Revslider Exploit: How to Fix Revslider Vulnerability & Protect Your Website
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.
Do you use the RevSlider (Slider Revolution) plugin? Was this plugin added to your WordPress dashboard by your theme? Severe vulnerability found in this plugin can cause attacks on your WordPress site!
When a hacker takes control of your WordPress website, they carry out all sorts of malicious acts. They steal your customer’s data and payment information or sell drugs and illegal products on your site. They even redirect customers to their own malicious sites.
You would lose visitors and revenue. Your site adwords account will be suspended. Plus, Google will blacklist your website and your web host will suspend your account if they find malware present.
But you don’t have to worry about the RevSlider Exploit because there is a fix. You can make sure your website is safe from hackers if you follow this guide.
Today, we’ll discuss the WordPress RevSlider exploit in detail. We’ll show you what you can do to keep your site secure against hackers. You’ll also learn how to fix a hacked website.
TL;DR: If you have a hacked WordPress website due to the Revolution Slider plugin, install MalCare immediately. It will scan your website to find the hack or any malware present. Once MalCare identifies the hack, you can clean your site in under a few minutes.
[lwptoc skipHeadingLevel=”h1,h3,h4,h5,h6″]
What is Slider Revolution?
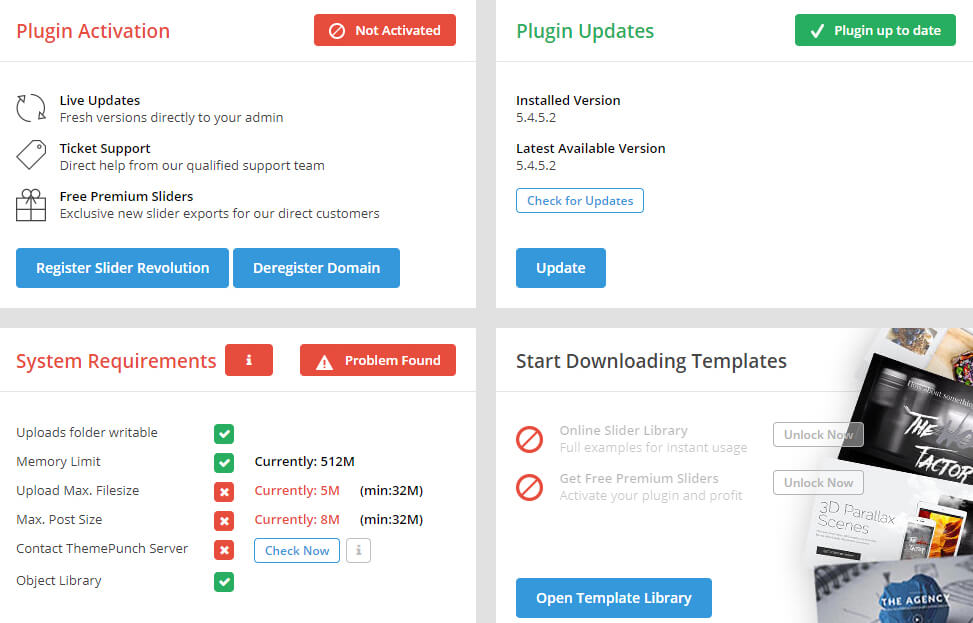
Slider Revolution, sometimes referred to as RevSlider, is a revolutionary WordPress plugin created by ThemePunch. It enables you to add sliders and carousels, hero headers, special effects, and content modules to your site.
It enables you to do all this without any coding experience. Building a simple gallery or a stunning responsive WordPress website is easy. Hence, 7 million users worldwide trust this plugin!
The RevSlider Exploit: What Happened?
RevSlider has seen three vulnerabilities develop over time including an XSS vulnerability (cross-site scripting) and a mass shell upload exploit. Here, we focus on the most severe vulnerability in the RevSlider plugin discovered back in 2014 – the WordPress SoakSoak Compromise.
So just how serious was the RevSlider Exploit? Hackers could gain full access to a website, exploit databases, and cause irreparable damage. They use the site to steal confidential data, defraud customers, sell illegal products, among a long list of malicious acts!
This vulnerability type (SoakSoak) is also known as Local File Inclusion (LFI). It allows remote arbitrary file downloads and arbitrary file uploads. This means, an attacker could access, review and download/upload a local file on the server.
To show you how remote attackers can download a file, we’ve illustrated an example.
If a website named example.com had the Slider Revolution installed (plugin versions 4.2 and below), a hacker could download the config file. They would do so using the following URL as a command:
http://example.com/wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php
This would show the hacker your wp-config file which contains your database credentials in plain text. This file doesn’t have any encryption so anyone can read it just as you’re reading this article.
In this way, the hacker could download any file from the website’s server remotely. They could also upload a php file and use this to exploit author privileges and gain admin access.
To avoid making the vulnerability public and allowing hackers to target millions of sites, ThemePunch patched the RevSlider Exploit silently. But this caused even more problems.
The RevSlider Exploit: Where did things go wrong?
After discovering the vulnerability, ThemePunch released a patch promptly but silently. There was no public announcement made based on guidance they received.
If you purchased the slider plugin from them, it has an auto-updater. So with the release of version 4.2 with the patch, your plugin would’ve automatically been updated without any intervention from you.
However, the plugin has over 7 million installs. Many WordPress themes offer it as a part of their packages. It is also available in marketplaces like CodeCanyon. If you have purchased this premium plugin from one of these marketplaces or if it has been embedded in one of your WordPress themes, then you would not have received the update. You also would have no notice that you need to update.
This is where things went wrong. The vulnerability was eventually made public and was being actively exploited. But many site owners didn’t receive any alert or notification about the Revslider Exploit.
If the RevSlider Exploit led to a hacked website, here’s how you can fix it.
How to Fix a Website Hacked through Slider Revolution Exploit
We explained earlier, that in a WordPress RevSlider attack, hackers are able to gain access to your server. They can view wp-config.php files which contain database credentials. They can also download arbitrary files and steal data from your website. Moreover, they can create fake admin accounts and install backdoors on your website.
Trying to fix a hacked site on your own would prove ineffective. Hackers intelligently disguise their malware or hide them from you. Not only is it difficult to spot, but the infection would also be widespread. Other than being free, we find that the manual method has no other benefits. If you do want to pursue it, you can check our guide on how to fix hacked WordPress site.
What we DO recommend is using a WordPress security plugin to clean your site. Today, we’ve selected the MalCare Security Plugin to show you how to get rid of a hack. Here’s why:
- It can find any kind of malware, whether it’s hidden or disguised. MalCare checks the behavior of the code and this helps it determine whether it’s malicious or not.
- MalCare carries out a deep scan of your WordPress site. This includes all files and databases.
- If malware is present, it will display a report on how many infected files were found.
- While other WordPress plugins may take hours or days to clean a site, MalCare has an option to Auto-Clean your website. It takes a few minutes.
How to Use the MalCare Security Plugin
Setting up MalCare on your WordPress site is easy and takes just a few simple steps:
Note: If you cannot access your WordPress site and cannot install the plugin, contact our team or use our emergency clean up services.
1. Install MalCare on your site.
2. Add your site to the dashboard.
3. Once done, the deep scan will automatically run. If you’re already a MalCare user, on the dashboard, access Security > Scan Site.
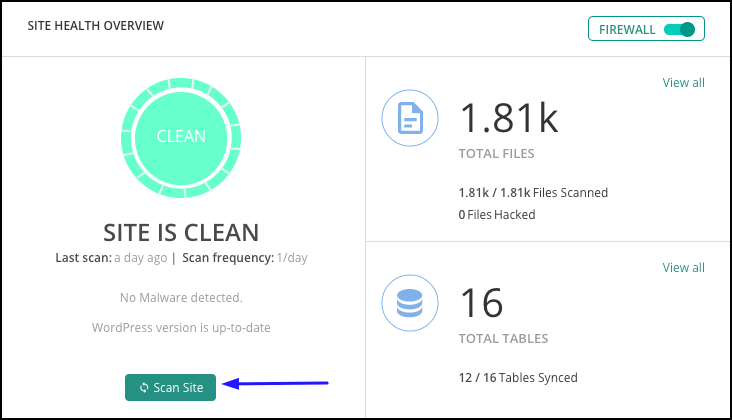
4. Once malware is found, you’ll see a prompt like so:
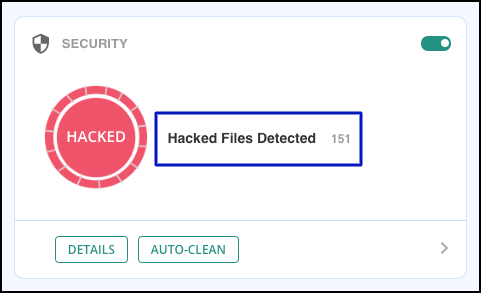
5. You can select ‘Auto-clean’ to start the cleaning process.
6. It will take a few minutes and you’ll receive a notification once it’s complete. We recommend visiting your website to see that everything is normal.
MalCare is also extremely handy if you need to manage multiple websites as you can add all of them to a single dashboard.
This kind of Local File Intrusion (LFI) attack compromises sensitive information such as your database credentials. So, we recommend a few more steps after cleaning your site.
After Care for RevSlider Exploit Attack
We suggest you take these steps to ensure your Slider Revolution responsive website is safe from future attacks:
- Update Slider Revolution plugin to the latest version.
- If you use a WordPress theme package that has Slider Revolution, contact your theme developers and ensure they update the plugin for you.
- Access your wp-config file and change your database password. You need to do this manually via cPanel or FTP.
- Check the list of WordPress plugins and themes you have installed on your site. Delete any that you don’t recognize or don’t use anymore. Also do scan your site themes and plugins regularly.
- Check user accounts on your WordPress dashboard. Delete any that you don’t recognize.
- Change passwords of all user accounts.
- Implement recommended WordPress hardening measures.
- Run regular penetration tests on your WordPress site. You can use Kali Linux for this.
Preventing an Exploit of RevSlider’s Vulnerabilities
If you use the RevSlider Plugin, to prevent your site from being exploited, you need to update your plugin immediately! Ensure your WordPress site is running the latest version of Slider Revolution.
If you do not see an option to update from your WordPress dashboard, you need to uninstall the vulnerable versions and reinstall the new version. Alternatively, contact the developers to get guidance on how to update the plugin.
If you are using a WordPress theme package, check to see if you have the Revolution Slider bundled in the package. Most WordPress theme packages have auto-updaters. Contact your theme’s support team if you need help updating.
We’re confident that your WordPress website has protection from any future hack attempts if you’ve taken the above measures.
Conclusion
The RevSlider Exploit caused thousands of attacks on WordPress websites. As the developers released a patch silently, many websites were blissfully unaware that their sites were vulnerable and being targeted.
Situations like this bring to light how important it is to take your own offensive security measures. With the MalCare security plugin installed on your site, you can rest assured that your site has protection against malicious activity. Its robust firewall and login page protection measures protects websites against brute force attacks, phishing hacks, etc. It will scan your website regularly and protect it at all times.
Category:
Share it:
You may also like
MalCare Free vs Premium: Differences Explained
MalCare is a new face in WordPress plugins for security, but is considered a strong contender alongside the biggest names like Wordfence and Sucuri. But, does it make sense to…

How to Check If Your Website Has Been Hacked
Did you receive a security alert for your website that made you wonder, “Is my website hacked?” Or are you just concerned because you noticed something off about it? Either…

Top 9 MainWP Alternatives: Manage Multiple Sites Easily
Managing multiple WordPress sites can be a daunting task. Keeping track of updates and security patches, and maintaining backups can quickly become overwhelming. This is where solutions like MainWP come…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








