How To Protect Your WordPress Website From File Upload Vulnerability?
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.
One of the core strengths of WordPress lies in its file upload functionality. The ability to seamlessly upload and integrate various types of files, from images and documents to multimedia content, is a cornerstone of content creation and website enhancement. However, if not properly secured, this very functionality can become a vulnerability, leaving your website exposed to malicious exploits.
File upload vulnerabilities in WordPress can arise due to various factors and can have severe consequences. They can pave the way to everything from website defacement to complete site takeover by malicious actors. In this article, we look at what file upload vulnerabilities are, ways to prevent them, understand their types, and explore how hackers exploit them. In case you are already facing attacks that exploit this vulnerability, start by scanning your site with MalCare.
TL;DR: File upload vulnerabilities in WordPress can expose your site to severe threats like data theft and malware injection. To prevent these, implement secure file upload practices, keep WordPress updated, and use MalCare’s robust firewall and activity log for comprehensive protection.
What is the file upload vulnerability in WordPress?
File upload vulnerability in WordPress is a critical security flaw that stems from the ability to upload files to the site server. This functionality is designed for content management purposes, allowing users to upload images, documents, and various media types. However, vulnerabilities can arise if these capabilities are not meticulously secured, exposing the website to potential attacks.
File upload vulnerabilities are usually caused by:
1. Install a security plugin
Consider using a sophisticated WordPress-specific security plugin like MalCare. MalCare is designed not only to check and alert you of vulnerabilities but also includes a malware scanner and cleaner to deal with any threats swiftly.
Additionally, its Atomic Security firewall acts as a robust barrier, filtering out harmful traffic and preventing unauthorized access. It proactively protects from all severe file upload vulnerabilities right out of the box, even before they are found and publicly disclosed.
2. Regularly update all components of your WordPress site
Keeping your WordPress core, plugins, and themes updated is crucial for security. These updates often contain patches that address newly discovered security flaws. If you’re concerned about how updates might affect your site, test them on a staging site first.
For MalCare users, the UpdateLens feature provides a detailed safety assessment of each update, helping you to decide confidently whether to apply it.
3. Choose trusted sources for plugins and themes
To minimize vulnerabilities, ensure that you download themes and plugins from reliable sources. Nulled plugins, which are often pirated versions of paid offerings, could contain malicious code and compromise your site’s integrity.
When selecting plugins, consider their maintenance record as well; a well-maintained plugin with frequent updates is usually a safer choice. Only use products from reputable providers to ensure the highest security standards.
4. Utilize audit logs to monitor site activities
Audit logs are vital for security, providing detailed records of site access and activities. Regular examination of these logs can help you spot unusual patterns or unauthorized actions, allowing for prompt intervention. Using tools like MalCare that include built-in log monitoring can aid in effectively overseeing these aspects without having to manually check them constantly.
5. Tighten control over file uploads
Managing file upload functionalities with precision can drastically enhance your site’s security. Specify which file types are permitted, focusing on allowing only non-executable files. Additionally, set limits on the file size that can be uploaded to prevent large, potentially dangerous files from being uploaded. It’s generally more effective to define explicitly which file types are allowed rather than trying to list all undesirable types, closing off potential loopholes used by attackers.
Moreover, keep the file upload functionality on your site only if your users need it. If the file upload functionality is not absolutely necessary, it is prudent to remove it from your site and shut the door on potential file upload vulnerabilities once and for all. For the rare occasion where you absolutely need to upload files, we recommend doing it via FTP/SFTP.
6. Rethink upload storage practices [RISKY]
The default storage location for uploads in WordPress is public_html/wp-content/uploads/, which is well-known to hackers. Changing this can decrease risk, although it involves modifying system files and/or folders that could potentially disrupt site operations. If you are comfortable doing this, here are some steps you can take to protect your uploads directory:
Hide your uploads directory
This is one of the most basic methods of protecting your uploads directory. Making the uploads directory hidden from public view can ensure it remains inaccessible to hackers even if they are inside your site. You can achieve this by using plugins like WP Hide and Security Enhancer.
Change the uploads directory name
Alternatively, changing the name of your uploads directory can add another layer of security to it. All you need to do is rename the uploads directory to any other name. You can do this in one of two ways:
A. Using cPanel
If your hosting provider has provided a cPanel for site administration, you can use it to access your site files. Here are the steps to do so:
- Login to your site’s cPanel and access the File Manager.
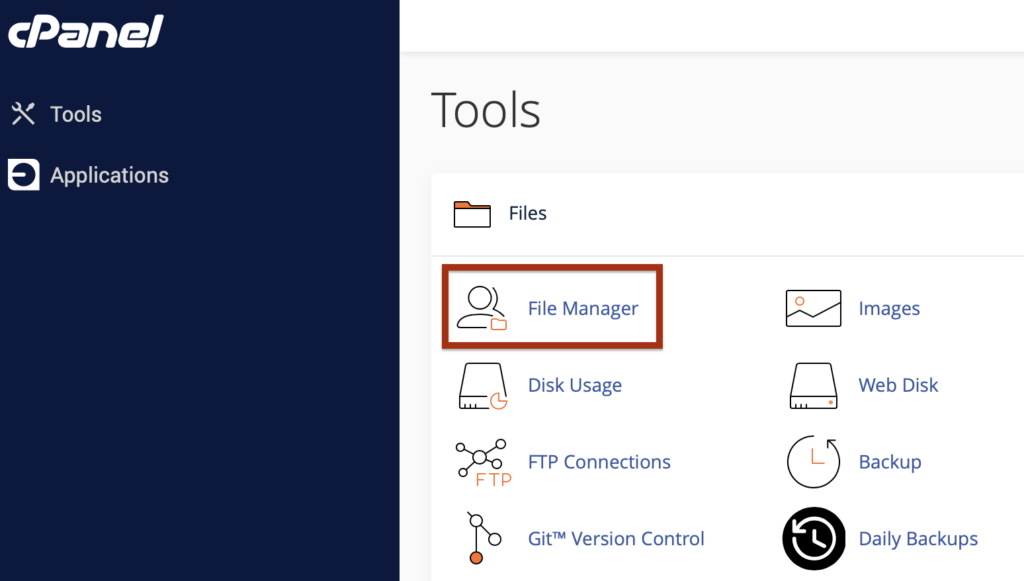
- Navigate to public_html and then to wp-content using the left hand navigation pane and select the uploads directory.
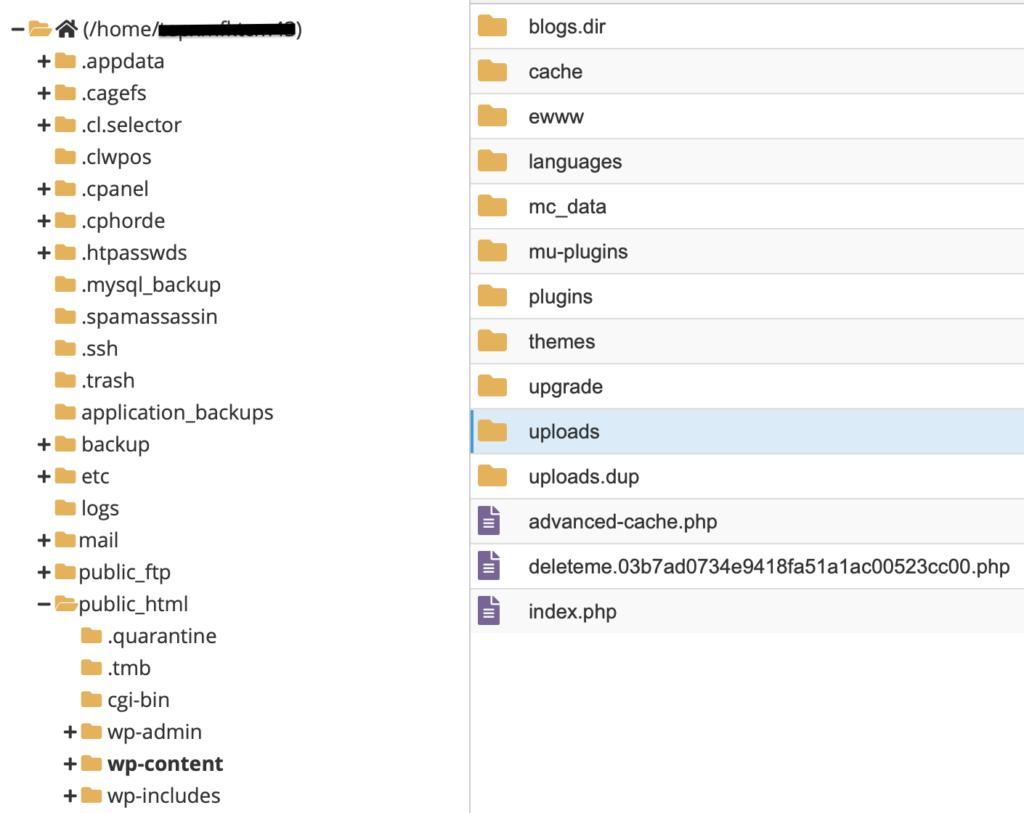
- Right-click on the uploads directory and select Rename from the context menu.
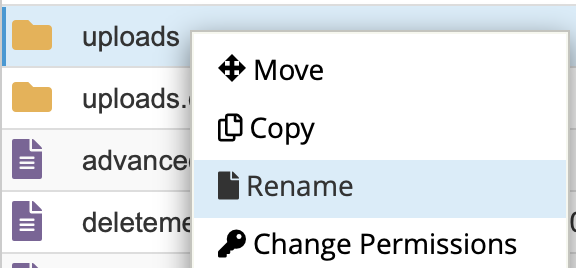
- Add the name you prefer and hit Enter to save the name. Your uploads directory has now been renamed.
B. Using an FTP client
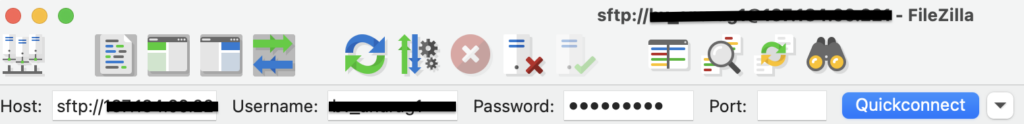
In case your hosting provider does not provide a cPanel for site administration, you can take the FTP way to rename your uploads directory. For this, you will need an FTP client like Filezilla and the FTP credentials for your site, which should ideally be available on your hosting provider’s site dashboard.
- Login to your site through FTP using Filezilla. You will need to add the host IP address, username, password, and port number (if any).
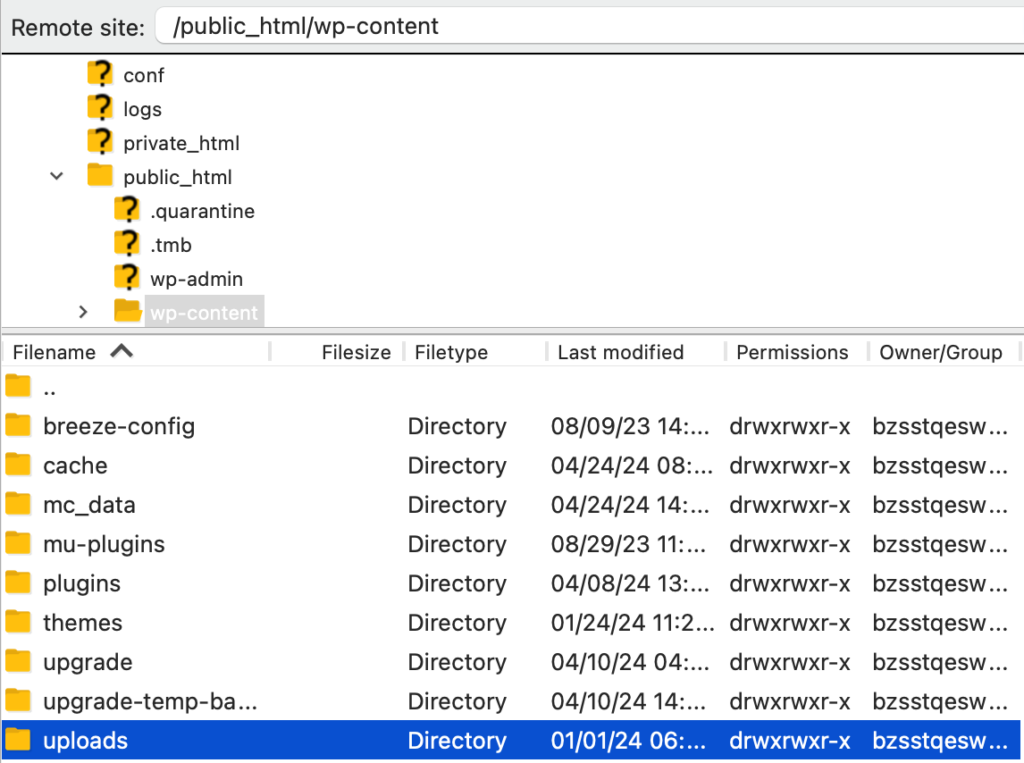
- Once you are connected, use the Remote site pane to navigate to /public_html/wp-content/ and select the uploads directory.
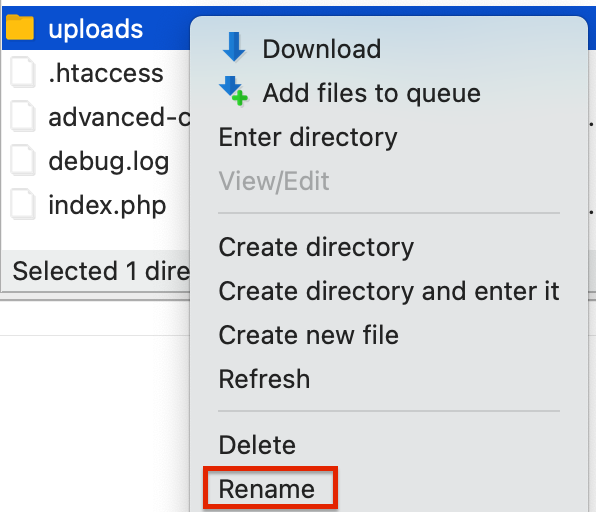
- Right-click on the uploads directory and select Rename from the context menu.
- Add the name you prefer and hit Enter to save the name. Your uploads directory has now been renamed.
Change the default uploads directory
This is one of the best ways to secure your uploads directory. You will need to create a separate directory with a different name than uploads (obviously!) and then redirect all your future uploads to be stored in this new directory. However, it requires you to edit your site’s wp.config.php file, so we would advise you to be cautious while doing it. Here’s how you can do it:
- Access your site’s wp-config.php file either by using cPanel or FTP. It is usually located in the public_html directory.
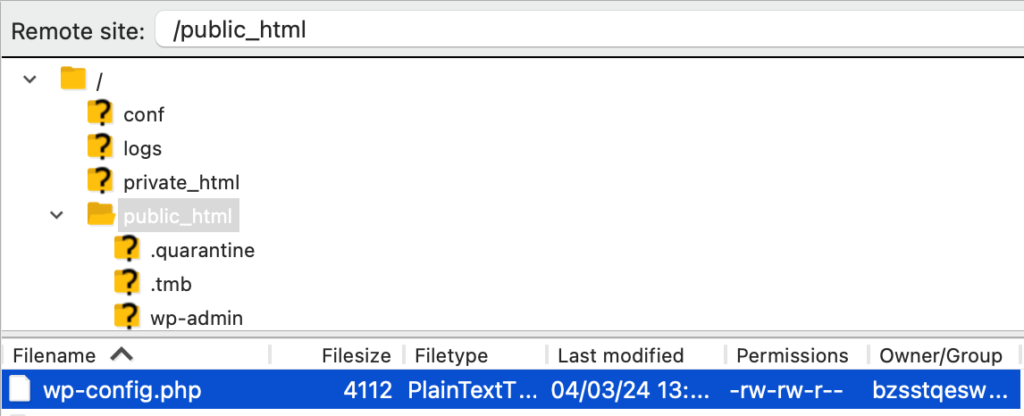
- Right-click on the file and click on Edit, if you are using cPanel, or View/Edit, if you are using Filezilla.
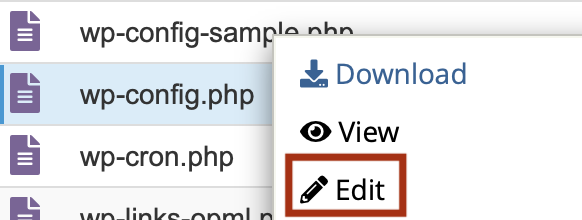
cPanel
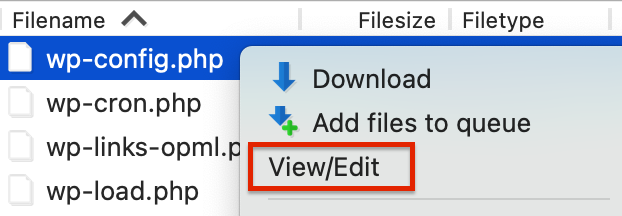
Filezilla
- Once the file opens in an editor, add the following line of code before the file ending and above the line that says /* That’s all, stop editing! Happy blogging. */
define('UPLOADS', 'your/chosen/directory');Here, replace the your/chosen/directory value with the correct path to your chosen directory.
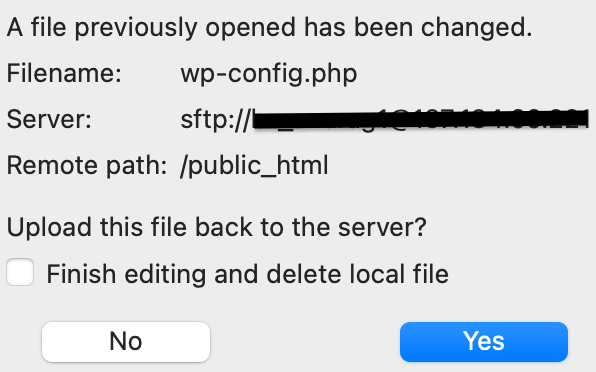
- Hit Ctrl+S, if you are on Windows, or Cmd+S, if you are on Mac, to save the edits. If you are using Filezilla, close the editor window and click Yes on the follow-up popup to upload the file back to your site.
What are the different types of WordPress file upload vulnerabilities?
File upload vulnerabilities in WordPress can manifest in various forms, each posing unique risks and challenges. Understanding these types can help in ensuring better security measures to protect your WordPress site.
Unrestricted file uploads (Local)
This type of vulnerability occurs when WordPress sites allow users to upload files without enforcing restrictions on the file types. Typically, secure systems should limit uploads to non-executable file types to prevent the execution of malicious scripts. When there are no such restrictions, attackers can easily upload scripts disguised as harmless files, which when executed on the server, can lead to serious security breaches including site takeover.
Insecure path uploads (Remote)
Insecure path file upload vulnerabilities happen when the files are uploaded to a directory that users can access via a URL. An example of this type is when users are required to upload files to a cloud location like Google Drive, Dropbox, etc. instead of the main site itself.
This practice can be risky especially if the directory is not protected by proper access controls, allowing anyone to download or execute files stored there. If executable files are uploaded into such directories, they can be directly accessed and run by attackers, enabling them to perform malicious activities remotely.
Metadata-based vulnerabilities
Files like images and PDFs can contain executable code embedded in the form of hidden metadata. This metadata might be exploited by attackers to inject malicious content or scripts. For example, an image file could carry a PHP script within its metadata. When processed by the server, this script could be executed unintentionally. Sanitizing or stripping metadata from uploaded files is required to mitigate this risk.
Storage space consumption
Attackers might exploit file upload functionalities to perform a denial of service (DoS) attack by consuming the available storage space on the server. They do this by uploading large files or a high volume of files, which fills the server disk space, subsequently preventing legitimate file uploads and other normal operations. This can be partially mitigated by setting limits on the size and number of files a user can upload.
An example of this type includes sites with insecure file naming conventions. Some platforms require files to be uploaded with a specific filename format, such as CVs that are named using the applicant’s name and date of birth. Hackers can exploit this by uploading numerous files that conform to this naming format but are designed to either occupy significant storage space or potentially overwrite legitimate files.
How do hackers exploit WordPress file upload vulnerabilities?
File upload vulnerabilities provide hackers with a potential backdoor into WordPress sites. By exploiting these weaknesses, attackers can bypass conventional security measures and perform a range of harmful actions. Here are the steps hackers can take:
- Scout for entry points: Hackers begin by identifying entry points in a website. This typically involves scouting for weak spots where the site allows user interactions, such as file uploads, without stringent security checks. Sites that lack proper validation and sanitation of uploaded files are prime targets.
- Test the ‘locks’: Once a vulnerable site is spotted, hackers proceed to test the extent of the vulnerability. This involves uploading different types of files to see what the system accepts—ranging from small benign files to larger files, and eventually to malicious scripts disguised as harmless files. This step determines how much the attackers can manipulate the site’s upload features.
- Slip inside: If the test uploads succeed, especially those involving disguised scripts, hackers then activate the malicious script. This script typically creates a backdoor in the system, allowing the attackers unfettered access to the site’s backend without the need for further authentication.
- Perform malicious actions: With backdoor access established, hackers can then conduct a variety of malicious activities. They might steal sensitive data, redirect visitors to fraudulent sites, inject malware, deface the website, or use the server’s resources for tasks like cryptocurrency mining. Each action can have severe consequences for the site’s reputation, user safety, and operational integrity.
- Clean up after them: Depending on their motives, some hackers may opt to erase traces of their entry and activities to avoid detection and prolong their access. However, they usually ensure that the backdoor remains open for potential re-entry. This stealth approach can make it particularly challenging to detect and address the breach.
Once hackers gain access to your site by exploiting file upload vulnerabilities, they can perform malicious activities like:
Final thoughts
Navigating the complexities of WordPress security can often feel like maintaining vigilance over a digital fortress. As we’ve learned, file upload vulnerabilities represent a significant threat—one that can pry open doors to various malicious exploits if left unguarded. The potential consequences, such as data theft and complete site takeover, are daunting but preventable. Understanding the exploration of types, exploitation methods, and preventive strategies helps arm you with the tools necessary to fortify your site’s defenses.
To solidify this protection, it is crucial to integrate a robust security solution like MalCare. MalCare’s advanced malware scanning and cleaning capabilities, along with its robust firewall, offer a comprehensive shield against file upload vulnerabilities. It not only guards against potential breaches but also ensures quick recovery tools are at your disposal should the need arise. Regular updates from MalCare keep it adept at countering the latest threats, making it a wise and necessary addition to your WordPress security toolkit.
FAQs
What are file upload vulnerabilities?
File upload vulnerabilities occur when a website allows users to upload files to the site server without sufficient security checks, enabling attackers to upload malicious files. These vulnerabilities can be exploited to execute harmful scripts, steal data, or gain unauthorized access to the website. Proper validation of file types, sizes, and user permissions is crucial to prevent such security breaches.
How vulnerable is WordPress?
WordPress is generally considered fairly vulnerable to security threats if not properly maintained and secured. As a widely used content management system, it is a common target for hackers looking to exploit vulnerabilities. Regular updates, secure hosting, using a WordPress-specific security plugin like MalCare, and following security best practices are important for mitigating risks when using WordPress.
How do I secure a file upload?
To secure file uploads, employ measures such as restricting allowed file types and extensions, scanning files for malware, limiting file sizes, implementing access controls based on user roles, etc. Following these best practices can mitigate risks like arbitrary file uploads, remote code execution, and directory traversal attacks.
How often is file upload vulnerability exploited?
File upload vulnerabilities are frequently exploited by hackers. According to the OWASP Top 10 Web Application Security Risks, unrestricted file uploads rank among the most commonly exploited vulnerabilities. Security researchers and databases like CVE Details and ExploitDB consistently report new file upload vulnerabilities being discovered and exploited across various web applications and platforms on a regular basis. The prevalence of this vulnerability highlights the importance of implementing proper file upload security controls to prevent malicious file uploads that could lead to data breaches, remote code execution, or other serious consequences.
What are the effects of malicious file uploads?
Malicious file uploads can enable remote code execution allowing complete system compromise, lead to data theft by providing access to sensitive information, deface or vandalize websites, cause denial of service by consuming excessive server resources, and turn platforms into malware distribution channels. Properly securing file uploads is crucial to prevent these severe consequences that jeopardize data integrity, system availability, and user trust.
Category:
Share it:
You may also like

How to Fix the Google Blacklist Warning from Your Website
Google blacklist is a colloquial term used to describe big red warnings visible when visiting websites. There are a few flavours, depending on various factors, but they all mean that…

MalCare Stands Strong Against WP Activity Log Premium SQL Injection Vulnerability
A significant SQL injection vulnerability was identified in the WP Activity Log Premium plugin, a popular tool for tracking user activity on WordPress sites. An SQLi vulnerability poses a serious…
Fix Pharma Hack on WordPress and SEO
Pharma hack is a prolific malware that redirects visitors from your site to an online pharmacy that sells Viagra, Cialis, Levitra, Xanax, Tadalafil, and other drugs. It also shows up…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








