How to Disable XML-RPC in WordPress?
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

The wp-login or wp-admin page is not the only way a hacker can brute force their way into your site. WordPress has a feature called XML-RPC which enables other systems to communicate directly with your site. As you can imagine, this can be quite a vulnerability.
Login security is a big part of WordPress security, so much so that people go to extraordinary lengths to hide their login pages or remove admin as a username. Disabling XML-RPC is an important measure, and arguably more effective than some hardening measures.
But don’t worry, we’re here to help! In this article, we’ll explain everything you need to know about WordPress XML-RPC vulnerabilities, what risks they pose, and how to protect your site. Whether you’re a developer, a security professional, or just a WordPress user who wants to stay safe, we’ve got you covered.
XML-RPC is a communication protocol that allows third-party apps to interact with your WordPress site from a remote location. Unfortunately, this also means that it can make your site vulnerable to security issues. While you can disable xml-rpc.php, the best way to protect your site is to use a powerful WordPress security plugin like MalCare. The advanced firewall blocks bots, malware, and attackers from accessing your site, keeping it safe and secure—even with the odd vulnerability here and there.
What is the WordPress XML-RPC.php?
XML-RPC is a way for other systems or applications to communicate with your WordPress site remotely. XML-RPC can be compared to a post office that receives and sends mail on behalf of your home or business. The post office is like the xml-rpc.php file, which acts as a middleman between your WordPress site and other systems. When an application sends a request to your site through XML-RPC, the xml-rpc.php file processes it and sends a response back, just like how a post office receives and sends mail on your behalf.
XML is the file format that WordPress uses to export your site’s content. And then there’s RPC—Remote Procedure Call—which is a protocol used to execute code from a different computer. In simpler terms, it lets you do stuff on one computer when you’re using another computer. XML-RPC combines these two things and used to be a big deal for posting content from mobile apps to WordPress sites. But now we have the REST API, which is way more versatile than XML-RPC. Although the underlying code for XML-RPC is still stored in a file called xmlrpc.php on your site, it’s no longer needed.
Why disable XML-RPC in WordPress?
You’ll hear a lot about how you need to disable XML-RPC for security. But why?
XML-RPC can make your WordPress site vulnerable to two types of attacks: brute force attacks and DDoS attacks.
Brute force attacks occur when an attacker tries to guess your username and password combination repeatedly until they gain access to your site. With XML-RPC, attackers can use automated bots to guess login credentials through the WordPress xmlrpc.php file, making it easier for them to launch a brute-force attack. To put it in simpler terms, imagine someone trying to guess the lock combination of your safe repeatedly until they get it right.
DDoS attacks, on the other hand, involve overwhelming your site with traffic, causing it to crash or become unresponsive. With XML-RPC, attackers can use a technique called “pingback” to send a large number of requests to your site’s xmlrpc.php file, overloading it with traffic and causing your site to go down. Imagine someone sending thousands of mail packages to your house at the same time, causing your mailbox to overflow and preventing other packages from getting through.
How to check if WordPress XML-RPC.php is enabled?
Before you go through the trouble of disabling xml-rpc, do you even have it enabled? It’s not as simple as using an FTP client to check if the file exists—because it does exist. It’s a core file that gets installed in every WordPress installation for backward compatibility. Instead, you have to use the XML-RPC Validator to check.
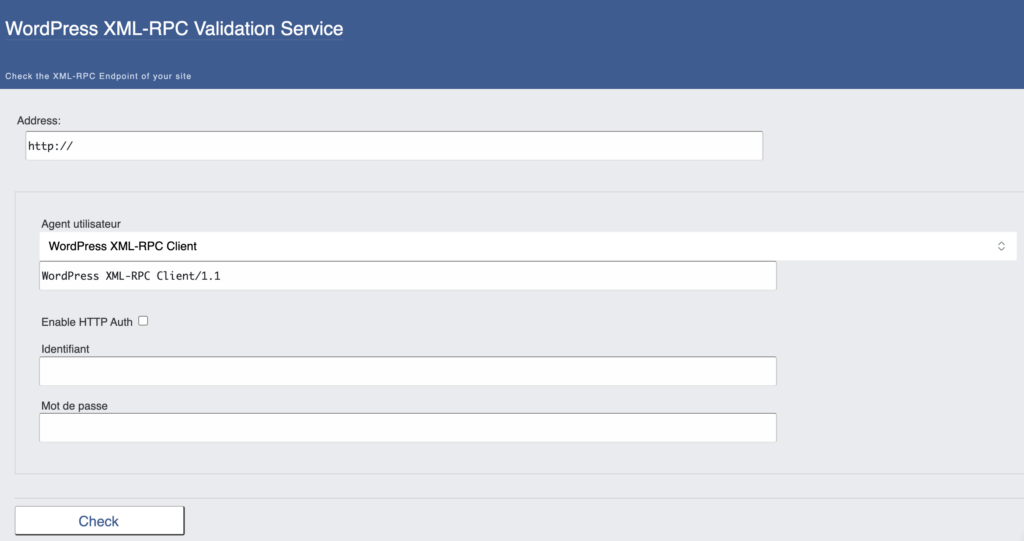
Here are the steps:
- Enter your site’s URL into the text box provided on the XML-RPC Validator page.
- Click the “Check” button to run the validation.
- If XML-RPC is enabled on your site, you will see a message that says “Congratulation! Your site passed the first check.” This means that XML-RPC is enabled and can be accessed.
- If XML-RPC is disabled on your site, you will see an error message instead.
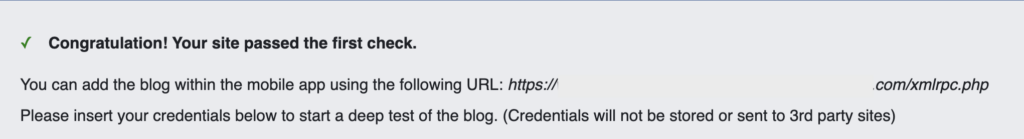
How do you disable XML-RPC in WordPress?
You get it now. It was useful. Not anymore. In fact, it needs to be disabled. It is important to note that simply deleting the xmlrpc.php file to disable it is not sufficient, as this action will result in your site breaking. So what do you do? There are a few different methods to disable the file. Starting from the easiest, here’s how you can disable the file:
Disable xml-rpc in WordPress with a plugin
If you’re looking to disable XMLRPC.php on your WordPress site, installing a plugin is the easiest and quickest solution. We’re using Disable XML-RPC to do this.
From the Plugins menu, search for “Disable XML-RPC” by Philip Erb. Install and activate it. That’s it. With the plugin now active, XML-RPC will be disabled on your site.
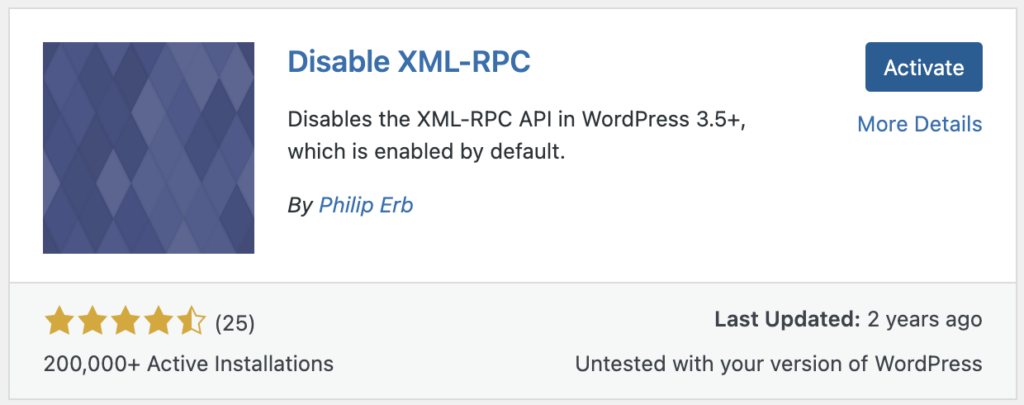
However, if you’d like to keep XML-RPC enabled but disable certain functions that are commonly abused by attackers, you can try the “Disable XML-RPC Pingback” plugin instead. This plugin removes three specific functions while leaving the rest of XML-RPC intact.
To install and activate Disable XML-RPC Pingback, follow the same steps as above. Once the plugin is activated, the specified functions will be disabled while the rest of XML-RPC remains functional.
Block xmlrpc.php via the .htaccess file
If you prefer not to use a plugin to block XMLRPC.php on your WordPress site, you can manually add some code to your website’s .htaccess file instead. However, please note that if your site is hosted on an nginx web server, you won’t have an .htaccess file at all. In that case, you’ll need to contact your hosting provider’s support team to have XML-RPC disabled for you.
To edit the .htaccess file, you can use FTP, cPanel, or the file manager on your web hosting account. The changes you will be making are to your site files, so we can’t stress enough about the importance of a backup. You can use BlogVault to take a full site backup in minutes.
Once you’re done, here’s how to edit the file using an FTP client (in this example, we’ll use Cyberduck):
- Connect to your website using its FTP credentials. These are a username, password and IP address that your web host will have.
- In the root folder of your site, you will find the .htaccess file.
- Double click on the file to download it and open it in a text editor.
- Add the following lines of code to the top of the file, then save and close it:
# Block WordPress xmlrpc.php requests
<Files xmlrpc.php>
order deny,allow
deny from all
</Files>If you want to customize who you are denying requests from, replace the word “all” with those specific IP address as below:
# Block WordPress xmlrpc.php requests
<Files xmlrpc.php>
order deny,allow
deny from xxx.xxx.xxx.xxx
</Files>Disable xmlrpc.php using custom code (Without a plugin)
Another way to disable XML-RPC on your WordPress site is to use a filter. This method requires you to create a site-specific plugin and add a line of code to it. This method is complicated and we recommend you backup your site before making any more changes. Use BlogVault to backup your site in just a few clicks. Then, follow these steps to write that code:
1. Create a new file in a text editor and save it as “your-plugin-name.php”. Replace “your-plugin-name” with a name of your choice.
2. Add the following code to the file:
<?php
/*
Plugin Name: Your Plugin Name
Description: Disable XML-RPC on your WordPress site
*/
add_filter('xmlrpc_enabled', '__return_false');
?>This code creates a new plugin and uses a filter to disable XML-RPC on your site.
3. Save the file and upload it to your site’s wp-content/plugins directory using FTP or the file manager on your web hosting account.
4. Activate the plugin by going to Plugins > Installed Plugins and clicking on “Activate” next to your plugin.
Alternatively, you can add the same line of code to your theme’s functions.php file. However, it’s generally recommended to create a site-specific plugin instead of editing the functions.php file directly, as any changes made to the functions.php file will be lost when you update or change your theme.
When does the XML-RPC.php file need to be enabled?
We’ve gone through the trouble to disable XML-RPC on your WordPress site. But there are some situations where you may want to keep it enabled. Here are a few scenarios where disabling XML-RPC is not advisable:
- Your website is running an older version of WordPress (pre-version 4.4) and doesn’t have access to the REST API. In this case, XML-RPC may be necessary for certain functionality.
- You or someone else you know is using a program that relies on XML-RPC to communicate with your website. If you block XML-RPC.php file, these programs may no longer work.
- Your website is integrated with a third-party application that can only use XML-RPC for communication. If you disable XML-RPC, this integration will break.
In these cases, it may be best to keep XML-RPC enabled, but be sure to take the necessary security precautions to protect your site from potential attacks. The best protection against brute force attacks is a WordPress firewall. Install MalCare, and you get an advanced WordPress firewall, a scanner, and one-click malware removal as well.
What are the best practices for WordPress site security?
While customizing the requests allowed or disabling XML-RPC altogether can help reduce the vulnerability of your WordPress site, it’s not a foolproof solution. For a more comprehensive approach to website security, consider using a plugin like MalCare.
MalCare offers a range of security features, including a firewall that’s designed to keep malicious traffic out of your site. It also has an easy-to-use interface, making it accessible to website owners of all skill levels. You can significantly reduce the risk of your site being compromised by attackers, without having to manually tweak your website’s settings or code.
Wrap Up
While XML-RPC may be outdated and can pose security risks to your WordPress website, simply disabling it may not be the best solution. Customizing XML-RPC requests or editing your website’s code manually can be complex and may not be foolproof. Instead, using a dedicated security plugin like MalCare can provide a more comprehensive approach to securing your site against potential attacks. With its range of security features and user-friendly interface, MalCare can help protect your website from various online threats, giving you peace of mind and ensuring that your site remains secure and functional.
FAQs
How do I stop WordPress XML-RPC attacks?
There are several ways to stop WordPress XML-RPC attacks. Here are some possible solutions:
- Disable XML-RPC: This is the simplest way to prevent XML-RPC attacks. You can block XML-RPC by adding a few lines of code to your website’s .htaccess file or by using a plugin specifically designed to disable XML-RPC.
- Limit access to XML-RPC: If you need to keep XML-RPC enabled for certain functions, you can limit access to it by whitelisting IP addresses or user agents that are authorized to access the service. This can be done using a plugin or by modifying your website’s code.
- Use a security plugin: A security plugin like MalCare can help protect your website from XML-RPC attacks by blocking suspicious requests and implementing other security measures.
By taking these steps, you can significantly reduce the risk of your website being compromised by XML-RPC attacks.
What are XML-RPC attacks?
XML-RPC attacks are malicious attempts to exploit vulnerabilities in the XML-RPC function of a WordPress website. XML-RPC is a remote procedure call protocol that allows external applications to communicate with WordPress sites. Attackers can use this protocol to launch attacks, exploit vulnerabilities, and compromise a website’s security. Some common types of XML-RPC attacks include brute force attacks on login credentials, denial-of-service attacks, and pingback attacks.
What is XML-RPC used for in WordPress?
In WordPress, XML-RPC (XML Remote Procedure Call) is a remote protocol that allows external applications to communicate with WordPress sites. XML-RPC provides a way for remote applications to access and manipulate WordPress content, such as posts, comments, and users. It also enables external applications to perform other functions, such as publishing posts, retrieving comments, and managing WordPress settings.
Is XML-RPC a vulnerability?
XML-RPC is not exactly a vulnerability. It is an old feature of WordPress that has long since stopped being used. However hackers can exploit the feature, therefore it is advisable to disable it from use.
What is the XML-RPC vulnerability?
The XML-RPC vulnerability in WordPress allows hackers to perform brute force attacks by guessing login credentials. It can also be used for denial-of-service attacks. To prevent these attacks, users can disable XML-RPC, use security plugins, ensure strong passwords, and limit login attempts.
Should I disable XML-RPC.php?
Yes, you should disable xml-rpc.php on WordPress sites, as hackers can exploit it to gain unauthorized access to your site.
How to stop XML-RPC php attacks?
To stop xml-rpc.php attacks, you need to disable the file. You cannot delete it, because that will cause your site to have a critical error. Use a dedicated plugin or add a rule to the .htaccess file to disable it from use.
Can I delete XML-RPC php from WordPress?
You cannot delete the xml-rpc.php file from WordPress sites directly. This will cause the site to experience a critical error. Instead, you need to use a dedicated plugin or add a rule to the .htaccess file.
Is XML-RPC php needed for WordPress?
In 99% percent of sites, xml-rpc.php is no longer required. It is an old feature of WordPress, designed to be a seamless connector between the mobile app. It was also used to manage pingbacks and trackbacks on posts and pages. The feature has mostly been phased out now, and is only included with latest versions of WordPress due to backward compatibility.
Having said that, there may be other plugins or integrations that use xml-rpc, although it is considered poor practice to do so. Try disabling the file with a plugin first, and test your site thoroughly to check if this is the case.
What does XML-RPC php do in WordPress?
The XML-RPC feature was created as a way for other systems or applications to communicate with your WordPress site. For instance, if you used the WordPress app to post content to your site, you were using the XML-RPC feature to login into your site remotely. It is also used to manage trackbacks and pingbacks.
What are the disadvantages of XML-RPC?
The major disadvantage of the XML-RPC feature is that it can be used to gain unauthorized access to your site. It is a way to login into your site remotely, and was used by external applications previously. However, it has largely fallen out of use, and therefore is considered a liability for login security.
How do I block access to XML-RPC?
To block access to XML-RPC, you need to add a rule to your .htaccess file (for Apache servers) or need to use a dedicated plugin.
Share it:
You may also like

MalCare Ensures Unmatched Protection Against User Registration Privilege Escalation Vulnerability
Imagine discovering that your WordPress site, which should be secure and under strict control, has suddenly become accessible to unauthorized users who have the same administrative powers as you. This…

MalCare Ensures Proactive Protection Against WP-Members XSS Vulnerability
MalCare continues to protect its customer sites from all kinds of attacks, even the ones exploiting zero-day vulnerabilities. The recent stored cross-site scripting (XSS) vulnerability found in the WP-Members Membership…
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








