How to Configure the X-Content-Type-Options Header in WordPress
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

Securing your WordPress site is non-negotiable in an age where digital threats are evolving rapidly. Key players in your security lineup are HTTP security headers, and a star defender is the X-Content-Type-Options (XCTO) header.
Configuring the XCTO header is a simple yet effective tactic that helps fortify your WordPress site’s defenses with just a few tweaks under the hood, ensuring that browsers respect the content type as served. If that doesn’t make a lot of sense right now, don’t worry, we’ll explain.
TL;DR: The X-Content-Type-Options header is a security measure for WordPress sites to prevent MIME-type sniffing by browsers. Setting it to “nosniff” helps ward off certain types of attacks. However, this header is only a piece of the overall security puzzle. To safeguard your website fully, pair it with MalCare’s robust firewall, malware detection and removal feature, and strong bot protection capabilities.
What is the X-Content-Type-Options header in WordPress?
The X-Content-Type-Options header is like a strict teacher in WordPress that tells your web browser to follow the rules and not guess what type of content (scripts, images, audio, etc.) it’s getting, also known as MIME-type sniffing. It prevents the browser from making mistakes about what to do with the data it receives. It’s a simple directive that comes with a powerful punch—set the header to “nosniff” and you effectively block the browser from falling prey to attacks that exploit MIME-type sniffing.
Knowing about and implementing this header is crucial for WordPress site owners because it safeguards against certain types of attacks. For example, it can prevent cross-site scripting (XSS) attacks, where a browser’s incorrect guess about a file’s content type could be exploited to execute malicious scripts. By enabling the XCTO header, you’re reinforcing your site’s defenses and maintaining a more secure user environment.
Check your WordPress site for X-Content-Type-Options configuration
Before you begin configuring your WordPress site for the XCTO HTTP header, it would be wise to check whether your site already has it set up. To do so, head over to the Security Headers website and run your website on its Scan box. The results will show you whether XCTO is configured on your site, along with a host of other security headers and their statuses.
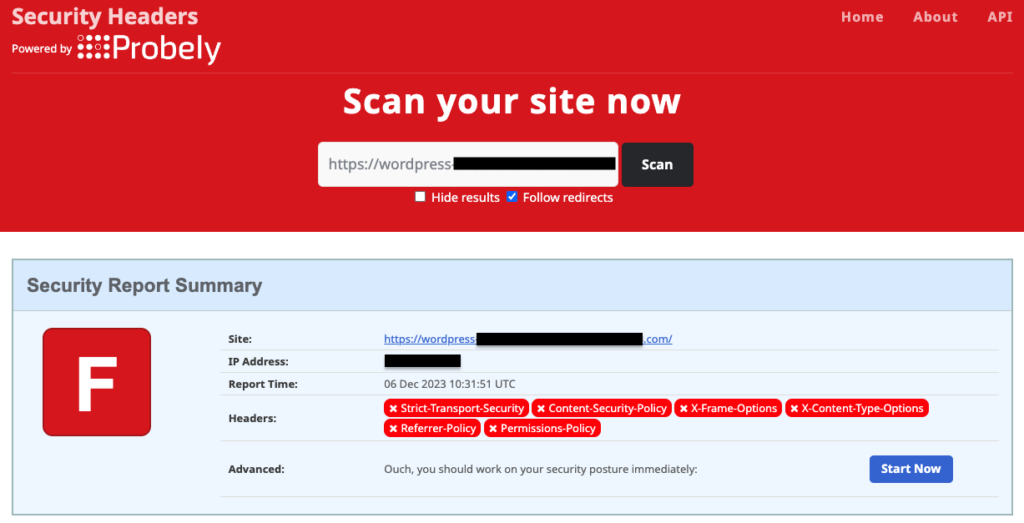
In case your WordPress site does not have the XCTO header configured, you can do so either by using a plugin like HTTP Headers or by editing the .htaccess file.
1. Configure X-Content-Type-Options in WordPress using a plugin
Using a plugin is an easy and quick way to configure your WordPress site to use the XCTO header. There are several reputed plugins available in the WordPress marketplace, like AIOSEO, that can help you do this. However, most of them require a paid version or subscription to access these and additional features.
If you wish to use a free plugin, HTTP Headers by Dimitar Ivanov is our go-to choice. It has a simple yet powerful interface that does the job and more. Whether you are a newbie to WordPress or a power user, you will find HTTP Headers very convenient to configure XCTO and other headers.
Here are the steps to configure XCTO on your WordPress site using HTTP Headers:
- Install and activate the plugin: From your WordPress admin dashboard, hover your mouse pointer over Plugins and click on Add New Plugin. Use the search box to find HTTP Headers, and then install and activate the plugin.
- Find the XCTO control on the HTTP Headers dashboard: Hover your mouse pointer over Settings and click on HTTP Headers. This will take you to the plugin dashboard. Click on Security and you will find the X-Content-Type-Options control therein.
- Modify the XCTO control: The XCTO option will be off by default since your site is not configured to use the XCTO header.

To change it, click on Edit, and then click on the On checkbox. You do not need to change the ‘nosniff’ option as there are no other options available. Click on Save Changes and you are done!
You can head back to Security Headers and scan your website again, which should show the updated header configuration. In case it does not, clear the browser cache and retry scanning after some time.
2. Configure X-Content-Type-Options in WordPress by editing the .htaccess file
Editing the .htaccess file is another way to configure your WordPress site to use the XCTO header if you are experienced in modifying system files and are not averse to taking some risks. Now, because .htaccess is a system file, we recommend creating a backup of your site using BlogVault before editing it. BlogVault takes a full backup of your site, including site files and database. Plus the backups are stored offsite, so even if there is an inadvertent error that crashes your site, you can restore in minutes with a BlogVault backup.
Once you have backed up your site, let’s look at how to edit the .htaccess file.
Please note that the .htaccess file is a server configuration file, and even spaces are important. Be very careful to copy exactly the code we have shown below.
A. Edit .htaccess file using an FTP client
For this step, you will need to use an FTP client and obtain your FTP credentials from your web host dashboard or by contacting your web host’s support. We prefer using Filezilla as our FTP client.
- Log in to your site: On the Filezilla window, enter your IP address, user name, password, and port number (if any), and click on Quickconnect.
- Locate the .htaccess file: On the right-side pane, double-click on your root folder to open it. In our case, it was the public_html folder. Once opened, find the .htaccess file. As it is a hidden file, you may need to enable this option in the settings of your FTP client.
- Edit the .htaccess file: Right-click on the .htaccess file and click on View/Edit. This will use your system’s default text editor to open the file. Add the following lines of code to it before the file ending:
<ifModule mod_headers.c>
Header set X-Content-Type-Options nosniff
</ifModule>- Save and re-upload the .htaccess file: Enter Ctrl+S for Windows or Command+S for MacOS to save the file. Closing the text editor window brings a pop-up box that asks you if you want to re-upload the file to your website and replace the original with it. Click on Yes.
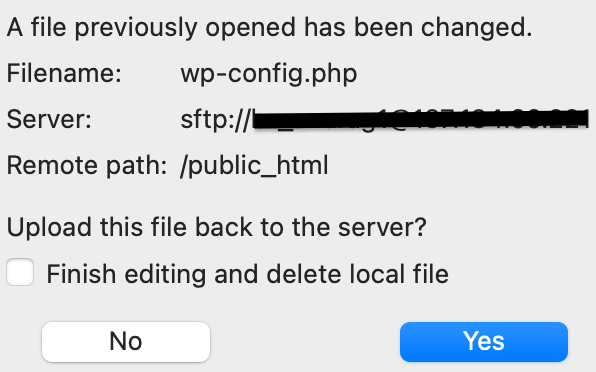
B. Edit .htaccess file using the cPanel File Manager
If your web host uses cPanel for site administration, you can use the built-in File Manager to edit the .htaccess file.
- Log in to cPanel: Access the dashboard using your WordPress site’s cPanel credentials.
- Locate the .htaccess file using File Manager: In the Files section, click on File Manager to open your site’s file structure in a new window. On the left pane, open the root directory. You will find the .htaccess file here, provided you have enabled viewing hidden files.
- Edit the .htaccess file: Right-click on the .htaccess file and click on Edit. Click on Edit again in the pop-up window to open the file in a new window. Add the following lines of code to it, just before the end of the file:
<ifModule mod_headers.c>
Header set X-Content-Type-Options nosniff
</ifModule>- Save the .htaccess file: Click on Save Changes in the top-right corner of your window and you are done.
C. Edit .htaccess file using SSH
You can use Command Prompt (for Windows) or Terminal (for MacOS) to edit the .htaccess file using Secure Shell (SSH). This is a more technical method than the previous two so be careful when using it.
- Connect to your site using SSH: Using either Command Prompt or Terminal, connect to your WordPress site by entering the following command:
ssh username@ipaddressHere, username and ipaddress can be replaced by the correct details that can be obtained from your web host’s dashboard. You will be prompted to enter your password upon entering the above command.
- Locate the .htaccess file: By default, you should be logged in to your site’s root directory, which, in our case, is public_html. In case you are not, navigate to the required directory by entering the following command:
cd directory_namewhere directory_name can be replaced by your directory.

Once inside a directory, list all the files within it by entering the following command:
ls -a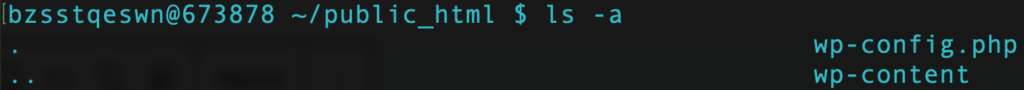
You should be able to locate your .htaccess file here.
- Edit the .htaccess file: Enter the following command to open the .htaccess file using the Vmacs file editor:
vi .htaccessHit i to enter edit mode and add the following lines of code to it:
<ifModule mod_headers.c>
Header set X-Content-Type-Options nosniff
</ifModule>- Save the .htaccess file: Hit Esc and enter :wq to save the file and exit the Vmacs editor.
Potential issues and how to troubleshoot them
When configuring the XCTO HTTP header in WordPress, you might encounter a few hiccups. These issues can typically be resolved with some troubleshooting.
Incorrect Configuration: If you’ve manually edited your .htaccess file and noticed your site behaving unexpectedly, double-check the syntax.
Multiple Headers: Sometimes plugins or server settings can add duplicate headers. This can conflict with or override your settings. Check the .htaccess file and ensure there’s only one XCTO header present.
Not Reflecting Changes: After setting the header, if it doesn’t appear to take effect, clear the website cache. Some caching plugins or server-side caching might store an old version of the site without the header.
Importance of HTTP headers in WordPress
Using HTTP headers thoughtfully is crucial for maintaining a secure and efficient WordPress site. They are not just a technical detail but a necessity for a safer web experience.
- Enhanced Security: HTTP headers in WordPress can increase security. They help fight against common threats like cross-site scripting (XSS) and code injections.
- Faster Loading: Proper caching headers control the browser cache. They make your site faster by reducing load times.
- Prevent Content Sniffing: Headers prevent browsers from guessing MIME types. It stops malicious content from executing.
- Protection From Clickjacking: Headers also prevent your site from being displayed in a frame or iframe. This action can block clickjacking attacks.
- Data Encryption: Headers also force browsers to only use HTTPS. It ensures all data is encrypted during transit.
- Ensure User Privacy: Headers can control the amount of information sent with requests, thereby ensuring only critically relevant information is passed.
Proper use of HTTP headers can lead to a more secure, performant, and reliable WordPress site. It’s key to manage them effectively for the best outcomes.
What is MIME-type sniffing?
MIME-type sniffing refers to the process by which a web browser examines and attempts to determine the actual content type of a downloaded document. This can happen when the server sends resources with an ambiguous or incorrect content-type HTTP header. Browsers analyze the content’s bytes to “sniff out” what type of file it might be—whether it’s HTML, CSS, JavaScript, or any other media type like image, audio, video, etc. This capability is designed to be helpful, ensuring that content is handled correctly even if the server does not properly label it. However, it can potentially expose security vulnerabilities.
The risk with MIME-type sniffing arises when an attacker manipulates this behavior to execute malicious code on a user’s browser. For example, an uploaded file with a misleading extension or MIME type could be interpreted and executed as a script rather than displayed as plain text. This loophole provides an avenue for XSS attacks, where harmful scripts are run in a user’s session. To safeguard against these threats, web developers use the XCTO HTTP header with the value ‘nosniff’, instructing modern browsers to disable MIME-type sniffing and strictly adhere to the server’s declared content type.
Implementing HTTP headers is not enough for your WordPress site’s security
Comprehensive security measures are essential for a secure WordPress site. HTTP headers are a part of it, but not the whole picture. Here are some other ways to secure your site:
- Keep WordPress, themes, and plugins updated. Updates fix security holes and add new features.
- Apart from using complex passwords, add two-factor authentication and limit login attempts to form an extra layer of security that protects your site against brute-force attacks.
- Install security plugins like MalCare. Its robust firewall, malware scanning and removal feature, as well as bot protection capabilities, ensure your WordPress site remains secure at all times.
- Regularly back up your site using a WordPress backup plugin like BlogVault. It quickly backs up your site to a secure location and helps restore it quickly in case something goes wrong.
- Assign appropriate roles to users and limit their access to only what’s necessary.
- Set strict file permissions to prevent unauthorized access to your files.
Final thoughts
Configuring the X-Content-Type-Options header on your WordPress site is a significant step towards safeguarding against MIME-type security risks. However, it’s crucial to understand that tweaking HTTP headers should be part of a broader, more comprehensive security strategy. Ensuring your HTTP headers are properly configured is a strong move, but it doesn’t make your site impervious to all vulnerabilities.
For total security coverage, integrating a robust security plugin like MalCare into your WordPress site is a proactive measure that goes well beyond HTTP headers. MalCare offers a powerful firewall, easy one-click malware removal, as well as strong bot protection. Moreover, its user-friendly setup doesn’t require any technical expertise, and the peace of mind it provides is invaluable. Don’t leave your site’s security to chance—consider getting MalCare today to ensure your WordPress site remains safe, secure, and running smoothly.
FAQs
Why is setting the X-Content-Type-Options header important?
Setting the X-Content-Type-Options header to nosniff prevents browsers from trying to ‘sniff’ and execute the wrong MIME type. This can, in turn, prevent major security issues like cross-site scripting (XSS) attacks.
Can setting HTTP headers break my site?
HTTP headers can cause issues If you incorrectly configure them in the .htaccess file. This is why we recommend that you always back up your site using a WordPress backup plugin like BlogVault before making any changes. This ensures that you can recover your site in case you make an error.
Is configuring HTTP headers all I need for WordPress security?
No. Configuring HTTP security headers is just one part of a multi-layered security approach for your WordPress site. Using comprehensive security plugins like MalCare, ensuring strong login security, regularly backing up and updating your site, etc. are some of the most common ways to keep your site secure.
What other security headers should I consider for my WordPress site?
Apart from the X-Content-Type-Options header, you can also configure headers like Content Security Policy (CSP), HTTP Strict-Transport-Security (HSTS), Referrer-Policy, etc. Together, they ensure your WordPress site is secure against various issues. However, remember to complement these measures with a security plugin like MalCare for a complete security regimen for your site.
Is configuring the `X-Content-Type-Options` header a one-time task?
Yes. Once set, the X-Content-Type-Options header generally doesn’t need to be changed unless your site’s security requirements change. Even then, it is a fairly simple process to modify it, which can be done either by using a plugin or by editing the .htaccess file.
How do I turn off content sniffing?
To turn off browsers’ content sniffing on your WordPress website, you have to set its X-Content-Type-Options HTTP header to ‘nosniff’. This can be done either by using a plugin like HTTP Headers or by editing the .htaccess file for your site.
What does nosniff mean?
The ‘nosniff’ parameter of the X-Content-Type-Options HTTP header instructs browsers to ‘not sniff’ for MIME-types on a WordPress site. Browsers perform MIME-type sniffing to understand the type of content when it has been served by the website with ambiguous or unclearly defined content types.
How do I add a content security policy to WordPress?
You can add a content security policy to your WordPress site by configuring the Content-Security-Policy HTTP header. It has multiple directives like default-src, script-src, img-src, etc., each with its own set of values, that you can set as per your site’s security requirements.
Category:
Share it:
You may also like
Fix Pharma Hack on WordPress and SEO
Pharma hack is a prolific malware that redirects visitors from your site to an online pharmacy that sells Viagra, Cialis, Levitra, Xanax, Tadalafil, and other drugs. It also shows up…
How To Protect Your WordPress Website From File Upload Vulnerability?
One of the core strengths of WordPress lies in its file upload functionality. The ability to seamlessly upload and integrate various types of files, from images and documents to multimedia…

MalCare Ensures Unmatched Protection Against User Registration Privilege Escalation Vulnerability
Imagine discovering that your WordPress site, which should be secure and under strict control, has suddenly become accessible to unauthorized users who have the same administrative powers as you. This…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








