What Happens When Developers Don’t Update Plugin?
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

Developers Don’t Update Plugin: WordPress site owners are always cautioned to keep WordPress Core and add-ons (themes and plugins) updated. When kept unattended, addons develop vulnerability that hacker exploit to break into a site. But what if a vulnerability was discovered some time ago and the developer of the plugin hasn’t released an update to address the issue yet? What do website owners like yourself do then? The goal of this post is to discuss a course of action that’ll keep the site safe until the developers release an update.
Back in 2016, a security blog reported cross-site scripting vulnerability found in W3 Total Cache, a popular caching plugin. W3 Total Cache was one of the most popular caching plugins with over 1 million active installs and was trusted by websites like pearsonified.com and mashable.com and even company website of AT&T. This wasn’t the first time W3 Total Cache plugin had developed a vulnerability. In fact, in the past Total Cache had had a good share of vulnerabilities and some of them were even exploited.
At the time of the report, there were complaints floating around on support related issues where users have been trying to communicate with the developers for months on end but without much success. One disgruntled user posted on a Facebook group saying the plugin had not been updated for over 7 months. At this point, concerns over potential damage that a cross-site scripting vulnerability could have on websites using W3 Total Cache is understandable.
Almost after a week since the vulnerability was disclosed, W3 Total Cache released an update and patched exploitable loopholes. Furthermore, they introduced new features to the product. But right after the release of the patch, many website owners reported that the update broke their site. It is not uncommon for new updates to break websites, which is why using a staging environment is recommended. It gives you an opportunity to test updates on a staging site before making changes to the live site. If the staging site breaks when making the update, you can raise the issue with the plugin developers without damaging your live site. And while it took some time for the developers of W3 Total Cache to release a patch but things didn’t lead to a total catastrophe.
What to Do When Developers Don’t Update Plugin?
WordPress is the world’s most popular website building platform, and one of the biggest reasons behind its popularity is the use of plugins which enables users to design their site and add functionality to it easily. Many WordPress plugins are made by developers as a side project. When a vulnerability crops up, it takes a lot of time and effort to not just identify the problem but also to develop a patch. Sometimes, they can’t immediately tend to the plugin vulnerability because they have a regular job to attend to. A side-project is not a priority. This leads to a delay in releasing a patch.
WordPress is an internet community spanning across the globe and news about any vulnerability found either in the core or any of its add-ons (i.e. themes and plugins) spread fast. Which means hackers who are always on the lookout for vulnerable websites would launch massives hack attempts on websites within hours. Thus when a plugin vulnerability is found, but the developers haven’t released an update yet, it’s important to take some course of action to keep to site from harm’s way. Here’s what to do when you find yourself in a situation like this:
- Disable the plugin until an update has been released by the developers to fix the vulnerability.
- If it’s not a premium plugin or premium version of a plugin, then go to the support forum on wordpress.org and leave a complaint there. Hopefully, enough complaints will push the developers to release a patch quickly.
- Usually, an update takes over 48 hours to comes through following the discovery of a vulnerability. But if it takes longer, get in touch with the developers and inform them about the issue. Quote your source, that is, from where did you hear about the vulnerability. In the plugin’s official website there must be a ‘contact us’ page or an email address somewhere on the site. Shoot them a mail.
- In the meantime, use an alternative plugin that’ll help you keep your site fully functional. It’s always recommended that you have a plan in place when a plugin stops working.
As we mentioned before, there are a lot of plugins in the WordPress plugin repository that are developed as a hobby or side project. This means a developer who is working to create a free product may abandon the product anytime. And that’s why many security experts only recommend using premium plugin created by developers who are well-known and respected in the community. Developers who are not getting paid for a plugin or theme they are building are likely to dedicate less time to enhancing or maintaining the plugin/theme. They may have a full-time job that keeps them busy and pays their bills which makes investing time in a product that brings no monetary benefit impractical.
Vulnerabilities will develop in WordPress plugins whether they are made by an expert or an amateur. If you keep using the abandoned theme/plugin, there will be no maintenance, therefore no updates. When an error occurs, you’d want to reach out to the plugin developers, but since the plugin has been abandoned by its team of developers, you won’t get any support either. That leaves you, the user, in a tight spot because switching to an alternative plugin or theme requires investing time and effort all over again but that’s the only viable option. Good website security practices urge the user to follow a few protocols on how to choose a plugin. We have listed them down here:
- Select a plugin that is developed by a renown developer to avoid a situation where you are using a plugin that has been abandoned by the creator.
- Make sure that the plugin is being regularly updated which would mean that the developers are fixing vulnerabilities that could have been used by hackers to break into your site. Go to the WordPress repository to see when was the last update made.
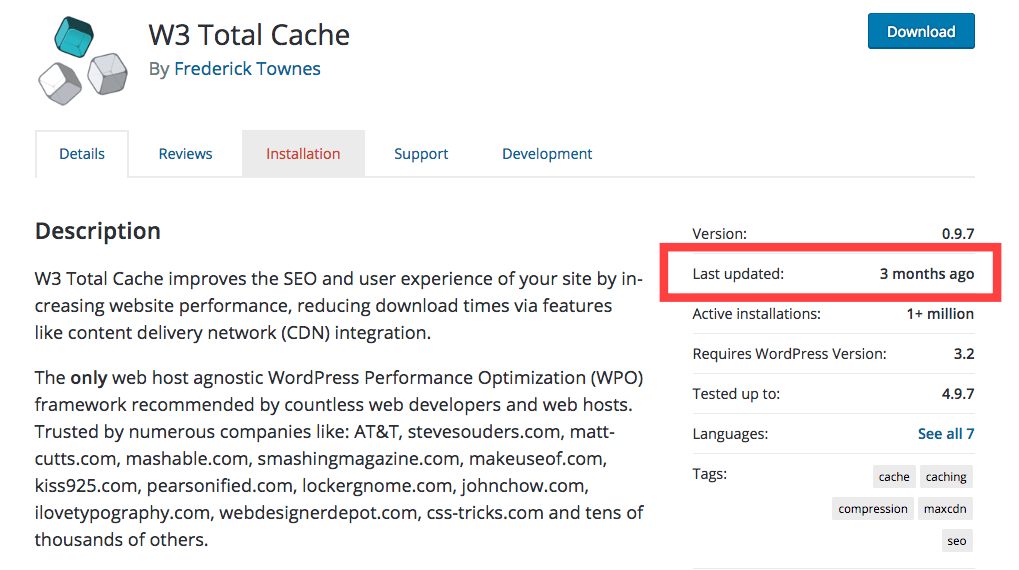
- Use a premium plugin instead of a free one. If there’s a free version of a plugin, then use it to test basic functionality, but we suggest that you upgrade to the premium version. Like we discussed earlier, free plugins can be abandoned, or important updates could take too much time to roll out.
We hope that this post helps to take a course of action when a developer isn’t updating his plugin. Thank you for reading and if you have any question, kindly write to us.
Category:
Share it:
You may also like

MalCare Ensures Unmatched Protection Against User Registration Privilege Escalation Vulnerability
Imagine discovering that your WordPress site, which should be secure and under strict control, has suddenly become accessible to unauthorized users who have the same administrative powers as you. This…

MalCare Ensures Proactive Protection Against WP-Members XSS Vulnerability
MalCare continues to protect its customer sites from all kinds of attacks, even the ones exploiting zero-day vulnerabilities. The recent stored cross-site scripting (XSS) vulnerability found in the WP-Members Membership…
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








