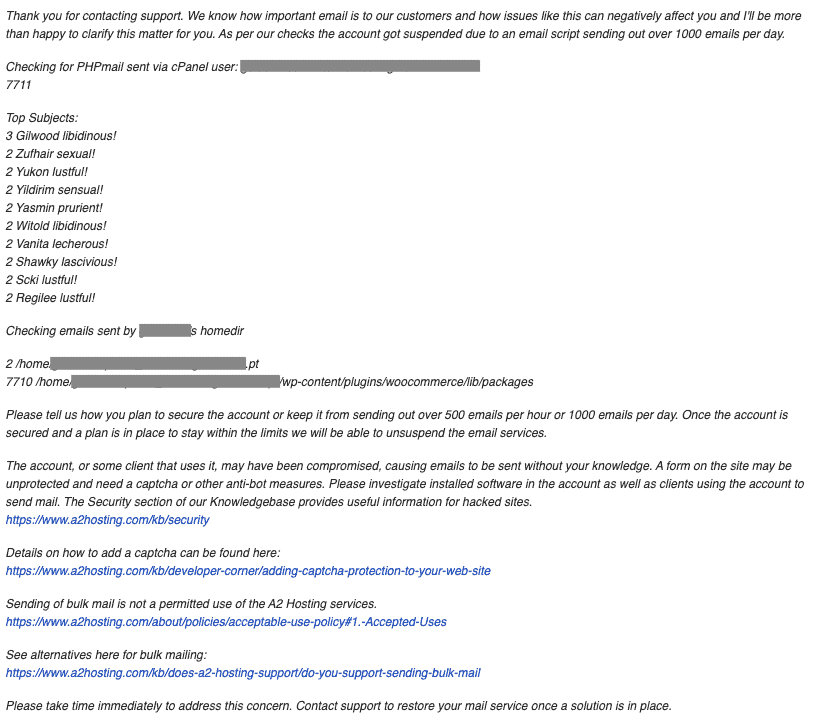
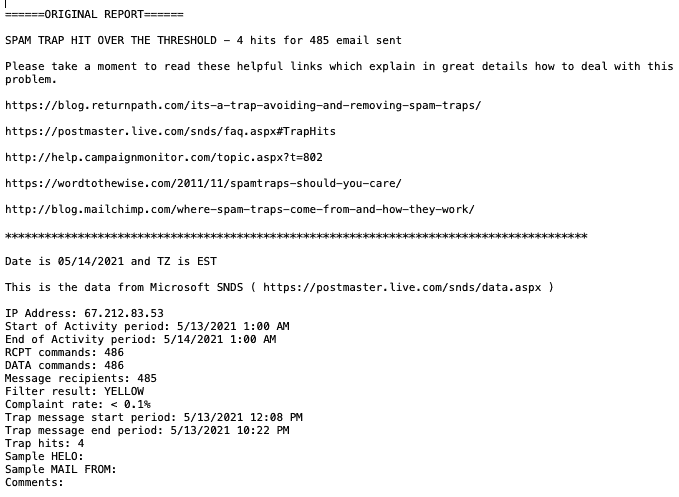
There is a solid chance that you see none of these symptoms at all. Perhaps you see other symptoms of malware; perhaps not. It is all down to the fickle nature of malware, and the insidious ways that hackers often employ.
What are the consequences of WordPress spam emails
In a word? The consequences of spam emails are bad. Here are some of the things we’ve seen happen to websites that have had this issue:
Things can get really bad, really fast. That’s one of the terrible things about having malware on your website. Please install a security plugin to protect your website, otherwise, you will always be at risk from hackers and their insidious malware.
Why are my emails landing in the spam folder?
Sometimes, we receive emails from customers whose emails are landing in the spam folders of their users. After scanning their websites, we have found that there is no malware so there is no need to fix WordPress. Plus the emails themselves are not phishing emails or other scams.
So why are emails landing up in user spam or junk email folders?
Turns out, spam filters also flag genuine emails for a variety of reasons. We have listed the most common reasons we have come across, but this list is not exhaustive by any means:
- Spammy practices while sending emails: There is a chance that you are sending emails that trigger spam filters. Certain keywords like ‘free’ or ‘now’ tend to trip filters. If the from info doesn’t match the return path, that can also cause emails to land in spam folders. We’ve also seen emails with different top-level domains also face this issue. You can check the spam score of your emails to figure out what the issue is.
- Incorrect DNS settings: Your email can get bounced between servers, depending on how email is configured. This can trigger a spam filter, because it can look like someone is using your domain to send out emails, a practice known as spoofing. The fix is to correctly configure DNS records to assure spam filters that the email is definitely coming from your domain.
- Server on a spam blacklist: There are chances that your email server is on a blacklist somewhere, because of previous missteps or perhaps because of someone else who is using the same server for emails. Maybe they hit a spam trap, and the server got blacklisted as a result. It is hard to say, but imperative to resolve. Figure out which blacklist your server is on, and request removal.
You can use any one of these free online tools in your browser and enter your IP address and check for blacklists:
If your site shows up on any blacklist, you will need to contact that particular online service and request for blacklist removal.
If none of the solutions above help, use this excellent troubleshooting guide to figure out the issue. In general though, always use good practices for your emails: opt-ins only, stay clear of spam keywords, and so on. Avoid purchased lists like the plague and scrub your list regularly, by keeping a hawk’s eye on engagement metrics and bounce rates.
How to stop receiving spam emails from my website?
Maybe the issue you are facing isn’t that your customers are receiving spam emails from your website, but you are. This is a completely unrelated problem, but we’re covering it because it involves spam emails as well.
Spam entries received from your website contact form are not caused by malware. Anyone can fill out an open contact form, and send you a spam email. There are however ways you can mitigate the issue:
- Add a captcha to an open contact form
- Install an anti-spam plugin to filter out contact form spam
The only caveat here is you need to make sure to keep an eye on the spam folder. Filters can sometimes flag legit queries, which could land in there by mistake.
Takeaways
WordPress sending spam emails to your customers will cause a lot of issues. Not only will customers lose trust in your business, but your web host and Google will soon follow. Losses can mount up very quickly as well because malware causes a lot of damage.
Apart from protecting your website from malware, also consider using a dedicated email service for large volumes of emails. The email service provider will take on the responsibility of delivery, and help with other critical configurations, like the DNS. In the long run, it works out better to safeguard your users from errant WordPress spam emails.
If you have any questions or comments, please drop us a line! We love hearing from you and are happy to chat about WordPress security.
FAQs
Why are my WordPress emails going to spam?
If spam emails are going to your users from your website that points to a hack. Malware can use email sending scripts in WordPress to send out spam emails in hundreds and thousands to unsuspecting users. There are many bad consequences of spam emails for you, the website owner. Your email service provider can blacklist your email, your customers could get hacked or scammed, and your website could be suspended.
How do I fix a WordPress spam email problem?
To fix your WordPress site from sending spam emails, you need to remove the malware that is causing the problem. Malware is very difficult to remove from WordPress websites, so you need a security plugin to clean it effectively.
Share it:
You may also like

MalCare Ensures Unmatched Protection Against User Registration Privilege Escalation Vulnerability
Imagine discovering that your WordPress site, which should be secure and under strict control, has suddenly become accessible to unauthorized users who have the same administrative powers as you. This…

MalCare Ensures Proactive Protection Against WP-Members XSS Vulnerability
MalCare continues to protect its customer sites from all kinds of attacks, even the ones exploiting zero-day vulnerabilities. The recent stored cross-site scripting (XSS) vulnerability found in the WP-Members Membership…
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








