Ultimate Guide To WordPress User Enumeration
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

As a developer setting up security measures or a new WordPress site owner learning about various ways to secure your site, you likely have concerns about user enumeration. It’s a vector through which attackers can glean usernames—a first step towards unauthorized access.
The stakes are high, as a compromised username list can lead to targeted brute-force attacks, account takeovers, and a host of other security breaches that jeopardize user trust and the site’s integrity.
In this article, we will break down user enumeration and walk you through the different ways that you can protect your site from it.
TL;DR: For robust protection against user enumeration on your WordPress site, use MalCare. MalCare’s bot protection, combined with login protection fights user enumeration on multiple fronts.
What is WordPress user enumeration?
WordPress username enumeration is the process by which someone can identify the valid usernames of a WordPress website. This is often achieved through automated bots that exploit features, such as author archive pages, REST API endpoints, or the login page error messages.
Attackers use this tactic to gather a list of usernames which can then be used to attempt login breaches, such as password brute-forcing, to gain unauthorized access to the WordPress admin dashboard or user accounts.
Prevent user enumeration attacks
Taking proactive steps can significantly reduce the risk of your usernames becoming a treasure trove for hackers.
The best and simplest solution is to use a firewall, like MalCare, with robust bot protection and good login security.
1. Install firewall with bot protection
Firewalls serve as the gatekeepers of your WordPress site, scrutinizing incoming traffic and blocking malicious entities. MalCare’s firewall is equipped with bot protection that automates the detection of suspicious activities often associated with user enumeration attacks.
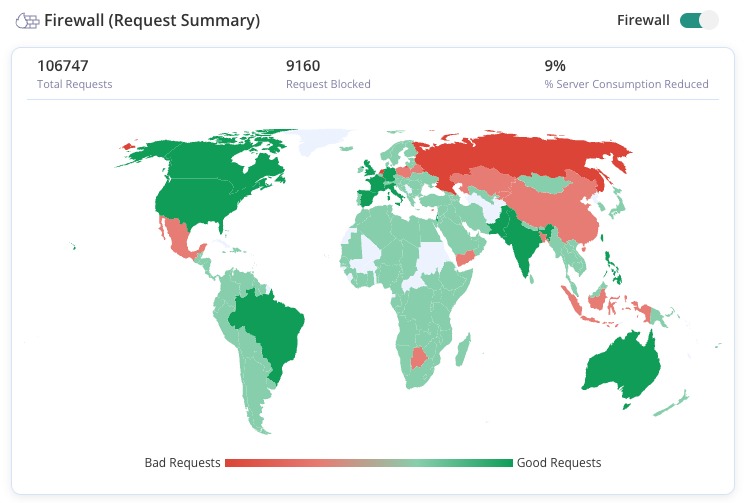
It is equipped to detect and block automated bots that are often employed for user enumeration. Since these bots can operate at scales and speeds that surpass human capabilities, having a firewall that automatically identifies and stops them is crucial in ensuring your site is not bombarded with enumeration attempts that could lead to further brute force or credential-stuffing attacks.
It only takes two steps to install MalCare:
- Create an account
- Add your URL to the dashboard
MalCare will scan your site and install a firewall automatically.
2. Limit logins
By restricting the number of login attempts from a single IP address, you can thwart brute force and dictionary attacks following user enumeration.
MalCare’s limit login attempts feature halts persistent attackers before they can break in. Once the limit is reached, MalCare will block the IP address for a specified duration.
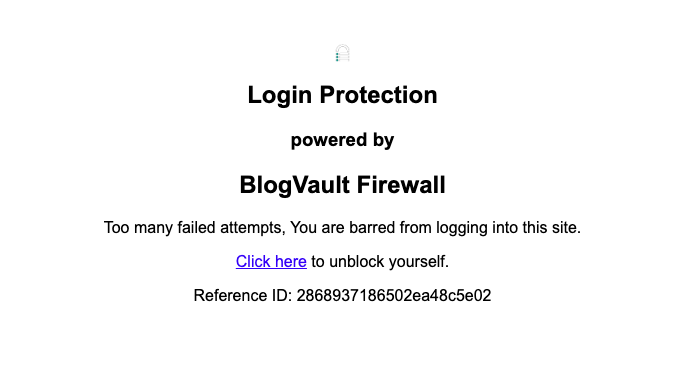
If you’re worried about genuine users getting blocked, MalCare has you covered. A genuine user just needs to solve a reCAPTCHA puzzle to regain access.
3. Monitor activity log
Keeping an eye on the activities within your WordPress site can alert you to unusual behavior that might indicate an ongoing attack attempt. MalCare’s activity log feature records user actions, making it easier for you to spot irregularities in user account activity.
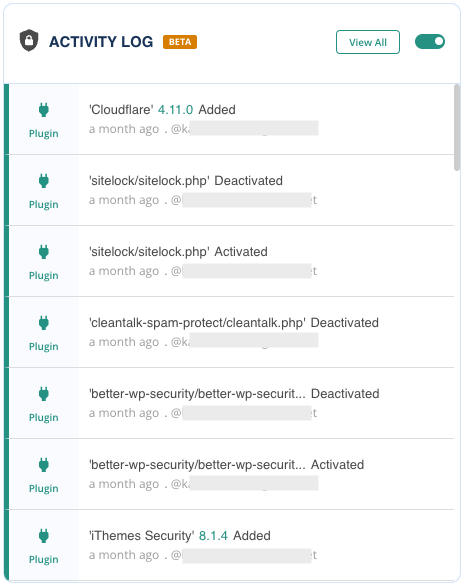
Regularly review the logs from your MalCare dashboard, paying close attention to repeated failed login attempts from single users or unusual user behavior.
4. Manage user roles
Role management acts as an internal safeguard, minimizing the risk posed by user enumeration by restricting privileges and access. By giving users only the permissions they need to perform their tasks, you reduce the potential damage of an account compromise.
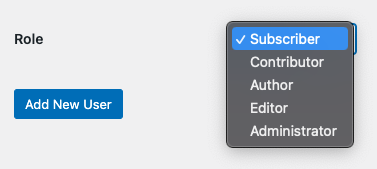
From the WordPress dashboard, review and adjust the roles and capabilities of your users. Avoid using admin as a username, as this is one of the most targeted by attackers. Assign roles carefully, adhering to the principle of least privilege.
5. Customize error messages
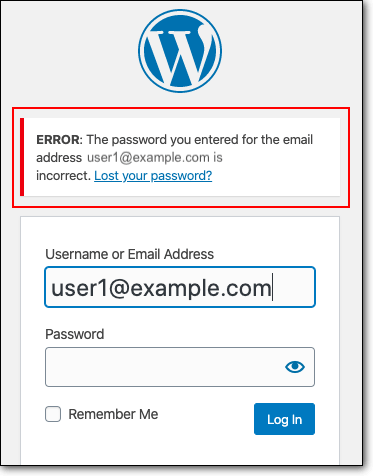
One often overlooked aspect of WordPress security is the error messages displayed during the login process. Standard error messages, such as “Invalid username” or “Incorrect password,” can unintentionally aid attackers in their user enumeration efforts by confirming the existence (or non-existence) of a user account.
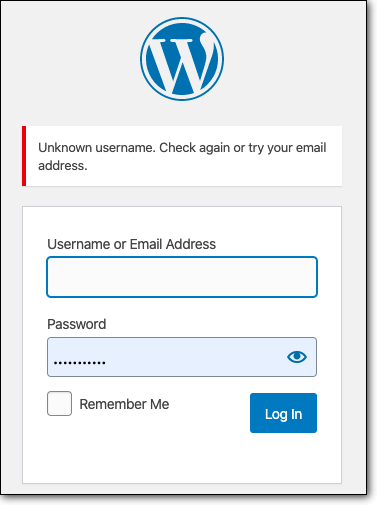
To mitigate this vulnerability, you can customize the error messages to be generic, ensuring that they do not differentiate between a nonexistent username or an incorrect password.
You can use a custom code plugin like Code Snippets to insert snippets of code directly into your site without modifying theme files, making the customization process safer and updates hassle-free.
- Install the plugin: Navigate to the Plugins section in your WordPress dashboard, click Add New, search for Code Snippets plugin, install it, and activate it.
- Write the custom code: Create a new snippet in the plugin with the following code or a variation of it to suit your needs.
PHP
function custom_login_error_message() {
return 'The entered information is incorrect. Please try again.'; // Custom message
}
add_filter('login_errors', 'custom_login_error_message');
This code uses the WordPress login_errors filter hook to modify the login error message and replace it with a generic response.
- Activate the snippet: Once you’ve added your custom code snippet, activate it within the custom code plugin’s interface. After activation, the plugin will execute this snippet of code, and your custom error message will replace standard error disclosures.
To ensure your code works as expected, test the login process with both incorrect usernames and passwords. The error message should now be uniform, regardless of which type of login error occurs.
6. Install security headers
HTTP security headers are a type of HTTP response header—sent by the server alongside content—that adds a layer of security to help mitigate attacks and security risks. They are not directly visible to users but work in the background to protect the integrity of the communication between the user’s browser and the website.
Security headers set policies that the browser enforces, such as content restrictions, connection requirements, and the handling of scripts. By setting these security-centric policies, headers can help to prevent cross-site scripting (XSS), clickjacking, code injection, and other types of attacks that could lead to user enumeration and the stealing of sensitive information.
7. Disable or modify author archives
The default URL for an author archive in WordPress is typically something like this: example.com/author/username/. This structure means that anyone can simply add /author/ after the main URL of a WordPress site and potentially guess or brute-force usernames to discover the corresponding author archive pages. It’s also very easy to use site operators and find the authors on Google too.
Attackers can also exploit WordPress’s template redirection features—for instance, when a non-existent author slug is entered, WordPress can redirect users to the author archive if the slug matches a valid username.
There are two things that you can do to reduce the chance of such attacks:
- Disable author archives: To completely disable author archives, add this code to your functions.php file:
add_action('template_redirect', 'disable_author_archives');
function disable_author_archives() {
if (is_author()) {
global $wp_query;
$wp_query->set_404();
status_header(404);
// Optionally redirect to homepage
// wp_redirect(get_home_url());
}
}This will redirect all author archive pages to a 404 page. If you’d like to redirect to the homepage instead, enable the redirection by removing the // in the the wp_redirect line
- Modify the archives: If you want to keep author archives but modify them, for example, to change their layout or the information displayed, you can usually do this through your theme’s files. You have to edit the author archive template. Author archive pages typically use the author.php file. If your theme does not have an author.php file, WordPress will use archive.php or index.php as a fallback. Once you’ve located the appropriate file, you can make changes directly to it. For example, you might want to:
- Remove the display of the author’s email or website:
Comment out the relevant lines so it looks like:
<?PHP
// Check if the author description exists
// if(get_the_author_meta('description')) {
// echo '<h2>About the Author</h2>';
// echo '<p>' . get_the_author_meta('description') . '</p>';
// }
?>- Add or remove certain user metadata from being displayed: Find the corresponding metadata functions and comment it out. For example:
<?php // the_author_meta('description'); ?>Your code may not look exactly like this. It’s dependent on whether you already have author archives and how you’ve designed them.
8. Secure APIs
Application Programming Interfaces (APIs), such as XML-RPC and REST API, are used to integrate external features into a website, like connecting to an external dashboard or posting content from outside wp-admin.
However, these same APIs can be vulnerabilities when it comes to user enumeration. By querying specific endpoints, external parties can potentially access sensitive user data, laying the groundwork for more severe, targeted cyberattacks. Querying specific endpoints involves sending specific requests to specific URLs, and without proper security measures in place, unauthorized users could potentially gain access to sensitive data or perform unauthorized actions within a system or application.
- Authenticating REST API access: One effective method to protect against unauthorized data scraping through the REST API is to require authentication for any requests. By restricting access to authenticated users, it becomes substantially more difficult for attackers to gain valuable information about user accounts.
You may consider reading up on Basic Authentication processes for REST APIs, which stipulate that requests must be accompanied by valid user credentials, such as username and password encoded in the HTTP header.
- Disabling REST API: If your website doesn’t rely on external applications or services that require the REST API, disabling it might be the safest course. This can be accomplished by inserting a snippet of code into your theme’s `functions.php` file:
add_filter( 'rest_enabled', '__return_false' );This code effectively disables the REST API, eliminating the possibility of user enumeration through this vector. Keep in mind, however, that this approach might affect the functionality of some plugins that depend on the REST API and it should not be taken without ensuring that your site’s functionality remains intact.
Similarly, you can disable XML-RPC completely, as it is rarely used any more, and it is mostly included for backward compatibility.
9. Update WordPress site
Outdated WordPress core, themes, and plugins may containcan introduce security holes that facilitate user enumeration and other attacks. Regular updates patch these vulnerabilities and improve your site’s overall security posture.
Regularly check for updates from your WordPress dashboard in the Updates section. Automate updates where possible to ensure your site remains at the forefront of security.
10. Prevent case sensitivity bypass
Case sensitivity bypass refers to the exploitation of the way servers handle different cases (uppercase vs lowercase) in URLs or parameters. Some servers or applications might treat different cases as equivalent, while others do not.
An attacker could attempt to access restricted directories or files by changing the case of the letters in the URL. For example, if example.com/ADMIN is restricted but example.com/admin is not, an attacker might gain access to sensitive areas by using the lowercase path.
The good thing is, this is dependent on the server you are using. By default, Unix-based systems are case sensitive but Windows isn’t. If you use a Windows server, check out WSL documentation or hire a professional developer to help you out. It is very technically difficult to do.
Another option is to set the correct file permissions. We recommend that you review file permissions anyway. File permissions are rules applied to files and directories on a web server that dictate who can read, write, or execute the stored content. In Unix-like operating systems, which most web servers run, these permissions are usually represented by a three-digit code, with each digit reflecting the rights of the user, group, and others, respectively.
By setting strict file permissions, you ensure that only authenticated and authorized users within the server can access these directories while preventing web-based access that ignores case sensitivity.
Test that your protective measures are working
If you’ve implemented authentication and authorization controls, you need to verify that they correctly identify and permit valid users while denying access to unauthorized users. Here are some things that you can do to check:
- Create user accounts with different roles (admin, editor, subscriber, etc.) and log in to test what each role can and cannot do.
- Use MalCare to find vulnerabilities in your WordPress installation.
- You can attempt to access your website repeatedly and rapidly to see if you get blocked or receive an error message after hitting the rate limit you set.
Why user enumeration is a security issue
A hacker manually, or using automated tools, enters different usernames into the login page of the target system. If there are known vulnerabilities in the system that leak information about usernames, the hacker may exploit these vulnerabilities to gather a list of valid usernames.
In some cases, the hacker may transition to brute force attacks, systematically trying various combinations of usernames and passwords to gain unauthorized access. Once valid usernames are identified, the hacker can use this information for further attacks, such as launching targeted brute force attacks to guess passwords or attempting to exploit weaknesses in specific user accounts.
The hacker may use the gathered information, including valid usernames, for social engineering attacks. For instance, they might attempt to impersonate users or trick them into revealing sensitive information.
To avoid detection, the hacker may cover their tracks by minimizing the number of failed login attempts or using techniques to obfuscate their activities. If successful, the hacker may maintain persistent access to the system, continuing to exploit the compromised accounts for various malicious activities.
Types of attacks that use user enumeration
Understanding the different faces of user enumeration is crucial for administrators and website owners who wish to protect their online presence. In this section, we will delve into the anatomy of various user enumeration attacks.
- Brute force attack: Attackers launch a brute force attack after successfully enumerating user names. They use these usernames and repeatedly try different passwords until the correct one is guessed. This method relies on persistence and the hope that users have employed weak or common passwords that are relatively easy to crack through constant automated guessing.
- Credential stuffing: Credential stuffing is a sophisticated offshoot of brute force attacks where attackers take advantage of usernames and password combinations that are already known—usually from data breaches on other sites—and try them out. This attack preys on the common user behavior of reusing passwords across multiple online services.
- Dictionary attacks: Once user enumeration has provided a list of valid usernames, dictionary attacks often follow. Unlike standard brute force attacks using random password combinations, dictionary attacks leverage a curated list of commonly used or likely passwords. Combining the enumerated usernames with these lists significantly increases the chances of an attacker gaining unauthorized access.
- Phishing and spear phishing: Leveraging the power of social engineering, phishing attacks involve sending deceptive messages to trick users into revealing their passwords.
In the case of spear phishing, the attack is more targeted. With access to the enumerated list of usernames, attackers personalize their deceptive communications to add credibility and drastically improve their chances of duping users into compromising their accounts.
Impact of user enumeration attacks
User enumeration is a security issue that, while often subtle in its approach, can have far-reaching and damaging consequences for individuals and organizations alike. By understanding the impacts associated with this vulnerability, WordPress site owners can appreciate the gravity of the threat and prioritize preventative measures. The following outlines key areas where user enumeration can have a significant impact.
- Privacy violation: User enumeration directly compromises user privacy. Attackers who gain access to personal usernames can pry into users’ site activities and link usernames to real-life identities. This violation of privacy can be distressing and dangerous for users and serve as a stepping stone for further personal data breaches.
- Account takeover: Enumerated usernames make it easier for attackers to focus their efforts on account penetration. With half of the login credentials in hand, all that remains is for an attacker to crack passwords, often through brute force attacks, leading to unauthorized access and control over user accounts.
- Information harvesting: Harvested usernames can be exploited to gather more information about individuals, especially if the same username is used across multiple platforms. Combined with other data harvesting methods, attackers can assemble detailed profiles of individuals, which can be used in targeted phishing schemes or identity theft.
- Reputation damage: A successful user enumeration attack can tarnish the reputation of a website or business. As users become aware of security shortcomings and the potential exploitation of their data, trust is eroded. Recovering from such reputation damage often requires significant effort, transparency, and investment in stronger security measures.
- Regulatory compliance issues: Many regions and sectors impose strict data protection regulations, such as GDPR in the European Union, which require the safeguarding of user data. A breach resulting from user enumeration could mean non-compliance, leading to investigations, fines, and mandatory corrective measures, all of which can be costly and damaging to an organization’s standing.
Final thoughts
User enumeration poses a very real threat to WordPress security, but with the right defensive strategy, it can be effectively countered. MalCare stands out as the best solution for combatting vulnerabilities, offering a comprehensive security suite that is both intuitive and robust. Through its intelligent firewall, regular updates, and an array of preventative tools, MalCare not only addresses the risks associated with user enumeration but elevates the overall security posture of your WordPress site.
FAQs
Is user enumeration possible in WordPress?
Yes, user enumeration is possible in WordPress. WordPress exposes usernames in various ways, such as through the author archives URLs, REST API endpoints, or within the HTML of posts, which can be exploited to discover user names.
How do I see the list of users in WordPress?
To see the list of users in the WordPress admin area, navigate to the ‘Users’ menu. Here you can view all registered users, their roles, and other details. Only administrators and users with permission can access this list from the dashboard.
What is user enumeration?
User enumeration is a technique used by attackers to reveal usernames, and sometimes other user details, on a system or application. It often involves exploiting predictable patterns or information leaks within a website or service.
Is user enumeration possible?
Yes, user enumeration is possible, particularly on platforms or sites where user information is not adequately protected or is inadvertently exposed through features such as login error messages, account recovery functionalities, or publicly available APIs.
What is user enumeration in WordPress?
In the context of WordPress, user enumeration refers to the process of obtaining a list of valid usernames from a WordPress website, often using methods such as exploiting the REST API, RSS feeds, or various author archive pages.
How can user enumeration impact the security of my WordPress site?
User enumeration can lead to privacy breaches, further targeted attacks like brute-force password hacking or phishing, and can serve as a stepping stone for larger-scale security breaches affecting your WordPress site.
Are there specific WordPress REST API endpoints vulnerable to user enumeration?
Yes, there are specific REST API endpoints in WordPress, such as `/wp-json/wp/v2/users/`, which can be used to enumerate users when not secured properly.
What measures can I take to prevent user enumeration attacks on my WordPress site?
To prevent user enumeration, you can hide login error messages, limit login attempts, install security plugins like MalCare, manage API access, keep WordPress and plugins updated, and adjust file permissions appropriately.
Does user enumeration have any implications for SEO?
User enumeration itself typically doesn’t have direct SEO implications. However, if it leads to a security breach and site integrity issues, it can negatively affect the user experience and trust, which consequently can impact SEO.
Can user enumeration lead to unauthorized access to user accounts?
Yes, once a user’s username is known, it can facilitate brute-force or password-spraying attacks, which may eventually lead to unauthorized account access.
What role does the REST API play in user enumeration vulnerabilities?
The REST API in WordPress can provide endpoints that may reveal user data such as usernames, unless access to these endpoints is secured through authentication or other restrictions.
Are there security plugins specifically designed to protect against user enumeration in WordPress?
Security plugins like MalCare are designed to protect against a variety of threats, including user enumeration, by providing firewalls with bot protection, login protection, and more.
How often should I update my WordPress site to mitigate user enumeration risks?
You should update your WordPress core, themes, and plugins as soon as updates become available, as these often include security patches to protect against known vulnerabilities, including those related to user enumeration. We recommend using a staging site to test your updates first, though.
What should I do if I suspect my WordPress site is vulnerable to user enumeration?
If you suspect your site is vulnerable to user enumeration, you should review your site’s security practices, update all components, and consider installing a security plugin to address any vulnerabilities. We recommend that you install MalCare, scan your site, and remove any malware that the plugin finds.
Category:
Share it:
You may also like

MalCare Ensures Proactive Protection Against WP-Members XSS Vulnerability
MalCare continues to protect its customer sites from all kinds of attacks, even the ones exploiting zero-day vulnerabilities. The recent stored cross-site scripting (XSS) vulnerability found in the WP-Members Membership…
![Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]](https://www.malcare.com/wp-content/uploads/2022/12/malcare-default-image.jpeg)
Top 9 ManageWP Alternatives To Manage Multiple Sites Easily [Reviewed]
ManageWP is a popular name in the WordPress maintenance plugins market. People love how much you get for a free plan, how easy it is to set up, and how…

MalCare Proactively Defends Against Icegram Express SQL Injection Vulnerability
MalCare’s recent data has revealed numerous attempts to exploit a newly found SQL injection vulnerability in the Icegram Express plugin. Attackers commonly use this sophisticated SQL injection technique to extract…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








