GoDaddy Data Breach 2021: What Happened and How It Affects You
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

GoDaddy, one of the biggest web hosts, discovered a data breach on November 17th, 2021. The WordPress community has been discussing the Godaddy data breach implications because the primary target of the security breach was GoDaddy’s Managed WordPress customers.
The trouble with this sort of news is that there is always a lot of noise as everyone jumps on the bandwagon. In the course of 10 years, we at MalCare have seen that people have a misguided sense of what constitutes WordPress security. Often the advice is not useful, and in some cases it can be actively harmful for websites.
GoDaddy customers are obviously panicking and looking for clear and straight answers to their concerns. In this article, we break down what happened as simply as possible, and tell you what your next steps should be.
Godaddy Data Breach: What happened, and why everyone is freaking out
GoDaddy had a serious data breach which they discovered on November 17th, and released a statement about on November 22nd. This is a quick summary of what went down:
- As per their investigation, the data had been compromised for over 2.5 months, before they realised it was happening.
- The SFTP and database credentials of 1.2 million of their Managed WordPress customers were compromised.
- Some WordPress admin passwords were exposed. These are the admin passwords that were set automatically by the system when the website was first created.
- SSL private keys were also compromised for certain users. An SSL private key is the most critical part of an SSL certificate, and it is the backbone of what makes it secure. Compromised private keys make the SSL certificate insecure and worthless.
- It was later discovered that resellers were also affected by the Godaddy data breach.
GoDaddy has tried to mitigate the damage, and has probably reached out to their affected customers directly. However, at a time like this, assurances from GoDaddy will not be well-received. Also, they are going to try their best to do damage control and retain customers, who will understandably want reparation or to leave GoDaddy entirely.
How does the Godaddy data breach affect you, and what you should do about it
If you are a Managed WordPress customer, have an SSL certificate issued by GoDaddy, or have purchased hosting through a GoDaddy reseller, you are one of the most affected by the GoDaddy data breach.
If you are a Managed WordPress customer, what should you do?
GoDaddy’s Managed WordPress customers are evidently the worst hit by the data breach. As disclosed in GoDaddy’s SEC filing, the hackers had access to SFTP as well as database credentials to every site hosted on the platform.
While a lot of people are miffed about the SFTP credentials being stored in clear text, which is extremely dangerous for sure, we feel that the compromised database credentials are the biggest cause of concern.
With the database credentials, it is possible to gain complete access to any WordPress site. This is one of the reasons why SQL injection attacks are so dangerous.
Hackers could have copied, modified and added to the files and database at any time. Therefore, the safest way to proceed is to assume the worst—that hackers currently have access to your site, and that your website potentially has malware.
How to recover your website
All is not lost, and if your website is still functioning, this situation can be resolved. Here are the steps you should take to recover your website from hackers.
1. Scan your website for malware
Your first priority is to deep scan your website because malware can be absolutely anywhere: core WordPress files, plugin and theme folders, and the database. Through the compromised credentials, hackers have had access to your website files and database for a prolonged period of time. Therefore, a frontend-level scanner is not going to cut it.
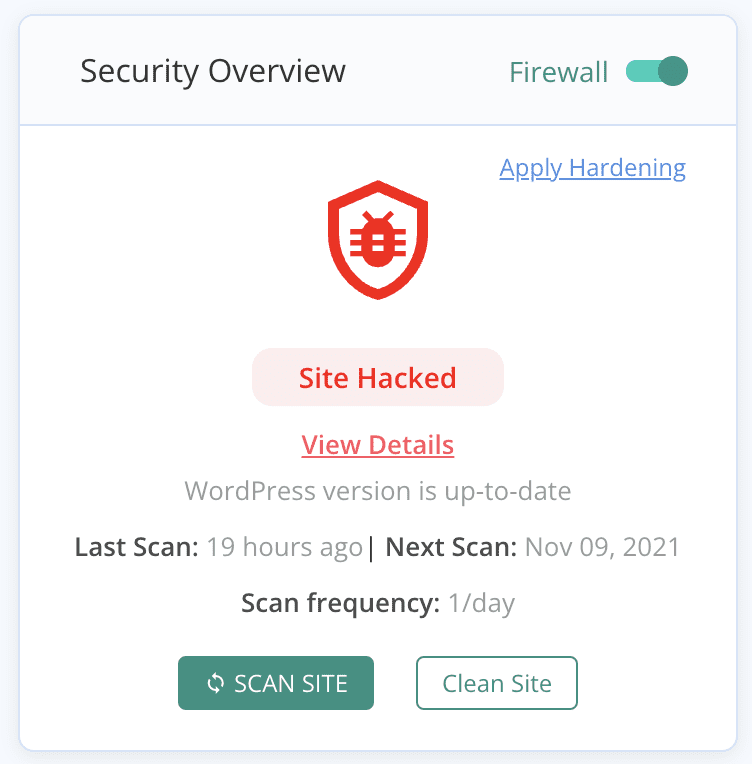
2. Remove the malware
If your website has been hacked, clean the malware without delay. You may have already seen the symptoms by now, and perhaps not realised that they are caused by malware. If Google hasn’t blacklisted your site, you’ve dodged a bullet and only have to focus on cleaning the malware immediately. Use MalCare to do this quickly and efficiently, so that your website is back on track as soon as possible.
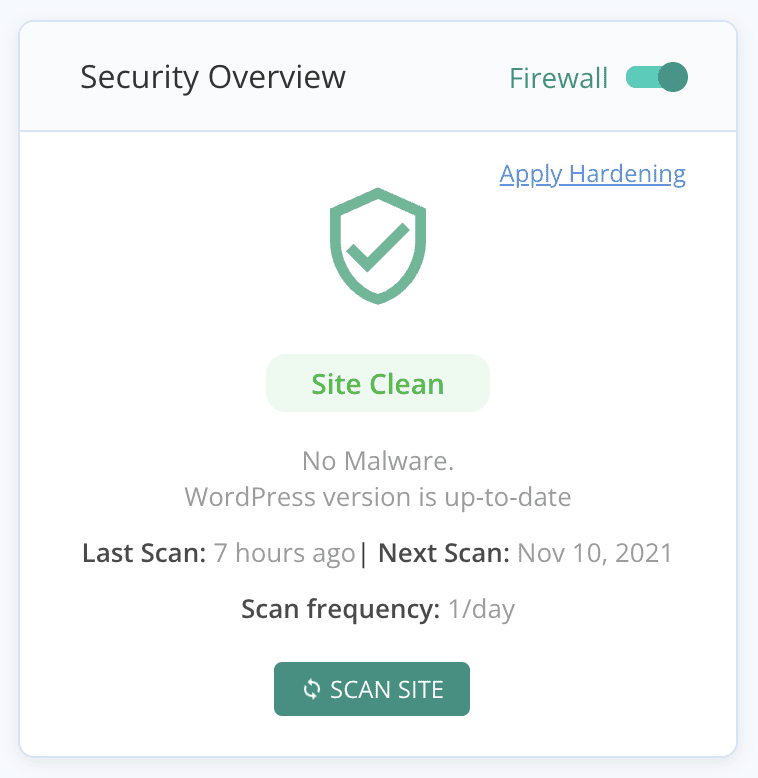
We don’t recommend trying to remove malware manually. Hackers often add cleverly hidden backdoors to website code, so that even if the malware is detected and removed, they can regain access via backdoors. The best way to get rid of malware is to use the best security for WordPress.
3. Change all your passwords
Whether you find malware or not, you need to change all the passwords: admin accounts, database passwords, SFTP credentials, the works. GoDaddy has already reset your SFTP and database credentials, but it is better to do so again, in case your website has malware.
This is a precaution for two reasons: one, if your website has been hacked, then it is part of the checklist; two, if you set your own SFTP password, then chances are that you reused the password elsewhere and those accounts are compromised as well. This is only step one in the post-hack security checklist, but it is a good start. It will stop the damage from getting worse.
4. Get another SSL certificate
In case your SSL certificate was compromised, GoDaddy would have reached out to you directly. In this case, it is better for you to get another SSL altogether from a different certificate authority. Although GoDaddy is resetting the certificates, to fast-track the process, it is better to deal with this on your own.
Ecommerce stores and membership sites
If your site is an ecommerce store or a membership site, there is an added layer of complexity for you. In these cases, you are storing your visitor data, like emails and login passwords at the least. Maybe you are storing other information too, like personally identifiable data. The only silver lining here is that you are most likely not storing any credit card details
5. Communicate with your website users
In this case, you need to ask your website users to reset their passwords as well. In fact, you should go ahead and do that anyway, and inform them accordingly. This is a responsible declaration, because you should assume that your website’s user data has been compromised, as well, because of the hacker’s access to your website database. In some cases, you may be legally required to do so.
Also warn your users to be on the lookout for phishing scams. These scams will try to extract more information from your users by impersonating a business or brand they trust. A good rule of thumb is not to click on any links sent via email.
Security breaches are frightening, and you may want to move your site to another web host, leaving the whole mess with GoDaddy behind. Choose a web host carefully, looking at their policies and making sure it suits your requirements. Questions to ask of your new host are things like: how do you ensure website security; how quickly do you respond to customer enquiries; and so on. Migrating the website itself is a simple task with the MigrateGuru plugin.
What should you do if your site is hosted on GoDaddy, but you are not a Managed WordPress customer?
According to their filing with the Securities and Exchange Commission (SEC), GoDaddy says that only the Managed WordPress customers and reseller accounts were involved in the data breach. Therefore, you don’t need to worry, but it is better to change all your passwords in any case.
If you use ManageWP, will you be affected?
As of writing this article, GoDaddy has not indicated that ManageWP users are affected by the data breach. However, this may be subject to change as their investigation into the breach progresses. So, to be on the safe side, we recommend you reset all your passwords.
The larger question to ask here is that if you are a ManageWP user and a GoDaddy customer, is it safe to put all your eggs in the same basket? If the Godaddy data breach was larger and the hackers had deleted websites, like what happened with Web Hosting Canada in August 2021, you would be in a bad spot as far as backups go. Because of this very reason, it is safer to have another backup provider. It is just not good practice to have backups on the same server as your website.
The security angle without the hysterics
GoDaddy is a prime target for hackers simply by the virtue of their size and popularity. Even though no system is 100% secure, GoDaddy should have taken strong measures to protect their customers, especially given their size and the resources at their disposal. Our major call out here is not that their system was breached, but that it took them over 2 months to find out. They should have processes in place to detect breaches much sooner. That is the scary aspect of this incident.
Where did GoDaddy go wrong, and why?
The general feeling about GoDaddy right now is extremely negative, and there are a lot of harsh opinions being bandied about. Some of it is unwarranted, and that is because WordPress security is not easily understood. Having said that, let’s be very clear: all security breaches are bad BUT to varying degrees.
Two problems have emerged from security researcher investigations:
- GoDaddy stored passwords in plaintext
- We can only speculate why, but generally we have seen most web hosts store SFTP passwords in plaintext. This is a convenience factor, because SFTP credentials are usually generated automatically, and not by the user. Therefore, for people to be able to use them, they are stored in plaintext.
- It took them over 2 months to detect the data breach
- As we said before, this is the real problem. Malware causes progressively more damage the longer it is left unaddressed. Hackers had access to website databases and their files for over 2 months. This is an unthinkable lapse.
What are the actions that GoDaddy is taking to resolve the issue?
GoDaddy has reset SFTP and database passwords for their customers, so all the sites should be scanned for malware and all other passwords should be changed. Additionally, GoDaddy is also in the process of reissuing SSL certificates for compromised accounts. If you have an SSL certificate issued by GoDaddy, don’t wait for them to resolve the issue. Please get a new one issued from a separate certificate authority right away.
Is GoDaddy secure? Should you change your hosting from GoDaddy?
The Godaddy data breach is serious, no doubt, and it should have been caught much earlier. However, you should make this decision based on several factors, not just this one.
SFTP and database credentials are almost always automatically generated during the setup of a website, and rarely by users.
This means two relevant things:
- The passwords are difficult to remember, and users are prone to forgetting or losing them
- The chances of these passwords being reused elsewhere is negligible.
Ideally, all stored passwords should be hashed, but in some cases this becomes impractical. And because auto-generated passwords are rarely used anywhere else, they preempt the real danger of breached credentials: passwords that have been reused on other accounts. That means, hackers cannot use these passwords to access any other account, and the damage is contained as a result.
SFTP credentials are needed for lots of admin tasks: backups, emergency cleanups, restoring websites, and much more—unless you are using a plugin that will take away that hassle. Therefore, GoDaddy, and other popular web hosts, make access to SFTP credentials easy for their customers.
Similarly with database credentials, web hosts prioritise making things easy for their customers. In fact, your wp-config file stores your database credentials in plaintext too.
So the bottom line is that all this GoDaddy bashing is focusing on the wrong problems. Plaintext passwords aren’t the issue; it is the lack of data breach detection processes that is. Web hosts are rarely the cause of websites getting hacked, so this is an aberration. It is a myth that web hosts are the entry points for malware for websites.
What about the threat of phishing?
If your email address was compromised, be aware of potential phishing scams. If you have an ecommerce store or a membership site hosted with GoDaddy, warn your website users that they should be on the lookout for phishing scams, and not to click on links sent via email.
Phishing is a type of social engineering attack, where people are fooled into giving up their data to hackers. Hackers use trusted brands to extract this information. The scam is usually two-fold: an email with bogus links, in addition to a spoofed web page with a form to collect the data.
What should I do to protect my website?
There are a few things you can do to protect your website, regardless of which web host you are using. Yes, a good web host is important from a security perspective, but up to a point. The lion’s share of the responsibility lies with you, the website owner.
Here are some things you can do right away:
- Install a security plugin with daily scans. A security plugin cannot protect you from a breach due to compromised passwords, but because you will have daily scans of your website, if there was malware on your website, you would have found out in less than 24 hours time, rather than 2 months. This is critical for malware detection and mitigating loss.
- Always opt for offsite and full backups. If anything at all happens to your web server and your backups are also stored there? That’s curtains for your website.
- Use strong and unique passwords. A compromised password is free entry into your account, and if you use the same password across multiple accounts you are essentially rolling out the red carpet to all those accounts. If there is one takeaway from this mess, it is to have different passwords for accounts. That way, even if there is a breach, the damage is contained and you are not scrambling around to secure everything else. Setting strong and unique passwords is tricky, so we recommend using a password manager.
Is WordPress secure?
Every time there is a security breach in the WordPress ecosystem, this old chestnut will reappear. People are entitled to their opinions, but the fact remains that WordPress is as secure as a system can get. It is a target for hackers because of its widespread popularity, and in fact, has evolved to resolve many of the security problems that still exist with other CMS.
As a website owner, you need to do your due diligence in making sure that the core, and all your plugins and themes are up to date.
Share it:
You may also like
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…

MalCare Proactively Defends Against Icegram Express SQL Injection Vulnerability
MalCare’s recent data has revealed numerous attempts to exploit a newly found SQL injection vulnerability in the Icegram Express plugin. Attackers commonly use this sophisticated SQL injection technique to extract…

Atomic Security’s Deep WordPress Integration Helps Protect Against Core XSS Vulnerability
The recent WordPress core vulnerability is a critical one, primarily because of two reasons. Firstly, it affects the WordPress core itself, which means that every WordPress site is vulnerable to…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








