How to Fix wp-feed.php & wp-tmp.php Malware in WordPress?
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

Is your malware scanner detecting a hacked WordPress site with no visible signs?
Are visitors complaining about spam ads that you can’t see? If so, your site may have fallen victim to the wp-feed.php malware.
Scan your site immediately to figure out if this is the case.
This hidden hack displays illegal product, drug, or adult content ads to visitors while remaining unnoticed by site owners. It’s one of the more cleverly disguised hacks and therefore removing it can be challenging.
In this article, we will uncover how this malware operates, provide preventive measures, and guide you through the process of clearing it from your WordPress site.
TL;DR: Scan your site to find if the wp-feed.php malware is on your site. Because the malware adds spam ads to your pages that are only visible to new users or visitors, it is super difficult to find without a great scanner. MalCare is the best way to detect and remove this persistent malware. Additionally, the firewall protects against future attacks, so wp-feed can’t come back.
What is the wp-feed.php malware?
The wp-feed.php malware is a pernicious malware that infects WordPress sites by masquerading as legitimate core files. A site infected with wp-feed.php looks entirely normal to the site admin and logged-in users, but is designed to display spam content or redirect visitors to harmful websites, compromising the user experience and potentially exposing visitors to security risks.
⚠️ The only way to definitively find malware on a site is to scan it. Malware scanners look for malware in every corner of the site, right from the core files to every row of the database. If you suspect your site is hacked, this is your most critical step to getting your site back.
Malware like this typically finds its way onto a site through the use of nulled plugins and themes. There are a few variants of this malware that target WordPress sites, such as wp-tmp.php, wp-vcd, helad.php, wp-best-feed.php, and admin_ips.txt. These files are often used by hackers to gain unauthorized access and control over a website.
Step 1: Remove wp-feed.php malware
As we said before, wp-feed.php is a particularly stubborn malware to remove. Once a site is infected with the malware, it spreads to many of the core WordPress folders, like wp-includes and wp-admin. Therefore, if you find and remove just the wp-feed.php file, chances are that you are cleaning only a fraction of the infection. Soon, the malware is back in full force, and you are back to square one.
There are 3 main ways to remove malware from a WordPress site. We’ve talked about all 3 in the order of effectiveness.
Option 1. Use a security plugin
The best method to effectively remove the wp-feed malware from your WordPress site is to use a security plugin like MalCare. MalCare is a best-in-class WordPress security plugin, which will scan every inch of your site for hacked files. Many scanners cannot scan the core files or identify malware in the database. MalCare does both very well, and you will have a definitive answer as to whether your site is hacked or not.

Once you have a result, you can use MalCare’s one-click malware removal to deal with the hack. It will surgically remove the malware from hacked files, leaving your site pristine as it should be.
We recommend using MalCare because it is the best malware removal and it works fast. Malware gets worse the longer it is left unaddressed on a site, and wp-feed.php is a poster child for this behavior.
Option 2. Hiring a removal service
If your web host has detected the malware on your site, they may have suspended your site. Web hosts are sensitive to malware on their servers, because it affects their reputation and other customers. So they are quick to take hacked sites offline to limit the liability and damage.
In the event you do not have access to your site, you can opt for a WordPress maintenance service. These are professionals who develop and maintain WordPress sites. They possess the expertise and tools to effectively identify and eliminate malware from your site. However it’s important to note that they may not be quick or affordable. You may be stuck in a queue of worried customers for hours and their skill set comes with a price tag.
Option 3. Manual removal of malware (NOT RECOMMENDED)
Manual malware removal is the least efficient option among the available methods. It is a time-consuming and challenging process that demands significant technical expertise. Moreover, manual removal can be unreliable, as even after a seemingly thorough cleanup, there remains a possibility of hidden malicious code lingering within your website.
Finally, and most importantly, manual malware removal is dangerous. The wp-feed.php malware—and its variants—primarily infect the WordPress core files and folders, including the active theme files. If any errors are made during the cleanup process, the site will crash. So if you want to undertake manual malware removal, we strongly recommend having WordPress development expertise as a prerequisite.
- Backup your website: The first step is to prioritize the safety of your website by taking a full backup. This crucial step ensures that you have a restore point readily available in case any issues arise during the cleanup process. By proactively backing up your WordPress site, you can proceed with confidence, knowing that you have a copy of your website’s data and settings to fall back on if needed. You should also take a copy to clean your site. The copy is what you will scan for malware.
- Download clean versions of WordPress core, themes, and plugins: Download clean versions of the WordPress core, themes, and plugins installed on your site. Check the versions, and make sure to download only those versions from official sources or the repository.
- Reinstall WordPress core: With the clean versions of the WordPress core, the next step in the manual malware cleanup process is to reinstall the core files.
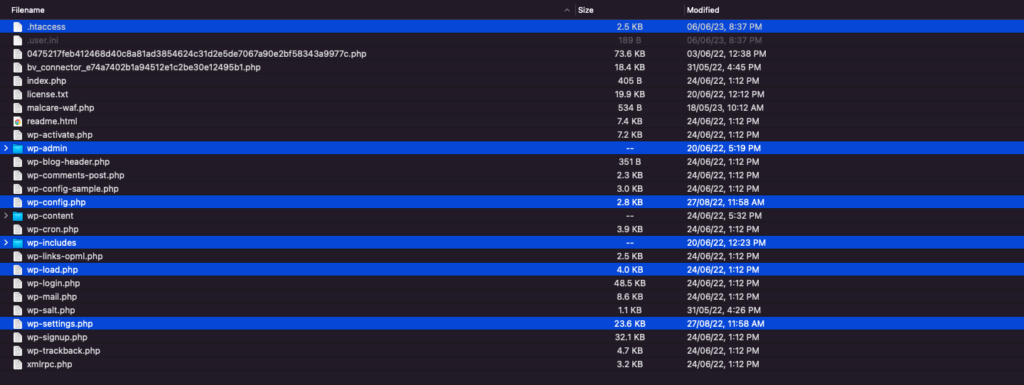
You will need to access your files using cPanel or an FTP client like Cyberduck. The core folders are generally in the root folder, which can vary from site to site. In our case, our core files were in the public_html folder. Replace the wp-admin and wp-includes folders using cPanel or SFTP to ensure a fresh start. These folders rarely have custom code, so you can replace them entirely. The wp-feed hack files, like wp-tmp.php or helad.php are often found in the wp-includes folder, so if you find them, you can rest assured your site is hacked.
Then, carefully examine key files like index.php,’ wp-config.php, wp-settings.php, wp-load.php, and .htaccess for any signs of malware. Remove any suspicious or unfamiliar code found within these files. Additionally, check the wp-uploads folder for any PHP files and delete them promptly.
- Clean themes and plugins: Compare the clean versions with the infected versions from your site. You should look for code that seems out of place or is malicious. Remember that, not all discrepancies are bad; it could just be customization.
- Remove all backdoors: The next step is to conduct a thorough search within your website’s files for common backdoor keywords such as eval, preg_replace, and similar terms. These functions are used to manipulate strings, and therefore hide malware. The functions themselves are legitimate, and can be used for real features on a site. However, they are more often associated with backdoors. Locate these code snippets, ascertain if they are malicious, and, if they are, delete them.
- Clean malware from database tables: Now that the site files are malware-free, we turn our attention to the database. Log into your database management system; which in most cases is phpMyAdmin. Check all the tables for suspicious content, focusing especially on wp_options and wp_posts. Unfortunately, since malware can take almost any form, there is no foolproof way to identify malware. It requires developer knowledge.
- Reupload cleaned files: After you’re done clearing everything, utilize cPanel or SFTP to reupload the files, similar to the process of manually restoring a backup. Ensure that you are using the clean versions of the WordPress core, themes, and plugins. By reuploading these clean files, you can overwrite any potentially compromised or infected files that were removed during the cleanup process. Do the same for the database as well, using phpMyAdmin. You will need to drop the existing database, and import the clean one in its place. This is an understandably fraught exercise, which is why we recommend backups at the outset.
- Clean the cache: The cache stores temporary data and files, including previous versions that may have been infected with malware. By clearing the cache, you eliminate the risk of serving compromised content to your visitors.
- Verify each plugin and theme: To ensure the security and stability of your WordPress site, it is recommended to disable all plugins and themes after malware removal, and then reactivate them one by one. By systematically enabling each plugin and theme individually, you can closely monitor your website for any unexpected changes or broken functionality. . If you do discover something is not working as it should, you may have deleted custom code thinking it was malware. Maybe only a part of it was malware, so be careful when replacing the custom code into your cleaned site.
- Use a security scanner to confirm: As a final check, we highly recommended performing a comprehensive scan using MalCare. It is the last step in ensuring that your site is squeaky clean.
🚨 Identifying and removing malicious code requires a thorough understanding of coding practices and cybersecurity. There is no definitive blueprint or library for malicious code and therefore it is crucial to have solid coding experience before attempting a task of this scale.
Even with development experience, the process can be complex, time-consuming, and unreliable, potentially leading to unintended consequences or incomplete removal of malware. Once again, the best option is to use MalCare, a tried-and-tested malware scanning and removal plugin.
Step 2. Protect your site from future attacks
Protecting your WordPress site from potential malware infections and hacking attempts requires proactive measures. By implementing preventive measures, like having a scanner that checks your site daily, you can significantly reduce the risk of compromise and ensure the long-term security of your website. In this section, we will discuss key preventive measures that can help safeguard your WordPress site against malware and vulnerabilities.
- Install a comprehensive security plugin
One of the most effective ways to enhance the security of your WordPress site is by installing MalCare, a reputable security plugin. MalCare has essential security features. The scanner finds the most stubborn malware, the one-click auto-removal feature is easy to use, and the sophisticated firewall blocks threats seamlessly.
- Use only legitimate versions of themes and plugins
Avoid using nulled versions of themes and plugins, as they often contain hidden malware or compromised code. Stick to legitimate sources for acquiring themes and plugins, such as official marketplaces or reputable developers’ websites. Legitimate themes and plugins undergo rigorous security checks and regular updates, reducing the risk of vulnerabilities and malware infiltration. Consider investing in premium versions of software to ensure that you receive timely updates and reliable support from the developers.
- Choose reputable plugins and themes
Opt for plugins and themes that are developed by reputable and trustworthy sources. Select options that have a strong track record, positive user reviews, and are actively maintained by their developers. Reputable developers regularly release updates to address vulnerabilities, improve functionality, and maintain compatibility with the latest version of WordPress. By using well-established plugins and themes, you minimize the likelihood of security gaps and ensure a more secure website environment.
- Keep your WordPress site updated
Regularly updating your WordPress core, themes, and plugins is essential for maintaining a secure website. Updates often include security patches, bug fixes, and enhancements that address known vulnerabilities.
Since updates can sometimes be a cause for concern due to potential conflicts or disruptions to your site, we recommend creating a staging environment to test updates before applying them to your live site. This approach allows you to identify and resolve any compatibility issues or conflicts in a controlled environment, reducing the risk of unintended disruptions while ensuring your site stays up to date with the latest security measures.
How did your site get infected?
So, how does a site get infected in the first place? Although WordPress websites are frequently targeted by hackers due to their popularity and open source nature, it is arguably one of the more secure CMSes available.
Hacking through the use of nulled plugins and themes
Nulled plugins and themes are pirated versions of a premium plugin or theme that are provided by a third party site. These modified versions of premium software are distributed for free, but often come bundled with malware. Many users are tempted by the allure of accessing premium features without paying, but by installing nulled plugins and themes, they unknowingly open their websites to potential hacks.
Exploiting vulnerabilities in plugins and themes
Hackers are constantly on the lookout for vulnerabilities in plugins and themes. These vulnerabilities may arise due to coding errors, outdated versions, or improper configurations. Once a vulnerability is discovered, hackers exploit it to gain unauthorized access to websites. They can inject malicious code, create backdoors for future attacks, or even take control of the entire site. It is crucial for website owners to regularly update their plugins and themes to patch any known vulnerabilities and minimize the risk of exploitation.
The wp-feed.php malware targets the wp-includes folder, which is a core WordPress folder that developers rarely modify. Once the malware gains a foothold in the wp-includes folder, it can quickly propagate to other directories and files, making it challenging to eradicate manually. Due to its ability to infect critical components of WordPress and hide from the admins, the wp-feed.php malware is an exceptionally persistent hack.
What is the impact of the wp-feed.php malware?
So, it’s a hard malware to find. It’s a hard malware to remove. Is it worth the effort? Yes. It definitely is. Here are some ways that it negatively impacts your site:
Final thoughts
The impact of the wp-feed.php malware can be immense, posing significant risks to your website’s traffic, revenue, and overall online presence. To safeguard your WordPress site effectively, it is crucial to employ robust preventive measures.
One of the most reliable and comprehensive solutions available is MalCare. With its powerful features, including a firewall, malware scanner, and one-click malware removal, MalCare provides an effective defense against malware attacks. By implementing MalCare as your preventive measure, you can proactively protect your website, mitigate risks, and ensure the uninterrupted growth and success of your online venture.
FAQs
How do I remove wp-feed.php and wp-tmp.php malware in WordPress?
To remove the wp-feed.php and wp-tmp.php malware from your WordPress site, first scan your website using a reliable security plugin like MalCare to detect and identify the malware. Once the malware is detected, use the plugin’s built-in malware removal feature to safely remove the infected files.
How do I remove malware from WordPress?
Removing malware from WordPress involves the following steps:
- Scan your website using MalCare to identify the infected files.
- Once the malware is detected, use the malware removal feature to clean your site.
What is PHP malware?
PHP malware refers to malicious code or scripts written in PHP programming language that are injected into websites to perform harmful actions. This type of malware can be used to steal sensitive information, redirect visitors to malicious sites, display unwanted ads, or gain unauthorized access to a website. PHP malware often exploits vulnerabilities in outdated software, weak passwords, or insecure server configurations. Regular security monitoring, updates, and strong security measures can help mitigate the risks associated with PHP malware.
What is WP VCD PHP?
wp-vcd.php is a well-known malware variant that specifically targets WordPress sites. It typically disguises itself as a WordPress plugin called “wp-vcd” and infects websites through nulled or pirated plugins and themes. The malware can inject spam links, display unwanted ads, redirect visitors to harmful websites, or compromise the security of the infected site. It is crucial to regularly update themes, plugins, and the WordPress core, and use only legitimate and reputable sources for plugins and themes to prevent infections.
How do I check for malware on my WordPress site?
You can check for malware on your WordPress site using the following methods:
- Use a reliable security plugin like MalCare, which offers malware scanning and detection features.
- Monitor your website for unusual behavior, such as unexpected redirects, strange pop-ups, or changes in site content.
- Regularly review your website’s access logs and server logs for any unusual or suspicious activity.
Share it:
You may also like

MalCare Ensures Unmatched Protection Against User Registration Privilege Escalation Vulnerability
Imagine discovering that your WordPress site, which should be secure and under strict control, has suddenly become accessible to unauthorized users who have the same administrative powers as you. This…

MalCare Ensures Proactive Protection Against WP-Members XSS Vulnerability
MalCare continues to protect its customer sites from all kinds of attacks, even the ones exploiting zero-day vulnerabilities. The recent stored cross-site scripting (XSS) vulnerability found in the WP-Members Membership…
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








