MalCare Proactively Defends Against Icegram Express SQL Injection Vulnerability
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

MalCare’s recent data has revealed numerous attempts to exploit a newly found SQL injection vulnerability in the Icegram Express plugin. Attackers commonly use this sophisticated SQL injection technique to extract data from vulnerable databases.
This vulnerability is particularly dangerous because it’s easy to attack—no special permissions or user roles are needed. This means that even if you lock down user accounts or manually review each user registration, hackers can still exploit this vulnerability to gain access to your site.
Notably, MalCare’s Atomic Security has effectively shielded sites from these attacks even before the vulnerability was publicly known. Unlike many WordPress firewall providers, MalCare blocked these attacks proactively, without requiring a virtual patch. This ensured immediate and robust protection for sites guarded by MalCare, giving the admin time to safely update the plugin without the fear of compromise.
What is the Icegram Express plugin vulnerability?
Plugin information
- Vulnerable plugin version: v5.7.14 and earlier
- Patch release version: v5.7.15 and newer
Icegram Express, also known by its full name as Email Subscribers by Icegram Express, is a WordPress email marketing tool. It helps in building user lists and sending newsletters and targeted emails. With over 90,000 active installs, it is one of the popular email marketing tools in the WordPress ecosystem.

About the vulnerability
The Icegram Express vulnerability is caused by an improper implementation of SQL queries in versions up to and including v5.7.14, thereby allowing data extraction via SQL injection. It doesn’t properly escape user-supplied inputs or adequately prepare the SQL queries, allowing unauthenticated attackers to insert extra SQL commands into existing queries. These commands could potentially be used to access sensitive information from the database. Consequently, this vulnerability has received a CVSS score of 9.8 (Critical).
Specifically, the maybe_apply_bulk_actions_on_all_contacts() function in the Email_Subscribers_Admin class contains the vulnerability. This function queries the subscribers from the database using the IG_ES_Subscribers_Query class. The run() function that queries the database contains the following code snippets:
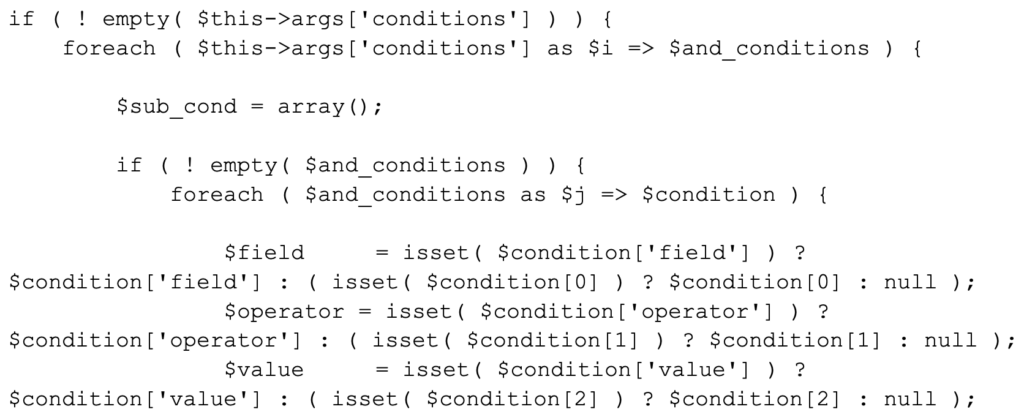
The function builds a complex query. In such a case, escaping the parameters with the esc_sql() function would be a suitable solution. Unfortunately, this is missing in the vulnerable version.

The JOIN statement is added to the query without the WordPress wpdb prepare() function.
Ideally, the prepare() function would parameterize and escape the SQL query for safe execution in WordPress, thereby providing protection against SQL injection attacks.
Since UNION-Based SQL injection is not possible due to the structure of the query, an attacker would need to use a time-based blind approach to extract information from the database.
This means that they would need to use SQL CASE statements along with the SLEEP() command while observing the response time of each request to steal information from the database.
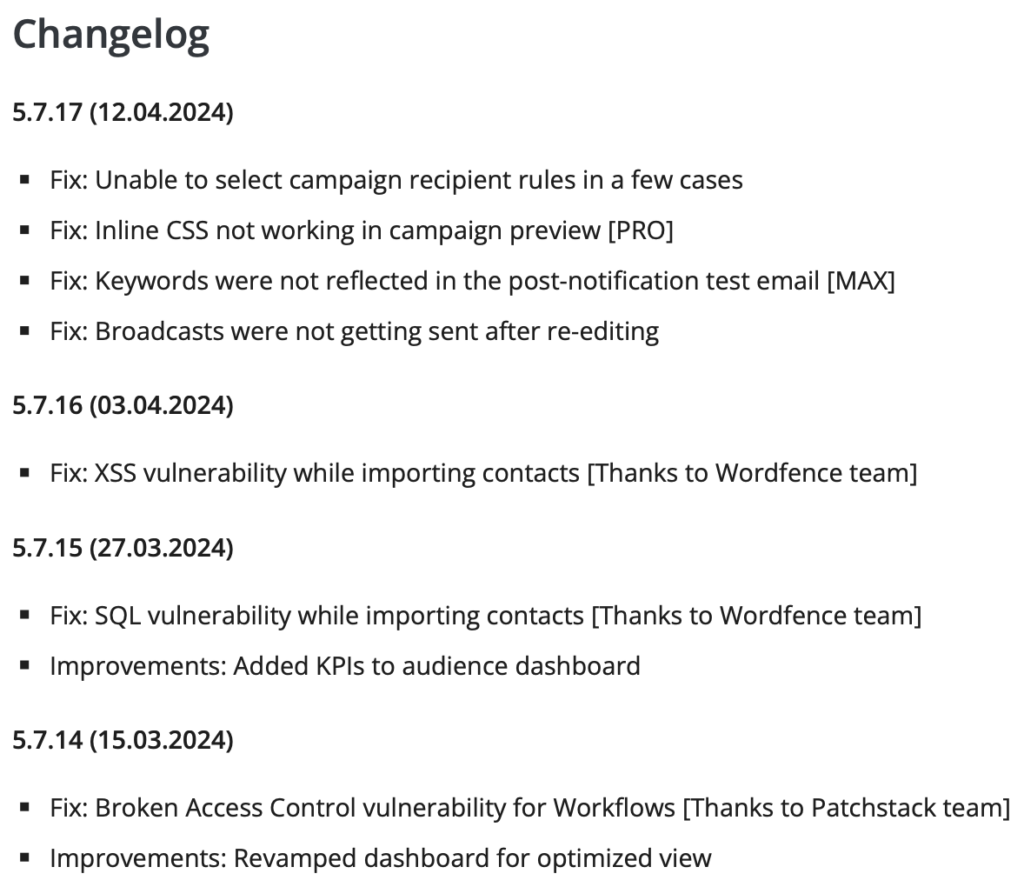
The vulnerability has now been fixed with the release of Icegram Express v5.7.15 on March 27, 2024.
Who discovered this vulnerability?
The SQL injection vulnerability in Icegram Express was identified by independent WordPress security researcher Arkadiusz Hydzik and reported through Wordfence’s Bug Bounty Program. After being alerted by Wordfence on March 25, 2024, the developers at Icegram released a patch for the issue on March 27, 2024.
How is your WordPress site at risk?
Your WordPress site is at risk if it runs the Icegram Express plugin v5.7.14 or earlier.
Hackers constantly search for vulnerabilities to exploit, including SQL injection flaws in WordPress plugins like LayerSlider. Here are some ways they might exploit such weaknesses:
- Extracting sensitive data: Through SQL injection, hackers can retrieve sensitive details from the WordPress database, such as user profiles, email addresses, and passwords. Even hashed passwords could be targeted for cracking, along with other personal data on the site.
- Modifying database information: Beyond data theft, attackers can manipulate database information. This includes altering product prices in an online store, changing user roles (upgrading a user to an admin), or embedding malicious content in posts or pages.
- Website defacement: SQL injection allows hackers to replace website content with their own, often to spread specific messages or simply demonstrate their hacking capabilities.
- Denial of service: The objective might sometimes be to disrupt service. Attackers can delete essential data or overload the database through manipulated SQL queries, causing the website to crash.
- Planting backdoors: Using SQL injection flaws, hackers can insert backdoors into the WordPress site. These backdoors provide persistent backend access, even after the original vulnerability is resolved.
Hence, we strongly recommend you update the Icegram Express plugin on your WordPress site immediately, at least to v 5.7.15.
What are the symptoms of a hacked site?
If you have reason to suspect that your WordPress site might have fallen victim to attacks exploiting this vulnerability, check for:
- a record in your site’s activity logs containing the path /wp-admin/admin-post.php
- a query string in your site’s database logs containing advanced_filter
The presence of this path and query string together could mean that your site is compromised. Take immediate action to update the Icegram Express plugin and scan and clean your site using MalCare.
How to clean your site?
When your WordPress site is compromised, it’s crucial to remain calm. Follow these steps to recover and enhance your site’s security:
- Initiate a MalCare scan: Install MalCare to remove any malware swiftly and boost your site’s defense against future threats with its Atomic Security feature.
- Update plugins and themes: Frequently update your plugins and themes. These updates help fix vulnerabilities which hackers might exploit. MalCare’s dashboard helps by notifying you of any outdated plugins and themes, aiding in their management and further securing your site.
- Refresh WordPress salts and security keys: This action logs out all users and terminates all active sessions, significantly enhancing site security. MalCare includes this feature in its cleanup process.
- Review user roles and permissions: Examine all user roles and permissions. Any discrepancies should lead to immediate revocation of access.
- Change login details: Promptly update your admin password. Ensure all users are logged out, prompt them to change their passwords, and encourage the use of strong, new passwords.
- Strengthen login security: Implement two-factor authentication (2FA) and limit login attempts to minimize the risk of unauthorized access.
- Monitor your site: Leverage MalCare’s monitoring capabilities. It continuously scans for unusual activities and potential threats, keeping your site secure.
How does MalCare protect your site?
MalCare provides robust security features for your WordPress site, including:
- Quick malware detection and cleanup: MalCare conducts daily scans for malware automatically. If any threats are detected, its efficient removal tool swiftly eliminates them, restoring your site’s safety and health.
- Strong firewall protection: MalCare includes Atomic Security, a sophisticated firewall that monitors incoming traffic and blocks malicious attacks. It continuously updates to protect against the latest security threats.
- Vulnerability notifications: MalCare continuously monitors your plugins and themes for potential vulnerabilities. If any risks are identified, it promptly alerts you, allowing you to fortify your site’s defenses.
- Bot defense: MalCare recognizes the impact of bots on site performance and has robust measures in place to deter these automated threats, ensuring smoother site operation.
- Efficient backups: MalCare’s automated, offsite backup system keeps your data safe, providing a quick recovery solution in case of any issues.
MalCare envelops your WordPress site with multiple layers of protection, employing proactive and robust defenses to secure your online presence.
Category:
Share it:
You may also like

MalCare Stands Strong Against WP Activity Log Premium SQL Injection Vulnerability
A significant SQL injection vulnerability was identified in the WP Activity Log Premium plugin, a popular tool for tracking user activity on WordPress sites. An SQLi vulnerability poses a serious…
Fix Pharma Hack on WordPress and SEO
Pharma hack is a prolific malware that redirects visitors from your site to an online pharmacy that sells Viagra, Cialis, Levitra, Xanax, Tadalafil, and other drugs. It also shows up…
How To Protect Your WordPress Website From File Upload Vulnerability?
One of the core strengths of WordPress lies in its file upload functionality. The ability to seamlessly upload and integrate various types of files, from images and documents to multimedia…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








