How to Use WPScan: A Step-by-Step Tutorial
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

Vulnerabilities in outdated WordPress plugins or themes can allow hackers access to your website. WPScan is a vulnerability scanner for your site, identifying critical vulnerabilities and helping you keep your site up-to-date and secure from cyber threats.
The article serves as a step-by-step tutorial for beginner WordPress users to learn how to use WPScan to find security vulnerabilities. As security experts, we understand the importance of keeping your website secure from cyber threats. That’s why we’ve tested WPScan ourselves and can provide you with reliable information and guidance on how to use it to scan and secure your WordPress site.
WPScan is incredibly user-friendly and straightforward to use, especially for smaller sites. All you need to do is create an account, install the plugin, and you’re ready to go. However, for larger sites, if you want to use the plugin for free, you’ll need to select which plugins and themes you want to monitor. It’s essential to remember that vulnerability scanning is just one aspect of WordPress security, ideally you need a security plugin with a firewall like MalCare to protect your site even if it has vulnerabilities.
WPScan is a vulnerability scanner designed specifically for WordPress websites. As the name implies, it scans your site for vulnerabilities and offers some hardening features.
With one of the most comprehensive vulnerability databases available, WPScan can identify vulnerabilities in even the most obscure plugins and themes with fewer than 100 active installs.
All that being said, WPScan is not a complete security plugin and doesn’t include a firewall or malware removal feature, which is critical for comprehensive WordPress security. For that, you’ll need MalCare.
How to use WPScan to find vulnerabilities?
Using WPScan requires a bit of setup and knowledge of how it works. In this section, we’ll guide you through the process of installing, setting up, and using WPScan so that you can protect your website from potential attacks.
Step 1: Create an account
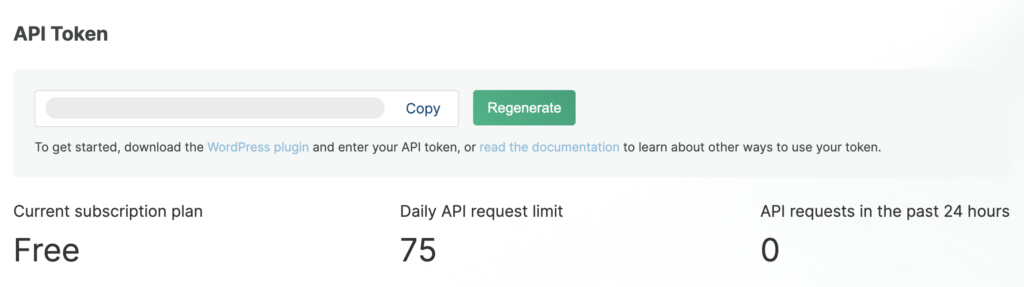
When using WPScan, you’ll need to obtain an API token in order to access the service. This token is unique to each user and is required for the service to track usage and prevent abuse.
To obtain your API token, you’ll need to sign up for WPScan and create an account. Once you’ve created your account, you’ll be able to access your API token in your profile settings.
Step 2: Install WPScan on your WordPress site
There are two methods to choose from when it comes to installation. The first method is beginner-friendly and involves using the WPScan plugin directly from the WordPress dashboard. The second method is a bit more advanced and involves installing WPScan from the command line. Let’s take a look at both methods in more detail.
Install WPScan with a plugin
The quickest way to start using WPScan is by using a plugin.
1. Install and activate the WPScan plugin from the plugins page on your WordPress dashboard.
2. Obtain your API key by signing up for a WPScan account and finding the key in your profile.
3. Enter the API key in the wp-admin dashboard to enable scanning functionality.
4. Deselect any plugins or themes you don’t want checked, as the free version of WPScan only allows for 25 API calls per day. Each plugin or theme takes 1 API call. If you keep your WordPress version updated regularly, you can deselect that from the list of items to be checked.
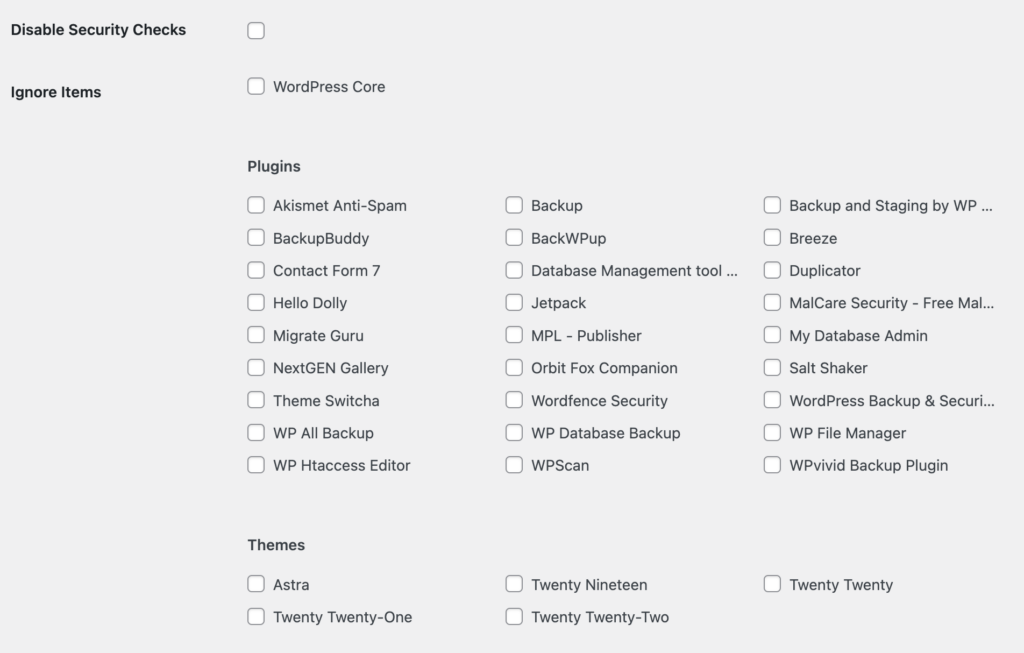
Customize the scan settings to suit your site’s needs, but make sure to check all installed plugins and themes, especially if you don’t keep them regularly updated.
Install with WP-CLI
To install WPScan via the command line, enter one of the following commands in the terminal:
If you’re using Windows: gem install wpscan
If you’re using a MacOS: brew install wpscanteam/tap/wpscan
Step 3: Scan your site with WPScan
If you installed WPScan as a plugin, you can access it through your WordPress dashboard. If you installed it using a command-line tool, you’ll need to use the terminal to run scans.
Use the plugin
After setting up WPScan, it will automatically run a daily scan at a fixed time.
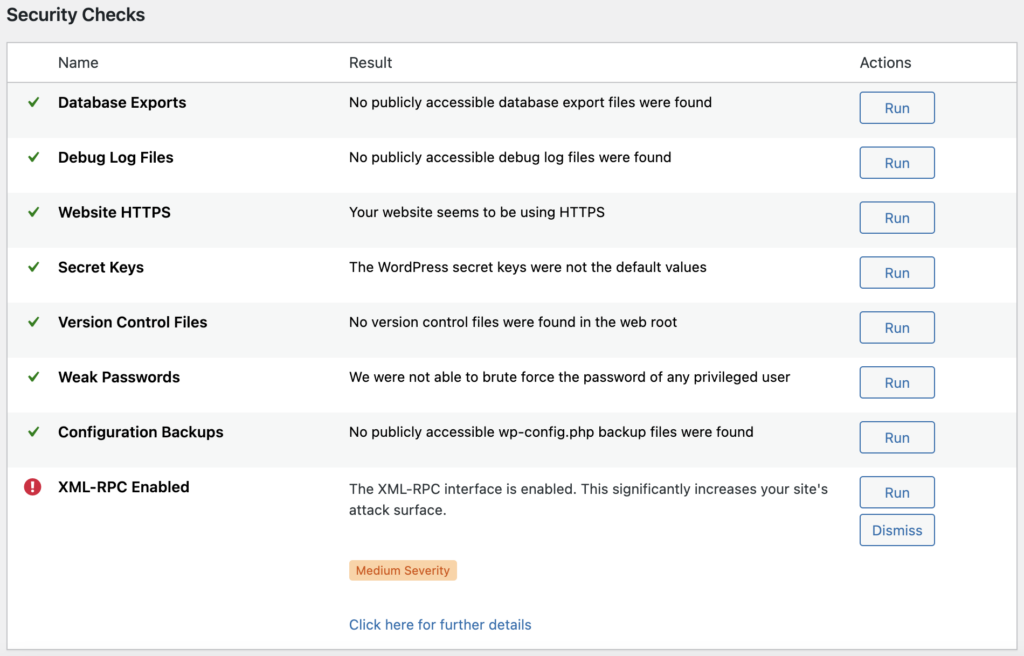
To run a manual scan, click on “Run All” in the “Click the Run All button to run a full vulnerability scan against your WordPress website.” box.
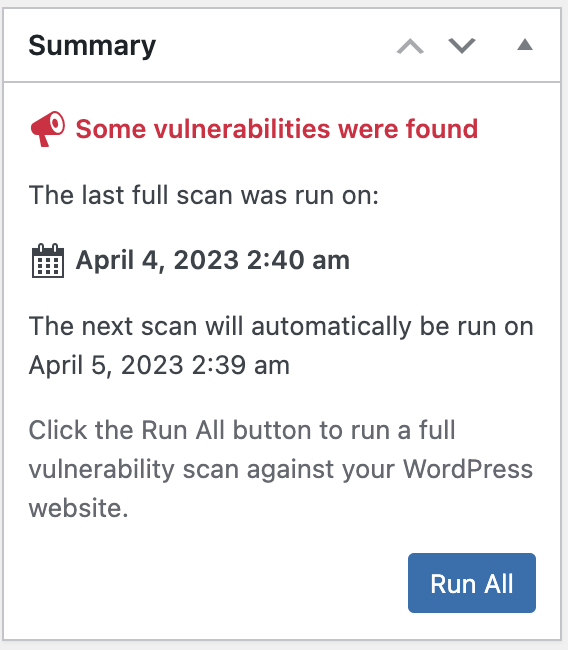
Each plugin or theme will have a corresponding result and recommended action, usually to update if a vulnerability has been fixed in a subsequent update, with a link to more information.
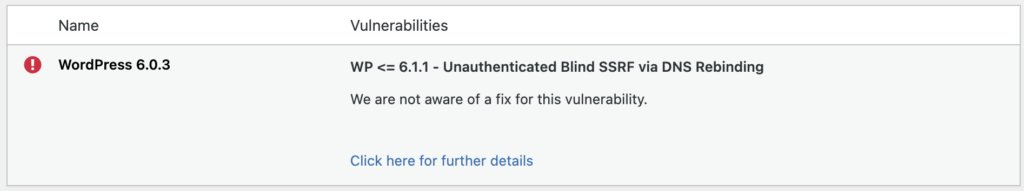
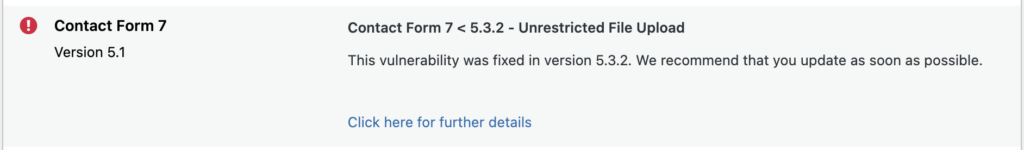
You can click through to see the vulnerabilities discovered and reference links.

Additionally, you can configure email alerts for scan reports.
Use WP-CLI
The basic scanner can be used with the following command:
wpscan --url <your site URL here> This will check if your plugins and themes are up to date. There are several commands you can use from the command line. WPScan can also be used to test your site against brute force attacks. Bear in mind, some of the commands will require the use of the API token.
Step 4: Check other hardening measures
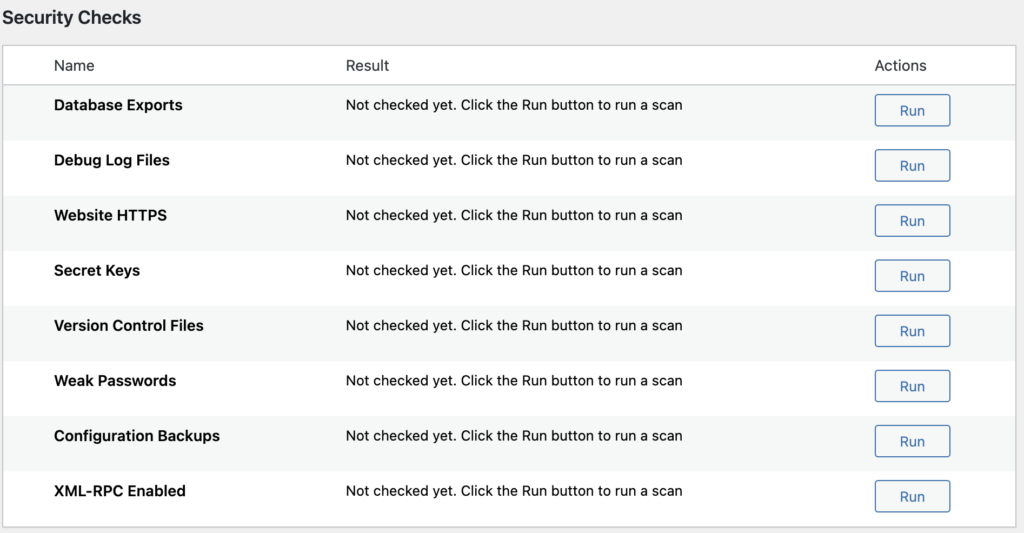
Here are some extra things to look out for in a WPScan report, apart from a basic scan:
- Check for debug.log files: log files may contain sensitive information that can be used by attackers to exploit vulnerabilities.
- Check for wp-config.php backup files: wp-config.php contains sensitive data such as database credentials and password salts, and should be kept secure.
- Check if XML-RPC is enabled: XML-RPC presents a potential security risk as it provides an alternative way to log into a site. It is recommended to disable it if not needed.
- Check for exported database files: backups stored in publicly accessible folders can contain sensitive user data and should be kept secure.
- Check for weak passwords: use a password strength checker to ensure passwords are secure.
- Check if HTTPS enabled: make sure SSL is enabled on the site.
Pricing
WPScan is a great tool to have under your site security belt. It’s an important part of WordPress security that is easy to use and effective. With that out of the way, let’s talk pricing.
The free version of WPScan is available for personal and non-commercial use, but it is not actively supported. Many people choose to use Jetpack instead.
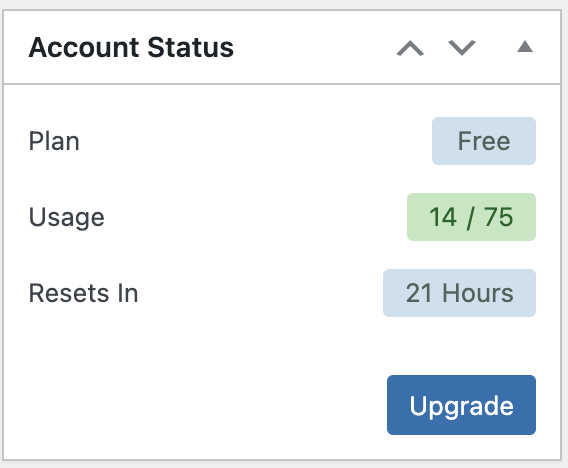
The enterprise edition of WPScan offers a free version that allows for up to 25 API calls per day. You can check how many API calls you’ve used in the “Account Status” box on your dashboard.
Commercial users can opt for Jetpack Protect, which includes WPScan. For enterprise users, developers can integrate WPScan directly into their site.
Wrap up
While WPScan is a great tool for identifying vulnerabilities in your WordPress site, it is not a complete security solution. If the scanner reveals vulnerabilities, your site may have malware already. To be absolutely clear, WPScan cannot detect malware at all.
If you suspect your site has malware, you will need a malware cleaner to remove it. Additionally, to protect yourself from future attacks, you will need a firewall in place.
This is where the MalCare plugin comes in. It is the most comprehensive security plugin that not only includes a powerful malware cleaner but also a firewall to protect your site from future attacks.
FAQs
What is the use of WPScan?
WPScan is a security tool designed specifically for WordPress sites. It is used to identify vulnerabilities in WordPress plugins, themes, and the core WordPress installation itself. The tool scans for vulnerabilities using a database of known issues, and provides information on how to patch those vulnerabilities. WPScan can be used by website owners, developers, and security researchers to identify potential security weaknesses in their WordPress site and take necessary actions to prevent any potential attacks.
Where do I put the API token in WPScan?
The API token can be added to WPScan’s dashboard, or used with the appropriate command from CLI.
Some of the commands require an API token for WPScan’s advanced features, such as enumerating plugins and themes, test brute force attacks, and vulnerability testing. To use the API token with WPScan, you need to run the command with the –api-token option, followed by your API token.
For example, the command would look like this:
wpscan --url https://example.com --api-token ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789Replace https://example.com with the URL of your website and ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789 with your API token.
Share it:
You may also like

MalCare Ensures Proactive Protection Against WP-Members XSS Vulnerability
MalCare continues to protect its customer sites from all kinds of attacks, even the ones exploiting zero-day vulnerabilities. The recent stored cross-site scripting (XSS) vulnerability found in the WP-Members Membership…
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…

MalCare Proactively Defends Against Icegram Express SQL Injection Vulnerability
MalCare’s recent data has revealed numerous attempts to exploit a newly found SQL injection vulnerability in the Icegram Express plugin. Attackers commonly use this sophisticated SQL injection technique to extract…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








