How To Protect Your WordPress Website From File Upload Vulnerability?
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.
Do you suspect that your website has a file upload vulnerability? Are you worried that hackers will exploit it to hack your site?
We wish we could tell you that there’s nothing to be worried about but the truth is, a file upload vulnerability is a serious issue.
If a hacker finds this vulnerability on your site, they can hijack your site and take full control. They can cause severe damage to your site by defacing your pages, deleting files, stealing data, and even sending spam emails to your customers. You can check the top WordPress vulnerabilities here.
Moreover, things can snowball into much bigger security issues. When Google detects the hack, they will blacklist your website immediately to prevent Google users from accessing it. Further, your web servers provider will suspend your account.
But don’t worry, you can prevent all this from happening by taking the right steps to fix and prevent file upload vulnerabilities on your site.
In this article, we’ll explain what a file upload vulnerability is and show you the most effective ways to protect your site against it. You can also learn how hackers hack WordPress.
What is a File Upload Vulnerability?
Many WordPress websites give visitors the option to upload files for various purposes. For instance, a job portal would allow a user to upload a resume and certificates. A banking website would allow you to upload supporting documentation such as identity, address, and income proof. When a file is uploaded to your site, WordPress check the file and store it in a specific folder called the Uploads directory.
Generally, the documents or some file being uploaded by file uploaders are in a format that cannot execute any commands without showing any error messages.
For images, the accepted formats include png and jpeg. For documents, the formats include PDF and Docx. And for videos, it includes mp3 and mp4 files extension. The formats or file types allow you to only view these files.
As we said, these formats are non-executable which means even if there’s malicious code in them, the code cannot execute any command on your site.
Generally, the upload fields on a website accept only non-executable files. But if it malfunctions, it can start accepting unrestricted file uploads.
Hackers can take advantage of this and upload executable codes in file formats such as PHP file, JavaScript, and exe. These files can run commands wreaking havoc on your website. You can check how to prevent SQL injection attacks.
This is what is known as a file upload vulnerability.
In the sections below, you’ll learn how to protect your website against such vulnerability.
Luckily, there are measures you can take to protect your website against such a vulnerability. However, it’s important to understand how this vulnerability works. So before we discuss protective measures, we’ll take a deeper look into the basic file upload vulnerability in the next section.
What Are The Different Types of File Upload Vulnerability?
Earlier we explained how file upload vulnerability works. We said that in a WordPress website there are fields to upload files. You can only upload certain types of non-executable files. But if the upload field malfunctions (due to a vulnerability), hackers can upload malicious executable files.
Now there are two ways in which the vulnerable upload field accepts a file.
1. It can accept a file directly into the website. In that case, hackers can upload malicious files directly. This is called local file upload vulnerability.
2. Some upload fields don’t allow direct uploads. They ask you to upload your files on a different website say on cloud services like GDrive, Dropbox.
Next, you need to share the location in the form of an URL. The website will fetch the file from the location. It’s an indirect way of uploading files that allow an attacker to upload malicious files on a website. This is called remote upload vulnerability.
Local upload vulnerability and remote upload vulnerability are the two different types of files upload vulnerabilities.
One example of remote upload vulnerability that comes to mind immediately is the TimThumb vulnerability. It was a popular image resizing plugin and the vulnerability affected a large number of WordPress websites. It allowed users to import images from image-hosting websites (like imgur.com and flickr.com). However, due to the lack of security measures, hackers were also able to upload malicious files, in place of images. Those files can have a different file name or various file sizes. But the file content can be very dangerous.
How Do Hackers Exploit A File Upload Vulnerability?
The process of hacking a website is complex and technical. We’ve simplified it as much as we can and laid down the steps in a way that’s easy for anyone to understand.
→ Hackers are always on the lookout for vulnerabilities using which they can gain access to websites.
→ In a WordPress website, it’s common to find vulnerabilities in plugins and themes. When developers of plugins and themes learn about such vulnerabilities, they quickly release an update.
→ Updates contain details of the fix which is how hackers learn that a specific plugin or a theme has a vulnerability that can be exploited.
Learn more about common Website hacking techniques.
What Happens When You Don’t Update Your Site?
→ Hackers rarely target a single website. They scour the internet to find thousands of websites using the vulnerable plugin. Many website owners tend to defer updates as they are unaware of the importance of WordPress updates. They keep running on old versions of the plugin that are vulnerable.
→ Let’s assume you’re using a plugin to enable a comments section on your blog. The developers of this plugin recently discovered a file upload vulnerability. To fix it, they released a patch through an update. For some reason, you were unable to update the plugin. The vulnerability remains in the plugin. Hackers discover that your site is using the old version of the comments plugin. They upload malicious files into your website by exploiting file upload vulnerability (penetration testing). The file contains scripts using which they can start executing malicious activities.
→ Once the infected files are inside your website, hackers execute commands which enable them to steal sensitive data such as your website’s database login credentials. They can escalate the hack further by using the data to log into your website and gain complete control of your site.
How to Protect Your Website From File Upload Vulnerability?
As we mentioned earlier, a file upload vulnerability can have devastating technical impacts on your website. However, if you implement the following steps, you can fix the vulnerability and protect your site against hackers.
Here are 6 important website security measures we recommend you take immediately:
1. Install a WordPress Security Plugin
It’s a good idea to have a WordPress security plugin installed on your site. As we mentioned before, vulnerabilities are bound to appear and for some reason, if you are unable to update the plugin, hackers are going to take advantage of this and hack your site.
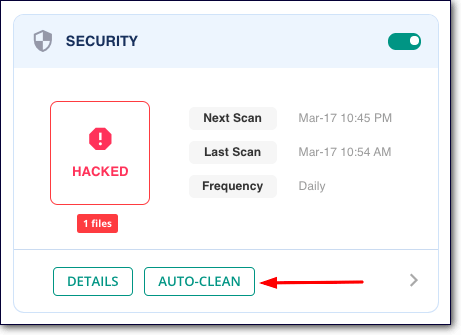
We recommend using our security plugin – MalCare. It comes with a scanner and cleaner, among other things. The scanner uses advanced detection techniques to find hidden malware. And the cleaner is automated which allows you to clean your website with just a few clicks.
The plugin’s vulnerability scanner will scan your website every day and alert you about the hack immediately. It’ll also help you clean your website in under a minute before hackers can damage your site.
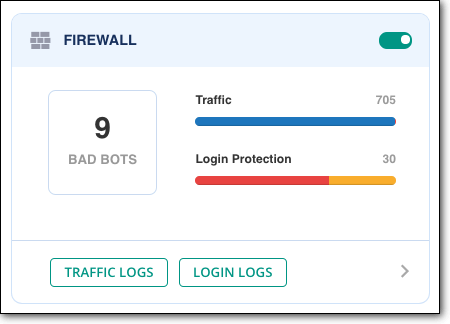
Moreover, the security plugins protect your website through a WordPress firewall.
A WordPress firewall functions like your very own web security superhero who blocks malicious traffic from accessing your website. It checks all incoming traffic of your website. It allows good traffic to access your site and bad traffic are promptly blocked.
This means even if your website contains vulnerabilities, hackers cannot exploit it because they are being prevented from accessing the website by the firewall.
2. Keep Your Website Updated
We discussed earlier that when developers discover a file upload vulnerability in their plugin or theme, they fix it and release an updated version. The new version will contain a web application security patch. Once you update to this version, the file upload vulnerability will be fixed on your site.
That said, updates can sometimes be a hassle. They are frequently available and can sometimes cause your site to break or malfunction. We recommend setting aside time every week to update your website safely by using a staging site.
You can use our plugin, MalCare to set up a staging site, and test updates before installing them on your live site. If you run multiple websites, the plugin enables you to manage and update them all from a centralized dashboard. This makes updates easier, faster, and hassle-free.
3. Buy Plugins & Themes From Reputed Marketplaces
Vulnerabilities frequently develop in poor quality themes and plugins. This is why we suggest using only good quality themes and plugins. A good way to determine the quality of the software is to buy them from reputed marketplaces like Themeforest, CodeCanyon, Evanto, Mojo Marketplace, etc.
Reputed marketplaces have strict policies and security protocols for developers to follow. So products available on these platforms are created with care and maintained well.
4. Retire File Uploading Function (If Possible)
If you feel the file upload function on your website isn’t important, you could consider disabling the feature.
For some websites such as recruitment sites, this might not be an option. However, if the file upload function is not required on your website, we strongly suggest you retire it.
If you’re using a plugin to run the file uploads feature, we suggest deactivating and deleting the plugin. This will remove the possibility of a file upload vulnerability altogether.
5. Change Storage Location of Uploaded Files (Risky)
Everything uploaded on your WordPress website is stored in the Uploads folder. The folder is located inside the public_html directory which stores all the critical files of your WordPress website.
When hackers upload a malicious file into the Upload folder, it enables them to gain access to the public_html directory, i.e. your entire website.
If you move the Upload folder outside this directory, it’s going to make it much harder to gain control of your website.
WARNING: Moving the Upload folder requires expertise so if you are not familiar with the inner workings of WordPress, we suggest you skip this step. Even if you have knowledge of WordPress, we strongly recommend taking complete website backups before making any changes. The slightest misstep can cause your website to break.
These are the 6 file upload vulnerability prevention measures. By taking these measures, your site will be protected against file upload vulnerabilities. That brings us to the end of preventing file upload vulnerabilities on your WordPress site.
In Conclusion
Protecting your WordPress site against file upload vulnerabilities is a step towards ensuring that your website is safe and secure from hack attacks.
However, hackers have many other ways of trying to break into your site. To prevent any kind of hack attempts on your website, we recommend the following –
1. Always have a security plugin like MalCare installed on your site. The plugin comes with a security scanner that will scan and monitor your site daily. Its firewall will also prevent hackers from accessing your site.
2. Updating your WordPress site regularly. Ensuring that you are using the latest version of the WordPress core and all plugins and themes installed on your website.
3. And finally, harden your WordPress site. Site hardening measures will ensure that your site is difficult for hackers to break into.
Take these measures so that you can have peace of mind knowing that your site is secure.
Try MalCare Security Plugin Right Now!
Category:
Share it:
You may also like
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…

MalCare Proactively Defends Against Icegram Express SQL Injection Vulnerability
MalCare’s recent data has revealed numerous attempts to exploit a newly found SQL injection vulnerability in the Icegram Express plugin. Attackers commonly use this sophisticated SQL injection technique to extract…

Atomic Security’s Deep WordPress Integration Helps Protect Against Core XSS Vulnerability
The recent WordPress core vulnerability is a critical one, primarily because of two reasons. Firstly, it affects the WordPress core itself, which means that every WordPress site is vulnerable to…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








