What Is SEO Spam and How to Remove It From WordPress Site?
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.
After investing a great deal of time, money, and effort into optimizing your website for search engines, your website is showing spam results on Google.
SEO spam is a malicious attack that involves hackers infiltrating your WordPress site and filling it with spammy links. Hackers exploit vulnerabilities in WordPress websites to carry out their attacks. If left unaddressed, SEO spamming can lead to a loss of traffic, revenue, and credibility for your website.
The first thing to do is scan your site for the hack causing the spam attack.
However, the good news is that there are ways to identify and defend against these attacks. In this article, we’ll provide you with all the information you need to understand what is SEO spam, how they work, and most importantly, how to protect your website from them.
TL;DR: Spamdexing can have a devastating impact on website owners, causing significant damage to their online reputation and customer trust. Scan your site comprehensively with MalCare to instantly detect SEO spam infection on your website.
What is SEO spam or spamdexing?
SEO spam attack is a black hat SEO technique used by hackers to manipulate search engine results by filling your website with spam links and keywords. You wouldn’t even be any the wiser, unless you have a daily malware scanner installed on your site to flag these issues.
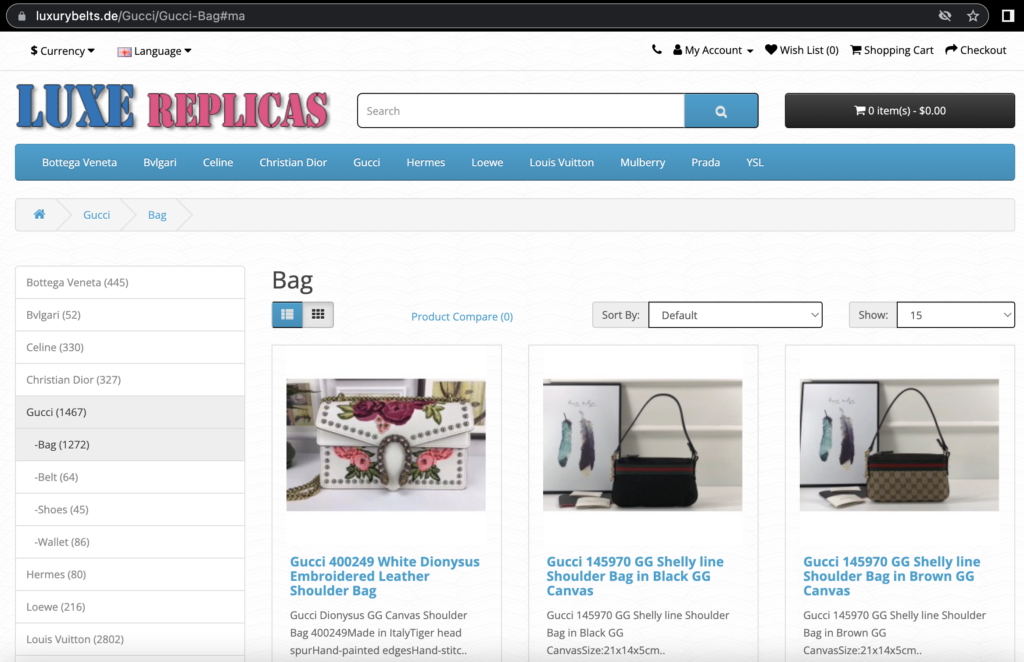
Search engines like Google typically reject spammy links to fake products, pharmaceutical ads, and adult, or gambling sites. But, they may mistakenly index the spam pages on your site due to their SEO value and authority.
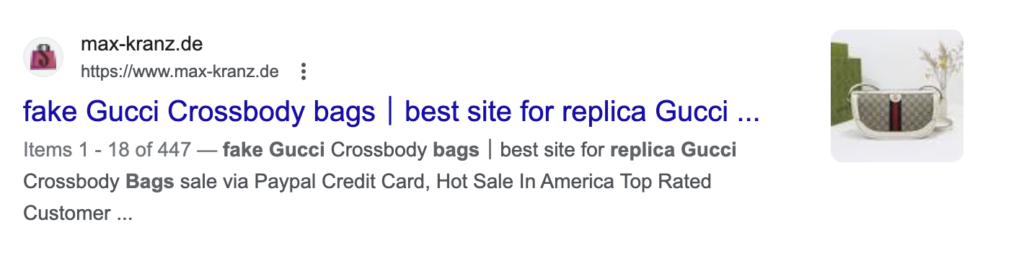
This tactic aims to attract people looking for these queries and get them to click through to the spam pages. Unfortunately, this is a short-lived strategy, as Google will eventually flag your site for malware and blacklist it. However, hackers often execute this attack on thousands of sites to maximize their returns.
If your WordPress is infected with SEO spam, you may notice some hack symptoms. These include a slower site, abnormal analytics with an increase in bounce rates or unexpected spikes in traffic, and visitors complaining about strange content on your site that you may not be able to see.
🚨 Scan your site with MalCare to find out whether it is infected with SEO spam.
Step 1. Diagnose an SEO spam attack
Identifying SEO spam as soon as possible is crucial to minimize the damage to your website’s reputation and search engine ranking. There are a few ways to do so, and we’ve listed them out in order of efficacy.
Option 1. Deep-scan with a security plugin
The quickest, most effective method is to scan your site with a security plugin. MalCare offers a comprehensive scanning process that checks your website for malware and other security issues. Here are the features that you will find helpful:
- Database and file scanning for malware
- Accurate detection of backdoors
- Minimal impact on site performance during scans
- Advanced scanning algorithm beyond file matching
- Scans WordPress cron to detect reinfection malware
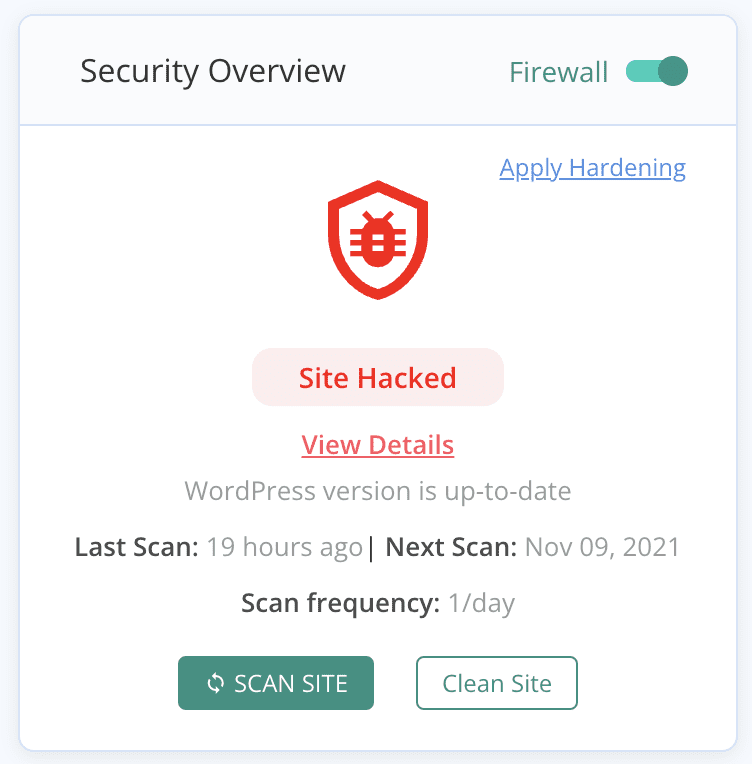
We thoroughly tested all the major WordPress security plugins. iThemes Security, Sucuri, and WordFence, amongst others, all have scanning functionality. However, our tests showed that none of them really did a good job of identifying malware on your site consistently. Sitelock, for example, may throw out the following message:
html-seo spam-nlp sitelockMalCare, on the other hand, is the best plugin for scanning your website for SEO spam malware.
Option 2. Online scanners
Online malware scanners are web-based tools that allow you to scan your website for malware and other security issues. These scanners work by analyzing your website’s code and checking it against a database of known malware signatures.
If Sucuri Sitecheck detects SEO spam in the public areas of your website, it may show one of the following messages:
spam-seo.hidden_content
spam-seo.spammy_keywordsHowever, there is one major caveat with online scanners. They cannot access every part of your site, and so they cannot detect malware in critical files and folders that are not publicly visible. In fact, this is one of the main reasons why malware is often found in those particular site files. Online scanners will often give you a clean bill of health even if there is malware in the wp-includes folder for instance.
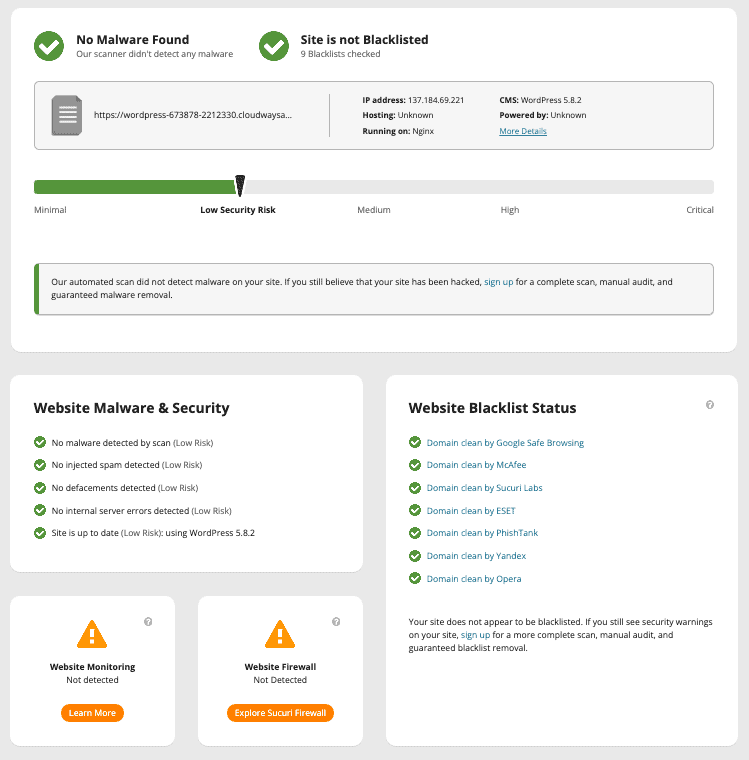
While these scanners can detect some malware, they can’t remove it. That’s why using a security plugin like MalCare is a better option.
Option 3. Manual scanning
Manual malware scanning involves comparing your website’s files and databases with a known-good backup or a clean version of the site. This process requires checking each file manually, line by line, to identify any malicious code or security issues.
Manual scanning is the least effective method of detecting malware. On top of that, it is an incredibly time-consuming process and requires considerable technical expertise. There is also a huge chance of missing malware altogether, either because it is very well-hidden or you don’t know what it looks like.
Unfortunately, there is no set template for malware, making it challenging to identify all security issues manually. This is precisely why scanners use malware signature databases, and even those have problems because malware changes frequently.
Manual malware scanning, and indeed removal, is a last ditch resort or a learning exercise only. Security plugins are a far better solution.
Other diagnostics
Deep-scanning your site for malware is always the best route to take, however if an online scanner has given your site a clean bill of health, you can look for confirmation in other places.
- Check search results for your site
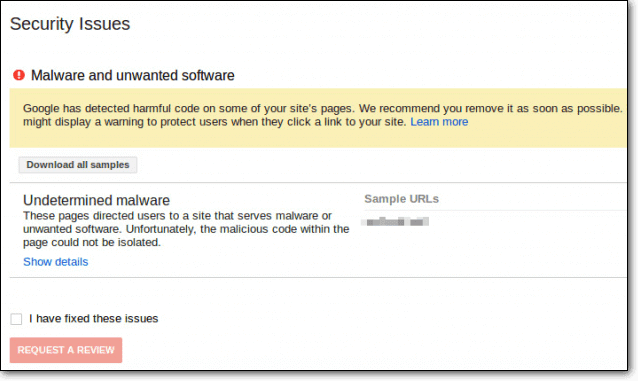
- Check Google Search Console; especially the Security Issues tab for alerts
- Check your sitemap for spam pages
- Use the URL inspection tool to check for cloaked content and potential 404 errors
- Check for any extra .htaccess files as your website generally has only one
Step 2. Remove SEO spam from WordPress
There are three ways to remove SEO spam from your WordPress site: automatically with a security plugin, using a malware removal service, or manually. As you can imagine, automatically is the best and manually is the worst.
Option 1. Remove SEO spam with a security plugin
The easiest and most effective way to remove malware is by using a security plugin. The best security plugins will scan your site for malware, identify the malicious files, and remove them automatically—keeping your site 100% intact. MalCare is an excellent example of a security plugin that can remove malware quickly and effectively.
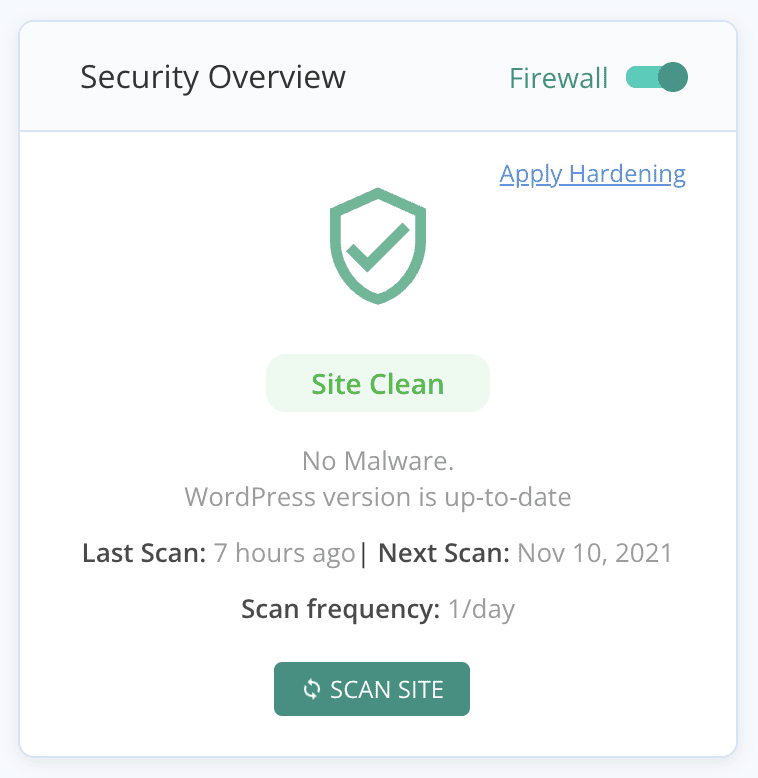
Option 2. Hire a WordPress maintenance service
Another option to deal with a hacked site is to reach out to an expert service. There are several WordPress maintenance services that specialize in malware removal.
There are two downsides to using a maintenance service: firstly, they are always busy, and so your site may not get a slot for weeks. Secondly, services like these are prohibitively expensive.
All things considered, we still recommend opting for a maintenance service rather than cleaning the site on your own.
Option 3. Remove SEO spam in WordPress manually
The manual malware removal process involves going through your site file by file, and removing the malicious code from them. Then you need to repeat the process with the site’s database as well.
This method requires technical expertise, not only to identify and remove the malware, but also to make sure not to mess up legitimate site code. It’s also essential to identify and fix the vulnerability that allowed the malware to infect your site in the first place to prevent future attacks and reinfection. Also, you need to be aware that leaving even the smallest trace of malware can undo all your work in a matter of hours.
Ultimately, automatic removal with a security plugin is the recommended method as it’s quicker, more effective, incredibly precise, and doesn’t require technical expertise.
1: Regain access to your site
If your website has been taken offline by your web host due to malware, you need to act quickly to regain control of your site. The first step is to contact your hosting provider and request that they whitelist your IP at the very least. This will allow you to access your website.
While you’re on the line with your hosting provider, ask if they have any logs or records related to the malware that caused the blacklisting. This information can help you identify the type of malware that you need to remove and determine how the attack occurred in the first place.
2: Take a backup
Always take a backup before attempting to manually remove malware from your website. Create a separate backup for the cleaning process to avoid overwriting critical files.
3: Make a note of all plugins and themes
List all the plugins and themes with their version numbers. Note down any customisations in the code too. This list will help download fresh extensions and add back customisations later.
4: Download WordPress, plugins, and themes
Download the correct WordPress, themes, and plugins versions from official sources. These are the clean files that you will use to compare your corrupt files with. It is important to match the versions to the ones installed on your hacked site. Developers can change quite a lot in updates.
5: Compare the clean and corrupt WordPress files
The hard part starts now. To identify malware on your website, compare downloaded files to those on your site, and scrutinize PHP scripts for suspicious content.
Pay especial attention to the index.php, wp-config.php, wp-settings.php, wp-load.php, and .htaccess files. The /wp-uploads folder should never contain PHP files; remove them immediately. Be very careful about what you are removing. Always make changes on a backup, ensuring that another backup is available in case something goes wrong.
6: Clean plugins and themes
Within the /wp-content folder, you will come across directories for both themes and plugins. While reviewing the files for any potentially malicious code, keep in mind that not all differences signify a threat. Customizations made to your website can also appear as differences. In the event that you do not value these customizations, it may be more efficient to replace the entire folder instead of attempting to identify individual files.
7: Remove the malware from the database
Malware can be lurking in the database, making it crucial to comb through the wp-posts and wp-pages tables for spam pages. These pages can number in the hundreds of thousands and cause significant problems. Hacked redirect malware is also very prevalent and may be found in multiple locations, making removal more challenging.
8: Look for suspicious files
The public_html folder, or the root folder, contains the core files, themes, and plugins of your WordPress website. Starting from here, look for lurking malicious files.
9: Remove the backdoors
Backdoors are a type of malware used by hackers to gain access to compromised websites, circumventing login pages and other safeguards. These also cause malware reinfections.
Look for unusual code functions like eval, base64_decode, and preg_replace to detect backdoors. Although these are legitimate functions, they are often used to obscure malware.
Removing backdoors can be technical, but plugins and tools are available to help. Immediate removal is crucial to prevent further damage. Seek professional assistance if unsure.
10: Upload the clean files
After removing malware from your website’s files and database, upload the cleaned versions using cPanel or an FTP client. To manage the database, use cPanel or a database manager and upload it separately, as you would for a manual backup.
11: Check plugins and themes
After uploading clean files and databases, ensure all plugins and themes are functioning properly by checking every page on the website. Look to make sure all your pages are working as normal.
12: Remove malware from subdomains and nested WordPress sites
When removing malware from your website, don’t forget to check subdomains, nested WordPress sites, and staging sites. Malware can spread between sites on the same cPanel. Repeat the removal process on all affected sites to ensure your website is completely clean.
13: Scan the whole site once more
Once you have cleaned up your website, the final step is to scan the entire site using a trusted security plugin or an online scanner. This ensures that there are no remaining traces of malware, providing added peace of mind and protection for your site.
Step 3. Post-cleanup checklist
After successfully removing malware from your website, it is essential to take a few additional steps to ensure that your site is fully secured. This post-hack checklist outlines some important steps you should take to prevent future attacks and restore your site’s credibility
- Remove any unauthorized owners from Google Search Console (GSC) and revoke their verification token from your website. This may involve checking your website’s .htaccess file as well.
- Clean all website caches to remove any remnants of the malware.
- Request that Google re-index your site and submit a cleaned sitemap. If you have cleaned your website of malware but are still seeing spam characters in your search results, it may be because Google has not yet recrawled your site.
Step 4. Prevent further SEO spam infections
Now that you have cleaned up your site and removed the malware, it’s important to protect your WordPress site from getting infected with SEO spam or other attacks in future. A daily malware scan is a great monitor for highlighting problems as soon as they occur. In addition, here are some great tips to keep your site secure:
- Install a security plugin with a firewall: A firewall acts as a barrier between your website and the internet, blocking malicious traffic and preventing unauthorized access. Website application firewalls are specifically designed to protect web applications and are crucial in protecting against attacks like SQL injections and cross-site scripting attacks (XSS). MalCare is a security plugin with top-notch firewalls that provide real-time protection against malicious traffic. It actively observes and evaluates incoming traffic for any abnormal actions or trends.
- Make sure your site has SSL: SSL (Secure Socket Layer) encrypts data that passes between your website and the user’s browser, making it harder for hackers to intercept and steal sensitive information. Google also favors sites with SSL and may rank them higher in search results.

- Keep everything updated: Regularly updating your WordPress version, plugins, and themes helps to patch any security vulnerabilities that may have been discovered. This reduces the risk of your site being compromised due to outdated software.
- Implement login security measures: Implementing login security measures like two-factor authentication (2FA) and limiting login attempts can prevent brute force attacks. A brute force attack is when a hacker tries to guess your login credentials by repeatedly trying different combinations of usernames and passwords.
What are the types of SEO spam?
Spam attacks can come in different forms, and it’s important to understand them to protect your website. Here are some common types of spam attacks and what they entail:
- Spammy keyword insertion: This type of attack involves inserting spammy keywords into your website’s content or meta tags. This can negatively impact your website’s search engine rankings and make your content difficult to read for users.
- Spam link injection: In this attack, spammers inject links to their own websites into your site’s content or comment sections. These links can be harmful to users and also negatively affect your search engine rankings.
- Creating spam pages: Spammers may create new pages on your website that contain spammy content or links. These pages can be hidden from admin or regular users but still affect your website’s search engine rankings.
- Display spam ads and banners: This type of attack involves displaying spammy ads or banners on your website without your consent. These ads can be harmful to users and negatively affect your website’s reputation.
- Spam emails: Spammers may also send spam emails to your website’s users, which can contain harmful links or phishing attempts.
- Other SEO spam attacks: We’ve talked about SEO spam attacks, but the following are specific cases of SEO spam:
- Japanese SEO spam: This is a type of attack where spammers insert Japanese keywords into your website’s content, which can negatively affect your search engine rankings.
- Chinese search results spam: Similar to the Japanese keyword hack, this type of attack involves spammers manipulating your website’s search engine results with Chinese keywords.
- Pharma hack: In this type of attack, spammers create new pages on your website that advertise gray market and illegal pharmaceutical products.
Why did my website get hacked?
Hackers and attackers have various motives for hacking websites, ranging from spreading malware to stealing sensitive information. In this section, we will explore the common reasons why websites are hacked
- Websites can be hacked to improve clients’ SEO by filling the site with links, without the knowledge of the client or reseller.
- Hackers may use a compromised website to send spam emails from a server that hasn’t been blacklisted by email providers.
- Hackers may also hack websites to make money by replacing or adding advertisements to the site.
- Some hackers may use a hacked website’s resources to help them hack into other sites or for cryptocurrency mining.
- Websites can also be hacked to steal credit card information and other credentials.
- Hackers may use a hacked website as a place to store downloads containing viruses.
- Unethical competitors will hire hackers to compromise a site for negative SEO.
What is the impact of SEO spamming?
Website security impacts SEO significantly. Concurrently, SEO is a key part of digital marketing. Therefore, attacks like SEO spam can significantly affect a website in multiple ways:
- It can negatively impact the website’s search engine rankings as Google and other search engines penalize websites that use black hat SEO techniques.
- It can damage the website’s reputation and credibility as it may lead to the display of irrelevant and spammy content to users.
- It can lead to the website being flagged by or anti-malware tools, or even end up on blacklists, like the Google Transparency Report.
- It can harm the website’s user experience as users may be redirected to irrelevant or harmful websites or encounter spammy pop-ups and ads.
- It can potentially result in the theft of sensitive user data, such as login credentials, credit card information, and personal information.
Overall, SEO spam can upend your SEO strategy, wiping out months of effort and investment.
Wrap up
Website security is crucial for any website owner. The increasing frequency of website hacks and SEO spam attacks demands a robust security solution to protect your website. MalCare offers the best solution with its advanced website security features such as website application firewalls, malware scanners, login protection, and much more. Its real-time protection, easy-to-use interface, and timely alerts make it the ideal security solution for all websites. By taking the necessary preventative measures and using a reliable security plugin like MalCare, you can safeguard your website against any potential security threats and enjoy peace of mind.
FAQs
What is SEO spam?
SEO spam refers to the tactics used by hackers to manipulate search engine rankings and drive traffic to their websites. This can include inserting spammy keywords and links, creating spam pages, and injecting spam ads and banners.
How do I fix spam SEO?
To fix spam SEO, you need to first identify and remove any malicious code or content from your website. This can be done manually or with the help of a security plugin. Once the spam has been removed, you should request Google to reindex your site and resubmit a cleaned sitemap. Implementing preventive measures, such as installing a security plugin with a firewall, keeping everything updated, and implementing login security measures, can also help prevent future attacks.
What is SEO malware?
SEO malware is malicious code that is injected into a website to manipulate search engine rankings and drive traffic to spammy or malicious websites. It can be difficult to detect and can cause serious harm to the website’s SEO and reputation.
How do I get rid of SEO spam?
To get rid of SEO spam, you need to first identify and remove any malicious code or content from your website. This is best done using a security plugin. Once the spam has been removed, you should request Google to reindex your site and resubmit a cleaned sitemap. Implementing preventive measures, such as installing a security plugin with a firewall, keeping everything updated, and implementing login security measures, can also help prevent future attacks.
Share it:
You may also like

MalCare Ensures Proactive Protection Against WP-Members XSS Vulnerability
MalCare continues to protect its customer sites from all kinds of attacks, even the ones exploiting zero-day vulnerabilities. The recent stored cross-site scripting (XSS) vulnerability found in the WP-Members Membership…
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…

MalCare Proactively Defends Against Icegram Express SQL Injection Vulnerability
MalCare’s recent data has revealed numerous attempts to exploit a newly found SQL injection vulnerability in the Icegram Express plugin. Attackers commonly use this sophisticated SQL injection technique to extract…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








