How to Protect Against WordPress SQL Injections
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

SQL injections are some of the most devastating attacks on WordPress sites. In fact, they are rated second on the list of most critical WordPress vulnerabilities, second only to cross-site scripting attacks. A WordPress SQL injection lets a hacker gain access to your site database, and thereafter flood your site with malware.
If you suspect your site has experienced an SQL injection attack, scan your site for malware immediately.
SQL injection attacks cause a lot of damage on WordPress sites. We will tell you exactly how to deal with the malware from these attacks, and more importantly how to prevent them from happening in the first place.
TL;DR: Prevent SQL injections with MalCare, a powerful WordPress firewall. MalCare keeps out all kinds of attacks, as well as scans for malware daily, and removes it in minutes from your website. SQL injection attacks are very dangerous for any website and can lead to extensive damage. Protect your website with MalCare, a best-in-class WordPress firewall plugin.
What are WordPress SQL injection attacks?
WordPress SQL injection attacks are attempts to gain unauthorized access to your website’s database. Your website database contains all your user-generated information and content, like posts, pages, links, comments, and even users. It is a vast storehouse of important information, and therefore a goldmine for hackers.
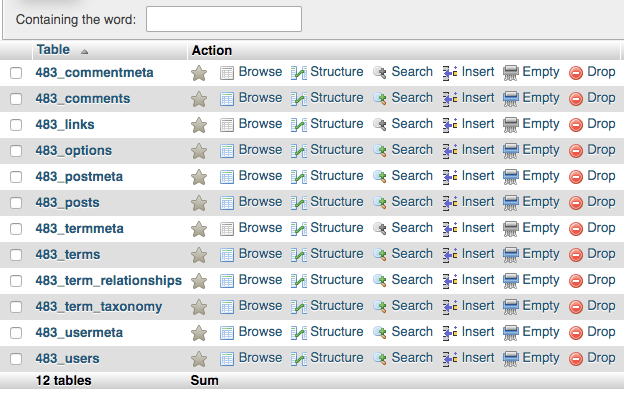
WP SQL injection, unsurprisingly, makes use of SQL commands. Structured Query Language, or SQL, is the language used to interact with databases. It has commands that can add, delete, or modify information stored in database tables. SQL enables your website files to find and fetch the correct data from the database to display on your website.
The way that SQL injection attacks work is by inserting SQL commands in your site’s form fields. For example, a hacker can use your contact form to input data into your website. The data has SQL commands that are executed by your website, and thus can modify your database. Then, once a hacker has gained access to your site database, they can fill your site with malicious code, or cause other kinds of havoc.
There are various entry points for SQL injection attacks. Usually, hackers target forms and any other open fields, like search bars. Carts are also known to be susceptible to SQL injections.
How to check if your WordPress site has SQL injection vulnerability?
The biggest reason that SQL injection attacks are successful at all is vulnerabilities. Vulnerabilities are lapses in code, whether in WordPress core, plugins, or themes. We will get into the mechanics of how WordPress SQL injection exploits work later in the article, but suffice it to say that vulnerabilities are the entry points.
There are a few ways to figure out if your site has an WordPress SQL injection vulnerability:
- Check if anything on your site needs to be updated. If there is a discovered vulnerability in any of the software on your site, the developers of that software will invariably release an update with a security patch. This is the biggest reason we always advocate for keeping your site updated.
A quick way to do this is to use MalCare to check for vulnerabilities. Update those plugins and themes first.

- Use a penetration testing tool. A very popular SQL injection tool, sqlmap, tests your site for WordPress SQL injection vulnerability.
- Test your website with SQL code. This step requires you to have some technical expertise. Depending on which database your site uses, you can use this cheatsheet to figure out the right commands to try.
There are also online scanners that will test for SQL injection vulnerabilities. sqlmap is one of them, but there is also Acunetix, Website Vulnerability Scanner, and other open-source tools. These are penetration testing tools though, and cannot protect your website from SQL attacks. To protect your website from attacks, you need to install a WordPress firewall.
How to get rid of malware that has come in through an SQL injection attack
The WordPress SQL injection exploit is not malware itself, but a mechanism to potentially insert malware into your site’s database or your site itself.
1. Check for symptoms of malware on your website
Malware doesn’t always show up obviously on a website, however, there are some symptoms that you can look out for:
- Spam in your website’s Google search results
- Security issues on Google Search Console
- Errors and other problems on your website, like broken code showing up on pages or spam popups
- Unexplained backend changes to the website
- Site redirects to another website
- Google blacklists your website
- Web host suspends site or sends a warning email
- Performance issues like site slowing down
- User experience issues, like spam email being sent out to users
- Changes in analytics patterns with sudden spikes in traffic
- Google Ads account gets blacklisted
Just one of these markers could be an anomaly, but a combination of two or more is a sure sign of malware.
2. Scan your website for malware
If you see an unexplained occurrence on your website, you need to confirm the presence of malware on your site. The best way to do that is to scan your website for malware. There are three ways to scan your website, which we have listed in decreasing order of efficacy.
- Deep scan with a security scanner to find the smallest traces of malware in your website or database. This is the definitive way to determine if there is malware on your website.
- Scan using an online scanner is a less effective method for scanning, but a good first step to finding out if something is wrong.
- Scanning for malware manually is the least effective, and therefore we don’t recommend it at all.
3. Clean malware from your website
Once you have determined that your site has malware on it, you need to prioritise cleaning it immediately. Malware is egregious, and gets worse with time.
There are 3 ways you can clean malware from your WordPress website:
- Use a WordPress security plugin
- Hire a WordPress maintenance service
- Clean the malware manually
a. Use a WordPress security plugin
Of the 3 options, using the security plugin is your best bet. We recommend MalCare to clean the malware on your website in minutes. It uses an intelligent system to surgically remove only malware from your website, while keeping your data completely intact.
In fact, WordPress SQL injection can insert malware into your site’s database, and MalCare stands head and shoulders above all other WordPress security plugins when it comes to cleaning malware from a database.
To use MalCare, all you need to do is install the plugin, activate it, and enter your email address. The site starts syncing right away, and within minutes you have a scan report. If malware is detected on your website, all you have to do is upgrade to clean it instantly.
b. Hire a WordPress maintenance service
The next best option is to hire a maintenance service or a security expert to clean your site of malware. Be warned though that these services are expensive and rarely indemnify the cleanup. You may end up with a large bill at the end.
c. Clean the malware manually
We strongly recommend against cleaning malware manually. Apart from the time it takes, there is always room for human error. However, if you choose to proceed with manual cleaning, we have put together a WordPress hacked guide to help you through the process.
4. Post-hack checklist
After the malware has been removed, there are a few things you should do. These are housekeeping tasks that take into account that a hacker might potentially have had access to your website and database for some time.
As a rule, it is best to assume that sensitive information like passwords may have been compromised, and thus need to be changed.
How to prevent WordPress SQL injection?
The best way to deal with malware and exploits is to prevent them from happening in the first place. To prevent WordPress SQL injections, there are steps you can take to make sure that your website is as secure as possible:
If you are a developer or creating custom code for your website, you can do the following things to prevent WordPress SQL injection vulnerabilities on your website:
There are ample coding resources available that will be able to help you from a development perspective.
On a happier note, WordPress uses salts to store passwords, so that’s one less type of WP SQL injection you need to worry about.
How do SQL injection attacks work?
SQL injections work when a remote attacker inserts SQL commands into the website and gain access to the database. There are many ways they do this, which we cover in the section about types of SQL injection attacks.
Essentially, hackers take advantage of unsanitised inputs. Unsanitised inputs are user inputs that are not checked or validated by the system; in this case the website. The inputs will be executed by the database and the results are sent back. It is about using the SQL command creatively to get the outcome they are looking for.
For example, hackers use special characters contained in SQL to extract information from the database. Symbols or characters are known as operators which have a special meaning in the language. The asterisk symbol (*) is an operator meaning “all”. Operators are used to make coding more efficient, but because they are not specific, they can be misused if not utilized carefully.
WordPress SQL injection example
Let’s see an example of how an SQL injection attack works:
Suppose you had a login form, where you know one of the login usernames or email addresses.
SELECT * FROM users WHERE email = 'admin@siteemail.com' AND pass = 'password' LIMIT 1Guessing the password might not get you through. However, you can then try adding a special character: a single quotation mark ‘. The result is that you get an unexpected error.
The logs will show that there was a syntax error, which means that the single quotation mark was read as code, rather than a character from the password. The single quotation mark has special significance in SQL, and therefore it caused an error.
SELECT * FROM users WHERE email = 'admin@siteemail.com' AND pass = 'password'' LIMIT 1If you look at the second line of code, the single quotation mark changes the syntax entirely. The pair of single quotation marks on either side of the password indicates where the password starts and stops in this line of code. Therefore, anything between those marks should be considered a password. However, by adding an additional quotation mark at the end of the password, you are ending the password data earlier than expected. The unexpected error tells a remote attacker that this form could be vulnerable to SQL injections, since it is taking whatever is entered into the form fields exactly as typed, and sending it to the database.
This is interesting information for the hacker, by the way. This information gives them insight into how the database processes commands.
Now, we’ve entered ‘ or 1=1-- into the password field.
SELECT * FROM users WHERE email = 'admin@siteemail.com' AND pass = '' or 1=1--' LIMIT 1This gave us access to the system. Why? The single quotation mark, as we explained earlier, ended the password field. And the 1=1 we entered converted into a TRUE value in the system.
Next, the -- made the database ignore everything else after the TRUE value. Therefore, the user was authenticated because the code returned a true value to say that the password was correct.
Types of WordPress SQL injection attacks
The example in the previous section is a small illustration of a very basic SQL injection attack. Most WordPress software already protects against attacks like these. It is known as a classic on in-band SQL injection.
Apart from these classic SQL injections, there are a few more categories. However, before we talk about the other types, there are a few terms that would be helpful to know in the context of WordPress sites:
- Web application: In most web security resources, explanations of the SQL injection attacks refer to web applications. In our article, we are talking about WordPress sites specifically. Therefore, the web application in this case is the website. It is the frontend that a user interacts with, and essentially this is to differentiate it from the website backend, i.e. the database.
- Web server: The web server in question is the one where your WordPress website is stored. All websites are stored on web servers with hosting companies.
- Requests/Responses: Communication on the internet takes place using requests. A person interacts with your website using their browser. The browser sends a request to the web server, which then acts upon the content of that request, and sends a response back to the person’s browser. For example, if you click on a website link on Google, the request is sent to the website’s server. The response is that the website loads on your browser.
- Channel: The channel is the mode of communication used for injection attacks and the results of that attack. In the following categories of injection attacks, the main differentiator is the channel. With in-band attacks, the channel of response is the same as the request. However, with inferential attacks and out-of-band attacks, the channel is different. In the case of WordPress sites, the hacker uses the site to attack. If the results of the attack are visible on the site itself, the SQL injection is said to be using the same channel.
Types of attacks
- In-band SQL injection/Classic SQL injection: There are various ways to understand how an underlying system works, and errors and other system messages are a good way to gain that insight. In-band SQL injections essentially send SQL statements to be executed, and the results are shown on the same page. There are two major types of classic SQL injection attacks:
- Error-based attack: Here, the SQL statement in the injection deliberately contains incorrect syntax or input. When executing, the system returns an error message. Based on that error message, the remote attacker is able to piece together information about the database. Error messages are supposed to be as helpful as possible to developers, and enable them to pinpoint errors quickly. This is a gross misuse of that functionality.
- Union-based attack: Union operators are SQL commands that combine two or more statements into one. On websites with this vulnerability, the malicious SQL query is tagged onto the end of a normal query, so that it is forced to execute. The results are displayed on the page as an HTTP response.
- Error-based attack: Here, the SQL statement in the injection deliberately contains incorrect syntax or input. When executing, the system returns an error message. Based on that error message, the remote attacker is able to piece together information about the database. Error messages are supposed to be as helpful as possible to developers, and enable them to pinpoint errors quickly. This is a gross misuse of that functionality.
- Inferential SQL injection/Blind SQL injection: In contrast to the in-band SQL injection attacks, errors or results of SQL queries are not visible on the page. So, a hacker tries various types of inputs, and then analyses the resulting behaviour to figure out how the database works.
Think about this like a bat’s audio signal. When the signal bounces off objects, the bat can infer the size and distance of the object, and if it is food or a threat. There are two main types of inferential SQL injection attacks:
- Boolean attack: The hacker first starts by sending an SQL query that they know will result in a TRUE result, and observes the behaviour of the web application. An example of this could be a condition like 1=1, which will always be TRUE. Next, the hacker will observe the behaviour when the query resolves to FALSE.
Once they have this information, they know how the database reacts to TRUE and FALSE. It may not be immediately clear how the hacker can use this information to extract data. However, the hacker can now construct queries that are essentially a series of true-false questions. To extract passwords of admin accounts, for example, the hacker can check the password character-by-character against a list of letters, numbers and special characters. Because that list is finite, the password will slowly be revealed.
Granted, this is a tedious, time-consuming process. However hackers automate it, so that it happens in minutes. - Time-based attack: Similar in theory to the Boolean attack, the time-based attack relies on time delay instead of a TRUE/FALSE outcome. If the SQL query is correct, the response will be returned after a time delay. If not, it will happen immediately.
- Boolean attack: The hacker first starts by sending an SQL query that they know will result in a TRUE result, and observes the behaviour of the web application. An example of this could be a condition like 1=1, which will always be TRUE. Next, the hacker will observe the behaviour when the query resolves to FALSE.
Inferential SQL injection attacks can take longer, because of the way they are set up. However, that doesn’t make them any less dangerous.
- Out-of-band SQL injection attack: These types of attacks are the next step up from inferential SQLi attacks. With out-of-band SQL injection attacks, the responses are not visible on the website at all.
So out-of-band SQLi attacks work by getting the underlying system to send the responses to another system altogether, which is generally controlled by the hacker.
Consequences of SQL injection attack on your WordPress Site
The consequences of a WordPress SQL injection can vary greatly, depending on what the hacker chooses to do with their ill-gotten access. Here are some of the things we have seen hackers do to websites:
- In the worst-case scenario, the hacker can delete all the contents of your database. This will break your website, and make it impossible to recover, unless you have independent backups.
- With SQL injection in WordPress, the hacker can insert malware into your database. This can mean SEO spam malware and its variants, like the Japanese keyword hack or the pharma hack. It can also mean hacked redirect malware, which infects all posts and pages.
- A hacker can take control of a user account, and escalate their privileges. If you see odd activity from a user, it may be a sign of a compromised website.
- Since the hacker has access to your database, they can add, modify, delete or even steal the data. This creates a huge privacy issue, especially if you are storing sensitive data like emails or personal details. Data breaches put users at risk.
- Finally, SQL injection attacks can lead to remote code execution attacks as well.
What is the impact of malware on your site?
Malware causes a ton of damage and loss to a website. It eats away at resources, takes away visitors and causes immense stress. The admin is usually left in a state of panic. Apart from that, here are some effects of malicious code we have seen on hacked websites:
- Organic traffic tanks
- Google blacklists your website
- Web host suspends your website
- Visitors stop coming to your website
This list doesn’t even scratch the surface of problems; it is just the most egregious problems. Basically: malicious code should never be taken lightly.
Long story short, SQL injection attacks are the mechanism used by hackers to gain unauthorised access. Once they do, there is a lot of damage they can do. In 2019, two-thirds of all attacks were SQL injection attacks. This number has gone down a bit, but that doesn’t make them any less dangerous. However, understanding what a WordPress SQL injection attack does, and how it works goes a long way in protecting your website.
Why are SQL injection attacks so common?
SQL injections result in a lot of valuable data for hackers. That is the primary reason that they are so prevalent. There are other reasons though:
- Most website databases use SQL
- The attack works mostly through form fields, and most websites have at least one field that allows input. A contact form, a search field and so on.
- There are many scanners available online that can detect SQL injection vulnerabilities on a website. These are usually ethical hacking tools that are intended to caution the website admin about lapses in their security, but can also be used by hackers.
- Unfortunately, SQL injections are easy to perform. They don’t require too much technical knowledge or expertise.
- It is difficult to account for these vulnerabilities. In fact, SQL injection vulnerabilities have been discovered in WordPress security plugins too. The one place where you wouldn’t expect to find them.
In early 2022, WordPress core was found to have SQL injection vulnerabilities as well. As developers implement safeguards to protect against older attacks techniques, hackers have found new ways to exploit websites.
Conclusion
There is little a WordPress admin can do to mitigate WordPress SQL injection vulnerabilities on their website, apart from making sure everything is updated. However, a good WordPress firewall will stop hackers from exploiting these vulnerabilities, so the website remains secure. The best course of action any admin can take for WordPress security is to install a security plugin.
FAQs
What is a WordPress SQL injection?
A WordPress SQL injection is a type of attack that inserts SQL code into the frontend of a website, in order to gain access to the website’s database. The hacker can use this unauthorised access to insert malware into a website, steal or modify sensitive data in the database, or even delete it altogether. All in all, a WordPress SQL injection attack can cause websites a ton of damage and loss.
Share it:
You may also like

MalCare Ensures Proactive Protection Against WP-Members XSS Vulnerability
MalCare continues to protect its customer sites from all kinds of attacks, even the ones exploiting zero-day vulnerabilities. The recent stored cross-site scripting (XSS) vulnerability found in the WP-Members Membership…
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…

MalCare Proactively Defends Against Icegram Express SQL Injection Vulnerability
MalCare’s recent data has revealed numerous attempts to exploit a newly found SQL injection vulnerability in the Icegram Express plugin. Attackers commonly use this sophisticated SQL injection technique to extract…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








