5 Steps to Fix Adminer Vulnerability Exploits (Adminer.php Hack)
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.
Do you use Adminer on your WordPress website? Did you hear about its vulnerabilities? Are you worried that your site could be hacked because of it? Have you ever heard of adminer.php hack?
Adminer, a popular database management tool, is used by hundreds of thousands of websites. But a dangerous vulnerability that can be exploited by hackers was discovered years ago and it still exists! Attackers can abuse the security flaws to hijack your WordPress site.
The consequences are brutal. When a hacker takes control of your site, they target your customers, steal their information, sell illegal products, to name a few! You could face high financial costs and irreparable damage to your reputation.
Fortunately, there is a way to fix the vulnerability and prevent it. Today, from this article, you’ll learn how to identify and fix the Adminer’s hack and how to take preventive measures against future hack attempts.
TL;DR: If your WordPress website is hacked due to the Adminer vulnerability present on your site, you need to fix your website immediately. We strongly suggest that you download and install this plugin – Adminer Hack Removal Plugin. It will scan your website & all types of malware present on your site. The plugin will also help you clean your site in under 1 min.
Table of Content
→ What Are Adminer’s Biggest Vulnerabilities?
→ How to Fix the Adminer Hack Vulnerability?
→ How to Fix a Website Hacked Through Adminer.php?
→ How Hackers Exploit The Adminer Vulnerability?
→ Impact of the Adminer.php Vulnerability on WordPress Website
→ Steps To Take After Fixing The Hacked Site
What is Adminer?
Adminer (formerly known as phpMyAdmin) is a tool to manage the content of MySQL databases that was released in 2007.

It is used by developers and site owners to work with databases. It enables users to select their database, edit tables, insert more table rows, along with a host of other functions.
Adminer replaced phpMyAdmin as it brought about drastic improvements in areas of user experience, performance, and security. It was also developed to support more MySQL features.
But like any other software Adminer too develops vulnerabilities from time to time.
What Are Adminer’s Biggest Vulnerabilities?
The first Adminer vulnerability was discovered in version 4.3.1 which had a server-side request forgery vulnerability.
Recently William de Groot tweeted about another vulnerability and how Magecart hackers would be so happy about it:
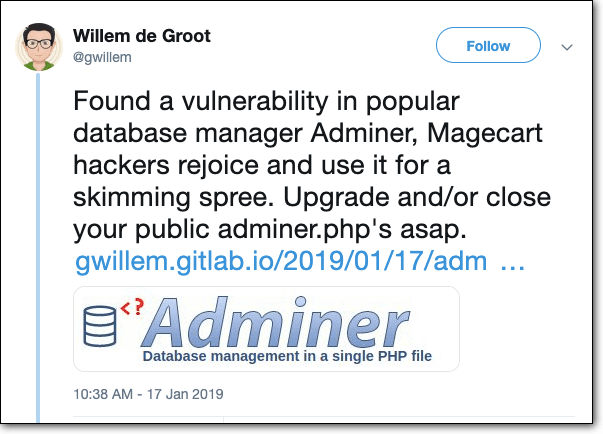
However, this vulnerability was discovered a long time ago. The vulnerabilities lie in versions below 4.6.3. If you’re using version 4.6.3 and above, Adminer is secure.
Versions 4.6.2 and below contain an application security gap that allows hackers to read files on the server. This can happen if webmasters leave the Adminer scripts publicly accessible while using Adminer.
Now let’s look at how to fix these vulnerabilities.
How to Fix the Adminer.php Hack Vulnerability?
If you’re using Adminer, make sure you’re running the latest version available. Any version below 4.6.3 is vulnerable.
You need to update immediately!
When a vulnerability is discovered, developers fix it and release the security patch in a software update. They also release bug fixes, performance improvements, and new features in these updates. So in the future, if you see software updates available, be quick to update it.
How to Fix a Website Hacked Through Adminer.php?
In attacks launched by exploiting this vulnerability in Adminer, the malicious scripts could be spread across multiple files and your database. Hackers also create fake admin accounts and install fake plugins and backdoors.
Fixing the hack on your own would take days and prove to be ineffective. This is because hackers hide and disguise their malicious code. It becomes very difficult to spot their hacks.
That said, we DO recommend installing MalCare Security Plugin to clean a hack caused by the Adminer vulnerability. Here’s why:
Why Use MalCare Security Plugin to Fix a Hacked Site?
- It will do a complete and thorough scan of your entire WordPress site. This includes all files and databases. This ensures every inch of your website is checked in a matter of minutes.
- It will hunt down any kind of malware present on your site, even if it’s disguised or hidden. The plugin can do this because it smartly analyses the behavior of the code. It checks what kind of activities it performs and flags the malicious ones.
- You will be alerted on how many hacked files have been found.
- The plugin has an option to Auto-Clean your website. The cleaner will delete and clean up all malware present on your website. It will also get rid of any backdoors created by hackers.
- You can update your website directly from the MalCare dashboard.
- Your website will be protected from common hack attacks with a proactive firewall. This will block any known malicious IP addresses and brute-forcing hack attempts. The plugin will continue to scan your site regularly and keep your website secure.
Plus the plugin is easy to use and gets the adminer.php hack removed in under a few minutes!
How to Use the MalCare Security Plugin?
Using MalCare on your WordPress site is easy. Follow the steps below:
Note: If you’re locked out of your WordPress site and cannot install the plugin, contact our team, or use our emergency clean up services.
Step 1: Sign up with MalCare and set up an account. MalCare will automatically run a full security scan.
Once the scan is complete, MalCare will display how many hacked files have been found.
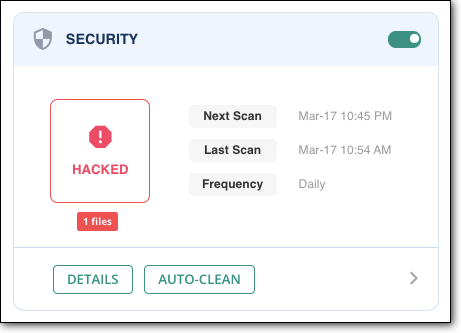
Step 2: To clean up your website, click on the Auto Clean button.
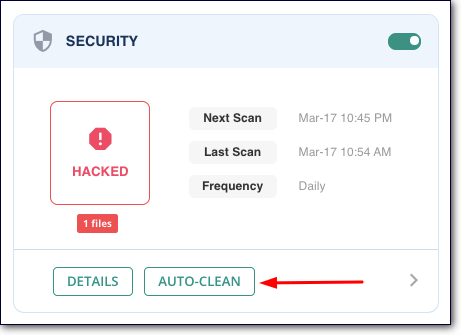
After the clean up is complete, you’ll be notified. We recommend visiting your website to see that everything is normal. You can run another scan to double-check that it’s completely clean.
Steps To Take After Fixing The Hacked Site
There are a few extra steps you need to take since your database was attacked.
- Update Adminer to the latest version.
- Change your database password. You can follow your WordPress hosting provider’s instructions on this as it may differ between hosts. Alternatively, you can change it in the wp-config file.
- Delete any user accounts that you don’t recognize on your WordPress dashboard.
- Delete any plugins or themes that you didn’t install on your site. Look out for a plugin called Super Socialat. It is a fake plugin used by hackers in this attack. We recommend also deleting any plugins and themes that you don’t use.
- Reset passwords of all user accounts.
- Implement recommended WordPress hardening measures.
- Regular penetration testing is a must.
Now, you can relax as your WordPress site should be secure and safe from adminer.php hack! However, the work’s not done yet. It’s important to know how hackers exploit this vulnerability and the impact it can have on your site. This will help you gain a deeper understanding of what hackers do and what can potentially happen to your website.
How Hackers Exploit The Adminer Vulnerability?
Let’s go step by step and understand the adminer.php hack attack vector:
1. Identify Website With the Vulnerability
Hackers first need to find a website using Adminer.php files. This is quite an easy task. Hackers run targeted scans on the internet. What this means is they can search for WordPress sites that use a particular plugin or a theme that they know is vulnerable. In this case, they can search for WordPress sites that use the vulnerable software Adminer.
2. Use Vulnerable Site to Launch Hack Attacks
If a hacker is able to find just one vulnerable website, they can hack it and then use it to find more sites. They install scripts on the compromised website to scan other sites and find publicly accessible Adminer databases. In this way, they are able to find thousands of vulnerable sites.
3. Locate Adminer Files
Next, they launch their attack. A hacker needs to locate the Adminer files. This is usually in the site’s root directory (public_html). These files are usually left with obvious names such as adminer.php or adminer-4.3.1-mysql-en.php. This makes it easy to locate.
Then, the hacker uses the ‘Load Data Local Infile’ statement to access logs and read files. Then, they use these files to run scripts that will connect the site to a database of their own on a remote server.
4. Access Victim Site’s Database
When they establish a connection with their server, they can use a data import request to steal the content of local files such as the wp-config file that stores database credentials. They use these credentials to access the victim’s local database.
This is how an entire website can become compromised due to this vulnerability. Now, a hacker can inject malware, steal sensitive information, steal payment card data, or redirect sites to their own malicious content.
They are also quick to install backdoors on the site which is like their own private entrance. This allows them to hack the same website over and over again as long as the backdoor is present.
Impact of the Adminer.php Vulnerability on WordPress Websites
If a website is using a version of Adminer below 4.6.3, then it is at a severe risk of being hacked. This particular hack can exploit multiple vulnerabilities present in Adminer as well as in the WordPress core or plugins and themes. This enables a hacker to gain full control of a website and its database. A few of the severe repercussions a compromised site could face are:
1. Loss of Control
In an Adminer attack, a hacker could assign themselves an admin role and lock you out of your WordPress dashboard. You would have no control over getting back into your website unless you employ professional website security services like MalCare (which we’ll discuss in the next section).
2. Data Breach
The Adminer.php hack vulnerability could be used to steal customer information such as personal details, payment information, contact and shipping details, and even preferences. They could use this data to their advantage, carry out fraudulent activities against your customers, or sell the data. Apart from customer data, they also steal sensitive and confidential data of your business.
3. Attacks on Others
If your site is compromised, hackers have malicious scripts that they run on your website to find other vulnerable sites. You’d be the cause of more attacks on other WordPress sites.
4. Google Blacklist
If your site has been compromised and puts your users at risk, Google will be quick to blacklist your website. It will also suspend your ads account. They rank user experience above all and will take all measures necessary to protect their users. Once you’re blacklisted, you won’t receive traffic to your site. You would need to fix your site and submit it to Google for review to remove the Google blacklist.

5. Web Host Suspension
If your site is hacked, it puts your host’s web servers at risk too. It could also affect the performance of other sites they host. Your web host will suspend your account and take your site offline as soon as they notice the hack.
6. Recovery Costs
The cost of recovering from such a hack can skyrocket. You would not only have to spend on cleanups, but you might also face legal penalties from your government. Plus, recovering your SEO efforts and restoring your site back to normalcy will also cost you.
That brings us to the end of this article. Knowing just how bad the impact of this adminer.php hack vulnerability should be encouragement enough to always keep your adminer.php updated.
Final Thoughts
The Adminer vulnerability shows just how devastating attacks could be launched at hundreds of websites. To avoid these attacks, always keep all your software up to date. Here’s what Adminer recommends:
The Adminer.php attack is only one of the million other attacks that could be launched on your website. It’s time to ramp up the security of your site. With MalCare active on your site, you can rest assured that your site is safe against hackers!
Secure your Website with our MalCare Security Plugin!
Category:
Share it:
You may also like

How to Fix the Google Blacklist Warning from Your Website
Google blacklist is a colloquial term used to describe big red warnings visible when visiting websites. There are a few flavours, depending on various factors, but they all mean that…

MalCare Stands Strong Against WP Activity Log Premium SQL Injection Vulnerability
A significant SQL injection vulnerability was identified in the WP Activity Log Premium plugin, a popular tool for tracking user activity on WordPress sites. An SQLi vulnerability poses a serious…
Fix Pharma Hack on WordPress and SEO
Pharma hack is a prolific malware that redirects visitors from your site to an online pharmacy that sells Viagra, Cialis, Levitra, Xanax, Tadalafil, and other drugs. It also shows up…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








