MalCare Proactively Blocks Attacks on LayerSlider SQL Injection Vulnerability
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

In our recent data, we have seen a number of attacks trying to exploit a SQL injection vulnerability, recently discovered in the LayerSlider plugin.
This vulnerability is a critical one, considering its low barrier for attacks. Attackers do not need any authorization or elevated user roles to mount such attacks. Moreover, while this particular method of SQL injection is quite intricate, it is a frequently and successfully used one to get information from vulnerable databases.
MalCare’s Atomic Security has been protecting sites from these attacks, even before the vulnerability was discovered. Unlike the majority of WordPress firewall providers, the attacks were prevented proactively by MalCare—without the need of virtual patch. This means, sites under MalCare’s protection had strong defenses right from the beginning.
What is the LayerSlider plugin vulnerability?
Plugin information
- Vulnerable plugin version: v7.9.11 and v7.10.0
- Patch release version: v7.10.1
LayerSlider is a paid slider plugin. It boasts of being a visual web content editor, a graphic design software, and a digital visual effects application all in one. It helps create popups, professional animations, rich web content, and one-page templates for WordPress websites with ease.
About the vulnerability
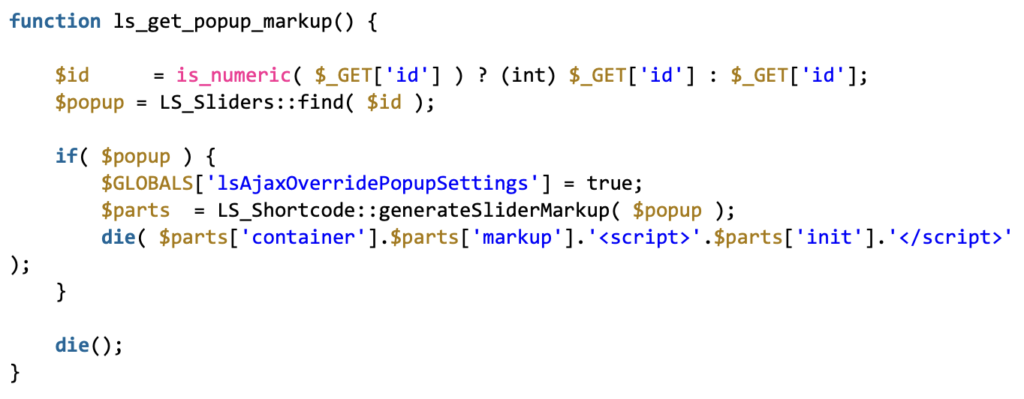
The LayerSlider vulnerability is due to an insecure implementation in code, and therefore it permits malware to be inserted via SQL injection. The vulnerability is in the ls_get_popup_markup() function, where the user-provided id parameter is not properly sanitized before being used. This oversight could lead to a time-based SQL injection attack if the parameter were to be manipulated by an attacker.
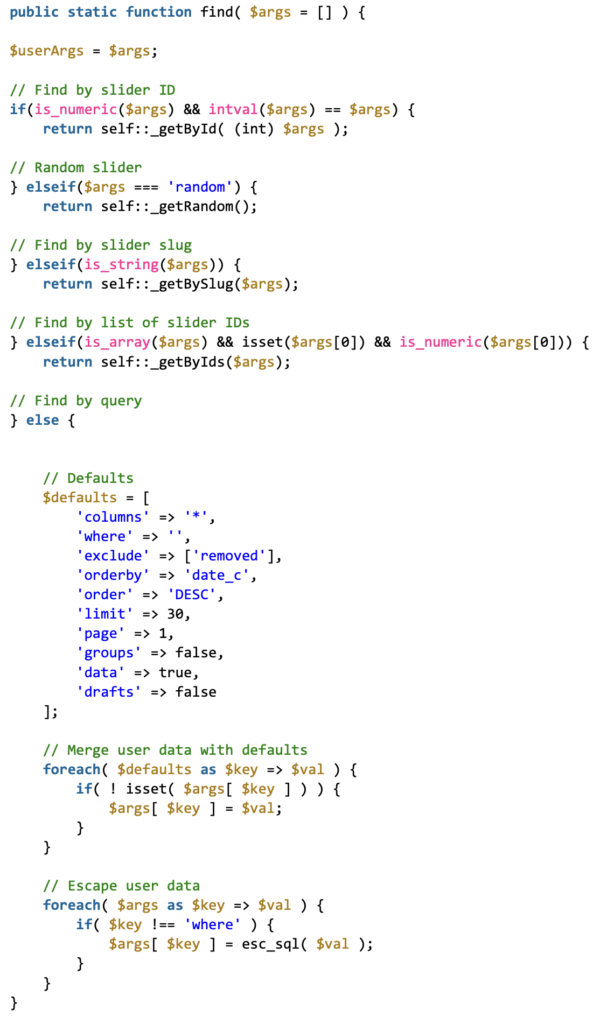
If the id parameter is not a number, it is directly passed on to the find() function in the LS_Sliders class without being sanitized. This function handles the parameter differently based on its type:
The SQL query does not employ WordPress’s $wpdb->prepare() function, which is crucial for preventing SQL injection attacks. This function ensures that SQL queries are parameterized, blocking attackers from injecting malicious SQL.
Because the query structure prevents union-based attacks, attackers might turn to a time-based approach instead. They could use SQL CASE statements along with the SLEEP() command, gauging the response times to infer information from the database stealthily.
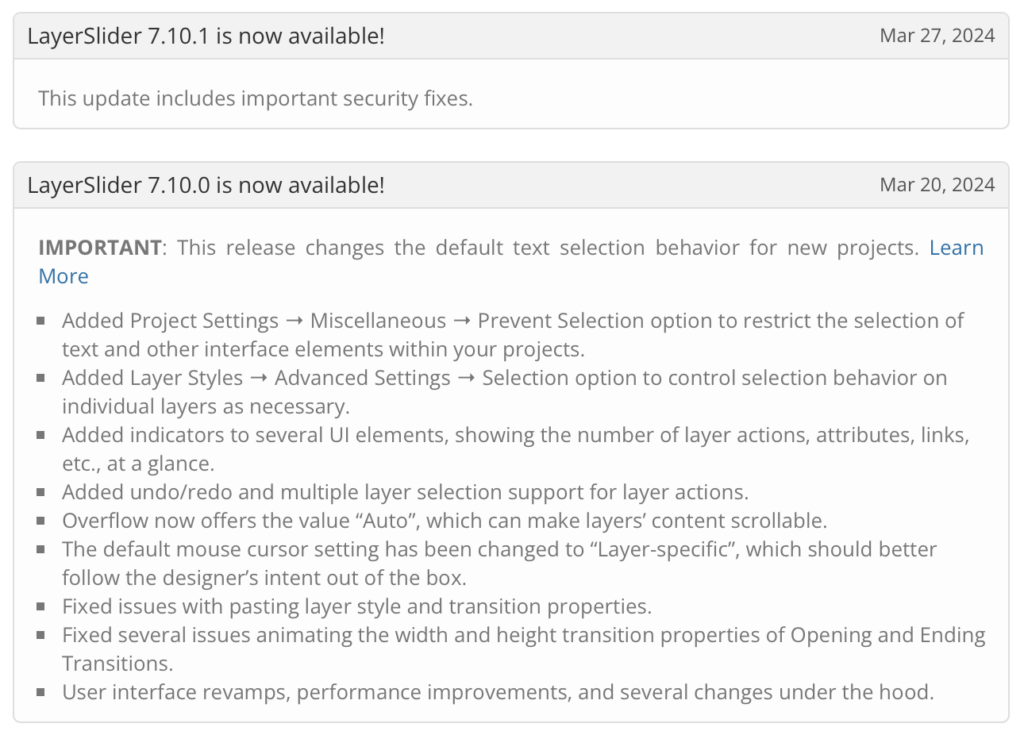
The vulnerability has now been fixed with the release of LayerSlider v7.10.1 on March 27, 2024.
Additional information
Top origin IPs for these attacks
138.68.139.21
171.247.178.238
167.99.197.61
68.183.41.92
165.232.102.37
Who discovered this vulnerability?
The LayerSlider SQL injection vulnerability was discovered by independent WordPress security researcher AmrAwad, who reported it to Wordfence’s Bug Bounty Program. Consequently, Wordfence informed Kreatura, the plugin developers, on March 25, 2024, following which a patch was released on March 27, 2024.
How is your WordPress site at risk?
Your WordPress site is at risk if it runs the LayerSlider plugin v7.10.0 or earlier.
Hackers are always on the lookout for ways to exploit vulnerabilities, including SQL injection vulnerabilities in WordPress plugins like LayerSlider. Here’s how they might take advantage of such gaps:
- Extracting sensitive data: Hackers can use SQL injection to access sensitive information stored in the WordPress database. This includes user profiles, email addresses, passwords (even if they’re hashed, they might try to crack them), and any personal data stored on the site.
- Modifying database information: Attackers can not only steal data but also alter it. This could mean changing prices in an online store, modifying user privileges (elevating a normal user to admin), or inserting malicious content into posts or pages.
- Website defacement: Using SQL injection, hackers can deface a website, replacing its content with their own messages. This is often done to spread a particular message or simply to prove it can be done.
- Denial of service: In some cases, the goal might be to make the WordPress site unavailable to its users. By manipulating SQL queries, they can delete crucial data or overload the database, causing the site to crash.
- Planting backdoors: Hackers could use SQL injection vulnerabilities to plant backdoors in the WordPress site. This would allow them ongoing access to the site’s backend, even if the initial vulnerability is fixed.
Hence, we strongly recommend you update the LayerSlider plugin on your WordPress site immediately, at least to v7.10.1.
What are the symptoms of a hacked site?
If you have reason to suspect that your WordPress site might have fallen victim to attacks exploiting this vulnerability, check for:
- a record in your site’s firewall logs containing both the path /wp-admin/admin-ajax.php and an action on ls_get_popup_markup
- a query in the form of query_string contains id[where] in your site’s database logs
The presence of this path could mean that your site is compromised. Take immediate action to update the LayerSlider plugin and scan and clean your site using MalCare.
How to clean your site?
When your WordPress site gets hacked, it’s important to stay calm. Here are effective steps to recover and strengthen your site’s security:
- Start with a MalCare scan: Install MalCare to quickly eliminate any malware and to fortify your site against future attacks with its Atomic Security feature.
- Update plugins and themes: Regularly check for and apply updates to your plugins and themes. Outdated plugins can contain vulnerabilities that hackers exploit. MalCare’s dashboard can alert you to outdated plugins and themes, making it easier to keep them updated and secure your site further.
- Update WordPress salts and security keys: Doing this logs out all users and ends all active sessions, a boost for your site’s security. MalCare makes this easy as part of its cleanup process.
- Check user roles and permissions: Look over the roles and permissions of all users. If anything seems off, remove access right away.
- Change login details: Immediately change your admin password. Ensure all users are logged out, ask them to update their passwords, and encourage strong, new passwords.
- Enhance login security: Add two-factor authentication (2FA) and limit login attempts to reduce the risk of unauthorized access.
- Keep an eye on your site with monitoring: MalCare has you covered here. It watches over your site for any odd activities, alerts you to possible threats, and keeps scanning for malware.
How does MalCare protect your site?
MalCare offers comprehensive security for your WordPress site with several key features:
- Quick malware detection and cleanup: MalCare diligently scans your site every day, automatically searching for malware. If malware is found, its powerful removal tool quickly gets rid of it, ensuring your site is secure and healthy once again.
- Strong firewall protection: Included in MalCare is Atomic Security, an advanced firewall that watches over incoming traffic, stopping malicious attacks in their tracks. It’s regularly updated, keeping your site safe from the latest threats.
- Vulnerability notifications: MalCare is always on the lookout for potential vulnerabilities in your plugins and themes. If any issues are spotted, it alerts you right away, allowing you to strengthen your site’s defenses.
- Bot defense: Aware of how bots can slow down your site, MalCare puts up strong defenses to keep these automated nuisances at bay, helping your site run smoothly.
- Efficient backups: With MalCare’s automated, offsite backup system, you’re always one step ahead. Should anything go wrong, these backups ensure you can quickly bounce back.
MalCare wraps your WordPress site in a protective layer, using a blend of proactive measures and strong defenses to keep your online presence secure.
Category:
Share it:
You may also like
Fix Pharma Hack on WordPress and SEO
Pharma hack is a prolific malware that redirects visitors from your site to an online pharmacy that sells Viagra, Cialis, Levitra, Xanax, Tadalafil, and other drugs. It also shows up…
How To Protect Your WordPress Website From File Upload Vulnerability?
One of the core strengths of WordPress lies in its file upload functionality. The ability to seamlessly upload and integrate various types of files, from images and documents to multimedia…

MalCare Ensures Unmatched Protection Against User Registration Privilege Escalation Vulnerability
Imagine discovering that your WordPress site, which should be secure and under strict control, has suddenly become accessible to unauthorized users who have the same administrative powers as you. This…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








