Fix Contact Form 7 Vulnerability on WordPress
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

Contact Form 7 is one of the most popular WordPress plugins with almost 10 million active installs. Over the years, it has been revealed to have several major security flaws. Unsurprisingly, these vulnerabilities have caused many sites to be hacked.
In particular, there’s one from 7 years ago – the privilege escalation vulnerability. Other vulnerabilities have been relatively minor and not exploited to much extent. But the privilege escalation vulnerability still causes major security breaches and hacks in websites all over the world.
We’ll explain more over the course of this article and give you a surefire way to fix the Contact Form 7 privilege escalation vulnerability.
TL;DR: If you suspect your website has been hacked, install the MalCare security plugin. It will scan your WordPress site and identify the hack. You can clean your site instantly and protect your site from future attacks as well.
What is the Contact Form 7 vulnerability?
The Contact Form 7 vulnerability allows hackers to upload malware to the WordPress uploads folder; specifically the /wp-content/uploads/wpcf7_uploads/ folder. Once the file is uploaded, the hackers can then take over control of the entire website.
Now, one would imagine that deleting the contents of the wpcf7_uploads folder would resolve the problem. But that’s not true. So, if you’ve tried that method and failed, you’re not alone.
Over time we have seen that hackers spread malware all over the site, once they gain access. The Contact form 7 vulnerability gives complete access to the hacker, and thus the hacker can, and usually does, infect thousands of files and the database.
Obviously, this complicates the cleaning process considerably. Therefore it is important to install a good scanner and then a cleaner to clear out every trace of this pernicious malware.
How to fix the hacked site
As we’ve already explained, fixing a website that got hacked because of a privilege escalation vulnerability is incredibly difficult. It’s not as simple as deleting a malicious file from a specific folder.
The second the hacker uploaded the file, they got access to every folder on the server. This means that the hacker could have planted malware on literally any file or database table. They may even have left backdoors to reinfect your website another time.
With that in mind, we’re going to give you 3 simple and effective steps to fix this issue. Remember to follow along in this exact order:
Step #1: Find and remove the malware
If you’re using Contact Form 7, we highly recommend that you install MalCare right now and get a FREE malware scan of your website. It doesn’t really matter if there are visible signs of your WordPress site being hacked. There are hundreds of malware that can lie dormant on your server.
This step is crucial. As we’ve said before, deleting the uploads folder is inadequate. Many of you may not even know how to do this in the first place. Using a malware scanner, you can pinpoint the location of the malware and remove it once and for all.
We recommend using the MalCare Security Plugin for a server-level scan of your entire website. MalCare is capable of detecting hidden and even unknown malware in your website’s files and database.
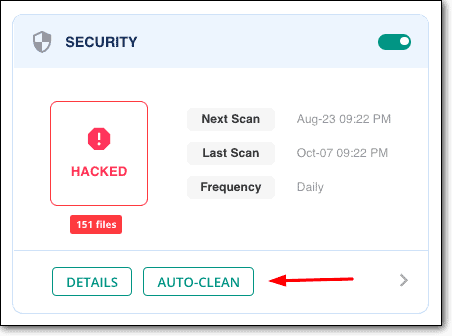
You can also remove all traces of malware from your website instantly by using the Auto-Clean option. In a matter of seconds, MalCare will remove the malware from your website without breaking the code.
Now, there are many security “gurus” who insist that removing the malware from your website manually is a much better option. But the reality is that knowing how to do that requires some serious coding chops. Unless you’re a cybersecurity professional yourself, we do not recommend this method under any circumstances.
That said, if you’re interested in knowing more about how to remove malware manually from a WordPress website, we have an article on that topic as well.
Again, we don’t recommend that under any circumstances.
Step #2: Remove ghost admins
If you followed along with the article this far, then you’ve managed to remove the malware safely from your website. So, before you make any further changes, we strongly recommend that you backup your site now.
One of the most dangerous changes that hackers can make using the Contact Form 7 privilege escalation vulnerability is to create fake administrators. This is such a subtle change that most websites never notice it at all.
The dangerous part is that even if you remove malware from your website, no malware scanner will be able to detect a fake admin user.
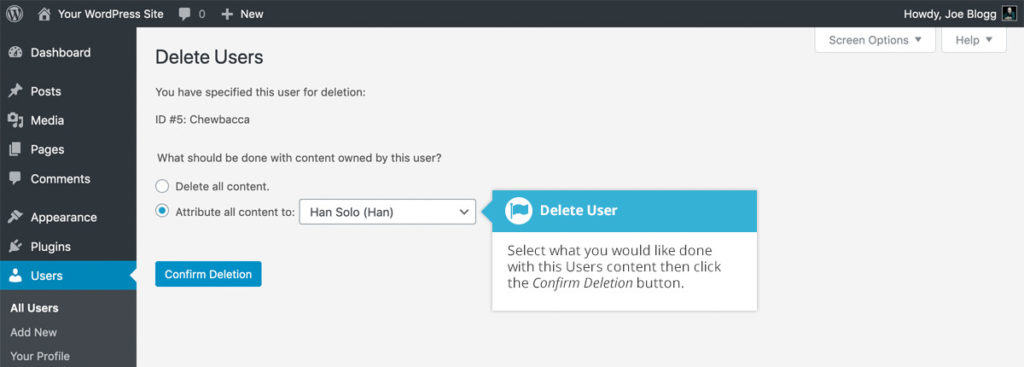
In your WordPress dashboard:
- Select Users > All users
- Hover over the username you want to delete and click the Delete link that comes up.
- You’re taken to a Delete user page, with two options: Delete user posts or assign posts to a new user.
- Select “Attribute all content to:”
- Choose the new username you created as the new author for these posts.
- Click the Confirm Deletion button.
Step #3: Update Contact Form 7
The Contact Form 7 privilege escalation vulnerability was patched by the original developer in version 5.0.4. Currently, Contact Form 7 is distributing version 5.3.2 and we highly recommend that you update your plugin to the latest version.
Updating the plugin removes the vulnerability. This means that a hacker cannot use the same vulnerability to break into your website any longer.
How to prevent the hack in the future
There are a few measures you can take to safeguard your website against hackers exploiting similar security vulnerabilities. The Contact Form 7 privilege escalation vulnerability is just one instance of a popular plugin posing security threats to your website.
Hackers keep finding new vulnerabilities every single day. With that in mind, here are a few basic tips to safeguard your site against future attacks:
Install MalCare
We highly recommend that you install MalCare. MalCare comes with its own website security scanner that automatically detects malware on your website. There’s very little manual action required from your end.
You also get a one-click malware removal tool that will make your life much easier.
More importantly, you also get an advanced firewall that blocks out malicious IP addresses and bots from country or device even before your website is loaded. This keeps your website safe and secure against the most common attacks.
MalCare runs on a cutting-edge learning algorithm that keeps getting smarter. If MalCare encounters a particular malware or malicious IP in one of the 250,000+ websites that it protects, it automatically prevents that for all the websites on its network.
Update themes and plugins
Themes and plugins are incredibly complicated code. Sometimes, they’re more complex than the WordPress core itself. Such complexity often causes security flaws such as the Contact Form 7 privilege escalation vulnerability.
This may come as a surprise to you, but there are hackers who spend every waking moment of their lives looking for such vulnerabilities to exploit.
Keeping your themes and plugins updated is a good way to secure your website as new versions patch these vulnerabilities. So, make sure you update your WordPress plugins and themes as and when new versions are available. We also recommend deleting any themes and plugins that you don’t use anymore.
WordPress hardening
WordPress hardening is a set of security measures that you can take to make it extremely difficult for hackers to modify your website even if they manage to gain access.
Now, hardening is a pretty broad topic. Some of these measures are quite simple such as changing the user passwords. But there are also more complicated measures such as changing salts and security keys.
So, we created an entire article on WordPress hardening – the safe way.
With that, your WordPress website is secure from not just the Contact Form 7 privilege escalation but also a bunch of other attacks including:
Privilege escalation hacks explained
This section is a bit technical but if you’re using the Contact Form 7 plugin on your WordPress site, you’ll probably want to understand what’s happening.
The Contact Form 7 privilege escalation vulnerability is exploited in two steps:
- Step 1: Gain access to a lowly subscriber role in a WordPress website.
- Step 2: Use the vulnerability to gain unrestricted administrative access.
WordPress websites assign the lowest access level to a new user by default – a WordPress subscriber. Now, this role won’t fetch you enough authority to change anything on a WordPress website. But the Contact Form 7 privilege escalation attack allows the hacker to change their user role to anything that they please.
What does that mean exactly?
Contact Form 7 is one of the most powerful WordPress plugins, used to create forms of different kinds. On submission, the data accepted by its forms is stored in a folder called ‘wp-content’ on your WordPress website.
Commonly, this folder contains content of all kinds from different parts of the website. But these are all public information and none of the data in this folder is sensitive or personal.
This makes a lot of sense for more reasons than one. Anyone submitting data to your forms is a WordPress subscriber. They shouldn’t have any access to any sensitive information on the website.
On the other hand, a form is usually created by an admin or an editor. These are user roles that require a lot of freedom and access to specific parts of the website. So, how exactly does Contact Form 7 assign a new WordPress user the role of subscriber and not an administrator?
In simple terms, Contact Form 7 uses a parameter called ‘capability_type’ to define user permissions for read, edit, and delete functions. The flaw exists inside this parameter and it allows a hacker to upload files directly to the home directory of WordPress.
From this folder alone, a hacker might be able to deface your site completely or launch spamvertising attacks.
In some cases, the attacks can be dangerous enough to get your website blacklisted by Google.
But the privilege escalation vulnerability allows attackers to launch a much more dangerous attack. There are also files outside the wp-content folder such as your wp-config file and .htaccess file.
Now, these files contain database credentials and configurations of your website. So, a hacker exploiting the Contact Form 7 privilege escalation vulnerability can gain access to these files by modifying a user role’s capabilities.
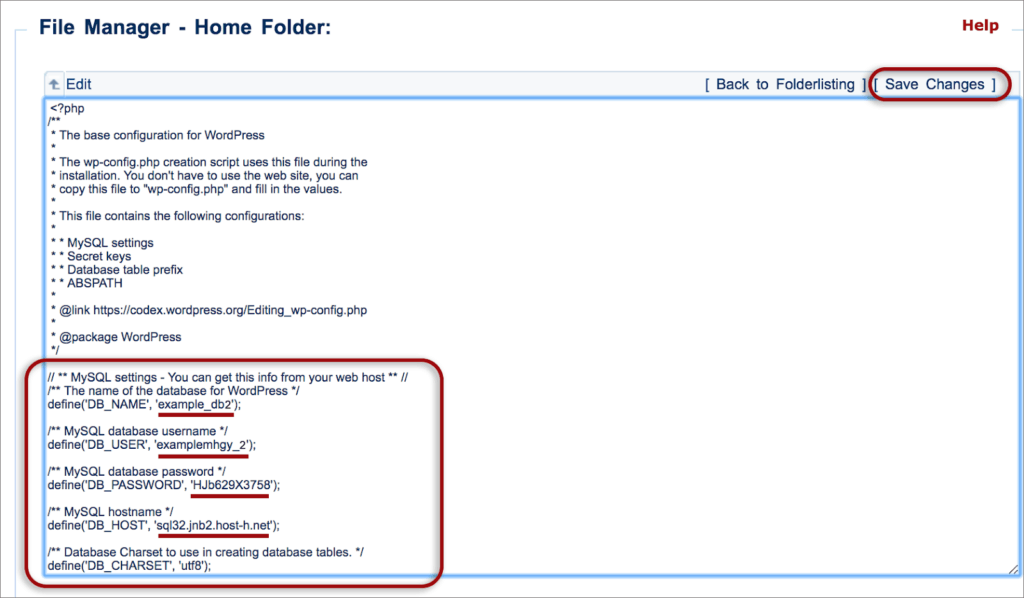
Within minutes, the hacker can find access credentials to your entire website. Or worse, they can create a ghost administrator account so that they can get direct unrestricted access to the entire website.
This is incredibly dangerous as it enables the hacker to edit the form and grant themselves access to files outside wp-content. It could also be used to edit what kinds of user inputs the forms can accept. The vulnerability essentially allows any user roles to make changes to the website.
Unrestricted file upload vulnerability explained
Some forms accept files, such as a resume or ID proof. Standard formats like PDF, JPEG, PNG, and GIF are acceptable and shouldn’t cause any trouble on your site.
However, the Contact Form 7 plugin vulnerability allows a user to change the types of files accepted. This vulnerability recently affected over 5 million websites that use Contact Form 7 and is known as the unrestricted file upload vulnerability.
The unrestricted file upload vulnerability means your website could start accepting executable file formats such as PHP and ASP. Check especially for double extensions such as .php.png.
These files execute commands and functions on your site. This means a hacker can submit a PHP file with a malicious script through a contact form created using Contact Form 7.
This is a variant of an XSS attack and can be used to:
- Create a backdoor on your website that would allow a hacker to access it when he wants.
- Create ghost admin users that will grant them access through your login page.
- Modify the content on your site to sell or promote illegal products and drugs.
- Redirect your visitors to malicious or adult websites.
There are a bunch of other attacks that a hacker can launch quite effectively with very little effort once they gain access to your website. It’s always a better option to prevent the attacks as far as possible.
We highly recommend installing a malware scanner that offers round-the-clock malware scanning and a WordPress firewall to protect your website against future attacks.
What’s next?
Hackers find all sorts of ways to break into your site. They can use brute force attacks to guess your access credentials, exploit Cross site scripting (XSS) vulnerabilities, and steal your browser cookies. There’s really no end to this madness.
To truly and completely protect your website from security threats and attacks, we recommend that you install MalCare. The firewall will proactively block hack attempts and its scanner will check your website every day.
Also, check out our tips on WordPress hardening. You can secure your website from the MalCare dashboard with a few simple clicks and harden your website security.
FAQs
Is Contact Form 7 secure?
No. Although the current version has no known vulnerabilities, older versions of Contact Form 7 are riddled with security flaws. The simplest way to patch the vulnerabilities is to update to the latest version. But we also recommend that you scan your website for malware just in case.
Does Akismet work with Contact Form 7?
Yes, but Akismet is to protect against spam form inputs. It doesn’t fix the privilege escalation vulnerability. To patch the vulnerability, we recommend updating to the latest version of Contact Form 7 immediately.
What is privilege escalation and why is it important?
Privilege escalation is a vulnerability that hackers can exploit to gain access to files and databases of a website that are otherwise restricted. Using this vulnerability, hackers can gain access to any sensitive information on your website and even deface your content at will.
What is the most likely mechanism of privilege escalation?
Most WordPress plugins and themes come with many privilege escalation vulnerabilities. Some of the most common causes are cross-site scripting, improper cookie handling, and weak passwords.
What are good alternatives to Contact Form 7?
There are several alternatives to Contact Form 7. In terms of security, though, we would recommend the latest version of Ninja Forms, Gravity Forms, and Visual Form Builder plugins.
Share it:
You may also like
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…

MalCare Proactively Defends Against Icegram Express SQL Injection Vulnerability
MalCare’s recent data has revealed numerous attempts to exploit a newly found SQL injection vulnerability in the Icegram Express plugin. Attackers commonly use this sophisticated SQL injection technique to extract…

Atomic Security’s Deep WordPress Integration Helps Protect Against Core XSS Vulnerability
The recent WordPress core vulnerability is a critical one, primarily because of two reasons. Firstly, it affects the WordPress core itself, which means that every WordPress site is vulnerable to…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








