MalCare Proactively Blocks 10,000+ Attacks Targeting LiteSpeed Cache XSS Vulnerability
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

MalCare has been proactively blocking over 10,000 cross-site scripting (XSS) attacks targeting customer websites. These attacks attempt to exploit a vulnerability found in the popular LiteSpeed Cache plugin.
Although the vulnerability was discovered and patched in October 2023, the spate of recent attacks shows that many websites have not updated their LiteSpeed Cache plugins to the patched versions. This puts them at significant risk because this attack has a very low barrier to entry. This means the hacker doesn’t need an account on the target site for an attack to be successful. A single request is all it takes to breach the site and steal confidential information like user credentials.
Attacks rear their ugly heads
Starting in late February, MalCare saw an uptick in the number of XSS attacks faced by its customer websites. The origins of these attacks were spread across multiple IPs from Europe and North America.
All these attacks targeted a security vulnerability in the LiteSpeed Cache plugin.
What is the LiteSpeed Cache plugin vulnerability?
Plugin information
- Vulnerable plugin version: v5.7 and earlier
- Patched plugin version: v5.7.0.1 and later
LiteSpeed Cache is a popular WordPress caching plugin, with over 5 million active installs. It is an all-in-one site acceleration plugin that boasts an exclusive server-level cache and several optimization features. Its ability to support WordPress Multisite and compatibility with plugins like WooCommerce, bbPress, and Yoast SEO, are the reasons behind its popularity.

About the vulnerability
The LiteSpeed Cache vulnerability occurs because the code that handles input from the user doesn’t implement sanitization and output escaping. This means that a malicious actor can inject malicious scripts, such as redirects, advertisements, and other HTML payloads into your website. These scripts will get executed when guests visit your site and steal confidential information as they are entered.
The vulnerability was fixed with the release of LiteSpeed Cache v5.7.0.1 on October 25, 2023.
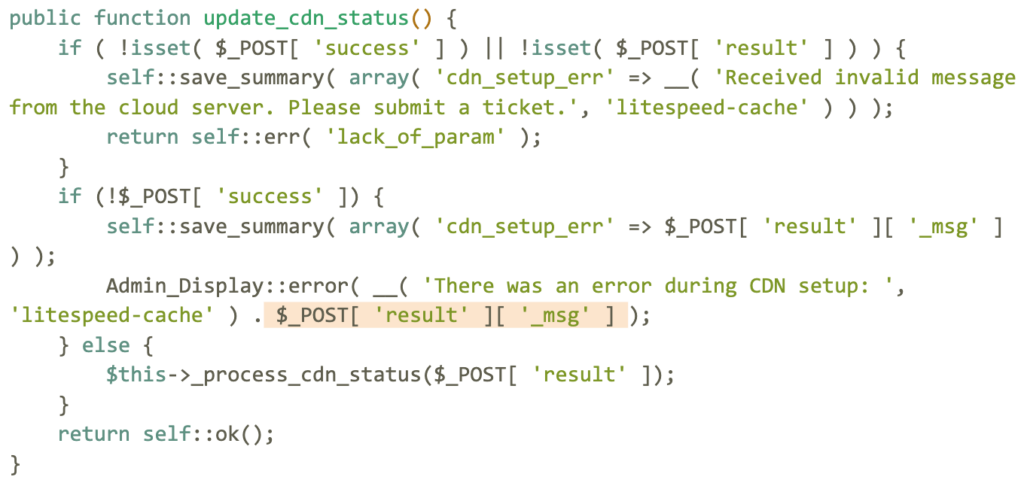
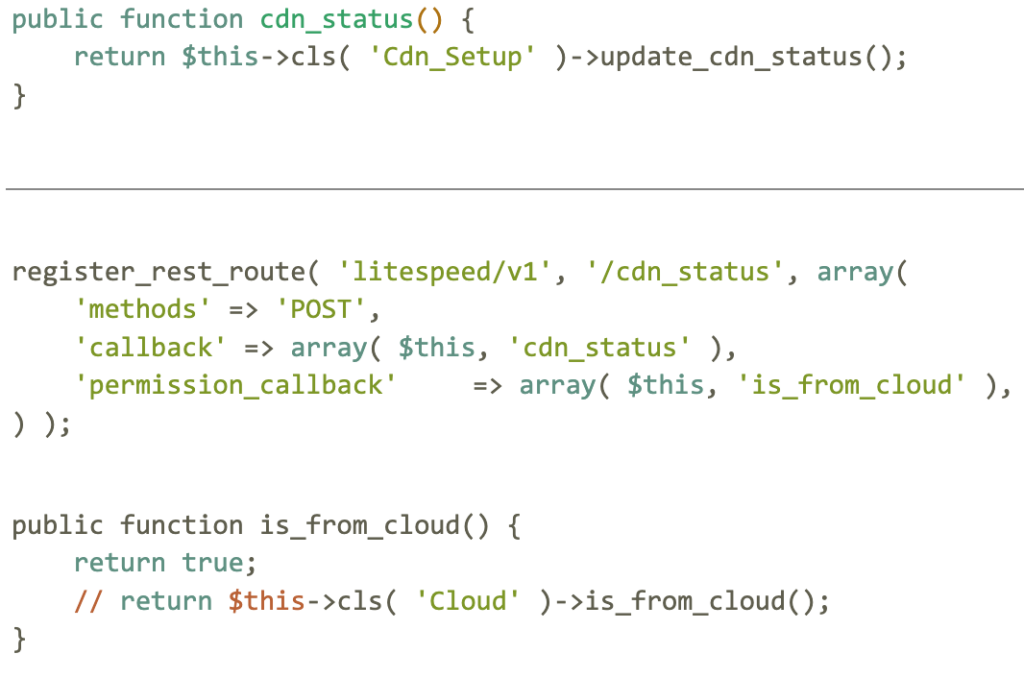
Additional information
Top origin IPs for these attacks
192.95.30.227
2607:5300:60:2de3::1
217.160.71.43
168.119.163.100
167.86.91.103
194.60.201.161
52.48.17.189
67.205.58.81
217.76.159.96
3.7.169.138
158.220.97.36
31.186.23.33
161.97.84.183
144.202.75.134
2a02:c207:2048:9276::1
37.128.144.106
84.19.174.40
104.225.216.192
66.33.203.134
192.241.240.50
157.245.134.118
31.135.90.40
185.70.93.6
Top origin countries for these attacks
Canada
Germany
United States of America
Ireland
Spain
India
Turkey
Netherlands
Russian Federation
Who discovered this vulnerability?
Patchstack security researcher Rafie Muhammad discovered the vulnerability in the LiteSpeed Cache plugin. Subsequently, the developer released the patch on October 25, 2023, followed by a full disclosure of the vulnerability on February 27, 2024.
How is your WordPress site at risk?
Your WordPress site is at risk if it runs the LiteSpeed Cache plugin v5.7 or earlier.
Hackers can exploit this particular vulnerability to conduct harmful activities, such as:
- Injecting malicious scripts for phishing or clickjacking attacks, or simply to redirect users to prohibited sites;
- Using compromised sites as command-and-control centers for broader attacks and eventually getting them blacklisted by Google;
- Installing backdoors to re-infect cleaned sites;
- Creating unauthorized admin accounts to seize complete control over sites; and
- Accessing and stealing sensitive information like user credentials and personal details stored in databases.
Addressing this vulnerability is crucial. To date, more than 40% of worldwide sites that use LiteSpeed Cache have not updated to the patched version of this plugin, despite the vulnerability being disclosed more than 5 months ago. This leaves them, and their visitors, exposed to potential attacks—unless, of course, they are using MalCare.
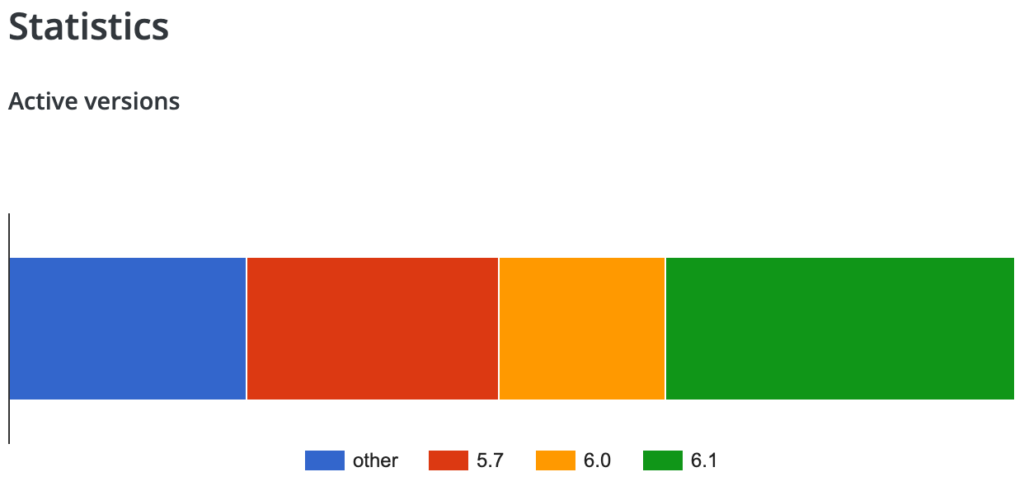
Hence, we strongly recommend you update the LiteSpeed Cache plugin on your WordPress site immediately, at least to v5.7.0.1.
What are the symptoms of a hacked site?
If you have reason to suspect that your WordPress site might have fallen victim to attacks exploiting this vulnerability, check for:
- a path containing litespeed/v1/cdn_status in your site’s firewall logs, or
- a plugin folder on your site named wp-cleansong, or
- a file named wp-blog-header.php or a folder of the same name on your site.
The presence of any of these could mean that your site is compromised. Take immediate action to update the LiteSpeed Cache plugin and scan and clean your site using MalCare.
How to clean your site?
If your WordPress site has been compromised, there’s no need to panic. You can take the following steps to restore and fortify your site’s security:
- Scan and clean with MalCare: The first step should be to install MalCare. Its advanced technology not only swiftly removes malware but also shields your site against future threats with its Atomic Security.
- Inspect user roles and permissions: Review the roles and permissions assigned to all users. Immediately revoke access if you find anything out of place.
- Refresh WordPress salts and security keys: This action forces all users to log out and ends all active sessions, boosting your site’s defense. Conveniently, MalCare facilitates the resetting of WordPress salts and security keys as part of the cleanup process.
- Update login details: Change your admin password without delay. Make sure all users are logged out, prompt them to reset their passwords, and encourage the creation of robust new ones.
- Strengthen login protocols: Implementing two-factor authentication (2FA) and limiting login attempts can significantly diminish the chances of unauthorized entries.
- Stay vigilant with monitoring: With MalCare, you’re well-equipped in this area. It monitors your site for unusual activities and promptly notifies you of any potential threats, continuously scanning for malware.
How does MalCare protect your site against such attacks?
MalCare provides a thorough protective shield for your WordPress site through several strategic actions:
MalCare’s comprehensive suite of tools wraps your WordPress site in a robust security blanket, employing a proactive and durable strategy to safeguard your online presence.
Category:
Share it:
You may also like

MalCare Ensures Unmatched Protection Against User Registration Privilege Escalation Vulnerability
Imagine discovering that your WordPress site, which should be secure and under strict control, has suddenly become accessible to unauthorized users who have the same administrative powers as you. This…

MalCare Ensures Proactive Protection Against WP-Members XSS Vulnerability
MalCare continues to protect its customer sites from all kinds of attacks, even the ones exploiting zero-day vulnerabilities. The recent stored cross-site scripting (XSS) vulnerability found in the WP-Members Membership…
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








