Atomic Security’s Deep WordPress Integration Helps Protect Against Core XSS Vulnerability
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

The recent WordPress core vulnerability is a critical one, primarily because of two reasons. Firstly, it affects the WordPress core itself, which means that every WordPress site is vulnerable to these XSS attacks. Put this in the context of 44% sites on the Internet running on WordPress, and you see the scale of the issue at hand.
Secondly, it has a low barrier for attacks. Attackers do not require any authorization or elevated user roles to perform attacks.
This is exactly why we built Atomic Security: to deeply integrate with and secure every unique WordPress website.
Atomic Security has established a track record of thwarting zero-day attacks that exploited vulnerable plugins before they were even patched. Read on to see how it reacted when a vulnerability appeared in the WordPress core itself.
What is the WordPress core vulnerability?
- Vulnerable WordPress version: v6.5 and earlier
- Patch release version: v6.5.2 and newer
WordPress v6.0 saw the introduction of a new Avatar block. This block is used to display a post author’s avatar within a post or to show a comment author’s avatar when used inside a comment block.
Unfortunately, the code used to display a link to an author’s supplied website URL or post archive was insecurely implemented, resulting in insufficient output escaping on the display name. This made it possible to inject arbitrary JavaScript using an attribute-based XSS payload. Consequently, the WordPress core in various versions up to v6.5.2 is vulnerable to stored XSS attacks via the user display names in the Avatar block.
This vulnerability enables authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. In addition, it also enables unauthenticated attackers to inject arbitrary web scripts in pages that have the comment block present and display the comment author’s avatar.
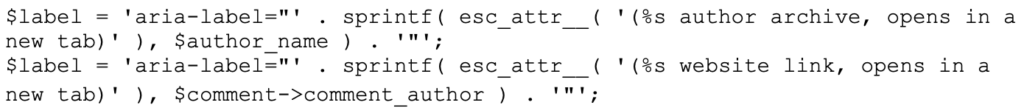
The vulnerability arises due to esc_attr() being performed prior to sprintf(). This means that the comment_author and author_name values are not escaped prior to being included into the HTML because the value is simply a placeholder until sprintf() runs.
This vulnerability has now been fixed with the release of WordPress core v6.5.2 on April 9, 2024.
Who discovered this vulnerability?
The WordPress core stored XSS vulnerability was discovered by John Blackbourn of the WordPress security team. Consequently, it was patched on April 9, 2024, in v6.5.2, which is the latest WordPress release at the time of writing.
How is your WordPress site at risk?
Your WordPress site is at risk if it runs on WordPress core v6.5 or earlier.
Hackers can take advantage of this vulnerability to engage in destructive actions such as:
- injecting malicious scripts to execute phishing or clickjacking attacks, or to redirect visitors to unauthorized websites,
- utilizing compromised websites as hubs for coordinating larger attacks, which can lead to these sites being blacklisted by Google,
- inserting backdoors to reinfect sites that have been cleaned,
- creating unauthorized admin accounts to gain full control over websites, and
- accessing and extracting sensitive data like user credentials and personal information from databases.
Hence, we strongly recommend you to update to WordPress core v6.5.2, or newer, immediately.
What are the symptoms of a hacked site?
If you have reason to suspect that your WordPress site might have fallen prey to attacks exploiting this vulnerability, check for:
- a record in your site’s activity log containing both the path /wp-comments-post.php and an author value containing a suspicious XSS payload
- a record in your site’s activity log containing both the path /wp-admin/profile.php and a first_name value containing a suspicious XSS payload
The presence of any one or both of these records could mean that your site is compromised. Take immediate action to update the WordPress core and scan and clean your site using MalCare.
How to clean your site?
If your WordPress site is hacked, staying calm is key. Here are steps to regain control and improve your site’s security:
- Start a MalCare scan: Deploy MalCare to quickly clear out any malware and strengthen your site’s defenses using its Atomic Security feature.
- Update plugins and themes: Regularly update your plugins and themes to patch potential vulnerabilities that hackers could target. MalCare’s dashboard facilitates this by alerting you to outdated plugins and themes, helping you manage updates to better secure your site.
- Renew WordPress salts and security keys: This measure forces all users to log out and ends all active sessions, dramatically increasing your site’s security. MalCare automates this in its cleanup routine.
- Audit user roles and permissions: Carefully check all user roles and permissions. Quickly remove access if you spot any inconsistencies.
- Update login credentials: Change your admin password immediately. Make sure all users are logged out, instruct them to update their passwords, and advocate for robust, new passwords.
- Enhance login security: Add two-factor authentication (2FA) and set limits on login attempts to decrease the risk of unauthorized entries.
- Keep an eye on your site: Use MalCare’s monitoring tools. It consistently watches for odd behavior and threats, ensuring ongoing protection for your site.
How does MalCare protect your site?
Apart from a robust WordPress-specific firewall solution in Atomic Security, MalCare offers comprehensive security solutions for your WordPress site with the following features:
- Quick malware detection and cleanup: MalCare performs daily automated scans for malware. If threats are found, its powerful removal tool quickly eradicates them, ensuring your site remains safe and healthy.
- Vulnerability notifications: MalCare actively scans your plugins and themes for potential vulnerabilities. It alerts you immediately upon detection, helping you strengthen your site’s defenses.
- Bot defense: Understanding the negative impact bots can have on site performance, MalCare implements effective measures to block these automated threats, enhancing your site’s functionality.
- Efficient backups: With MalCare’s automated, offsite backup system, your data is secured and readily retrievable, giving you a rapid recovery option if needed.
MalCare wraps your WordPress site in a protective layer, using proactive and effective defenses to maintain your online security.
Category:
Share it:
You may also like

MalCare Stands Strong Against WP Activity Log Premium SQL Injection Vulnerability
A significant SQL injection vulnerability was identified in the WP Activity Log Premium plugin, a popular tool for tracking user activity on WordPress sites. An SQLi vulnerability poses a serious…
Fix Pharma Hack on WordPress and SEO
Pharma hack is a prolific malware that redirects visitors from your site to an online pharmacy that sells Viagra, Cialis, Levitra, Xanax, Tadalafil, and other drugs. It also shows up…
How To Protect Your WordPress Website From File Upload Vulnerability?
One of the core strengths of WordPress lies in its file upload functionality. The ability to seamlessly upload and integrate various types of files, from images and documents to multimedia…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








