Cookie Stealing in WordPress: Understanding the Risks and Consequences
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

Cybercriminals can quietly steal information from unsuspecting website visitors by stealing their cookies. And while cookie stealing security advice online is typically geared towards users and site visitors, it’s important to understand that as a site owner, you’re also at risk from these types of WordPress attacks.
There are several ways that cookie stealing could cause problems for you. For example, if an admin is logged into the site and their cookies are stolen, this could lead to serious issues.
But don’t panic. In this article, we’ll discuss the dangers of cookie stealing and provide you with practical advice on how to safeguard your site and your users.
Cookie stealing is a serious threat to website security, potentially compromising sensitive user data and site functionality. Protecting against cookie theft involves implementing security measures like ensuring that your site has SSL encryption. Another important solution is to install a firewall with MalCare as a preventative measure.
What is cookie stealing?
At its core, cookie stealing is a form of cyber attack that involves stealing cookies from a user’s computer to gain access to their data or login information. Cookies are small text files that are stored on a user’s computer when they visit a website. They contain information about the user’s session and preferences, allowing the website to remember them and offer personalized experiences.
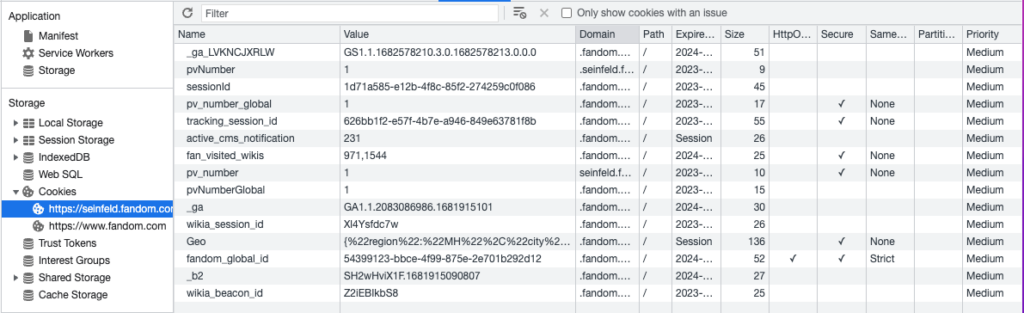
However, if a malicious actor gains access to a user’s cookies, they can use that information to hijack their session and access sensitive data. This is one of the mechanisms of session hijacking, a type of attack where an attacker takes over a user’s session to gain unauthorized access to a site.
It’s important to note that cookies themselves are actually the safest way to store session information on the user’s side, but they still require protection. WordPress uses cookies to keep users logged into sites, so they don’t have to keep logging in every time they need to do something on the site.
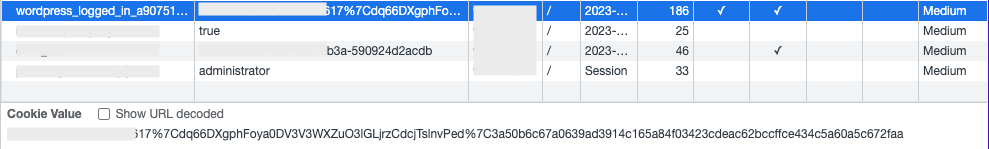
How are cookies stolen?
Understanding the various ways that cookies can be stolen is key to protecting your site and your users. Attackers use a variety of tactics to steal cookies, ranging from injecting malicious code into websites to tricking users into visiting fraudulent sites. Here are some of the most common methods of cookie theft:
1. Phishing attacks
In a phishing attack, attackers create fake websites or emails that mimic legitimate ones, tricking users into entering their login credentials or other sensitive information. Attackers can then use this information to steal cookies from the user’s browser.
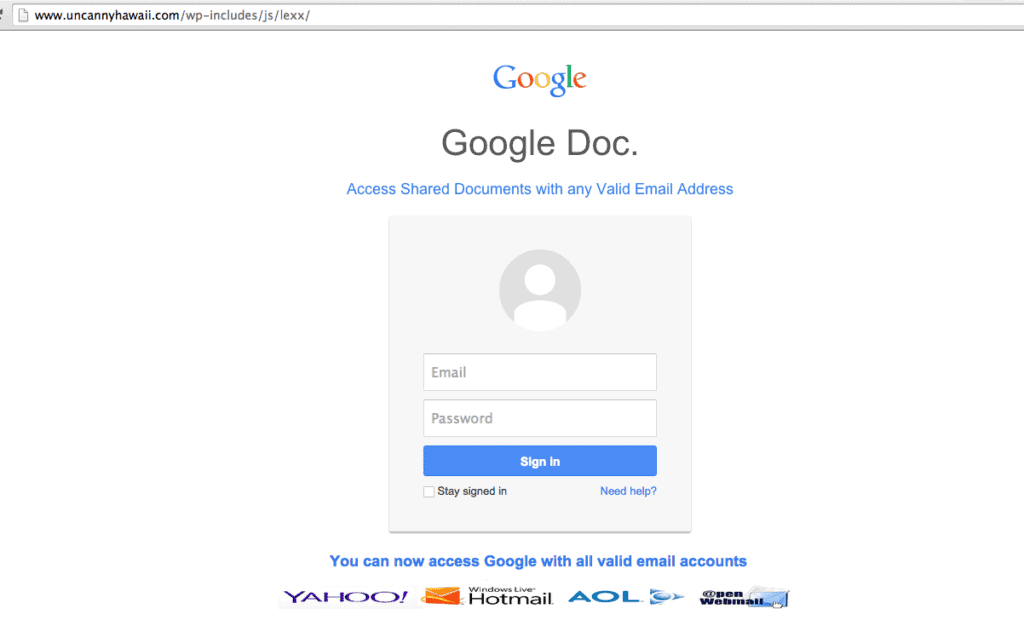
2. Malware from exploited vulnerabilities
Attackers can exploit vulnerabilities in website software to install malware that can steal cookies from users who visit the site. This method of cookie theft can be particularly dangerous as it can affect large numbers of users.
3. Man-in-the-middle (MITM) attacks
In a MITM attack, attackers intercept communication between the user’s browser and the website, allowing them to steal cookies or other sensitive information. This type of attack can occur on unsecured Wi-Fi networks, for example.
4. Trojans
Trojans are a type of malware that can give attackers access to a user’s computer, allowing them to steal cookies and other sensitive data. Trojans are often spread through email attachments or infected downloads.
With so many different ways that cookies can be stolen, it’s important to take steps to fix the gaps in security. In the next section, we’ll discuss some of the best ways to fight the cookie thieves.
How to recover from a cookie stealing attack?
Recovering from a cookie stealing attack can be a time-consuming and stressful process, but taking immediate action can help minimize the damage. Here are some steps you should take if you suspect that your site has been used to steal cookies:
- Scan for malware: Use a security plugin or scanner to search for any malicious code that may have been injected into your website. This can help you identify any vulnerabilities that attackers may have exploited to steal cookies. Use a comprehensive security solution like MalCare that can easily scan your site.
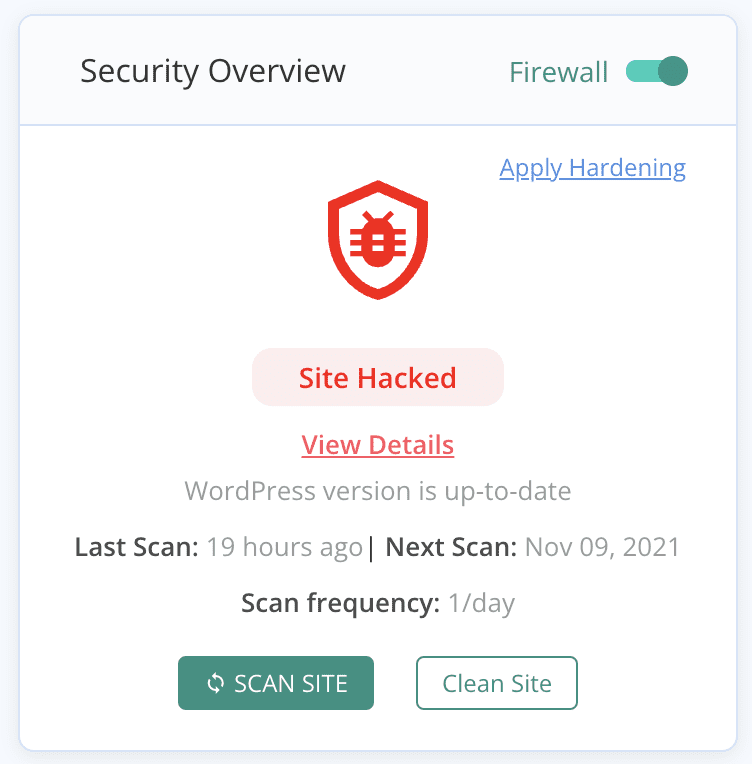
- Clean malware: If malware is found, remove it as soon as possible. Many WordPress security plugins have features that can help you automatically clean up your site. MalCare is a robust security plugin that can also clean any malware you’ve found on your site.
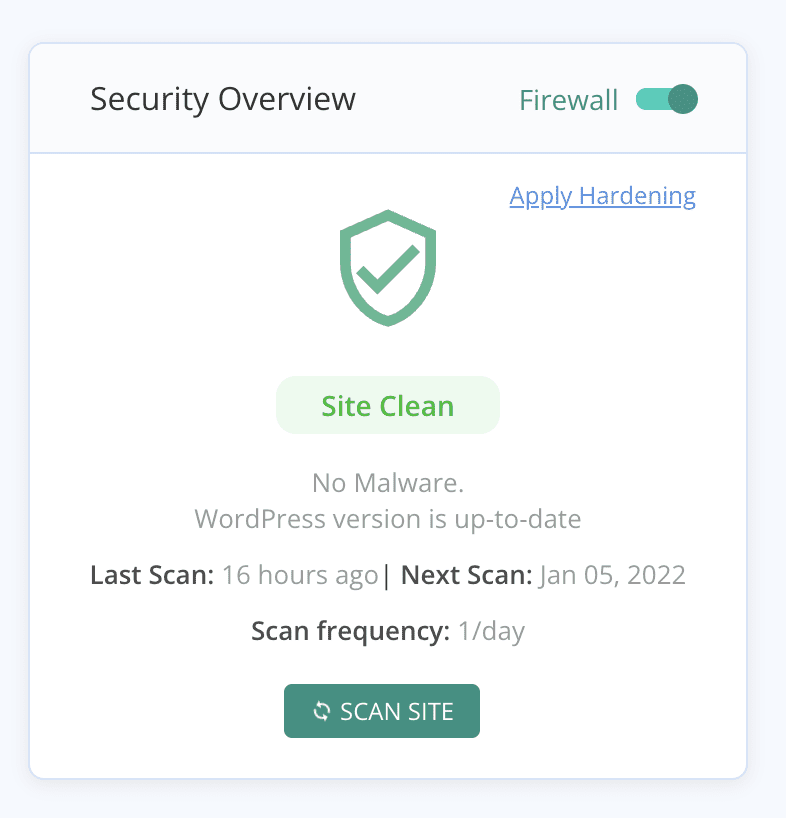
- Force logout of all sessions: Log out all users from their current sessions. This will invalidate any stolen cookies, preventing attackers from continuing to access user accounts.
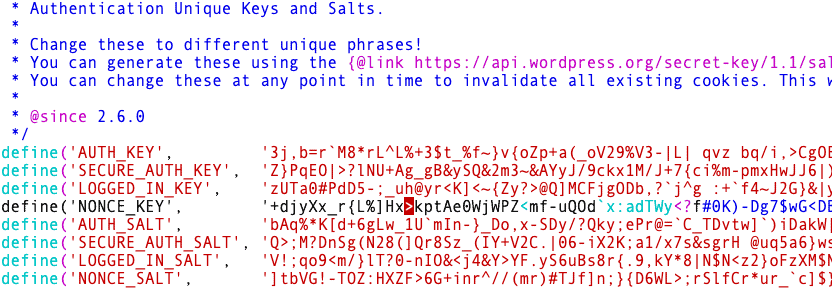
- Change passwords: Encourage users to change their passwords, and make sure that all administrative passwords are reset. This can help prevent attackers from gaining access to sensitive information. Also change the WordPress salts and security keys in the wp-config file. This will invalidate all sessions, and force log out any active users.
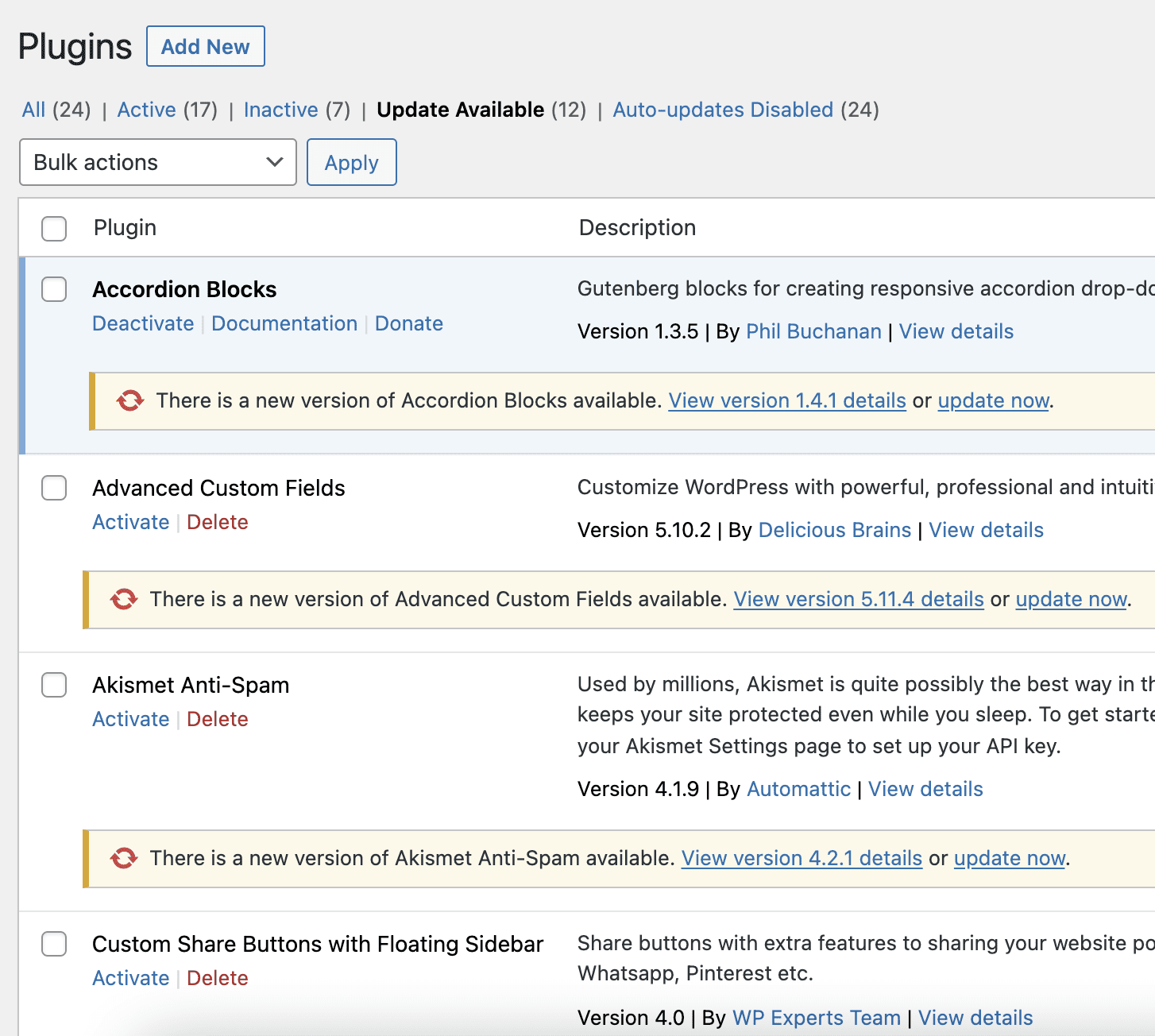
- Update plugins and themes: Make sure that all plugins and themes on your website are up-to-date. Vulnerabilities in outdated software can be exploited by attackers to steal cookies and other sensitive data.
How to prevent cookie hijacking?
Preventing cookie stealing attacks requires a proactive approach to website security. By taking the right precautions, you can help protect your users and your website from the negative effects of cookie stealing attacks. Here are some steps you can take to prevent session hijacking:
- Install a firewall: For the most effective defense against session hijacking attacks, install a firewall like MalCare. It can stop malicious traffic and filter out requests that exploit website code vulnerabilities. MalCare monitors incoming traffic and detects suspicious behavior or patterns related to session hijacking attacks. It also enforces security policies and rules to prevent session hijacking, such as blocking requests with suspicious session IDs or unauthorized access to sensitive resources.
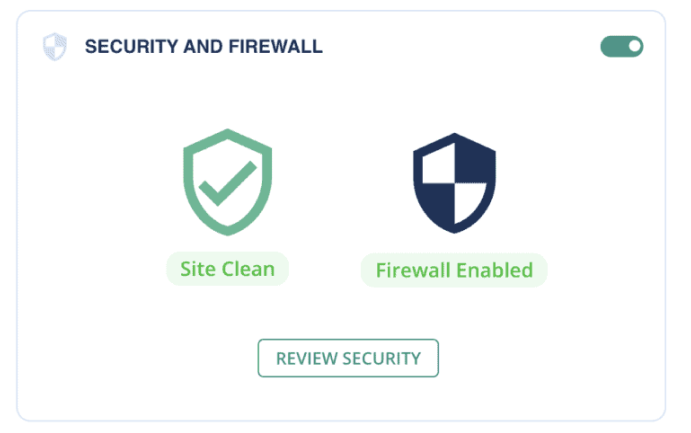
- Use SSL: It is imperative to use Secure Sockets Layer (SSL) to strongly protect sensitive information, including cookies, from interception or theft. By encrypting the data sent between the user’s browser and the server, attackers will find it extremely difficult to steal such data. Therefore, it is crucial to ensure that your site uses HTTPS to secure your users’ sessions.
- Use two-factor authentication: Incorporate Two-factor authentication (2FA) as an additional security measure for user accounts. This method requires users to provide a second form of identification along with their username and password, thereby enhancing the overall security of the account.
- Implement strong password policies: Encourage users to create strong, unique passwords and implement password policies that require passwords to be changed regularly and meet certain complexity requirements.
- Update WordPress, themes, and plugins frequently: Keep your website software up-to-date to minimize the risk of vulnerabilities being exploited by attackers.
- Educate admin users: Make sure all users with administrative privileges understand the risks of session hijacking and the steps they can take to prevent it.
Note: Using outdated versions of browsers can create vulnerabilities that could be exploited to steal cookies. Therefore, it’s important to keep your browser up to date with the latest version to minimize the risk of cookie stealing attacks. But, this attack vector has been eradicated for the most part.
What makes cookie stealing dangerous?
Cookie stealing is a pervasive and common cyber attack. On the surface, it may seem to only affect individuals, but that is not the case. There are dangers lurking further downstream as well.
- Gives unauthorized access: By stealing a user’s cookies, a cybercriminal can gain access to the user’s online accounts without permission. This unauthorized access can be used for nefarious activities, such as stealing personal information, financial data, or intellectual property.
- Sensitive data is made vulnerable: Cookies often contain sensitive information such as login credentials, personal information, browsing history, and more. If these cookies are stolen, this data becomes vulnerable to being accessed and used by cybercriminals.
- Difficult to detect: Identifying when your cookies have been stolen can be challenging. Cybercriminals can steal cookies without leaving a trace, making it difficult for users to detect any unauthorized activity on their accounts until it’s too late.
- Access to make unauthorized transactions: Once a cybercriminal gains access to a user’s online accounts through cookie stealing, they can perform a range of unauthorized activities. This could include making purchases using the user’s credit card, posting inappropriate content, or tampering with important data.
Wrapping up
Cookie stealing poses a serious threat to online privacy and security. As a WordPress site admin, you can protect your site and users by using a security plugin like MalCare. MalCare has an advanced firewall specifically designed for WordPress sites. Taking these steps can help protect your sensitive information and keep your users safe online.
FAQs
What is an example of cookie hijacking?
A common example of cookie hijacking is when a cybercriminal steals a user’s cookie containing their login credentials and uses them to gain unauthorized access to the user’s account.
Can session cookies be stolen?
Yes, session cookies can be stolen. In fact, they are often targeted by cybercriminals because they contain sensitive information that can give them access to the user’s account.
Can a hacker steal cookies?
Yes, a hacker can steal cookies through various methods, such as through XSS attacks, network sniffing, and social engineering tactics.
What is cookie hijacking attack?
Cookie hijacking attack is a type of cyber attack where a hacker steals a user’s cookie to gain unauthorized access to their online accounts.
What is an example of a cookie attack?
An example of a cookie attack is when a hacker uses a technique such as packet sniffing to intercept a user’s cookies as they travel over an unencrypted network, giving them access to sensitive information or unauthorized access to the user’s accounts.
Share it:
You may also like
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…

MalCare Proactively Defends Against Icegram Express SQL Injection Vulnerability
MalCare’s recent data has revealed numerous attempts to exploit a newly found SQL injection vulnerability in the Icegram Express plugin. Attackers commonly use this sophisticated SQL injection technique to extract…

Atomic Security’s Deep WordPress Integration Helps Protect Against Core XSS Vulnerability
The recent WordPress core vulnerability is a critical one, primarily because of two reasons. Firstly, it affects the WordPress core itself, which means that every WordPress site is vulnerable to…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








