How to Find & Remove Coinhive Malware from Your WordPress Site?
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

Are your customers complaining that your site is slowing down their computers? Before you panic, check your site files to see if you notice any unusual code that uses the word Coinhive, like Coinhive Anonymous or coinhive..com. Some quick research into your symptoms and CoinHive malware may come up as a possibility.
If you suspect your site is hacked and infected with malware, scan it immediately. The longer malware is left on a site, the worse it gets.
At its core, CoinHive is malware that harnesses a computer’s processing power for cryptocurrency mining. It gains access to your visitors’ computers by infecting your site with malware.
Frustratingly, it is particularly hard to find and identify. To detect it, you have to be really attentive to minor changes in your website. This makes it doubly important to use a security plugin like MalCare to automatically scan for malware on your site regularly.
TL;DR: MalCare’s automatic malware removal provides a simple and effective solution to get rid of CoinHive malware. With just one click, users can efficiently remove this unwanted malware from their websites. It’s an easy and hassle-free way to improve website security.
Being attacked by malware, especially when dealing with elusive and hard-to-identify strains, can be an incredibly stressful experience. It can leave website owners feeling vulnerable, frustrated, and uncertain about the extent of the damage. The invisible nature of some malware makes it challenging to detect and assess, compounding the anxiety.
With that in mind, let’s talk about what CoinHive Malware is.
What is the CoinHive malware?
Cryptocurrency mining involves verifying and recording digital transactions through complex computer puzzles, rewarding miners with cryptocurrency. CoinHive, an initially innovative service, enabled website owners to mine Monero using visitors’ processing power. However, hackers later exploited it by injecting the CoinHive code into compromised websites. This unauthorized use, often facilitated through malicious browser extensions or software, turned CoinHive into a form of Trojan horse virus.
Websites that were affected complained of performance issues, unusual network traffic, erratic browser behavior, and user complaints. In response to the growing misuse of its technology, CoinHive announced its shutdown in 2019.
Now that we understand the malware, let’s talk about how to find and clear it.
Step 1: Scan for malware
Spotting the presence of CoinHive malware is no easy task. It doesn’t come with flashy warnings or glaring pop-ups. Instead, it operates quietly in the background, making its detection a bit of a puzzle. To even suspect its existence, you might need to watch out for customer complaints of their computers slowing down or changes in site files that can’t be accounted for.
This gradual slowdown is a key indicator of CoinHive malware at work. It’s this attention to detail that can make the crucial difference. However, this is not the only malware that plays the stealth game. There’s a whole league of such hidden threats out there, and they’re not easy to spot, making a dependable scanner a necessary weapon in your cybersecurity arsenal.
In this section, we’ll talk about three different ways to scan for malware.
1. Deep scan with a security plugin:
The easiest, fastest, and most reliable way to scan for the CoinHive malware is to use a malware scanner plugin like MalCare. All you have to do is add your website to the dashboard and you can scan your site in minutes. The scanner can find malware in any corner by thoroughly scanning both your files and database.
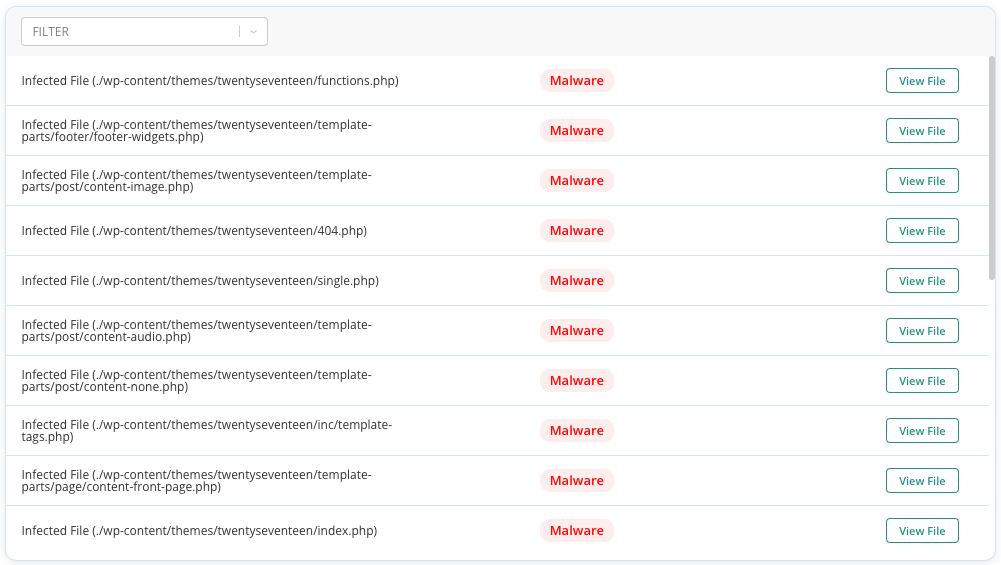
Why we recommend using MalCare
- Ease of use: It is the easiest and most accurate way to identify the malware on your site. The plugin is able to identify malware in every nook and corner of your site.
- Regularly scan for malware: Just add your site to the dashboard and MalCare will conduct regular scans. This becomes a preventative measure for future attacks.
- One-click removal: If malware is detected, you can remove the malware in just one click.
2. Frontend scan with an online scanner
Online scanners, such as Sucuri SiteCheck, provide a web-based platform to assess your website’s security status. These tools often offer a quick and accessible way to check for CoinHive malware, but they cannot be relied upon 100%.
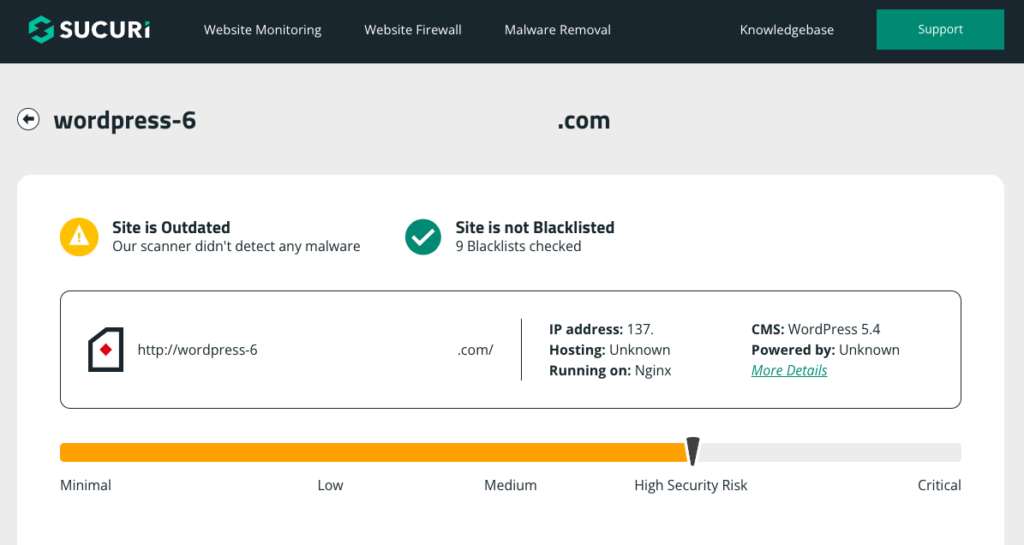
However, online scanners might not offer the same depth of scanning as dedicated plugins, potentially missing nuanced threats. They alsoonly offer one-time checks, necessitating repeated assessments for evolving threats.
3. Manual scanning
Manual scanning involves inspecting your website’s code and files personally to detect any traces of CoinHive malware. This hands-on approach demands a solid understanding of coding and web development.
When scanning for CoinHive malware manually, watch out for JavaScript code injections that typically hide within legitimate code sections. Specifically, look for suspicious functions that could be harnessing the user’s processing power without their consent. CoinHive’s presence is often concealed through obfuscation techniques, so keep an eye out for convoluted or encoded code snippets that could be indicative of malicious intent.
It should be noted that effective manual scanning requires advanced coding knowledge and familiarity with malicious code patterns. The manual process is also time-intensive, particularly for larger websites with complex codebases and you want to remove the malware as soon as possible. Additionally, because there’s a higher risk of missing or misinterpreting subtle signs of CoinHive malware, manual malware is also less accurate than Malware.
Step 2: Remove the CoinHive malware from WordPress site
Once you’ve located the CoinHive malware, it’s vital to remove it with precision. The malware may have infiltrated various corners of your website, leaving hidden traces that need to be systematically uprooted. In this section, we’ll talk about three different ways to clean your site.
1. Complete removal with a security plugin
Using a trusted security plugin like MalCare can be critical when removing CoinHive malware. This plugin can locate and eliminate malware, providing a quick and easy way to restore your website’s integrity.
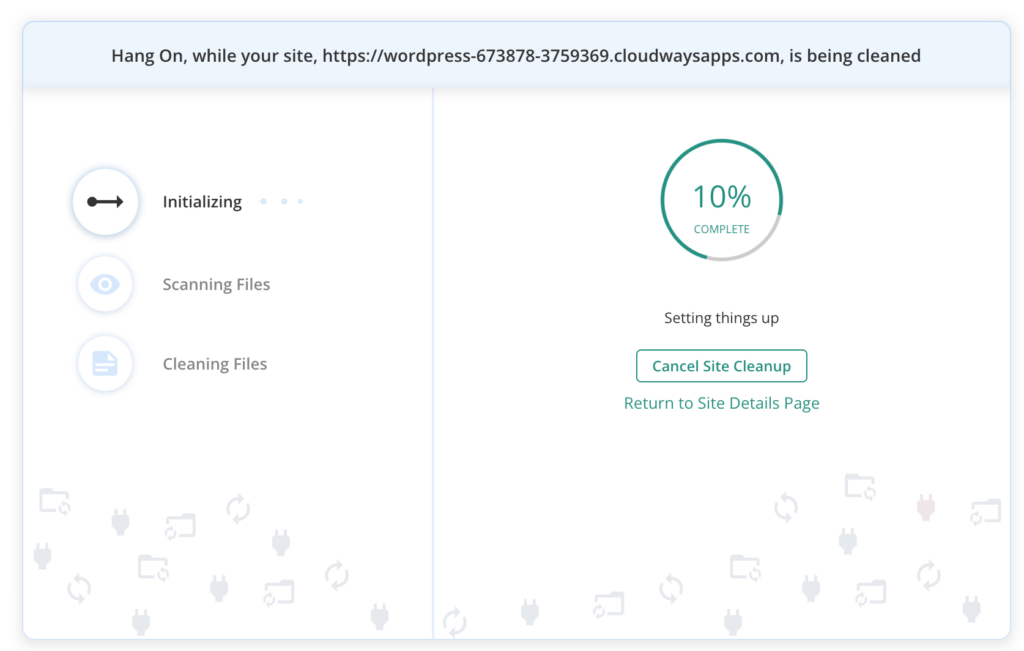
Why we recommend using MalCare:
- Ease of use: Security plugins are user-friendly and require minimal technical expertise to initiate the removal process. In fact, MalCare prides itself on being a one-click malware removal process. Considering the urgency of malware removal, this feature can be integral to your business.
- Automated cleanup: MalCare offers automated cleanup, swiftly identifying and removing CoinHive malware. It does it all while requiring very little human interaction.
2. Using a maintenance service
If the infection is particularly persistent or complex, seeking the expertise of a security professional can be a wise move. These experts possess in-depth knowledge and experience in dealing with a wide array of malware, including CoinHive. MalCare has the best security experts that can help you remove the most complex malware. However, it’s important to note that there can be a bit of a waiting period as the experts will already have a queue of hacked websites to clean. Depending on who you hire to help, it can also be more expensive.
3. Manually removing malware
For those with a solid understanding of coding and web development, manual removal of CoinHive malware is an option. This hands-on approach requires precision, attention to detail, and a lot of knowledge about coding. While we’d never recommend this method, here is a brief description on how to remove malware:
- Regain website access: To initiate the manual malware removal process, it’s essential to regain access to your compromised website. If your web host has suspended your account, contact them to resolve the issue or request a whitelisting of your IP address to access the site. Additionally, inquire with your host for a list of infected files if they suspended your account due to malware detection.
- Backup your website: Before taking any actions on your website, prioritize taking a backup of your site. This precautionary step is critical because manual cleaning can sometimes result in unintended issues. Furthermore, web hosts may delete compromised websites, and their backup retrieval is often unreliable. Therefore, having your own backup is highly recommended.
- Download clean WordPress files: Obtain clean installations of the WordPress core, plugins, and themes that match the versions currently on your website. These clean files will serve as a reference for identifying discrepancies during the cleaning process. Comparing these files with your website’s files will help detect any malicious alterations.
- Reinstall WordPress core: Begin by replacing the /wp-admin and /wp-includes folders on your website with the clean versions you downloaded. These folders primarily contain core files that should not have variations from clean installations. Additionally, inspect key files such as index.php, wp-config.php, wp-settings.php, wp-load.php, and .htaccess for any suspicious code.
- Clean plugin and theme folders: Proceed to the /wp-content folder, which houses your plugins and themes. Check for differences in the code between your current files and the clean installations. Keep in mind that legitimate customizations may appear as code variations. Focus on critical theme files like header.php, footer.php, and functions.php. Pay special attention to plugins with known vulnerabilities or outdated versions. When removing plugins, exercise caution, especially if uncertain about their legitimacy.
- Clean malware from the database: Extract the database from your backup or use phpMyAdmin to obtain a copy. Inspect the database tables for any abnormal content or scripts. Look for any newly created pages or posts that do not belong. Carefully revert modified settings to their original state and remove malicious content.
- Check root for suspicious files: While reviewing your website’s files, don’t forget to inspect the root folder. This is where some malware files may be stored. Not all PHP files in the root are harmful, as some plugins may add legitimate scripts for specific tasks.
- Remove all backdoors: Malware often leaves backdoors in websites as a means to reinfect them if discovered and removed. These backdoors can be disguised within code sections using functions like eval, base64_decode, gzinflate, preg_replace, or str_rot13. Exercise caution when deleting code sections that enable external access without proper analysis.
- Reupload cleaned files: After successfully cleaning out the malware, proceed to reupload the cleaned files and database to your website. Delete the existing files and database before doing so. You can utilize tools like File Manager, phpMyAdmin, or SFTP for this task.
- Clear the cache: Clearing the cache is essential to ensure that your website behaves as expected after the cleanup. The cache may store previous versions of your site, which could cause unexpected issues if not cleared.
- Verify plugins and themes: Test the functionality of each plugin and theme on your cleaned website to ensure they are working as expected. If you encounter issues, revisit the old plugin folders to identify code that may be responsible for the problems and transfer it to the cleaned website with caution.
- Repeat for subdomains and nested installations: If your website includes subdomains or nested WordPress installations, it’s crucial to apply the same cleaning process to them. Malware in one part of your site can easily contaminate others. Consider removing unused WordPress installations to minimize security risks.
- Use a security scanner to confirm: Finally, for peace of mind, employ a security scanner like MalCare’s free scanner to verify that all traces of malware have been successfully removed from your website. This step helps ensure that your site is clean and secure once again.
Why we don’t recommend manual cleaning
- Lack of expertise: Manual cleaning requires in-depth knowledge of malware behavior, coding, and website vulnerabilities, which most website owners lack.
- Incomplete removal: Malware can hide in unexpected places, making it difficult to find and remove entirely. Partial cleaning can result in reinfection.
- Unresolved vulnerabilities: Removing malware alone doesn’t address the underlying vulnerabilities or backdoors that allowed the hack to occur in the first place.
- Risk of website breakage: Without a thorough understanding of each file’s function and interactions, you may unintentionally damage your website during the removal process.
- Time-consuming: For large websites like e-commerce stores, manual cleaning is a time-consuming process, akin to searching for a needle in a haystack.
- Escalating damage: Hacks tend to worsen over time, leading to increased data loss and potential harm to your website.
- Data loss: Failed manual cleanups can result in data loss that cannot be recovered, leading to significant consequences for your website’s functionality and reputation.
- Repeated infections: If not all malware is removed, it can continue to replicate and reinfect your website, necessitating additional cleanup efforts.
- Limited resources: Manual removal can strain your time and resources, especially if you lack the necessary expertise, tools, and backup systems.
The most recommended approach is to install a security plugin or seek professional assistance to ensure a comprehensive and effective malware cleanup and protection strategy for your WordPress site.
Step 3: Post-hack checklist
With the successful removal of CoinHive malware from your website, the immediate threat might be wiped out, but to ensure that your site remains protected against future intrusions, there are several crucial steps you should take.
- Change passwords: Begin by changing all relevant passwords, including those for your website’s admin accounts, hosting providers, and any associated third-party services. This helps cut off potential avenues that attackers might exploit to regain access.
- Check for unauthorized users: Review your list of users and administrators. Ensure that only authorized personnel have access, and promptly remove any accounts that shouldn’t be there. This reduces the risk of unauthorized users exploiting your website in the future.
- Recover your content from a backup: WordPress hacks often result in content damage or loss. In such cases, it’s crucial to allocate ample time to restore your content using a backup. However, it’s important to note that the backup shouldn’t contain the malware either. Determining when your website became infected with malware can be challenging unless you have precise information. Additionally, be aware that the backup might still retain the vulnerabilities that initially led to the malware infection in the first place.
- Reach out to customers and notify them: If your website serves customers or users, consider sending out a notification about the security incident. Being transparent about the situation builds trust and provides them with the necessary information to take precautions on their end.
How does the CoinHive malware effect your site?
The Coinhive malware can have a range of detrimental effects on your website and its overall performance. These effects include:
- User experience issues: Slow-loading pages, unresponsiveness, and increased fan noise from users’ devices can negatively impact their overall experience on your website. This may deter them from returning in the future.
- High bounce rate: Visitors are more likely to leave your site quickly if they encounter sluggish performance or suspect that their devices are being used for cryptocurrency mining without consent. This can result in a high bounce rate, affecting your site’s engagement metrics.
- Reputation damage: If users discover that your website is engaging in cryptojacking (the unauthorized use of their computing resources), your reputation can be seriously damaged. They may view your site as untrustworthy and warn others to avoid it.
- Security risks: Malicious actors who inject Coinhive scripts into your site could potentially exploit other vulnerabilities or gain unauthorized access to your server. This can put your website and its data at risk.
- SEO impact: Google and other search engines may penalize your website in search rankings if it’s identified as hosting Coinhive malware. This can lead to decreased organic traffic and visibility.
- Loss of revenue: As visitors abandon your site due to poor performance and negative experiences, you may experience a drop in ad revenue, e-commerce sales, or other monetization efforts.
- Remediation costs: Cleaning up a site infected with Coinhive malware can be time-consuming and may require hiring cybersecurity experts to thoroughly analyze and remove the malicious code. This can result in financial expenses.
Protect your website from future attacks
Safeguarding your website from the clutches of CoinHive malware demands a proactive stance against potential threats. While no strategy can offer absolute immunity, adopting a combination of effective preventive measures can significantly reduce the risk of an attack.
- Install a firewall: A web application firewall (WAF) acts as a protective barrier between your website and potential threats. MalCare offers the best firewall in the industry because of how reliable it is. It analyzes incoming traffic, filtering out malicious requests and preventing unauthorized access. By implementing a robust WAF with MalCare, you can strengthen your website’s defenses against CoinHive malware and other cyber intrusions.
- Install a plugin with automated malware scanning: Leverage the power of automated scanning by installing a reputable security plugin like MalCare. MalCare performs regular, automated scans of your website’s code, identifying any signs of malware intrusion. Swift detection allows you to take immediate action and prevent the malware from establishing a foothold.
- Take regular backups: Backing up your website’s content, databases, and code at regular intervals is not only a prudent practice but also a crucial lifeline in case of an attack. In the event of a hack or security breach, having a recent backup allows you to quickly restore your website to a known, clean state. This minimizes downtime and ensures that your website can be up and running again promptly.
- Keep everything up to date: Hackers often exploit vulnerabilities in outdated software, themes, plugins, and WordPress. Regularly update all components of your website, including WordPress, themes, and plugins, to patch potential entry points for malware.
- Watch out for uploaded files: Monitor and scrutinize any files uploaded to your website. The best way to do this is using an activity log. An activity log can help you identify if files are being added to your site without any authority. By maintaining strict control over file uploads, you minimize the risk of malware embedding itself into your website.
Final thoughts
Different types of malware attacks can cause frustration and fear and they all feel equally violating. This is especially true for malware like CoinHive where the hacker is exploiting your websites and your visitors’ computers for their monetary gain.
However, there is no one-size-fits-all solution to safeguarding your WordPress site, and a multi-layered defense strategy emerges as a prudent choice. With its robust firewall, regular scanning, and malware removal capabilities, MalCare offers a strong defense against various types of malware, including CoinHive.
Additionally, using strong, unique passwords and implementing two-factor authentication strengthens your website against unauthorized access, reducing the risk of breaches that could lead to malware attacks.
FAQs
What is the CoinHive malware?
CoinHive malware is a type of malicious software that utilizes a website visitor’s processing power to mine cryptocurrency, specifically Monero, without their consent or knowledge. This unauthorized use of computing resources can slow down the user’s device and compromise their security. CoinHive malware often hides in compromised websites, browser extensions, or software, surreptitiously benefiting hackers by generating cryptocurrency through the unsuspecting user’s computer.
Is CoinHive illegal?
While CoinHive itself was initially introduced as a legitimate way for websites to monetize without ads, its misuse for cryptojacking led to ethical and legal concerns. The unauthorized use of someone else’s computing resources for cryptocurrency mining without their consent is generally considered unethical and, in many cases, illegal. Legal consequences vary depending on jurisdiction and the extent of harm caused to users.
What happened to CoinHive?
CoinHive ceased its operations in early 2019. The service was widely criticized for enabling cryptojacking attacks and negatively impacting users’ online experiences. This, coupled with the increasing awareness of cybersecurity risks and the ethical implications of cryptojacking, led to CoinHive shutting down its mining services. However, remnants of CoinHive’s code and the potential for similar malware threats persist.
What is cryptojacking?
Cryptojacking is a form of cyberattack where malicious actors exploit the computing resources of unsuspecting users to mine cryptocurrencies. This can be done through compromised websites, malicious browser extensions, or infected software. Cryptojacking often slows down the victim’s device, increases energy consumption, and compromises overall performance. It is a type of cybercrime that seeks to generate cryptocurrency for the attacker without the user’s consent or knowledge.
Share it:
You may also like
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…

MalCare Proactively Defends Against Icegram Express SQL Injection Vulnerability
MalCare’s recent data has revealed numerous attempts to exploit a newly found SQL injection vulnerability in the Icegram Express plugin. Attackers commonly use this sophisticated SQL injection technique to extract…

Atomic Security’s Deep WordPress Integration Helps Protect Against Core XSS Vulnerability
The recent WordPress core vulnerability is a critical one, primarily because of two reasons. Firstly, it affects the WordPress core itself, which means that every WordPress site is vulnerable to…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








