How To Completely Remove Defacement From WordPress Site?
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

WordPress defacement is an attack on sites, in which hackers tamper with legitimate content. Defaced sites are always jarring, and never more so than when the site is your own.
If hackers deface WordPress site, it is most likely a result of malware. Scan your site to get a definitive analysis so you can recover your site as soon as possible.
In this article, we will provide you with practical solutions that not only help you recover from the damage to your site but also equip you with the knowledge to prevent future breaches. From identifying the source of the breach to implementing security measures that act as a shield against potential threats, we’ve got you covered.
TL;DR: Scan your defaced WordPress site with MalCare. It will not only identify and remove malware but also fix backdoor vulnerabilities that hackers exploit for defacement attacks. MalCare is the most effective way to protect your website from any kind of threat.
Discovering that your WordPress site has been defaced can be a frustrating experience, especially if it’s not the first time your website has been hacked. Frequent hacking incidents are often a red flag, suggesting the presence of hidden backdoors that keep inviting unwanted intrusions. It’s natural to feel disheartened, but it’s fixable.
In this article, we will show you how to identify malware, remove them all (including backdoors), and put security measures in place to prevent future attacks. By following the steps outlined here and utilizing this proactive approach, you’ll be better equipped to regain control of your online presence and secure your website against future threats.
.
Step 1: Scan your website for malware
The first crucial step in dealing with a defaced WordPress site is to scan it thoroughly for malware. Malware is the most common cause of WordPress defacement attacks, and should be definitively identified as soon as possible. In this section, we’ll explore three distinct methods to conduct these scans: utilizing a comprehensive security plugin, leveraging online scanning tools, and manually inspecting your website.
- Using a security plugin: MalCare’s comprehensive scanning capabilities quickly pinpoint malware, both in the site files and its database. All you have to do is run your site URL through the free malware scanner and a report will be generated. Once you have this report, MalCare also scans for backdoor vulnerabilities that hackers could potentially exploit to perpetrate the attack in the future.
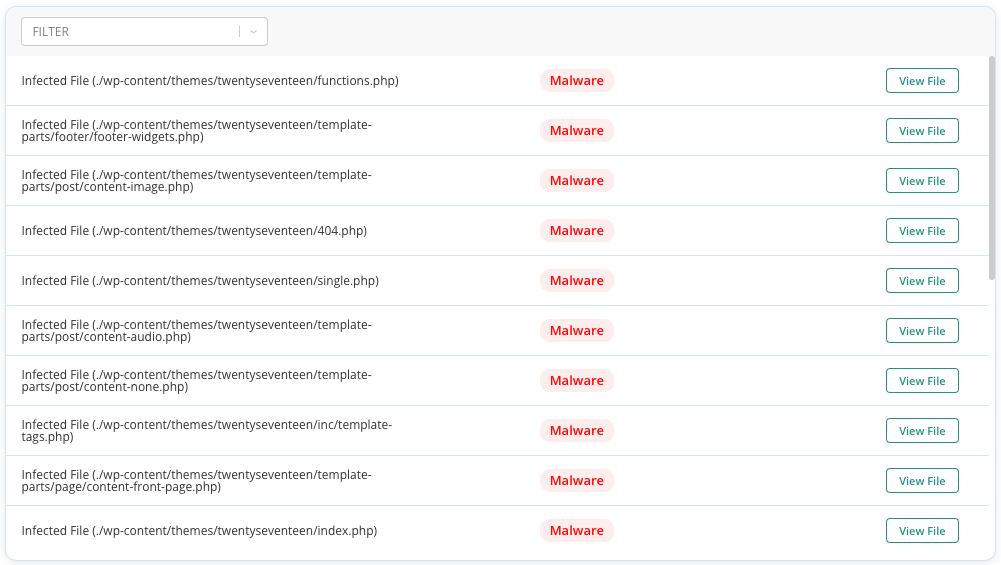
Why we recommend MalCare
- Comprehensive detection: MalCare has a specialized scanning algorithm, which thoroughly analyzes your site’s files, ensuring that even hidden malware and backdoors are identified.
- Automated process: The plugin automates the scanning process, saving you considerable time and effort. Regular automated scans also help you catch potential threats early.
- Backdoor identification: MalCare also actively detects backdoors that hackers could exploit to gain unauthorized access, if not removed.
- Using online scanners: Numerous online scanning services are available, like Sucuri Sitecheck, which offer quick and easy ways to detect malware on your site without installation. These tools scan your website remotely, analyze the publicly visible parts of your files, and provide a report on potentially malicious elements.
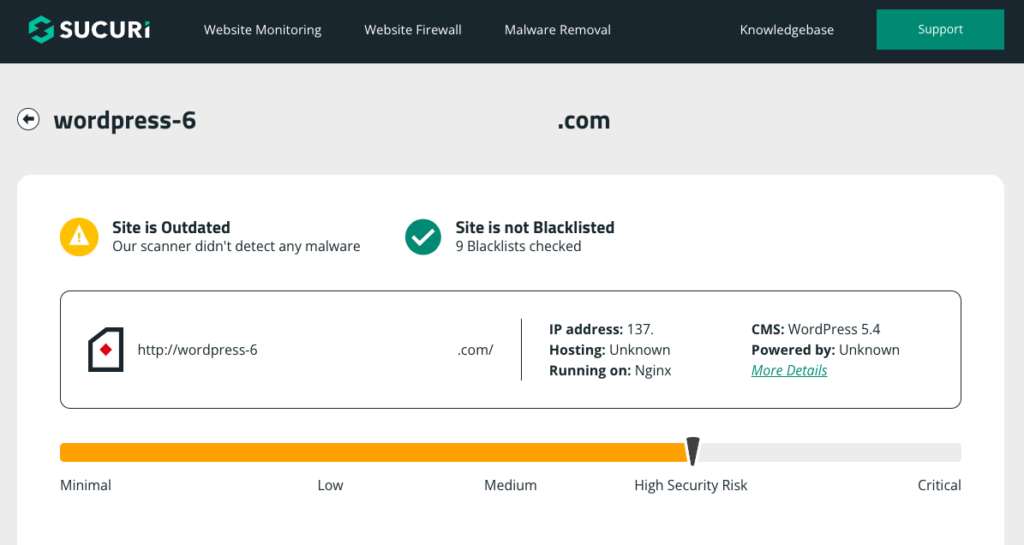
While online scanners are good first-level diagnostics, they cannot be relied on completely. Firstly, online scanners cannot delve as deep as dedicated security plugins because they do not have access to the private and restricted areas of your site. Obviously, malware has no such constraints, therefore use an online scanner with the knowledge that you may be potentially missing some hidden or complex malware.
- Manually scan for malware: If you are someone who prefers a hands-on approach to WordPress security, you can conduct a manual scan. This involves combing through your website’s files and database to identify any anomalies. While this method provides a deep level of control, it requires a high level of technical expertise and is very time-consuming.
There is a major drawback to manually scanning your site for malware: you need a considerable amount of coding experience to identify good vs. bad code. Even then, there is the danger of oversight; or equally a false positive. In the case of oversight, missing even the smallest bit of malware can rapidly lead to reinfection. False positives could lead to deleting a valid bit of code, and crashing your site. Either way, take a backup of your site before attempting manual scanning.
Step 2: Take your website offline
Once you have ascertained the presence of malware on your WordPress site, the next step is to take it offline and put it into maintenance mode. This not only safeguards your users’ experience, but helps limit the damage until you can set the defacement to rights.
- Create a maintenance page:
Use a plugin like WP Maintenance Mode or Coming Soon Page & Maintenance Mode by SeedProd to quickly set up an interstitial page. These plugins often offer customizable templates and themes, and user-friendly interfaces. You can also create it using a theme or a page builder like Elementor.
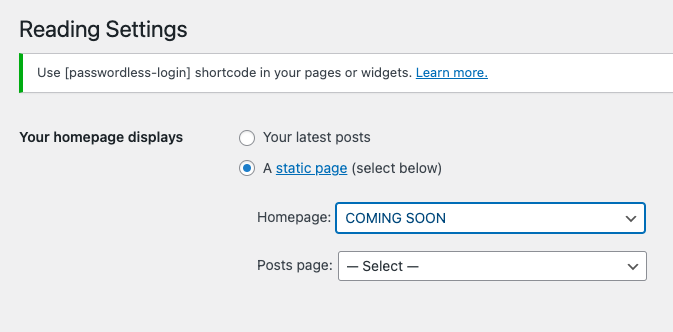
- Set your maintenance page as your static home page: On your WordPress admin panel, navigate to the Settings menu in the sidebar. From the dropdown, select Reading. Within the Reading Settings page, you’ll find a section titled Your Homepage Displays. Choose the option for a static homepage. This prevents your site from displaying dynamic content while you’re working on the recovery process.
In the dropdown menu under Homepage, you should see a list of available pages. Select the maintenance page you created earlier. Save changes when you’re done. With the changes saved, you can now preview your site. You should see the maintenance page you’ve set up, indicating that your site is undergoing maintenance and improvements.
By following these steps, you effectively put your WordPress site into maintenance mode. This not only shields your visitors from encountering an incomplete or compromised site but also demonstrates your dedication to rectifying the situation. With your site protected, you can proceed confidently to the next phase of restoring your defaced website to its former glory.
Step 3: Remove malware from your WordPress site
The next step is to remove the malware you’ve identified on your defaced WordPress site. There are a few different methods to do so, but you’re looking for tools that can distinguish between malware and legitimate code, remove the malware, and do it all without affecting your website.
- Remove malware with a security plugin: The best way to remove malware from your WordPress site is to use MalCare. It is a potent WordPress security plugin equipped with a one-click auto removal feature. MalCare surgically removes malware from your site, leaving the legitimate code untouched.
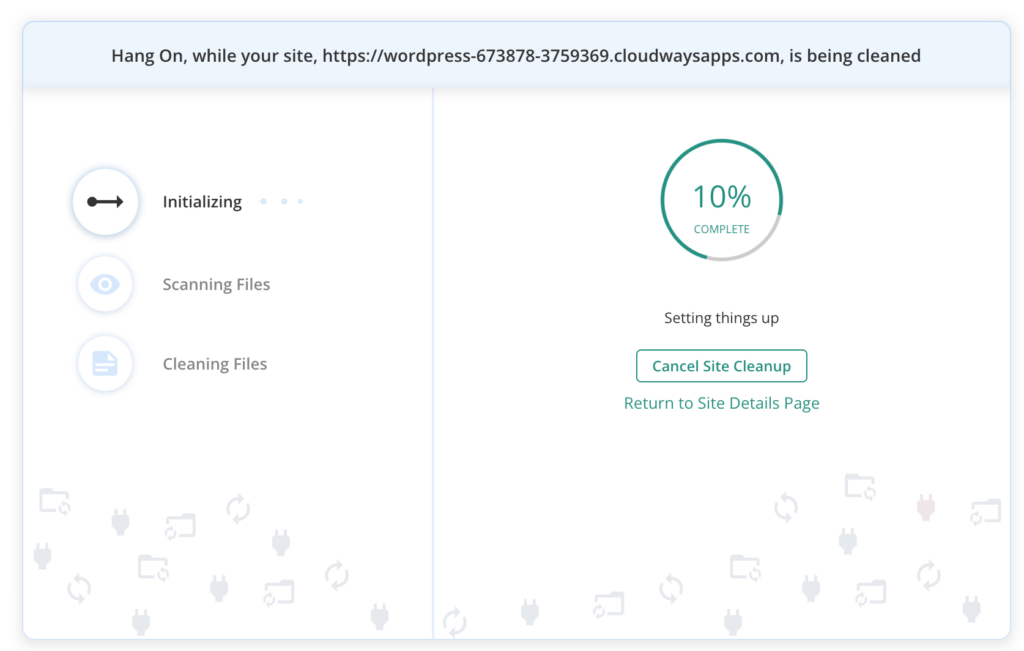
Why we recommend MalCare
- Automated cleanup: MalCare’s one-click auto removal feature streamlines the malware elimination process. With just a single click, the tool identifies and eradicates malicious code, ensuring a quick restoration of your website’s integrity.
- Comprehensive detection: MalCare employs advanced algorithms to detect a wide spectrum of malware types, even those lurking in the depths of your website’s files and code.
- Backdoor fixing: Backdoors are malware that lets hackers back into your site, bypassing logins. One of MalCare’s standout features is its ability to identify and remove backdoors. This preemptive action shields your website against future attacks.
- Time-efficient: The automated removal process minimizes downtime, allowing you to swiftly resume normal operations without protracted disruptions.
- Hire a security expert: When facing a defaced WordPress site, the complexity of malware removal might necessitate the involvement of a seasoned security expert. This is especially the case if your wp-admin is unreachable, and you cannot install a security plugin.
There are many WordPress maintenance services that include help from security professionals. MalCare has an emergency response service as well. All you need to do is contact support. Our team comprises security professionals who possess the knowledge and experience to navigate the intricate landscape of cybersecurity threats and can efficiently restore your site’s integrity.
- Manually remove malware: For those who seek a deeper understanding of their website’s intricacies and are comfortable with technical aspects, manual malware removal provides a hands-on approach to sanitizing your site.
Manual malware removal involves a meticulous examination of a website’s files, and databases to locate and remove malware This hands-on approach allows website owners or administrators to have direct control over the removal process and gain a deeper understanding of their website’s security vulnerabilities.
Here are the steps to manually remove the malware:
Step 1: Backup Your Website
Begin by creating a complete backup of your WordPress site using BlogVault. Backup your files and database so you can ensure that you can restore your site if something goes wrong during the cleanup process.
Step 2: Download Clean Versions of your site files:
Download clean versions of WordPress core, themes, and plugins. Make sure to match the versions on your website to compare and locate malware.
Step 3: Reinstall WordPress core:
Using cPanel or SFTP, replace the ‘wp-admin’ and ‘wp-includes’ folders with clean versions. Be sure to use the same version as before. Look for malware in key files such as ‘index.php,’ ‘wp-config.php,’ ‘wp-settings.php,’ ‘wp-load.php,’ and ‘.htaccess.’ Also check the ‘wp-uploads’ folder for PHP files. When you find malicious code or any php files in the “wp-uploads” folder, delete them.
Step 4: Clean Themes and Plugins Files Inspect themes and plugins:
in the ‘wp-content’ folder for malware. Compare each file to clean downloads. Be cautious not to remove legitimate customizations. Avoid using nulled themes or plugins as they often contain malware.
Step 5: Clean Malware from WordPress Database Tables:
Access your database admin panel and review tables, particularly ‘wp_options’ and ‘wp_posts,’ for suspicious content. Checkout a moredetailed guide to manually cleaning your database. Delete any suspicious entries. Test your site to ensure it functions correctly.
Step 6: Remove All Backdoors:
Backdoors are what allow a hacker to access your site without needing to breach your login. To prevent future infections, eliminate backdoors in your website’s code. Search for common backdoor keywords like ‘eval,’ ‘preg_replace,’ ‘str_replace,’ ‘base64_decode,’ ‘gzinflate,’ and remove them if found. Note: If you’re unsure, use the MalCare security plugin or expert.
Step 7: Reupload Cleaned Files:
Upload the cleaned files to your website, similar to restoring a backup manually. Delete the files and tables you plan to replace and then upload the clean versions. Keep your backup ready in case of issues.
Step 8: Clear the Cache:
Clear your WordPress cache to remove any cached versions of your site that may contain malware.
Step 9: Verify Each Plugin and Theme:
Disable all themes and plugins by renaming the ‘wp-content’ folder temporarily. Then, activate them one by one, checking for any issues or abnormal behavior. Ensure your extensions are malware-free.
Step 10: Use a Security Scanner to Confirm:
Use a reputable security scanner to perform a thorough scan of your website to confirm that it’s completely malware-free. If malware is still detected, consider using a security plugin for further cleanup.
Why we strongly discourage manual malware removal
- Technical expertise required: Manual removal demands a solid understanding of coding languages, file structures, and website functionality. Without proper knowledge, the process can be daunting and might lead to unintended damage.
- Time-consuming: The manual process can be time-intensive, especially if your website has numerous files and complex code. The thorough inspection required for manual removal might extend the duration of the recovery process.
- Risk of backdoors: While cleaning visible malware is essential, the challenge lies in identifying potential backdoors that hackers can exploit in the future. A meticulous examination of your site’s code is necessary to eliminate these hidden vulnerabilities.
Step 4: Post-hack checklist
Dealing with defacement on your WordPress site can be an unsettling experience, but with a systematic approach, you can swiftly regain control and restore your online presence. Here’s a comprehensive post-hack checklist to guide you through the process of recovery and fortification:
- Change passwords: One of your first actions should be changing all passwords associated with your website. Update passwords for hosting accounts, FTP accounts, and any user or admin accounts. Opt for strong, unique passwords that are challenging to guess, and consider employing a password manager for enhanced security.
- Restore site content: WordPress defacement often results in content damage or loss.So, take your time and restore the content using a backup.
- Check for unauthorized users: Hackers might create unauthorized accounts to facilitate future attacks. Thoroughly review your user list and delete any suspicious accounts. If you are unsure of any account, review login history to pinpoint unauthorized access attempts and remove corresponding accounts.
- Check for vulnerabilities: Employ MalCare’s vulnerability scanning capabilities to identify potential security weak points within plugins and themes. Update vulnerable components promptly. Prioritize security by keeping your software stack up-to-date.
- Notify users and customers: Open communication is essential. Notify your users and customers of the incident via email or social media. Explain the breach, the steps you’ve taken to rectify it, and provide them with any necessary guidance to safeguard their information.
How to Prevent WordPress defacement in future
By incorporating a range of security practices and utilizing specialized tools, you can significantly reduce the risk of defacement and maintain the integrity of your online presence. Here’s a comprehensive guide to preventing WordPress defacement:
- Install a firewall: A web application firewall (WAF) acts as a barrier between your website and potential threats. It filters incoming traffic, identifying and thwarting malicious attempts to breach your site’s security.
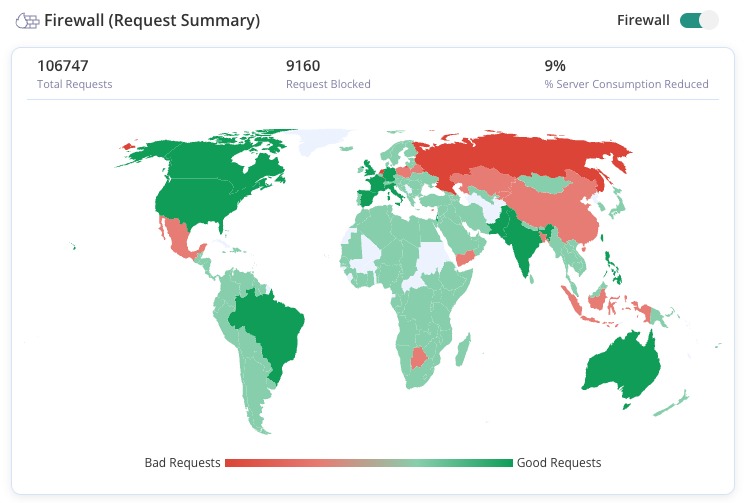
- Use automatic malware scanning plugins: Deploying a plugin that automatically and regularly scans for malware helps catch threats before they escalate. Plugins like MalCare provide ongoing monitoring and quick response to potential attacks.
- Take regular backups: Frequent backups ensure you have a clean version of your site to restore in case of defacement. These backups should be stored securely, off-site, and should be easily accessible when needed.
- Implement 2FA (Two-Factor Authentication): Enhance user authentication by implementing 2FA. This adds an extra layer of security by requiring users to provide two different types of verification before gaining access.
- Keep everything up to date: Regularly update your WordPress core, themes, and plugins. Outdated software can become vulnerable to attacks.
- Use strong passwords: Enforce the use of strong passwords for all user accounts. A combination of letters, numbers, and special characters significantly enhances password security.
- WordPress defacement detection/monitoring: Utilize change detection tools like Fluxguard and Visualping to monitor any unauthorized modifications to your site. These tools alert you to unexpected changes, helping you identify potential defacement early.
- Limit access: Restrict access to sensitive areas of your site. Grant privileges only to those who require them, reducing the potential attack surface.
- Use SSL (Secure Sockets Layer): Implementing an SSL certificate encrypts data transmitted between your site and users, ensuring secure connections and bolstering user trust.
- Employ reCaptcha: By integrating reCaptcha, you add an extra layer of security to your forms, thwarting automated bot-driven attacks.
- Maintain an activity log: An activity log keeps a record of what happens on your website, like who makes changes. It helps prevent defacement by letting you see if someone is messing with your site without permission. This way, you can stop them before it gets worse.
How do attackers deface WordPress websites?
Hackers identify potential target websites through various means, such as automated scans, searching for vulnerable sites, or even manually selecting high-profile targets. Then they analyze the target website to find potential vulnerabilities, which could include outdated software, unpatched plugins or themes, weak passwords, or other security flaws.
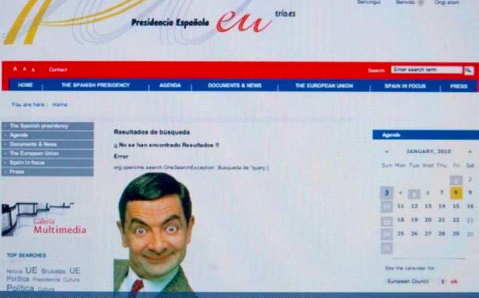
Once a vulnerability is identified, hackers leverage it to gain unauthorized access to the website using common techniques include SQL injection, cross-site scripting (XSS), and remote code execution. This gives them access to the website’s backend or server, often obtaining administrative privileges. Next, they upload files or change existing files on the website, and are able to alter the website’s appearance, content, or functionality to match their intentions. The following is an image of European Union website that has been defaced. In 2010, the Spanish President’s face was replaced by the popular comedic character Mr. Bean.
Hackers may also create hidden backdoors or additional vulnerabilities to maintain control over the compromised site, allowing them to return later or retain unauthorized access.
Why do hackers deface WordPress sites?
Hackers are driven by various reasons that lead them to deface WordPress sites. Some are basically just craving attention; they deface sites hoping to become the next big thing on the digital block. It’s like virtual graffiti, an online version of spray-painting walls.
Then there are those who see WordPress defacement as a way to showcase their beliefs. They hack a site and plaster it with their message, whether it’s political, social, or just something they want to make a big fuss about. It’s like hijacking a megaphone to broadcast their thoughts.
Some hackers do it to flex their tech muscles. They see a vulnerable site as a challenge, a way to prove they’ve got serious skills. It’s like showing off at a gaming tournament, but with code instead of controllers.
All in all, they do it because they can.
What are the consequences of WordPress defacement?
The aftermath of a WordPress defacement extends far beyond the surface-level visual disturbance. While the immediate impact might appear as altered aesthetics and misplaced content, the consequences run deeper, affecting various aspects of the website, its users, and the site owner. Let’s talk about these consequences in this section:
- Damaged reputation: Defaced websites can lose credibility and trust among visitors, customers, and stakeholders. Visitors may associate the website with incompetence or lack of security measures.
- User trust erosion: Users may lose confidence in the website’s security, leading to decreased user engagement and interaction.
- Business losses: E-commerce sites can experience financial losses due to disrupted sales, reduced customer footprint, and loss of customer trust.
- Search engine ranking drop: Search engines can detect unauthorized changes and penalize the site’s search ranking, leading to reduced visibility and hence, traffic.
- Data breach risk: Defacement may indicate a larger breach where attackers gain access to sensitive user data, putting visitors’ information at risk.
- Disrupted functionality: The altered website might not function properly, leading to poor user experiences and frustrated visitors.
- Legal consequences: If defacement involves illegal content or copyright violations, website owners may face legal issues.
- Costly recovery: Repairing the damage, identifying vulnerabilities, and restoring the website can be time-consuming and expensive.
- Downtime and lost traffic: Website downtime during recovery can lead to lost traffic, revenue, and customer interactions.
- Cleanup effort and resources: Website owners must invest time and effort in identifying the breach, cleaning up the site, and implementing stronger security measures.
Final thoughts
WordPress defacement is digital vandalism serves as a glaring indicator that the website’s defenses are lacking. Owners face the dual challenge of eradicating the unwelcome changes—often caused by malware—and fortifying their website’s security to prevent future breaches. In essence, WordPress defacement is more than just an aesthetic disruption; it’s a clear call to action, urging site owners to swiftly restore their digital canvas and bolster their virtual defenses against potential attacks.
It can also announce to everybody that your security is not up to par. Hence, it’s important to not let your guard down when it comes to your site’s security. Here, it is good to remind yourselves that there is no one size fits all solution for security, MalCare offers a fantastic malware scanner, cleaner, and firewall that can protect your WordPress site from defacement attacks.
FAQs
I saw a “Hacked by…” message on my landing page. What to do?
To address a hacked website, promptly take it offline, conduct a malware scan with MalCare to identify threats, thoroughly remove malware, and bolster security by installing a firewall. These actions are crucial for restoring your website’s integrity and safeguarding it against future attacks.You will then need to restore your site and put protective measures into place like changing your passwords.
I am constantly being hacked. What to do?
Use MalCare to remove the malware and install a firewall. MalCare can help remove the backdoor or the pieces of code that allow a hacker to hack you over and over again. A backdoor gives them access to your site without breaching your login. It’s used by hackers who have already gained access to your site to be able to easily replicate the damage. MalCare has a phenomenal malware remover and a top-notch firewall, making it the ideal plugin for your site.
What is WordPress defacement?
WordPress defacement is a form of cyber attack known as “vandalism” or “digital graffiti. It is when unauthorized individuals or hackers make unauthorized changes to your WordPress website’s appearance. They may alter the visual elements, replace content with offensive or unrelated material, or insert malicious links. This act can damage your website’s credibility, brand image, and user trust. Defacement often indicates a security breach, and addressing it promptly is crucial to restore your site’s integrity and protect it from further harm.
What is the impact of the defacement of WordPress sites?
The impact of WordPress defacement goes beyond the initial alteration of appearance and content. It can erode user trust, damage a brand’s reputation, disrupt the user experience, jeopardize sensitive user data, impact search engine rankings, result in loss of revenue, and lead to resource-intensive recovery efforts. Additionally, defacement can expose sites to legal and regulatory consequences and leave them vulnerable to further security breaches. Ultimately, the impact extends to various aspects of a site’s functionality, credibility, and overall online presence.
Share it:
You may also like
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…

MalCare Proactively Defends Against Icegram Express SQL Injection Vulnerability
MalCare’s recent data has revealed numerous attempts to exploit a newly found SQL injection vulnerability in the Icegram Express plugin. Attackers commonly use this sophisticated SQL injection technique to extract…

Atomic Security’s Deep WordPress Integration Helps Protect Against Core XSS Vulnerability
The recent WordPress core vulnerability is a critical one, primarily because of two reasons. Firstly, it affects the WordPress core itself, which means that every WordPress site is vulnerable to…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








