How to Fix the Google Blacklist Warning from Your Website
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

Google blacklist is a colloquial term used to describe big red warnings visible when visiting websites. There are a few flavours, depending on various factors, but they all mean that there is something radically wrong with the security of the site.
If you or your visitors are seeing these warnings, scan your site for malware. Malware is the biggest reason Google places sites on its blacklist, and often the hardest to resolve.
It is important to take your next steps quickly because these warnings scare visitors away, and will result in a drop in traffic. Additionally, several browsers use Google Safe Browsing to protect their users from harm and can block a chunk of traffic from your website.
TL;DR: Remove the malware causing Google to flag your website. With MalCare, you can clean the malware from your website in minutes, and use our post-cleanup checklist to send Google a review request.
What is the Google blacklist?
Google wants to make sure that its visitors have a safe search experience. So their Safe Browsing initiative flags sites that have malicious content or spam links with a series of different browser warning messages: deceptive site ahead, phishing attack ahead, this site may harm your computer, site ahead contains malware, the site may be hacked, this website has been reported as unsafe, this page is trying to load scripts from unauthenticated sources, and so on.
🚨 Scan your site if you see any of these warnings. They invariably mean that your site has been hacked.
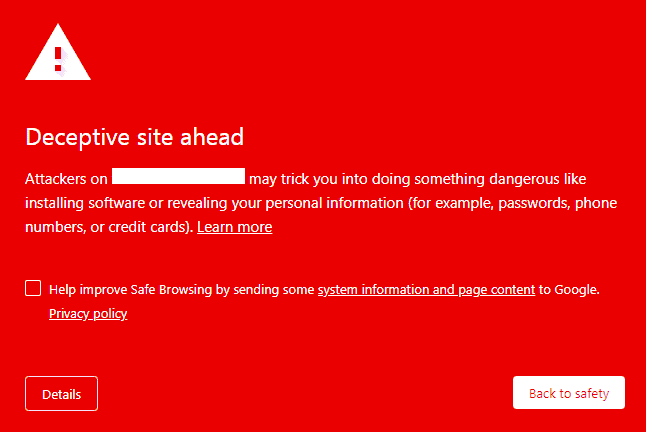
For this, Google flags several thousand websites every day that it deems unsafe to visit. These websites usually contain malware or deceptive content. When Google blacklists your website, visitors clicking through from search engines will see a big red notice, or a ‘Dangerous’ label in the URL bar.
But that’s not all, the Google blacklist will affect your WordPress site in more ways than just a big notice showing up on the screen. Once Google blacklists your website, it will also deindex it. This means that your website will stop showing up on the search pages of Google.
Consequently, as your website pages stop showing up in search results and any visitors are dissuaded from visiting your website, you will see a drastic drop in organic traffic. And since many antivirus solutions, web hosts, and browsers also refer to the Google blacklist, chances are that they will also flag your website or suspend your account.
In order to get your website off Google’s blacklist, there is a 5-step process:
- Scan your website to confirm the hack
- Clean the hacked files and malware from your website
- Complete the post-cleanup checklist
- [Bonus] Get rid of bad SEO
- Submit a review request to Google
Step 1. Check if your website is blacklisted by Google Safe Browsing
It is important to confirm whether your WordPress site is on the Google blacklist before you can fix it. In the best-case scenario—if there can be one—Google sends you an email, saying that your website has malware on it. They usually include helpful links to forums and articles, so that you can resolve the issue. But there are also other ways in which you can find out if your website is on the blacklist.
🚨 The quickest method is to scan your site. Use MalCare to find malware on your site in minutes, and confirmation that is indeed the culprit behind the warnings.
Deep scan your website for hacks
The first order of business is to figure out the extent of the malware on your website. A deep scan will check every file, folder, and line in your website database for malicious code that is causing a Google blacklist. It also checks for deceptive content, spam content and links, and vulnerabilities and backdoors.
Install MalCare, and in a matter of minutes, your website will be scanned completely. You will also get a report of how many files are affected by the hack.

Other diagnostics
Scanning your site is the only definitive way to know if your site is hacked. However there are other things you can check just as well:
- Use an incognito browser to visit your website.
- Google your website and check the results and number of pages indexed for an indicator of spam pages. Google may remove your website from their search results. Your website will no longer be indexed, so no one can find it without the address.
- Check activity logs for unusual user activity in case a hacker has managed to compromise one of your admin accounts.
- Analytics data might show odd spikes or troughs in traffic.
- Google Search Console warnings, under the Security Issues tab. It is a good idea to get familiar with Search Console at this point, because you will be filing a review request from here, later on. To do so, make sure that you have admin access.
- Out of date plugins and themes on your website might have vulnerabilities. You can check if any of your installed plugins or themes have recently discovered vulnerabilities.
- Nulled plugins and themes are a no-no. Nulled software is usually riddled with malware and backdoors.
- Antivirus programs will also block your website, or part of it from being displayed on people’s computers. If any of your customers complain of this, look into it with utmost concern.
- Finally, Google maintains an online directory for its blacklisted websites. You can check any website on the Google Transparency Report to find out if your website has been blacklisted by Google. It is a foolproof way to confirm whether you have been blacklisted.
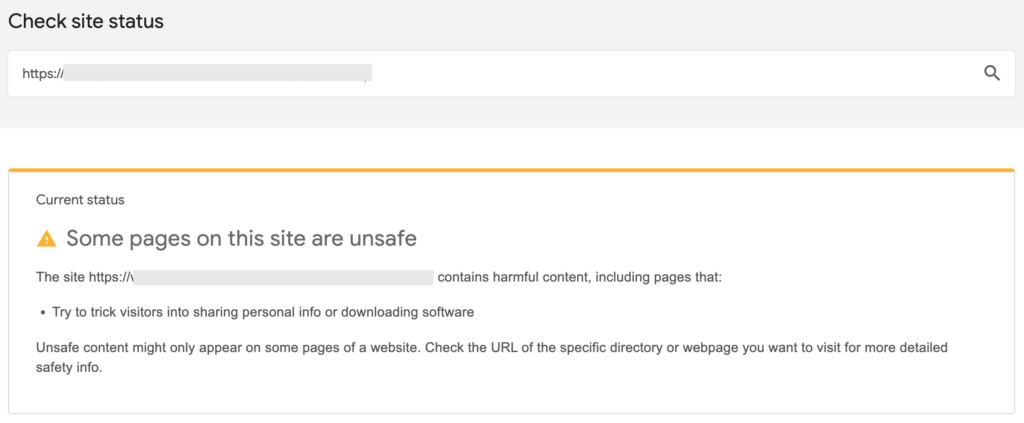
Pro tip: Check the date when Google discovered suspicious content. You can find the discovery dates next to the URLs provided in the ‘Detected Issues’ section. Google does not always provide a lot of information on the URL blacklist. Checking the dates can help you narrow things down even further. For instance, did you install a plugin right before that date?
Step 2. Remove malware from your site
Now that we have established that there is malware on your website, let’s talk about cleaning it up. We recommend removing malware by installing and using MalCare’s one-click auto-clean. There are 3 ways to clean your website of malware:
- Thorough cleanup with a security plugin [RECOMMENDED]
- Security expert services
- Manual cleanup
Option 1: Thorough cleanup with a security plugin [RECOMMENDED]
MalCare is a best-in-class security plugin that not only scans your website daily for hacked files and vulnerabilities, but also enables you to clean hacks instantly from your dashboard.
If you have installed MalCare for the free scan, all you need to do is upgrade to clean your website. If not, here are the steps:
- Install MalCare on your website
- Wait for the website to sync with MalCare servers
- Scan your website from the dashboard
- Auto-clean when prompted, and get rid of the malware
And that’s it! It really is that simple. MalCare checks every file and database table for hacks with a sophisticated algorithm. The algorithm doesn’t rely on simple file matching to check for hacks.
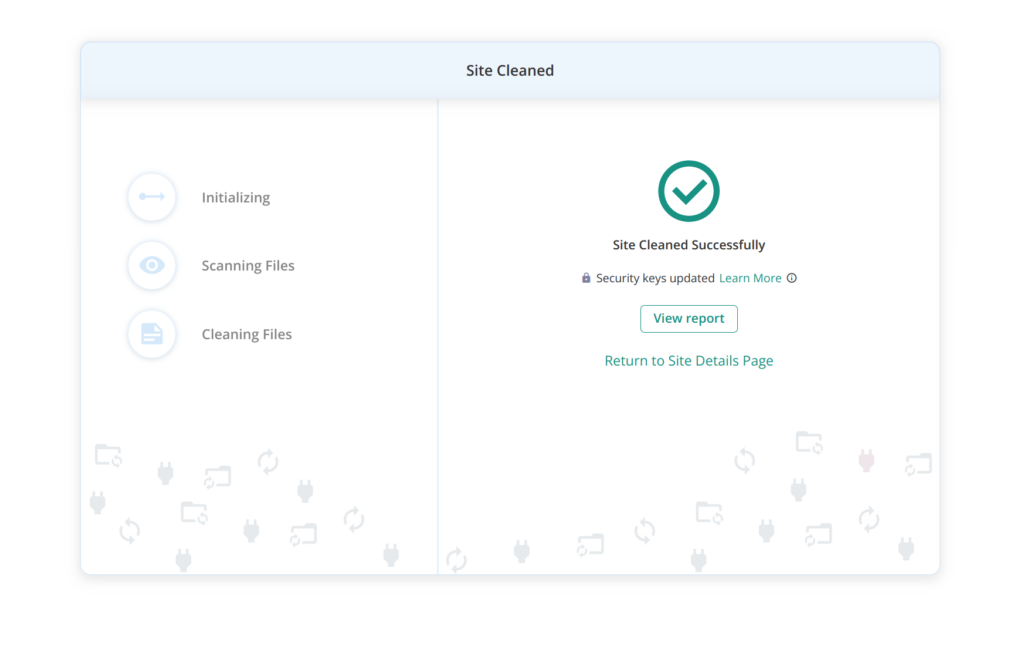
If the hack is not fully cleaned, you can request support to take over. MalCare support has a team of security engineers, and they will go through your website to find the hacked files. All of this is included in the same subscription.
On top of that, MalCare will protect your website with daily scans, an integrated firewall that defends your site against malicious traffic from countries or devices, and a powerful dashboard for ease of use.
How to install MalCare if your website has been suspended or is being redirected?
There are times you won’t be able to access your website because of a redirect hack or perhaps your web host has suspended your account.
This is a trickier situation, but it can still be resolved. Get in touch with us, and we will walk you through the steps to contacting your web hosting provider.
Option 2: Security expert services
There are hack removal cleanup services that will go through your website and get rid of the malware. MalCare also provides an emergency cleanup service, but we prefer to help you install the plugin instead.
Hack removal services are expensive, because they require manual expertise and take time. A security plugin is much better, and resolves the hack much faster. If you choose to go another route, we cannot speak to the efficiency of another hack removal service.
Option 3: Manual cleanup
At MalCare, we have cleaned thousands of websites. That is the expertise that goes into our security plugin, as a matter of fact. It is also why we don’t advise manual cleaning at all.
Even expert hack removal services use tools and programming knowledge to assist with manual cleaning. Going through each line of code is next to impossible, especially if it is an e-commerce site, or a large one with lots of posts and pages.
Apart from the time, there is always the risk of breaking the site altogether. If you choose to clean your website manually, please be warned that you are running that risk. Malware can vary significantly, so there is no tutorial that will fit your exact use case.
Now that we have got the warnings out of the way, let’s start with the cleaning process.
Prerequisites for cleaning your website manually
- Understand WordPress file and database structure
- Experience with coding, programming logic, and developer tools
- Familiarity with cPanel and other web host dashboard tools
Steps to cleaning your website manually
- Get access to your website, if it is suspended. Contact your web host, and ask them to whitelist your IP for cleaning.
- Get a list of hacked files from your web host, or from Google Search Console. This is a good starting point, although it will not take care of the vulnerabilities that allowed the hack in the first place, so avoid relying solely on this list.
- Backup your website immediately. A hacked site is bad, but it is still functioning. If the cleaning effort breaks your website, this backup will help you retrieve something that works at the very least.
- Download clean installs from the WordPress repository. This should include the WordPress installation and all plugins and themes. Remember to get the same versions that were on your website in the first place. You might have to look at archived versions to find those.
- Remove fake plugins from your website. Since you have a list of plugins and themes, you can see if there are any outliers on your website. Chances are these are fake plugins, which are essentially hacked files masquerading as plugins. They typically contain a single file or two at the most in their folders, and have weird names. Another way to check if a plugin is fake is to look for it in the repository.
- Delete nulled software. Nulled software are pirated premium plugins and themes, and will invariably have malware or backdoors hidden in the code. There is no such thing as a free lunch, remember, so hackers who are going to steal from developers are not altruistic Robin Hoods, but thieves. They will steal from you too.
- Reinstall WordPress, by deleting the old version and copying the files from the new install. WordPress core files have very little user data, and mostly have configuration information. Therefore replacing them will save you from having to comb through that code.
Log into cPanel or use SFTP to access the backend of your website. Delete the following folders, and copy the new versions entirely:
/wp-admin
/wp-includes
Next, look for strange codes like favicon_bdfk34.ico in these core files:
index.php
wp-config.php
wp-settings.php
wp-load.php
.htaccess
We cannot be more specific about what to look for, because malware can look very different from hack to hack. The easiest way to do this is to look for code that is not in the clean installs, and analyse what it does. However, just because it isn’t in the clean install doesn’t make it necessarily bad.
Finally, the /wp-uploads shouldn’t have any malicious PHP files at all. Delete any that you find in that folder.
- Repeat the clean up process for plugins and themes. There is an added layer of complexity here, because plugins and themes are usually customisable. That code is definitely not malicious, but it won’t be in the clean installs. The same goes for additional libraries that you may have installed.
A good place to start are the key theme files: header.php, footer.php, and functions.php - Clean malware from the database, which is much trickier than it sounds. The database contains, well, all your data. This means your content, user data, and everything else in between. Please be very cautious about deleting any information from here without being absolutely certain it is malware. You can lose a significant amount just by poking around in the database.
- Remove all backdoors now that you’ve removed the malware. Backdoors, exactly as the name suggests, are ways for hackers to gain unauthorised access to your website. The code can be hidden anywhere in your website. It is vital to remove backdoors and patch vulnerabilities, otherwise your website will most certainly get hacked again.
Look for functions like these:
eval
base64_decode
gzinflate
preg_replace
str_rot13
They aren’t necessarily backdoors because they can have legitimate uses. Also, hackers can obfuscate code to look like something else entirely, or find creative ways to disguise these functions. The general rule of thumb is to keep your eyes peeled for anything that looks awry in the code.
- Restore cleaned files to your website backend. Log into cPanel and use the File Manager to replace the files, and phpMyAdmin to replace the database. You will need to delete the existing files first, and then copy your clean files in their place. You can also use FTP or SFTP to manage your website restore. It is a more reliable process but can get tedious.
- Clear the WordPress and browser caches. Caches store older versions of your website to aid in performance. Therefore there will still be malware in cached files. Google often scans cached versions of websites, and detects the malware in those versions. This is often the reason why review requests are rejected.
Manual cleanups are difficult to perform thoroughly, especially on large websites. There is a big chance that something could go wrong, the site breaks and is then irretrievable. That’s why we also recommend you backup your working website, regardless of malware, as soon as possible.
Finally, even WordPress security experts use tools and coding skills to remove malware. Additionally, they are plugged into the ecosystem, and are aware of the new variants of malware that crop up. If you decide to avoid a plugin, a security expert is still a better choice than manually cleaning the website.
Step 3. Post-cleanup checklist
Malware removal plugins can zap the bad stuff off your site, sure. But they can’t undo everything the hackers did: like creating new user accounts for themselves or messing with your sitemaps. You’ll have to go in yourself after the cleanup and fix that kind of damage to get your site back to normal.
Also malware is really stubborn. It keeps coming back, sneaking in through backdoors or exploiting the same old vulnerabilities over and over again. It’s an endless game of whack-a-mole. That’s why we hook our customers up with this security checklist. Following those steps helps prevent those pesky hackers from waltzing right back into their WordPress sites after we’ve booted them out.
Install a good security plugin with an integrated firewall
Setting up a security plugin is a crucial step in protecting your WordPress site. These plugins are designed to scan, clean, and prevent hacks on your WordPress site. MalCare, in particular, excels at quickly diagnosing and resolving any malware issues. Additionally, it provides ongoing protection against future attacks through its advanced firewall.
One of the key advantages of MalCare is that, unlike some other security plugins, it does not compromise your website’s performance. Your site will continue to run smoothly and efficiently while being fully protected.
If you want to keep your WordPress site safe, secure, and operating at its best, utilizing a top-tier security plugin like MalCare is an absolute necessity.
Resubmit correct sitemaps
While this step is specific to malware that hijacks a site’s Google search results, it is well worth the extra effort. Hackers can add thousands of pages to your site to manipulate Google and exploit your SEO. To do this, they also submit sitemaps containing URLs of these illegitimate pages, effectively replacing your legitimate sitemap.
Since your site has landed on the Google blacklist, malicious sitemaps are considered during the review process for removal from this list. Therefore, it is important to check your sitemap on Google Search Console after a malware incident.
Review user accounts and passwords
Changing passwords and checking user accounts is very important after a security incident. One of the main reasons WordPress sites get hacked again is because of user accounts that were accessed or created by hackers. So, after fixing a security issue, you must change all passwords for users and the database.
In addition to changing passwords, you need to look at your user accounts. Delete any accounts that shouldn’t be there. For the accounts that need to stay, make sure they only have the lowest level of permissions needed for that account.
It’s also a good idea to remove any types of accounts that aren’t absolutely required. It’s becoming easier and easier for hackers to break in, with recent security holes letting them hack sites just by having a basic user or subscriber account.
Set up SSL on your site
Having SSL on your website is very important. It uses special encryption to protect all the information sent to and from your site, so no one else can see or steal it. For a while now, Google has been strongly encouraging all websites to use SSL. In fact, they will make your site rank lower in search results if it doesn’t have SSL set up.
Update your WordPress core, plugins and themes
Promptly updating your WordPress core, plugins, and themes as soon as new versions are released is a critical security measure. Updates often address critical vulnerabilities in plugins and themes. As soon as a vulnerability becomes public, hackers frantically attempt to exploit any websites that haven’t installed the necessary patch. Therefore, it’s crucial to ensure your WordPress site is updated before malicious actors can take advantage.
While updates can sometimes be inconvenient and potentially cause compatibility issues, leaving your site exposed to known security risks is simply not worth the risk. To stay on top of updates and maintain a well-functioning site, it’s essential to take regular backups and utilize a staging environment. Additionally, MalCare’s firewall prevents many vulnerabilities from being exploited before updates can be applied. Nevertheless, we highly recommend applying updates as soon as feasible to maintain optimal security.
Pick good plugins and themes
When choosing plugins and themes for your WordPress site, you need to be very careful about which ones you use. It’s best to stick to plugins and themes made by well-known, reputable developers.
There are two main reasons for this. First, reputable developers will help you if you ever have problems. They also regularly update their products to fix any security holes. These updates are really important for keeping your site safe.
Second, using nulled (illegally copied) plugins or themes may seem like a way to save money at first. But if your site gets hacked because of them, it will cost you a lot more in the long run. Nulled products are not only unethical, but they are also a major security risk because they often contain malware and backdoors for hackers.
💡 Pro tip: Apart from the website security angle, make sure to only use white hat SEO practices. It is just not worth the hassle if you don’t.
Step 4. Fix bad SEO practices
Black hat SEO is just a bad idea for your website and your business. Google takes a very serious view if your website has any of the hallmarks of bad SEO.
It is understandable that you want visitors to your website, and sometimes the sanctioned strategies take too long. However, trying to manipulate search engines is a short-term solution, with long-term consequences.
So if your website has any of the following workarounds, please remove them before requesting a review:
- Cloaking: Make sure that Google sees the same version of your website that a visitor sees
- Scraping: Don’t use bots to scrape data off other websites
- Keyword stuffing: Focus on building useful content, and then optimising with keywords
- Paid backlinks: You can approach other website admin to exchange backlinks if their content and yours are connected. You will also get better traffic as a result of doing this.
- Duplicate content: Develop your own content and delete any copied content
There are other SEO strategies that Google frowns upon. The rule of thumb is to provide value to visitors with your content, products and services, and avoid anything that is remotely deceptive.
Step 5. Request a review from Google
At this stage, you need to be 100% certain that your website is free of malware. Run a scan to double-check before proceeding to ask for a review. This is an important step because if Google finds any trace of malware on your website, it will reject the review request.
It is also worth pointing out here that Google reviews these requests manually. Therefore, if you have too many rejected requests, Google will flag you as a ‘Repeat Offender’. After that, you will need to cool your heels for 30 days before filing a new request.
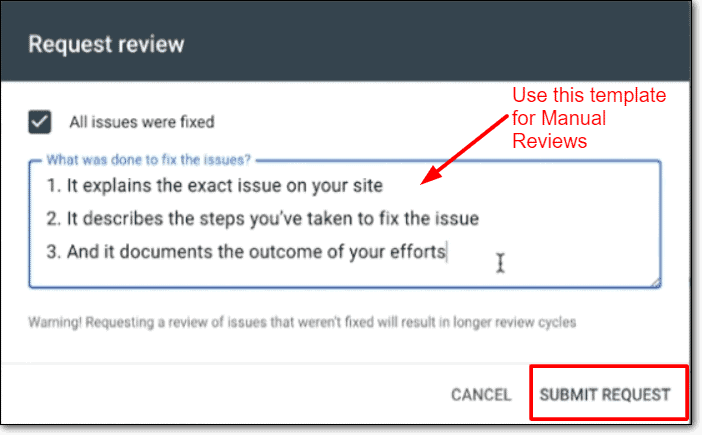
Google blacklist removal steps:
- Go to Google Search Console account
- Click on the Security Issues tab, and navigate to the bottom of the screen
- Hit the ‘Request a review’ button
- Use the form to indicate all the steps you took to resolve the security issues
- Submit
After submitting the form, be patient. Each request takes a few days to be resolved, but there is nothing you can do to hasten the process. In fact, if you do try and follow up too many times, that will also land you on the repeat offender list. So yes, be patient.
What if your site doesn’t have any malware and the review request is rejected?
There are a few cases where the review request is rejected by Google, saying that they still detect malware:
- The cache wasn’t cleaned: As a part of the post-cleanup checklist, please clean your WordPress and browser caches. If you don’t clear the website cache, Google will flag malware once again, and will not remove your website from the blacklist. You can then access some of the flagged pages, and if they return a 404, you know they don’t exist on your website.
- Old links as remnants: Check the scan results that Google shares with you, and see if any of the links still point to spam sites.
There is a chance that the malware wasn’t cleaned properly, especially if it was done manually. In this case, you will need to bite the bullet and get a security plugin to do the job. The manual cleanup wasn’t a success.
It is very unlikely that Google Safe Browsing shows false positives at all. So try resolving the issues as suggested above, and file another review request.
Why was your website blacklisted by Google?
As we explained before, when Google crawls your website and finds something bad, it adds your website to the blacklist. These “bad” things could be:
These are the most common reasons why Google would blacklist your website. For further reading, and to figure which action Google takes under which circumstances, check out their list of warnings.
Variations of the Google blacklist warning
There are various warnings that you can get based on why Google has blacklisted your website. Visitors clicking through from search engines will see a big red notice like the ones below, or a ‘Dangerous’ label in the URL bar.

Phishing attack ahead
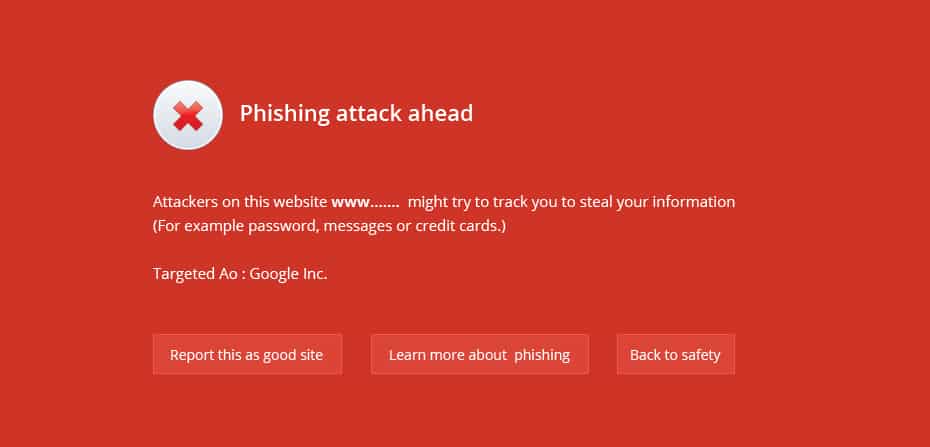
This site may harm your computer
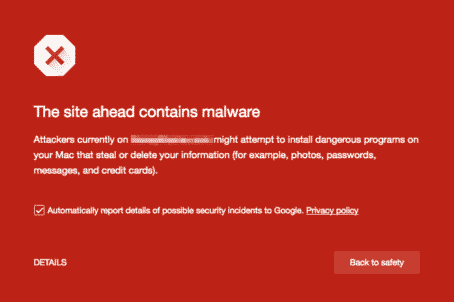
The site ahead contains malware
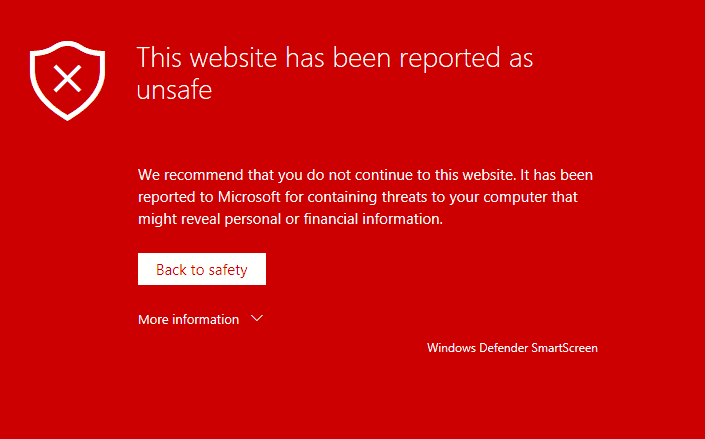
This website has been reported as unsafe
This page is trying to load scripts from unauthenticated sources
Government-backed attackers may be trying to steal your password
The site ahead contains harmful programs
How Google blacklists your website
Google periodically crawls your website in order to index it for their search results. This means that it reads the content on your website to understand what purpose it serves, and accordingly shows it to its search engine users. This is done through Googlebot, which crawls the websites on the internet to index them automatically.
Googlebot scans website code and checks it using an algorithm to see if it is malware. If the scan detects a malware, it immediately blacklists the site depending on the malware or deceptive content detected. Google also blacklists sites that violate their policies, like the use of black hat SEO.
To see if your website is on the blacklist, you can search for it on Transparency Report.
Why does Google Search Engine flag hacked websites
In all cases, malware on websites is caused by compromised website security, so it is not your fault. So you may be wondering why your website has been blacklisted by Google.
Google wants to protect its users from malware that can steal their identity or data, or infect their devices, therefore it blacklists any websites that use deceptive practices or contain malicious code. The types of hacks that Google flags are:
While the malware isn’t your fault, there are ways to protect your website. Therefore since the malware is on your website, it becomes your responsibility to deal with it.
What is the impact of Google blacklist on your website
The consequences of a hacked website range from bad to disastrous. There is obviously no good outcome, but some people are unaware of just how bad it can be. Here are a few of things that we have seen websites experience when they have been hacked:
- Suspended site by web host
- Loss of visitors and revenue
- Reduced site performance
- Legal issues
- Unhappy clients
- Data theft
All of the above also leads to financial losses, either directly with loss of revenue and cleaning costs, or indirectly through time and resources spent on damage control. All in all, it is a terrible situation to be in.
Takeaways
While there are many reasons why Google can blacklist your website, malware is the most serious and the hardest to recover from. You can give your website its best chance at security by installing a good plugin.
Have questions or comments? Drop us a line! We would love to hear from you.
FAQs
Why is my website showing as dangerous?
Your website is showing as dangerous because your website has been hacked. Your website has been blacklisted by Google, and now browsers are showing the dangerous warning in the URL bar to warn users from visiting a hacked website.
The best way to fix the problem is to install a security plugin on your website and clean the malware. After that, you need to request a review from Google to get your website removed from the Google blacklist.
How to fix the Google blacklist warning?
To fix the Google Blacklist warning, you need to address the issues that got Google to flag your website in the first place. Start with the email that they sent, and figure out the reasons for the URL blacklist. The biggest reason to land on the blacklist is the malware on your website.
Use a security plugin to clean the malware on your website. Then request Google for a review to remove site from Google blacklist warning.
Category:
Share it:
You may also like

MalCare Stands Strong Against WP Activity Log Premium SQL Injection Vulnerability
A significant SQL injection vulnerability was identified in the WP Activity Log Premium plugin, a popular tool for tracking user activity on WordPress sites. An SQLi vulnerability poses a serious…
Fix Pharma Hack on WordPress and SEO
Pharma hack is a prolific malware that redirects visitors from your site to an online pharmacy that sells Viagra, Cialis, Levitra, Xanax, Tadalafil, and other drugs. It also shows up…
How To Protect Your WordPress Website From File Upload Vulnerability?
One of the core strengths of WordPress lies in its file upload functionality. The ability to seamlessly upload and integrate various types of files, from images and documents to multimedia…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








