How to Implement Cross-Site Scripting Prevention?
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

Are you worried about cross-site scripting attacks on your website? We wish we could tell you that there is nothing to worry about!
But the fact is cross-site scripting attacks are very common. And it’s possible that your website will be affected by cross-site scripting attack sooner or later.
In this type of attack, hackers use the visitor’s browser to attack your website. Once they gain access to your website, they can steal sensitive data, store illegal files and folders, redirect your visitors to other malicious sites, manipulate search results with spammy keywords, launch attacks on other websites, among other things. Such malicious activities have the potential to destroy your website.
The attack will slow your website down and affect your website search engine rankings. You will experience a dip in traffic and eventually, your revenue will take a hit.
Things can snowball much further, and users will see warnings like deceptive site ahead, this site may be hacked on your website in search results, Google may blacklist your site, and your hosting provider may suspend your site.
But don’t worry, you can prevent all this from happening to your website by taking a few simple cross site scripting prevention measures.
In this article, we’ll help you implement the right steps to protect your website from cross-site scripting attacks.
TL;DR: Cross-Site Scripting is a dangerous hack and it causes serious damage to victim sites. But it can be prevented easily. You can install a WordPress security plugin like MalCare to protect your site against this type of attack.
[lwptoc skipHeadingLevel=”h3,h4,h5,h6″ skipHeadingText=”Before You Leave”]
What Is A Cross-Site Scripting Attack (XSS)?
In a cross-site scripting attack, a hacker hacks a website by impersonating the visitor.
The best way to understand this type of attack is to follow the steps the hacker takes to execute the attack.
→ Most websites have input fields (like contact or sign up form or a comment section) that allow visitors to enter data into the website.
→ These fields are enabled by a plugin. Generally, the plugins make sure that the data inserted into the fields is not malicious like a code snippet. But if the plugins develop XSS vulnerability, they can allow a visitor to enter malicious data or untrusted data.
For instance, a vulnerable comment plugin allows visitors to insert a malicious link.
→ When you click on the link, malicious code or a malicious javascript is activated and you are asked for permission to access your browser cookies.
→ It looks like your website is asking you to execute a specific function. It’s very likely that you will fall for the trick and allow access to your browser cookies.
By allowing access to your browser cookies you expose sensitive information to a hacker.
→ Browser cookies store all sorts of information including your login credentials. Once they gain access to your login credentials, the hacker can impersonate you and log into your website.
What Are The Different Types of XSS or Cross-Site Scripting Attacks?
There are two types of crosssite script attacks. Those are:
- Stored (or Persistent) XSS Attack – Target for this is the visitor of the site.
- Reflected (or Non-Persistent) XSS Attack – Target for this type of attack is the website.
Cross-site scripting attacks occur due to vulnerable plugins. Hackers scan the internet looking for a website using vulnerable plugins like form or comment plugins. These plugins generally develop issues with user input validation. Once they discover a website using a vulnerable plugin they start executing the attack.
By the end, hackers have access to the victim’s browser cookies that store crucial information like website login credentials, e-banking credentials, Facebook, and email credentials among other things.
If the hacker’s main goal is to hack your website, he’ll extract site login credentials. This is called a reflected XSS attack. But if the hacker is targeting the users or visitors of the site, he’ll extract e-banking, Facebook, and Gmail credentials. This is called a stored XSS or persistent XSS attack.
Now that you understand cross-site scripting and it’s different forms, let’s take a look at how to protect your website against this type of hack attack.
Cross-Site Scripting Prevention Measures
WordPress sites are built using plugins and themes. Most sites have an input plugin that enables a contact form or comments section that allows visitors to insert data.
Many input plugins develop XSS vulnerabilities over time. As we discussed earlier, hackers can use vulnerabilities to launch crosssite scripting attacks on your site. Since the plugin is an important part of the website, you cannot just delete it. What you can do is take measures to prevent XSS attacks on your website.
We’ll show you 5 measures you need to implement on your site for preventing xss vulnerabilities and protect it against XSS attacks.
- Install a Security Plugin
- Install the Prevent XSS Vulnerability Plugin
- Review Comments Before Making Them Live
- Keep Your Plugins Updated
- Use Plugins From Reputed Marketplaces
1. Install a Security Plugin
A good security plugin like MalCare will protect your website with a WordPress firewall and enables you to implement site hardening measures.
i. Firewall
WordPress firewall plugin investigates the oncoming traffic and prevents bad traffic from accessing your website. Visitors (including hackers) access your site using a device like a smartphone or a laptop. Every device is associated with a unique code which is called an IP address. MalCare’s firewall scans the internet looking for bad IP addresses. IP addresses that have been associated with malicious activities in the past are prevented from accessing your website.
In this way, hackers who try to access your site to implement an XSS attack are blocked at the onset.
ii. Site Hardening
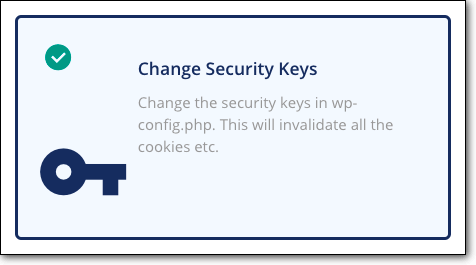
MalCare has many WordPress hardening measures and one of them is changing security keys. We know that in a cross-site scripting XSS attack, hackers try to steal user’s browser cookies which contain user credentials. However, WordPress stores these credentials in an encrypted manner. It adds security keys and salts to your password which makes it hard to decipher it.
If the hackers know what the keys and salts are, they can learn what your login password is. This is why web application security researchers recommend changing the WordPress salts and keys on a bi-yearly or quarterly basis. With MalCare, you can change your security keys with the click of a button.
2. Install the Prevent XSS Vulnerability Plugin
Once you have a reliable security plugin in place, we recommend installing the Prevent XSS Vulnerability plugin to identify parameters commonly found in XSS attacks.
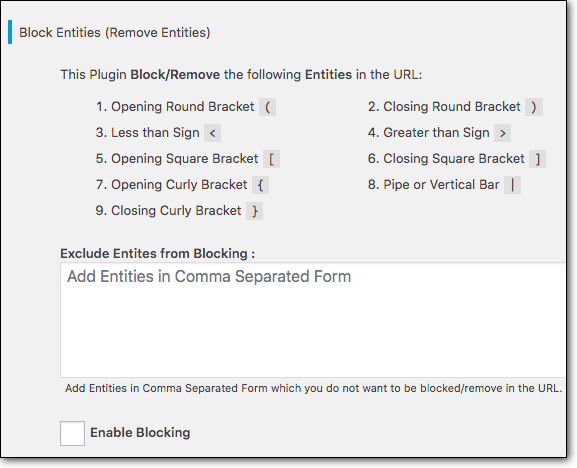
For instance in the injected malicious link that hackers may leave on your comment section may use symbols like exclamation marks, opening round brackets, etc. By blocking these parameters, the plugin will help prevent cross site scripting attacks on your WordPress website.
That said, this plugin can provide only limited protection against XSS. A firewall plays a crucial role in preventing and detecting XSS attacks early on. This is why we first recommend using this plugin in addition to a security plugin.
3. Manually Approve Comments Before Making Them Live
In crosssite script attacks, hackers leave malicious links in the comment section in hopes that someone will click the link.
It’s best to investigate comments before allowing them on your website. WordPress’ native comment system as well as popular comment plugins like JetPack, Thrive Comments, Disqus, etc allow you to manually review comments before accepting and publishing them.
That said, identifying malicious links is not easy. Hackers leave genuine comments with links disguised to look as legitimate. Even when investigating the link, if you accidentally click on it, it can initiate the hack attack.
Many site owners prefer to use comment plugins and not WordPress’ native comment system. This is because comment plugins have a better capacity to manage spam. But as we mentioned, plugins tend to develop vulnerabilities over time and this can open up your website to hack attacks.
To retain your comment plugin and overcome any content security vulnerabilities, we advise you to keep your plugins updated. We discuss why in the next section.
4. Keep Your Plugins Updated
When developers of plugins discover XSS vulnerabilities in their software, they quickly fix it and release a security patch.
This patch comes in the form of an update.
Once you update the plugin on your site, the XSS vulnerability will be patched. But if updates are deferred, then your website becomes vulnerable to cross-site scripting or XSS attack.
This is because once a security patch is released, the vulnerability becomes public information. It means hackers are aware that a vulnerability exists in the old version of the plugin. Hackers scan the internet using bots and tools to find WordPress websites using a particular version of the plugin that is vulnerable.
If you defer the update, your website will become a target for a hack.
They can then exploit the cross-site scripting vulnerability and hack your website. Therefore, as a rule of thumb, always keep your website updated.
5. Buy Plugins From Trusted Marketplaces
If you are using free plugins like Jetpack and Disqus, it’s best to download them from the official WordPress repository. If you are going to use premium plugins like Thrive Comments or WpDevArt, get them from their official website or trusted marketplaces like Code Canyon, ThemeForest, Evanto, etc.
Trusted marketplaces offer high-quality plugins that reduce chances of cross-site scripting vulnerabilities cropping up.
These days, there are plenty of websites offering pirated versions of premium plugins for free. Most of these pirated plugins come pre-installed with malware. Installing them on your site equates opening doors to hackers. Moreover, pirated plugins don’t receive updates which means vulnerabilities cropping up in the plugins remain, leaving your website vulnerable to a hack attack.
Avoid using pirated plugins from untrusted sources. Use plugins from only trusted marketplaces or the WordPress repository.
With that, we have come to the end of preventing cross-site scripting on your WordPress website. We are confident that if you implement these measures, your website will be protected against cross-site scripting attacks.
Before You Leave
Protecting your WordPress site against cross-site scripting attacks is a step in the right direction when it comes to website security.
However, cross-site scripting is only one of the common types of hack attacks (like SQL injection attacks) on WordPress sites. Hackers have plenty of tricks up their sleeves. It’s best to implement an all-round security solution on your website to prevent cross-site scripting attacks along with all other types of WordPress attacks.
We recommend installing a reliable WordPress security plugin like MalCare on your site for regular security testing. It comes with a security scanner or a web vulnerability scanner that scans and monitors your site while preventing hackers from accessing it. It also enables you to take site hardening measures to make your website more secure. You can run your website with peace of mind knowing it’s secured.
Category:
Share it:
You may also like
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…

MalCare Proactively Defends Against Icegram Express SQL Injection Vulnerability
MalCare’s recent data has revealed numerous attempts to exploit a newly found SQL injection vulnerability in the Icegram Express plugin. Attackers commonly use this sophisticated SQL injection technique to extract…

Atomic Security’s Deep WordPress Integration Helps Protect Against Core XSS Vulnerability
The recent WordPress core vulnerability is a critical one, primarily because of two reasons. Firstly, it affects the WordPress core itself, which means that every WordPress site is vulnerable to…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








