Beyond Cloudflare: Fortifying WordPress Security
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

In the WordPress ecosystem, it is widely believed that Cloudflare’s firewall is the gold standard of security that any site can get. Its arsenal of features, including robust DDoS protection and a powerful content delivery network (CDN), has earned it a solid reputation. Some of the top web hosts trust Cloudflare and its ability to give their websites a security and performance boost.
But here’s the thing: Cloudflare’s firewall on its own is not enough to ensure your site’s security. You need a dedicated WordPress security firewall.
95% of hacks on WordPress sites occur due to vulnerabilities, and WordPress-specific firewalls block exploits of those vulnerabilities. We, at MalCare, have long advocated the advantages of a dedicated WordPress firewall over a cloud-based firewall like Cloudflare for this very reason.
As we analyzed the data from a recent vulnerability-based attack, we could further validate this assertion. This data underscores the critical importance of specialized WordPress security over broad solutions.
The Forminator Vulnerability: A Wake-Up Call
Recently, a significant file upload vulnerability was exposed in the widely used WordPress plugin named Forminator, crafted by WPMU DEV. This plugin helps its users easily create forms, polls, quizzes, and surveys on websites. This vulnerability allowed attackers to insert malicious code into WordPress sites. This potentially gave them the power to perform remote code execution attacks, which put site and user data at risk, among other things.
The vulnerability was publicly disclosed by a security researcher on July 20, 2023, and the developer released a patch on August 16, 2023. As you can see, there was a significant gap of almost a month. As a result, the vulnerability was repeatedly exploited. This is the case with all vulnerabilities, even those disclosed responsibly by security researchers. There is always a gap before an update is released, which means sites are vulnerable to successful attacks.
Over the month, thousands of these attacks were attempted on sites protected by MalCare. MalCare’s firewall promptly blocked the exploits. And, all of this happened before the vulnerability was even publicly disclosed or patched.
Cloudflare’s Role in the Equation
During our analysis of the attack, we discovered that close to half of the websites were also utilizing Cloudflare’s firewall. This firewall sits on proxy servers right in front of the website servers and processes client requests. As such, no request directly reaches the website servers without going through Cloudflare’s cloud firewall.
This arrangement adds a strong layer of security by filtering all requests to the websites. The location of Cloudflare’s proxy servers in the communication tree makes them good at controlling traffic to the servers, handling DDoS attacks, and speeding up content delivery. These are some of the reasons why Cloudflare is trusted in our industry.
However, the Cloudflare firewall did not flag the attacks on the Forminator plugin as malicious. They allowed these attacks to reach the websites, putting them at severe risk.
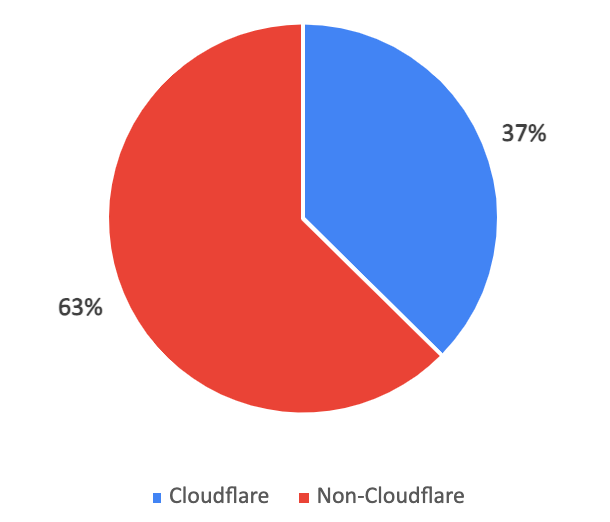
If these sites hadn’t had MalCare’s firewall, the malicious requests would have reached the sites, as they had been allowed through by Cloudflare. This conclusion is clear: Cloudflare cannot prevent WordPress-specific exploits proactively and is virtually ineffective against zero-day exploits.
Where Cloudflare Fell Short
Let’s get into the details. In the case of the Forminator vulnerability, Cloudflare’s standard security measures proved to be insufficient. Ideally, Cloudflare’s firewall should’ve been the hero of the day, swiftly detecting and preventing these attacks.
However, the Cloudflare firewall operates on a broad level, not distinguishing between WordPress sites and other platforms. While custom rules can be set, they may not always offer the precision required for WordPress sites. And let’s be honest: it is virtually impossible for most folks to correctly configure firewall rules for their sites unless they understand network security. This means that your site still remains vulnerable.
Cloudflare’s website provides an overview of their firewall plans and their associated rules. While Cloudflare provides predefined rules and custom rules, they are very generalized and not WordPress-specific. Moreover, the cheaper plans have limited features, like a limited number of applicable rules (as shown in the following image), which pose a significant risk to your site.
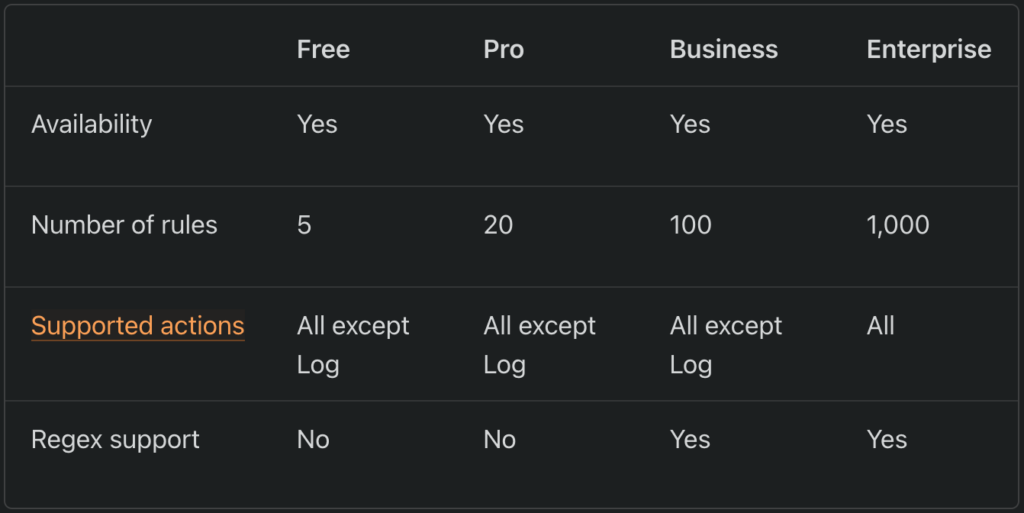
Setting up firewall rules requires specialist knowledge, and is well outside the skill set of most WordPress admins. Therefore, while Cloudflare allows for custom rules, it would be the rare user who can set this up effectively enough to safeguard their site.
Furthermore, WordPress sites require special rules to protect vulnerabilities from being exploited. In the security plugin landscape today, WordPress-specific plugins are the only ones to crack these rules—as evidenced by the Forminator exploit.
The WordPress Firewall Advantage
This brings us to the world of WordPress firewalls. Good ones are like your site’s personal bodyguards, trained specifically for WordPress threats. They are also much smarter than generic ones any day of the week.
For example, in the case of the Forminator vulnerability, it was critical to separate legitimate file uploads from malicious ones. This means that a site administrator must have access to upload certain files, but the same access must not be provided to a regular user. This can only be achieved if there is a clear way to distinguish one from the other.
This is something that Cloudflare will always find difficult to tackle, as its firewall rules are very generic. Instead, a WordPress firewall could smartly solve this with the use of WordPress APIs.
This is what MalCare did. Its firewall was critical in stopping those thousands of attacks exploiting the Forminator plugin. Why? Because it’s all about WordPress. With sharp algorithms and aggressive rule sets, it has a greater understanding of your site’s traffic. Plus, it’s right there on your WordPress site, so it knows the ins and outs like the back of its hand. In short, it is the perfect foil to attacks that manage to penetrate even the strongest defenses.
Is Cloudflare No Good?
We are not saying that at all. Cloudflare is a champion when it comes to stopping nasty DDoS attacks. These attacks can wreak havoc on your site, costing you time, money, and reputation. Although WordPress sites are not as prone to DDoS attacks, as to vulnerability exploits, you should definitely keep Cloudflare in your corner for its performance and DDoS protection.
Let us share a real-world incident. A close friend of ours runs a really popular blog site. As the blog gained traction, their readership also increased, until a sudden turn of events put their website to the test.
It all began on a seemingly ordinary day when our friend decided to check their website’s performance. They were accustomed to seeing a steady stream of visitors, but that day was different. As they logged into their website’s analytics dashboard, they were greeted with a surprising sight: a huge jump in site traffic. Now such an increase would make any website owner jump with joy. But as they dug deeper into their visitor logs, the surprise quickly turned into worry.
This was followed by several complaints from their users that they were receiving an HTTP 503 error whenever they tried to access the site. Even those who could access the site complained that it had become really slow. These were clear signs that their site was under the dreaded DDoS attack.
However, our friend was not someone to be caught off guard. Fortunately for them, they had decided to utilize Cloudflare’s services on their site. This decision would turn out to be critical in a very dramatic way.
As the attack became much more severe, Cloudflare’s firewall jumped into action. It started scanning all incoming traffic, promptly identified the bot IPs that were sending repeated requests, and blocked them. Gradually, the bot traffic died down and regular service was resumed on the site. Users were now able to access the site without any hiccups. All of this happened without our friend’s involvement and saved them from significant financial loss as well as reputation loss.
This was no small victory. Our friend’s website had survived a terrible DDoS storm and came out safe. In a nutshell, Cloudflare proved its worth in the DDoS arena.
What about WAF?
You are right to ask this question. A dive into Cloudflare’s documentation will show that a Web Application Firewall (WAF) also exists apart from their cloud-based firewall services. So, could the WAF have stopped these attacks?
To answer that, let us look at what the WAF is. The WAF is a part of Cloudflare’s firewall stack. It is a collection of 5 rulesets created and pre-defined by Cloudflare. Out of these 5 rulesets, only 1 (Free Managed Ruleset) is available to all customers. This means that to utilize the full feature set of the WAF, you will have to upgrade to one of their paid versions.
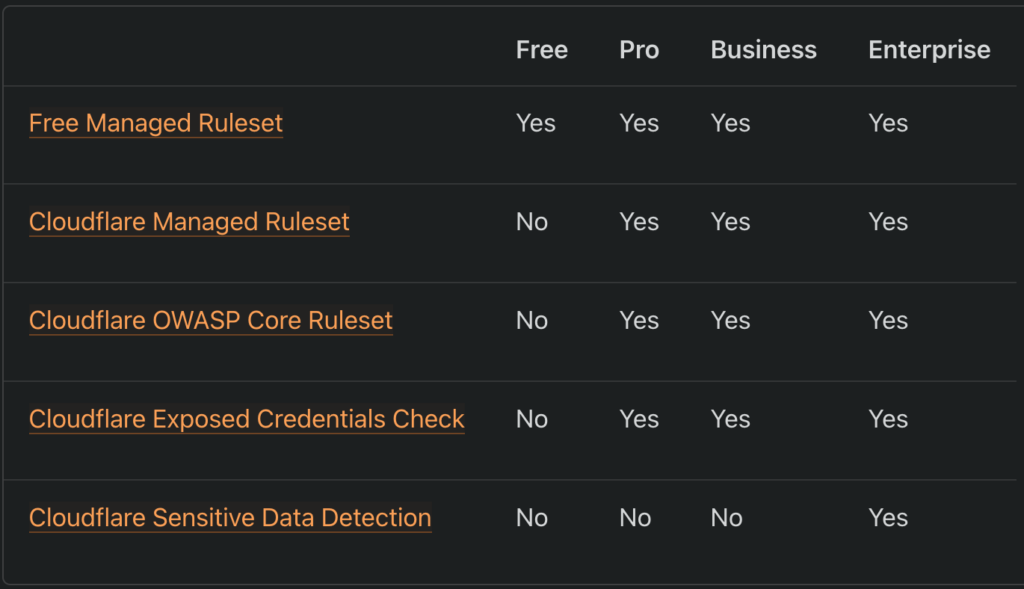
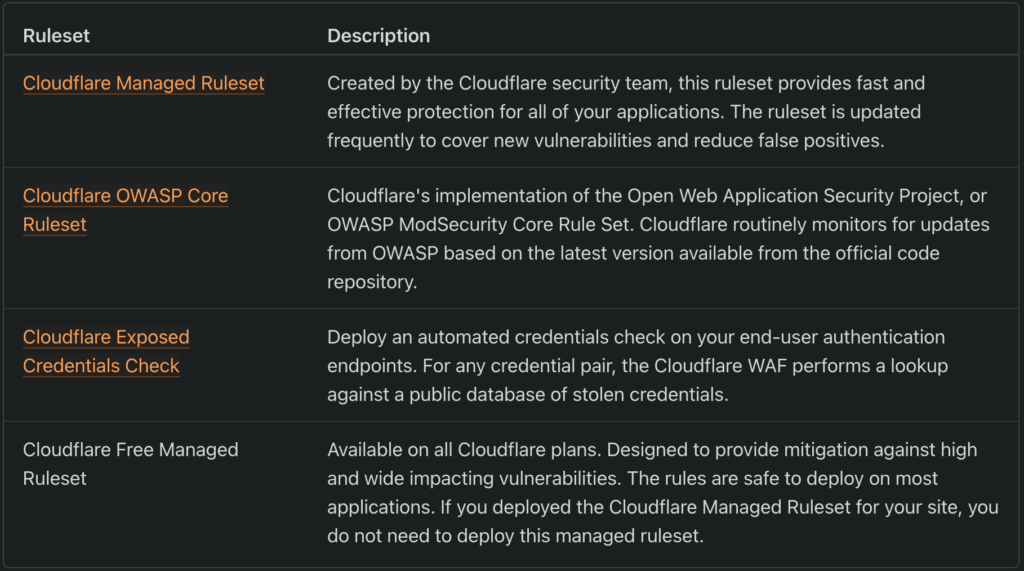
Now, when it comes to protecting WordPress sites, the Cloudflare WAF provides rules matching only the common exploits. This means that, while the WAF offers some level of protection against WordPress-specific attacks, it cannot protect your sites from much more severe and emerging threats.
This is what happened when the Forminator vulnerability attacks began. Since the Cloudflare WAF was not configured to address these attempts, it let them through. But when they reached MalCare’s firewall defenses, these attacks were thwarted right away.
Conclusion
To wrap it up, Cloudflare undoubtedly plays a crucial role in strengthening website security. However, it should not be viewed as the ultimate solution. The Forminator vulnerability incident serves as a wake-up call, highlighting the importance of specialized WordPress security plugins, which have been so far looked down upon. Hence, we would advise you to install a WordPress-specific security plugin on your website to keep it secure, over and above the services that your web host provides.
PS: A secure version of WordPress requires many different layers. Cloudflare’s WAF is one of them, but there’s of course lots that needs to be done at the application level. But the meme was too good not to use 😄
From – Remkus
Category:
Share it:
You may also like

How to Fix the Google Blacklist Warning from Your Website
Google blacklist is a colloquial term used to describe big red warnings visible when visiting websites. There are a few flavours, depending on various factors, but they all mean that…

MalCare Stands Strong Against WP Activity Log Premium SQL Injection Vulnerability
A significant SQL injection vulnerability was identified in the WP Activity Log Premium plugin, a popular tool for tracking user activity on WordPress sites. An SQLi vulnerability poses a serious…
Fix Pharma Hack on WordPress and SEO
Pharma hack is a prolific malware that redirects visitors from your site to an online pharmacy that sells Viagra, Cialis, Levitra, Xanax, Tadalafil, and other drugs. It also shows up…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








