Reasons Why Hackers Hack WordPress Sites
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

Why Hackers Hack: WordPress websites are a popular target for hackers. 714 new WordPress sites are created every day which makes WordPress the fastest growing content management service in the world. This sort of popularity has a price. It comes with a target placed on the back. It explains why hackers choose to target WordPress more than any other CMS but the question remains, what do hackers gain from hacking websites?
Websites can be hacked with a reason or randomly because hackers have learned how to utilize every website. To understand the exact nature of the payoff, we must first understand the intentions of the hackers who can be categorized into three groups:
- Hacktivists
- White-hat hackers
- Black-hat hackers
Hacktivists
Activists who hack websites with the goal of bringing awareness to an issue are called hacktivists. A majority of the time hacktivists deface website pages and inject a piece of sensitive information they want the visitors to see. Take the Panama Papers leak where hacktivists broke into CIA and FBI websites, extracted official information and later posted them online. Another time hacktivists defaced the ISIS website with performance-enhancing drugs. Whether hacktivism is a crime is a matter of debate. While supporters cry it’s a form of free speech, opponents argue it’s trespassing of property that causes damage to brand visibility.
White-Hat Hackers
These hackers don’t have malicious intentions because they look for vulnerabilities that can be reported responsibly. White-hat hackers are either developers themselves or they are part of a security team responsible for weeding out vulnerabilities thus contributing to making the WordPress community a safe experience.
Black-Hat Hackers
Black-hat hackers are the ones who exploit vulnerabilities for their personal gains. They are generally feared and disliked because they often break into websites to steal or modify or utilize the resources of that site. In general most black-hat hackers don’t target specific websites since they are not looking to promote an agenda like the hacktivists nor are they looking for specific vulnerabilities for the greater good. They mostly use Kali Linux and are no strangers of using brute-forcing techniques to find usernames and passwords for hacking WordPress websites.
Why Hackers Hack WordPress Sites?
Their intention can be divided into 3 categories, namely:
- For Reputation
- Exploitation of Resource
- Access to Information
1. For Reputation:
Black-hat hackers who seek a reputation in the hacking community can be divided into two types – experienced hackers and script kiddies.
The script kiddies are amateurs who use readily-available tools to break into websites. Their main purpose is to gain recognition among their peer and they usually don’t have any malicious intentions. Besides the technical knowledge, the hacking community also counts the rampage one hacker is able to create on his own. Since script kiddies are amateurs, performing hacks for them is a learning experience. It’s a road towards higher experience and greater reputation and acceptance in the hacker’s community. A script kiddy becomes an experienced hacker when he no longer relies on tools to perform hacks and can bypass usual security measures using the malicious code that he crafts.
Experienced hackers are interested in climbing the ladder of reputation that’ll enable them power over the community and also they’ll get paid well for their services. Some years back there was a forum called Darkode which was somewhat like an online black market. Black-hat hackers had profiles on the website and there was a ranking system in place. The ranking would depend on criteria like the number of websites hacked, difficulties faced while making the hack, how big the sites were, and finally how satisfied the customers were with the service (assuming that the hack was made following a request made by a customer). The higher one ranked, the more was the recognition and customers would pay more for their services.
If it’s a big website with a good reputation, or if the hackers had to overcome great security barrier, they’d be revered by a community. Experienced hackers are also proficient in utilizing resources. Not all information they acquire is useful to them, therefore they sell them to buyers who are ready to pay a hefty amount for the extracted data.
2. Exploitation of Website Resources
What does a website resource constitute? Generally, it involves the website database, site server, its users as well as visitors. This is what a lot of black-hat hackers are after. Several hackers break into WordPress with the intentions of using the website resources for executing actions like:
- Attacking other websites
- WordPress Sending spam emails
- Storing illegal files
- Mining cryptocurrency
- WordPress Pharma hack, etc
Attacking Other Websites
Using one site to attack other websites are risky because they are easy to track. Also relying on one site means, if it’s blacklisted, the hack operation is doomed. This is why hackers are always scavenging for new websites that they can use to attack targeted websites. More websites mean larger scale of execution.
Sending Spam Emails
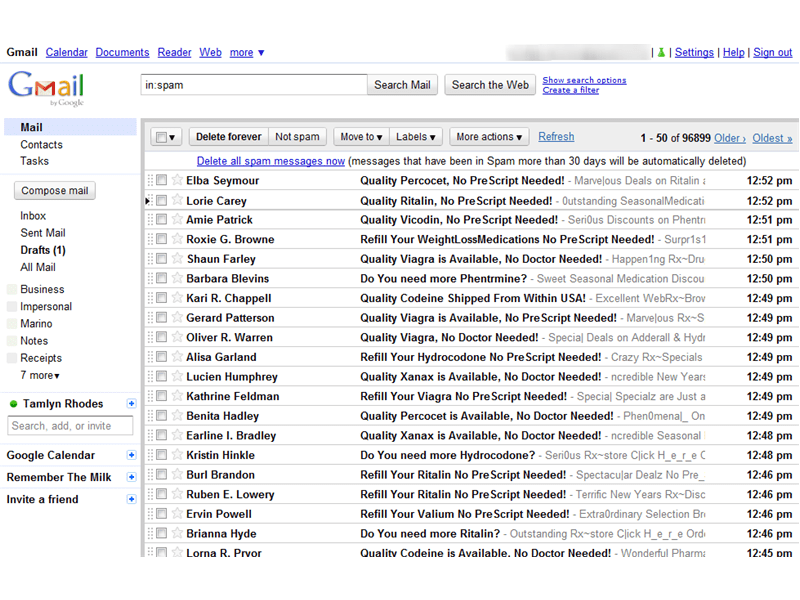
Anyone who has had an email account must have come across spam emails. Spam emails are unavoidable. Hackers often use compromised sites to send hundreds of thousands of spam emails for purposes like acquiring bank credentials or selling illegal drugs, etc. Most of the time, website owners are unaware that their WordPress website has been hacked and it’s being used to send spam emails. Hackers like to keep it that way because the moment the site owner finds out they’ll clean the site, wipe off backdoors and the hacker will no longer be able to access the site nor use its resources.
Storing Illegal Files
Sometimes hackers store millions of files like shareware, mp3 videos, pirated movies that tend to take up a lot your website disk space. When these files are run on your server, they tend to bog down your site. When web hosts find out they suspend the hacked site and Google blacklists the site. This means you lose organic traffic and your reputation takes a hit.
Mining Cryptocurrency
In today’s time, the most popular cryptocurrency is Bitcoin. It’s generated through a process called ‘mining.’ Over the last few years, Bitcoin has become such a rage that the hacking community has taken a particular interest in it, especially individuals who want to get rich quickly. For this purpose, they break into websites and install cryptocurrency miners that generate cryptocurrency every time a visitor requests a page of the hacked site. This has adverse effects on the website like if Google finds out, the hacked site will be blacklisted.
Pharma Hacks
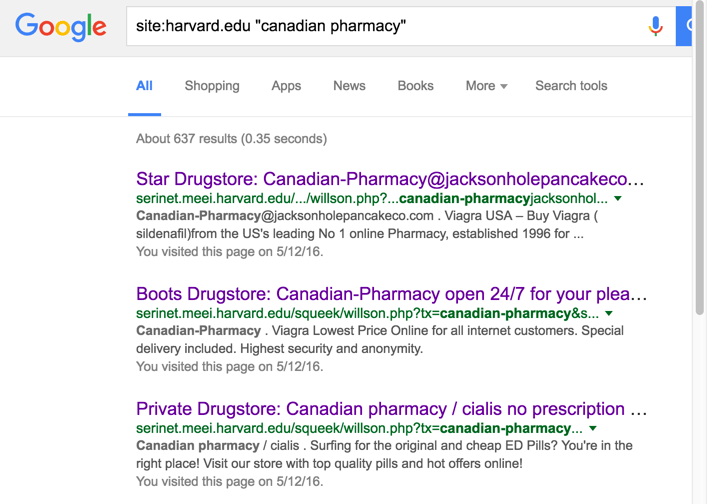
On the internet, there are restrictions on a few pharmaceutical drugs which prompts some drug companies to hacks websites, manipulates search results with spammy keywords and fills its pages with illegal drug advertisements. They do it to take advantage of the visitors to your website who’d be repulsed and never visit your site again. Or they’ll click on the ad and will be redirected to the hacker’s website.
3. Accessing Information
Data, especially for e-commerce websites are valuable. These data are not available publicly and therefore they are unique. Black-hat hackers sometimes hack sites to retrieve data or information like contact addresses, medical records, personal preferences, pictures, financial information, etc. Hackers use this information:
- To damage reputation by publishing sensitive data.
- To sell this sensitive information online.
- To blackmail the website from where the data has been retrieved and much more.
Publishing Information Without Consent
It need not be only financial information! Even data like email address can be used to launch a massive spam attack. Other malicious attempts could be along the line of damaging the reputation of an individual by posting sensitive pictures. If the hacked site conducts online business, publication of customer information will not just damage the reputation of the establishment but also ruin the trust of your customers.
Selling Information Online
Some sell data of celebrities (take the case of Pippa Middleton’s iCloud photos) for monetary benefits, other target medical websites for data like social security numbers, healthcare, and medical information. These cases of identity theft prove that hackers don’t just target financial information. There is a good reason too. For selling financial data, hackers have to race against time because information like the password can be changed. Moreover, people whose data are stolen take immediate precautionary actions like changing banks, blocking cards, etc. Hackers can get a good price for stolen financial data only if they are still valid. The validity of identity-theft is much longer and therefore the returns are much higher.
One can’t help but think what do the buyers do with the information? Using the information, buyers:
- Create fake IDs they use to execute malicious intentions
- Apply for prescribed drugs
- Take loans from banks
- Get credit cards using someone’s else’s identity
Since there is a good demand for these data which puts websites with any kind of user-information at great risk. With gains like the ones we mentioned above, it’s not surprising that black-hat hackers are in demand. And because the payoffs are so high hackers go to length to procure sensitive information. Often after extracting information, hackers leave behind backdoors which enables them to access the website later. Therefore, the website owner must plan for the worst from beforehand. Follow the best security practices and then hope for the best.
Category:
Share it:
You may also like

MalCare Ensures Proactive Protection Against WP-Members XSS Vulnerability
MalCare continues to protect its customer sites from all kinds of attacks, even the ones exploiting zero-day vulnerabilities. The recent stored cross-site scripting (XSS) vulnerability found in the WP-Members Membership…
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…

MalCare Proactively Defends Against Icegram Express SQL Injection Vulnerability
MalCare’s recent data has revealed numerous attempts to exploit a newly found SQL injection vulnerability in the Icegram Express plugin. Attackers commonly use this sophisticated SQL injection technique to extract…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








