Complete Guide To Removing Referral Spam
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

A sudden surge in website traffic is undeniably exciting for any online business or website owner. However, when you notice a significant increase in traffic from unusual and suspicious sources, alarm bells start ringing.
You might be experiencing the common menace known as referral spam.
As these misleading practices continue to infiltrate website analytics, accurately tracking real user behavior becomes a formidable challenge. In this article, we address the telltale signs of referral spam and shed light on effective strategies to block it.
TL;DR: Referral spam is is when bots target both your website and messes with your traffic analytics. MalCare, with a firewall and strong bot protection, is the most effective solution to fight every type of spam bot.
What is referral spam?
Referral spam is a technique used by spammers to artificially inflate website traffic by using bots to fake referral traffic to your website. The spammer can also potentially gain backlinks from doing this. By injecting fake data into your analytics reports, referral spam can disrupt the accuracy of your website analytics and distort your understanding of actual visitor behavior.
Types of referral spam
2 ways to stop referral spam
There are two different ways to block referral spam bots: you can use bot protection to stop spam bots automatically, or block well-known IP addresses for referral spam sites.
A. Install MalCare’s WordPress firewall
MalCare is a complete security plugin, with a built-in WordPress firewall. As most referral spam is caused by bots, with MalCare’s strong bot protection, you stay one step ahead.
This feature is built to adapt to the rapidly evolving techniques of spammers, ensuring your website remains uncompromised and accurate. Moreover, it is non-intrusive, meaning it doesn’t affect your website’s speed or its user experience. Its lightweight nature and the server load it neutralizes make it an all-around champion against referral spam.
- Create an account on the MalCare website.
- Add your URL and your admin credentials
That’s it. Once you’ve set it up, the plugin enables bot protection automatically. Super easy, right?
Why we recommend MalCare
MalCare is also a lot more than just bot protection. It’s a comprehensive security solution designed to keep your website safe from all corners.
B. Blacklisting IP addresses from the .htaccess file
.htaccess is a powerful configuration file within the root directory of your WordPress website. It is responsible for various settings, including rewriting URLs, redirecting traffic, and providing additional security measures. By altering this file, you can actively block malicious referral spam from accessing your website.
Note: If you choose not to install a firewall, you can block spam referral domains manually using this method. We strongly recommend against doing so, as fiddling with a core WordPress file is never a good idea. Additionally, this method is labor-intensive and not scalable. At some point, blocking domains individually is going to become impossible to maintain.
Option 1. FTP
Pro tip: Before making any changes, it is crucial to create a backup of your existing .htaccess file. This way, if any issues arise, you can easily revert to the previous version. We recommend using BlogVault to back up your entire site before making any changes.
- Connect to your server: Connect to your website’s server using an FTP client like FileZilla. You can find the FTP credentials on your hosting account. You’re looking for a username, password, and IP address. We’re using Cyberduck.
- Find the .htaccess file: The .htaccess file is in the root directory of your WordPress installation. In our case, it is the public_html directory. The .htaccess file is often hidden. We navigated to View in the menu and enabled Show Hidden Files.
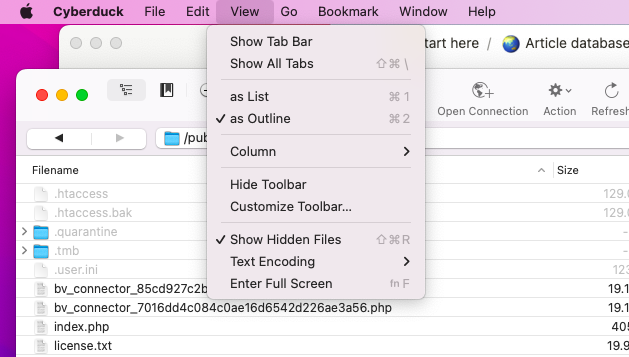
- Add code to block referral spam: Once you have the .htaccess file open it in a text editor. Then, insert the following code below the existing content in the file to block referral spam. Replace
spamdomain.comandanother-spam-domain.comwith the actual domains from which you are receiving referral spam. You can add moreRewriteCondlines for each spam domain. The NC flag ensures a case-insensitive match, and the OR flag indicates that if any of the conditions are met, the rule will be applied. The last domain on the list should not have the OR flag. F will return a 403 Forbidden response.
# Blocking Referral Spam
RewriteEngine on
RewriteCond %{HTTP_REFERER} spamdomain\.com [NC,OR]
RewriteCond %{HTTP_REFERER} another-spam-domain\.com [NC]
RewriteRule .* - [F]- Save the file and upload it: Save the changes to the .htaccess file and upload it back to your server. In the case of Cyberduck, you will have to upload a text file named htaccess and then rename it to .htaccess once you’re done.
Option 2. File Manager on cPanel
- Log into cPanel. Under the Files section, click File Manager.
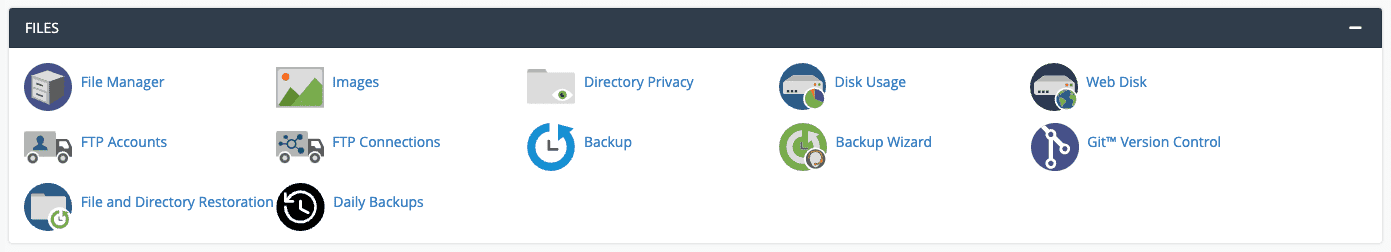
- Look for the .htaccess file. Right-click on the .htaccess file and select Edit or Code Edit. A text editor will open inside the browser.
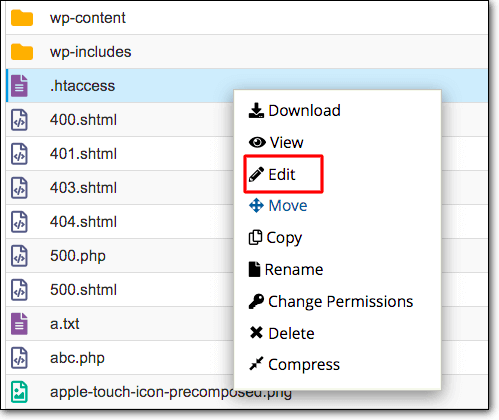
- Add the following code at the top or bottom of your .htaccess file. Replace
spamdomain1.com,spamdomain2.com, andspamdomain3.comwith the actual domains that you’re receiving referral spam from. The NC flag denotes ‘no case’, meaning it is case-insensitive, and OR lets you add multiple conditions. The last domain listed should not have the OR flag. F means that a matching request will be denied and the server will return a 403 Forbidden response.
RewriteEngine on
RewriteCond %{HTTP_REFERER} spamdomain1\.com [NC,OR]
RewriteCond %{HTTP_REFERER} spamdomain2\.com [NC,OR]
RewriteCond %{HTTP_REFERER} spamdomain3\.com
RewriteRule .* - [F]- After you have added the necessary domain names that you wish to block, save the changes file.
Option 3. SSH
- Connect to your server using a terminal or an SSH client (like PuTTY) and connect to your server with the following command. Replace
usernamewith your actual username andyour_server_ipwith your server’s IP address. Enter your password when prompted.
ssh username@your_server_ip- Your .htaccess file is in your website’s root directory. In our case, this is called public_html. Use the
cdcommand to navigate there. This is typically something likecd /home/username/public_htmlorcd /var/www/html.
cd /path/to/your/root/directory- Open .htaccess with a text editor using the command below. This command opens the .htaccess file with the nano text editor. If nano is not installed or you prefer another, replace
nanowith the editor of your choice.
nano .htaccess- Add the following code:
RewriteEngine on
RewriteCond %{HTTP_REFERER} spamdomain1\.com [NC,OR]
RewriteCond %{HTTP_REFERER} spamdomain2\.com [NC,OR]
RewriteCond %{HTTP_REFERER} spamdomain3\.com
RewriteRule .* - [F]- After editing, save the changes by pressing Ctrl + O. Hit Enter, and then exit by pressing Ctrl + X.
Pro tip: Just use MalCare. We found this method cumbersome and risky. It can be frustrating to manually block IP addresses, especially, if you’re being bombarded with them.
Here are some other reasons why we do not recommend this method:
- Syntax errors: Any typo or mistake in the code can lead to website misconfiguration or even a complete outage. Always double-check the code and ensure its accuracy before saving changes.
- Loss of valid traffic: There is a possibility of inadvertently blocking legitimate traffic if the conditions in the .htaccess file are not accurately defined. Regularly review your analytics data to ensure no valid referrers are being blocked.
- Limited effectiveness: While editing the .htaccess file can help mitigate referral spam, it is not foolproof. Spammers can continuously change their tactics and domains, requiring constant updates to your .htaccess file to keep up with new sources of spam.
- Compatibility issues: If you are running a complex server setup or using plugins that rely on specific .htaccess configurations, modifying the file may lead to conflicts and compatibility issues. Always test your website after making any changes to ensure proper functionality.
Using different Google Analytics tools
It’s important to note that there is a lot of advice on using the referral exclusion list. While the referral exclusion list within Google Analytics seems like it would be the perfect solution for referral spam, it unfortunately doesn’t work as well as intended for this issue. Here’s why:
- Misunderstood functionality: The primary purpose of the referral exclusion list is for e-commerce websites to prevent self-referrals and is not specifically aimed at blocking spam. When a user is redirected to a third-party site (like a payment gateway) and then returned to the website, Google Analytics might consider them as new sessions. By adding the third-party domain to the referral exclusion list, you can prevent this and keep the session intact.
- Ineffective against ghost spam: The referral exclusion list cannot stop ghost spam. These culprits bypass your website and hit Google Analytics servers directly, leaving a fake website referral while not interacting with your website at all. Since these spammers never visit your site, they can’t be excluded through the referral exclusion list.
- Adds more traffic: This is indeed a bit paradoxical. When you add a spam domain to the referral exclusion list, Google Analytics reclassifies the traffic from referral to direct instead of excluding it. So, you’ll still see spam traffic, just under a different category.
- Labor-intensive: The referral exclusion list requires manual updating. Given the proliferating number of spam domains, it can be an exhaustive and never-ending task to keep up with.
There is also some advice online about enabling Google Analytics’ bot protection. It was a feature in UA to help you enable bot protection to fight off spam bots towards the Google Analytics Property ID. But, with GA4, this feature is enabled automatically. So, on the analytics tool front, GA4 has you covered.
Symptoms of referral spam
Referral spam can manifest in various ways, leaving behind noticeable symptoms that can alert website owners to its presence. By being vigilant and monitoring your analytics data, you can identify these symptoms and take appropriate actions to mitigate the impact of referral spam. Here are some common symptoms to watch out for:
- Inflated traffic numbers: One of the key symptoms of referral spam is a sudden spike in website traffic. If you notice a significant increase in traffic from specific referral sources without any corresponding increase in user engagement or conversions, it may indicate the presence of referral spam. Spammers use automated bots or scripts to simulate traffic, artificially inflating the number of visitors reported in your analytics reports.
- Unusual referral sources: Referral spam often generates traffic from irrelevant or suspicious sources that have no logical connection to your website or target audience. Here are some signs that the referral sources are spam sources:
- If you notice URLs that you don’t recognize or that don’t align with your marketing efforts, there’s a high likelihood that the referral source is spam. Legitimate referral sources are typically associated with known websites or platforms that are relevant to your niche or industry.
- Another red flag is a high bounce rate because visitors leave your website after viewing only one page. Referral spam often generates high bounce rates because the traffic is not genuinely engaged with your content.
- Keep an eye out for referrals from unexpected source countries. Spammers frequently use this tactic to make their traffic appear more believable.
- Referral spam may exhibit perfect or suspiciously clean data in your analytics reports. This includes metrics such as zero-second session durations, unrealistic session times, or consistently high page views from specific sources. These anomalies often stem from automated bots or scripts, which typically exhibit behavior that real visitors would not.
- If you find referral links leading to unrelated or irrelevant content, it is likely an indication of spam. Legitimate referrers usually link to content that aligns with your website’s focus or industry.
- Referral spam may introduce out-of-place keywords into your analytics data. These keywords may seem unrelated to your website’s content or niche. Spammers use this strategy to trick search engines or artificially rank certain websites higher for specific keywords. Spotting unusual or unrelated keywords associated with referral sources is a telltale sign of spam.
- If you notice URLs that you don’t recognize or that don’t align with your marketing efforts, there’s a high likelihood that the referral source is spam. Legitimate referral sources are typically associated with known websites or platforms that are relevant to your niche or industry.
Impact of referral spam on your WordPress site
Referral spam can have several negative effects on your WordPress site, like:
- Skewed analytics data: Referral spam artificially inflates your website’s referral traffic numbers. This can cause inaccurate reporting and insights in your analytics platforms, making it difficult to accurately assess your website’s actual performance.
- Distorted conversion rates: One of the goals of referral spam is to trick website owners into visiting the spammer’s site out of curiosity. Since these visits typically have no real interest in your content, they don’t result in genuine engagement or conversions. As a result, your conversion rates may appear lower than they are.
- Increased server load: Depending on the volume of referral spam hitting your site, it can cause increased server load. This can result in decreased website performance, slower loading times, and even potential downtime in extreme cases.
- Negative user experience: Referral spam often leads to unexpected and irrelevant referral URLs appearing in your website’s analytics reports. This can be misleading and confusing for website owners trying to understand their traffic sources, causing frustration and hindering effective decision-making.
- Manipulation of SEO: Some referral spam links may have anchor text or keywords associated with them. When search engine bots crawl your site and encounter these spam links, it can negatively impact your site’s search engine optimization (SEO) by associating it with questionable or irrelevant content.
- Security risks: While not all referral spam poses direct security threats, some can lead to potentially harmful websites. Clicking on spam referral links can expose users to phishing attempts, malware distribution, or other malicious activities.
Why do hackers spam your site with referrals?
Hackers employ referral spam for a variety of reasons, each aimed at achieving their malicious goals:
- Distortion sabotage: By flooding your site with fake referral traffic, hackers aim to distort your website’s analytics data. This tactic makes it challenging for you to accurately evaluate your actual traffic, engagement, and campaign performance.
- SEO spamming: Some malicious actors use referral spam as a technique to improve their own website’s SEO. By generating fake referral traffic from your site, they attempt to create backlinks that may deceive search engines into thinking their site is popular or relevant.
- Phishing attempts: Referral spam can also be used as a gateway for phishing attempts. Hackers may trick you into visiting their malicious websites, which mimic legitimate sites, to extract sensitive information such as login credentials or financial data.
- DDoS attacks: In more severe cases, referral spam may form part of a larger Distributed Denial of Service (DDoS) attack strategy. With a massive influx of fake referral traffic, hackers overwhelm your server resources, leading to website crashes, slow performance, and potential downtime.
- Exploitation discovery: Hackers may employ referral spam to probe your website for vulnerabilities. By analyzing your server logs and responses to their spam visits, they can identify potential weaknesses or security loopholes to exploit further.
- Advertising: Referral spam can be used by hackers to attract attention to their websites or products. By appearing in your analytics reports, they aim to generate curiosity and potentially drive traffic to their site, boosting their own visibility and advertising efforts.
Final thoughts
Referral spam is frustrating to handle and difficult to identify without constant monitoring. But, thankfully it is completely preventable with good bot protection. MalCare not only installs a firewall that can block bots, but it also has features like a great scanner that offers real-time security. The plugin’s user-friendly interface and intuitive dashboard make it easy to monitor your site’s security and take proactive actions like updating vulnerable plugins.
MalCare is not only your defense against referral spam but also a shield against every other type of attack that a hacker can throw at you.
FAQs
What is referral spam?
Referral spam refers to the deceptive practice of artificially generating fake website referrals to drive traffic to particular websites. These spam referrals can skew website analytics data and negatively impact website performance.
How do I stop spam referrals?
To stop spam referrals, use bot protection from MalCare.
How can I identify referral spam?
Referral spam can be identified by analyzing your website analytics data. Look for sources that have abnormally high traffic with a high bounce rate, low session duration, and suspicious or irrelevant domains. Additionally, referrals with strange or nonsensical names are often indicators of referral spam.
Can referral spam affect my site’s SEO?
While referral spam does not directly impact your site’s SEO in terms of search engine rankings, it can distort your website analytics data and misrepresent your traffic sources. This can make it difficult to accurately measure the effectiveness of your SEO efforts.
Are there any tools or plugins to block referral spam?
Yes, there are tools and plugins available to block referral spam. MalCare is a popular bot protection tool that can help prevent spam referrals. Additionally, you can enable bot protection within your Google Analytics settings to further block such spam referrals.
Category:
Share it:
You may also like

How to Fix the Google Blacklist Warning from Your Website
Google blacklist is a colloquial term used to describe big red warnings visible when visiting websites. There are a few flavours, depending on various factors, but they all mean that…

MalCare Stands Strong Against WP Activity Log Premium SQL Injection Vulnerability
A significant SQL injection vulnerability was identified in the WP Activity Log Premium plugin, a popular tool for tracking user activity on WordPress sites. An SQLi vulnerability poses a serious…
Fix Pharma Hack on WordPress and SEO
Pharma hack is a prolific malware that redirects visitors from your site to an online pharmacy that sells Viagra, Cialis, Levitra, Xanax, Tadalafil, and other drugs. It also shows up…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








